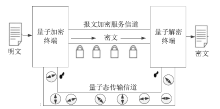
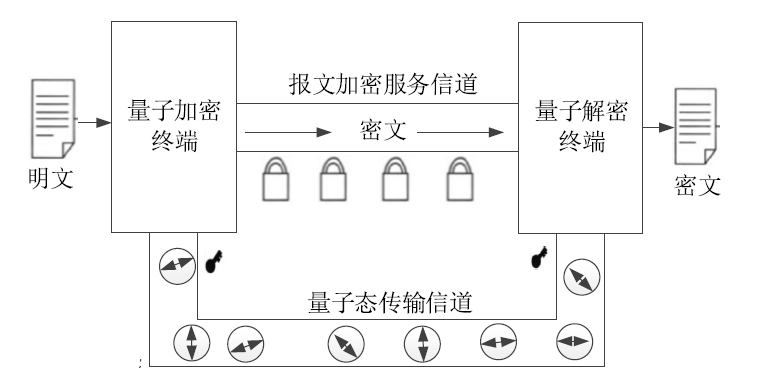
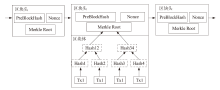
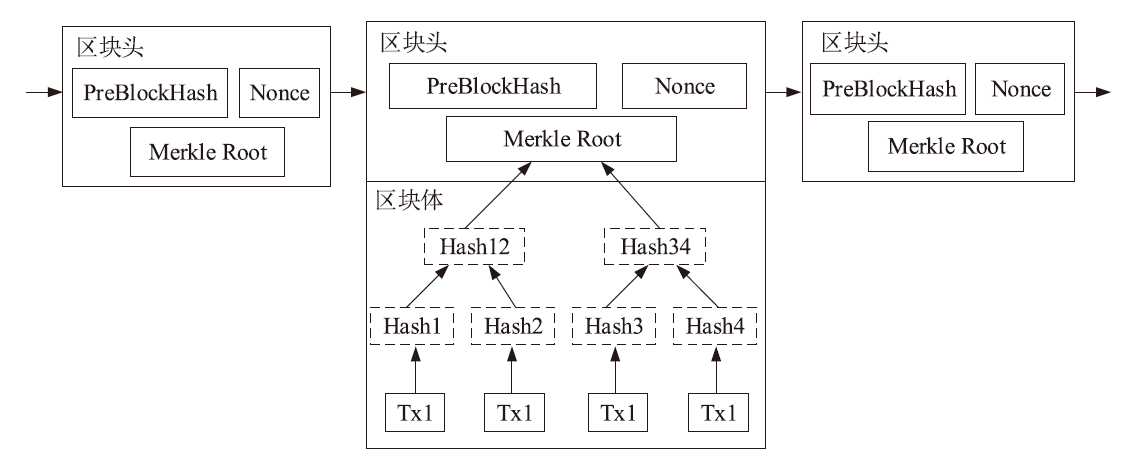
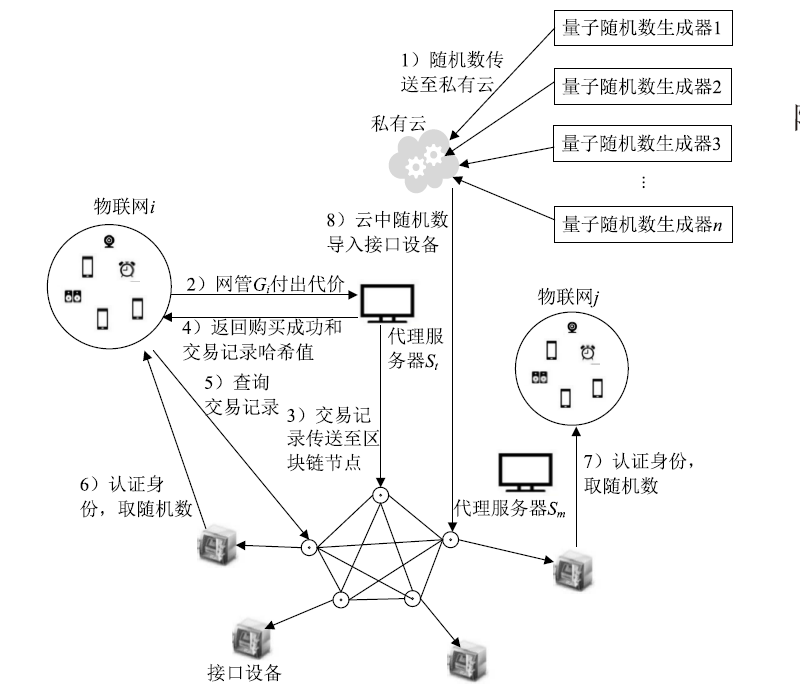
Netinfo Security ›› 2020, Vol. 20 ›› Issue (8): 1-8.doi: 10.3969/j.issn.1671-1122.2020.08.001
Previous Articles Next Articles
Key Management Scheme for IoT Based on Blockchain Technology
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2020-05-11Online:2020-08-10Published:2020-10-20 -
Contact:SHI Runhua E-mail:rhshi@ncepu.edu.cn
CLC Number:
Cite this article
SHI Runhua, SHI Ze. Key Management Scheme for IoT Based on Blockchain Technology[J]. Netinfo Security, 2020, 20(8): 1-8.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.08.001
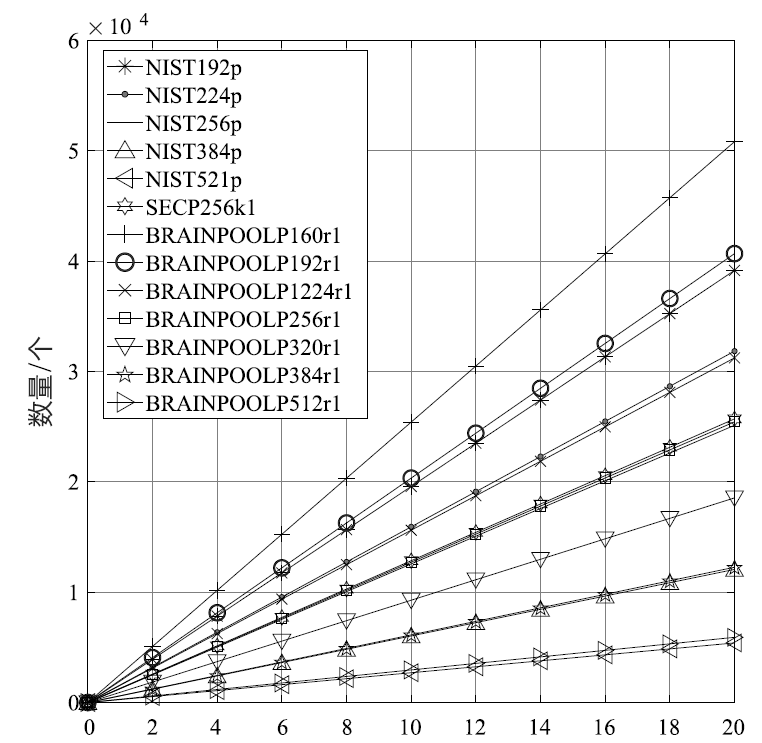
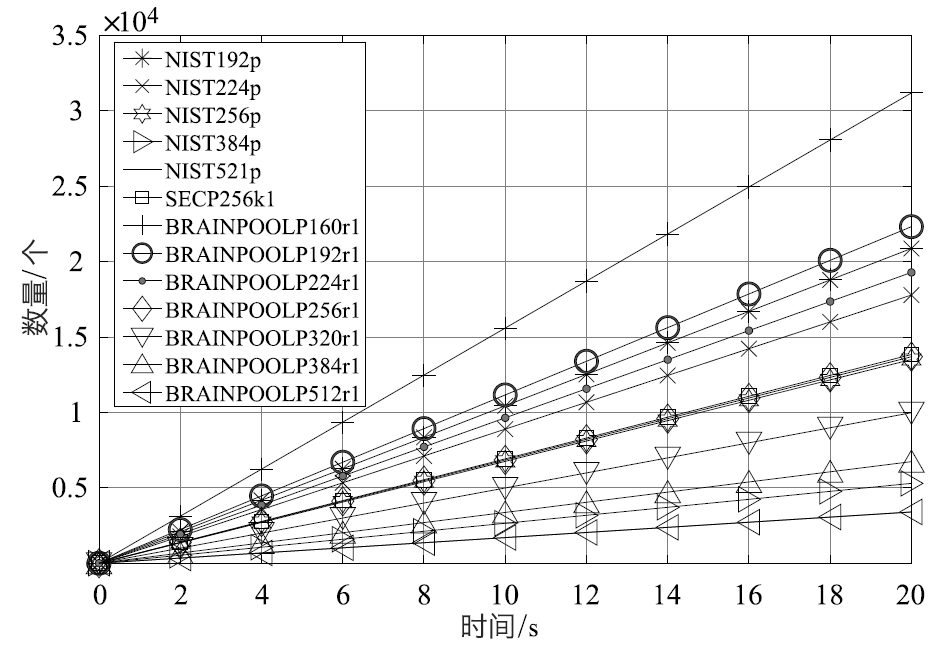
| 曲线 | siglen | sign | sign/s | verify | verify/s |
|---|---|---|---|---|---|
| NIST192p | 48 | 0.00051 s | 1958.15 | 0.00096 s | 1043.69 |
| NIST224p | 56 | 0.00063 s | 1592.33 | 0.00112 s | 889.21 |
| NIST256p | 64 | 0.00080 s | 1256.33 | 0.00148 s | 675.38 |
| NIST384p | 96 | 0.00166 s | 603.27 | 0.00378 s | 264.74 |
| NIST521p | 132 | 0.00370 s | 270.07 | 0.00589 s | 169.65 |
| SECP256k1 | 64 | 0.00078 s | 1285.33 | 0.00145 s | 692.02 |
| BRAINPOOLP160r1 | 40 | 0.00039 s | 2541.60 | 0.00064 s | 1559.46 |
| BRAINPOOLP192r1 | 48 | 0.00049 s | 2034.21 | 0.00090 s | 1116.00 |
| BRAINPOOLP224r1 | 56 | 0.00064 s | 1561.74 | 0.00104 s | 964.17 |
| BRAINPOOLP256r1 | 64 | 0.00079 s | 1271.84 | 0.00146 s | 684.67 |
| BRAINPOOLP320r1 | 80 | 0.00108 s | 927.34 | 0.00200 s | 498.99 |
| BRAINPOOLP384r1 | 96 | 0.00163 s | 613.03 | 0.00297 s | 336.76 |
| BRAINPOOLP512r1 | 128 | 0.00338 s | 295.45 | 0.00588 s | 170.02 |
| [1] | WU Hequan. Technology and Application Progress on Internet of Things[J]. Chinese Journal on Internet of Things, 2017,1(1):1-6. |
| [2] | YAQOOB I, HASHEM I A T, AHMED A, et al. Internet of Things Forensics: Recent Advances, Taxonomy, Requirements, and Open Challenges[J]. Future Generation Computer Systems, 2019,92(92):265-275. |
| [3] | ESCHENAUER L, GLIGOR V D. A Key Management Scheme for Distributed Sensor Networks[C]// ACM. 9th ACM Conference on Computer and Communications Security, October 20, 2002, Washington, USA. New York: ACM, 2002:41-47. |
| [4] | CHAN Haowen, PERRIG A, SONG D. Random Key Pre-distribution Scheme for Sensor Networks[C]// IEEE. IEEE on Security and Privacy, May 18, 2003, Berkeley, CA, USA. New York: IEEE, 2003: 197-213. |
| [5] | DU Wenliang, DENG Jing, HAN Yungsiang, et al. A Pairwise Key Pre-distribution Scheme for Wireless Sensor Network[J]. ACM Transactions on Information and System Security, 2005,8(2):42-51. |
| [6] | LIU Donggang, NING Ping. Establishing Pairwise Keys in Distributed Sensor Networks[C]// Association for Computing Machinery. CCS03: Tenth ACM Conference on Computer and Communications Security, October 21-23, 2003, Washington DC, USA. New York: ACM, 2003: 52-61. |
| [7] | LIU Donggang, NING Ping. Establishing Pairwise Keys in Distributed Sensor Networks[J]. ACM Transactions on Information and System Security, 2005,8(1):72-82. |
| [8] | MAURER U M. Secret Key Aggreement by Public Discussion from Common Information[J]. IEEE Transactions on Information Theory, 1993,39(3):733-742. |
| [9] | XUE Kaiping, MA Changsha, HONG Peilin, et al. A Temporal-credential-based Mutual Authentication and Key Agreement Scheme for Wireless Sensor Networks[J]. Journal of Network and Computer Applications, 2013,36(1):316-323. |
| [10] | VAIDYA B, MAKRAKIS D, MOUFTAH H T. Improved Two-factor User Authentication in Wireless Sensor Networks[C]// IEEE. 6th IEEE International Conference on Wireless and Mobile Computing, October 11-13, 2010, Niagara Falls, Canada. New York: IEEE, 2010: 600-606. |
| [11] | HE Daojing, GAO Yi, CHAN S, et al. An Enhanced Two-factor User Authentication Scheme in Wireless Sensor Networks[J]. International Journal of Ad Hoc & Sensor Wireless Networks, 2010,10(4):361-371. |
| [12] | TURKANOVIC M, HOLBL M. An Improved Dynamic Password-based User Authentication Scheme for Hierarchical Wireless Sensor Networks[J]. Elektronika Ir Elektrotechnika, 2013,19(6):109-116. |
| [13] | BENNETT C H, BRASSARD G. Quantum Cryptography: Public Key Distribution and Coin Tossing[C]// IEEE. International Conference on Computers Systems and Signal Processing, September 12, 1984, Bangalore, India. New York: IEEE, 1984: 175-179. |
| [14] | ELKOUSS D, MARTINEZ-MATEO J, CIURANA A, et al. Secure Optical Networks Based on Quantum Key Distribution and Weakly Trusted Repeaters[J]. Journal of Optical Communications & Networking, 2013,5(4):316-328. |
| [15] |
LO H K, CHAU H F. Unconditional Security of Quantum Key Distribution over Arbitrarily Long Distances[J]. Science, 1999,283(5410):2050-2056.
doi: 10.1126/science.283.5410.2050 URL pmid: 10092221 |
| [16] | WANG Yunxiao. Research on Mobile Application of Smart Grid Based on Quantum Communication Technology[EB/OL]. http://cpfd.cnki.com.cn/Article/CPFDTOTAL-GWDT201910001061.htm, 2020-2-11. |
| 王云霄. 智能电网基于量子通信技术的移动应用研究[EB/OL]. http://cpfd.cnki.com.cn/Article/CPFDTOTAL-GWDT201910001061.htm, 2020-2-11. | |
| [17] | LI Hongwei, CHEN Wei, HUANG Jingzheng, et al. Security of Quantum Key Distribution[J]. SCIENTIA SINICA Physica, Mechanica & Astronomica, 2012,42(11):1237-1255. |
| 李宏伟, 陈巍, 黄靖正, 等. 量子密码安全性研究[J]. 中国科学:物理学力学天文学, 2012,42(11):1237-1255. | |
| [18] | ZHANG Ziping, LIU Guojun, DONG Kai, et al. Key Pool Construction of Quantum Key Distribution Optical Network[J]. Laser & Optoelectronics Progress, 2019,56(21):231-237. |
| 张梓平, 刘国军, 董凯, 等. 量子密钥分发光网络密钥池构建方法[J]. 激光与光电子学进展, 2019,56(21):231-237. | |
| [19] | LIN Jingming. Development of Trng for Quantum Key Communication[D]. Harbin: Harbin Institute of Technology, 2017. |
| 林景明. 面向量子密钥通信的真随机数生成器研制[D]. 哈尔滨:哈尔滨工业大学, 2017. | |
| [20] | YANG Chao. Research on Model and Routing Technology in Wide-area Quantum Key[D]. Zhengzhou: Strategic Support Force Information Engineering University, 2018. |
| 杨超. 广域量子密钥网络模型及路由技术研究[D]. 郑州:战略支援部队信息工程大学, 2018. | |
| [21] | YUAN Cao, ZHAO Yongli, Colman Meixner Carlos, et al. Key on Demand(KoD) for Software-defined Optical Networks Secured by Quantum Key Distribution(QKD)[J]. Optics Expres, 2017,25(22):26453-26467. |
| [22] | YUAN Cao, ZHAO Yongli. Time-scheduled Quantum Key Distribution(QKD) over WDM Networks[J]. Journal of Lightwave Technology, 2018,36(16):3382-3395. |
| [23] | ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends[C]// IEEE. 2017 IEEE International Congress on Big Data(Big Data Congress), June 25-30, 2017, Honolulu, HI, USA. New York: IEEE, 2017: 557-564. |
| [24] | SZABO N. Formalizing and Securing Relationships on Public Networks[EB/OL]. http://ojphi.org/ojs/index.php/fm/article/view/548/469, 2017-4-7. |
| [1] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [2] | XU Huikai, LIU Yue, MA Zhenbang, DUAN Haixin. A Large-scale Measurement Study of MQTT Security [J]. Netinfo Security, 2020, 20(9): 37-41. |
| [3] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [4] | LI Li, ZENG Qingxian, WEN Yihong, WANG Shicheng. Data Sharing Scheme Based on the Blockchain and the Proxy Re-encryption [J]. Netinfo Security, 2020, 20(8): 16-24. |
| [5] | CHEN Lu, SUN Yajie, ZHANG Liqiang, CHEN Yun. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [6] | BIAN Lingyu, ZHANG Linlin, ZHAO Kai, SHI Fei. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [7] | MAO Zhilai, LIU Yanan, SUN Huiping, CHEN Zhong. Research on Blockchain Performance Scalability and Security [J]. Netinfo Security, 2020, 20(3): 56-64. |
| [8] | LANG Weimin, ZHANG Han, ZHAO Yifeng, YAO Jinfang. A Blockchain-based Behavior Regulation and Activities Management Scheme for Internet of Things [J]. Netinfo Security, 2020, 20(2): 22-29. |
| [9] | Jian KANG, Jie WANG, Zhengxu LI, Guangda ZHANG. A Model for Anomaly Intrusion Detection with Different Feature Extraction Strategies in IoT [J]. Netinfo Security, 2019, 19(9): 21-25. |
| [10] | Yihua ZHOU, Zhuqing LV, Yuguang YANG, Weimin SHI. Data Deposit Management System Based on Blockchain Technology [J]. Netinfo Security, 2019, 19(8): 8-14. |
| [11] | Aitong LU, Kuo ZHAO, Jingying YANG, Feng WANG. Research on Cross-chain Technology of Blockchain [J]. Netinfo Security, 2019, 19(8): 83-90. |
| [12] | Min ZHENG, Hong WANG, Hong LIU, Chong TAN. Survey on Consensus Algorithms of Blockchain [J]. Netinfo Security, 2019, 19(7): 8-24. |
| [13] | Yuanjian ZHOU, Dongmei QING, Yining LIU, Songzhan LV. Design of Electronic Warehouse Receipts System Based on Blockchain [J]. Netinfo Security, 2019, 19(6): 84-90. |
| [14] | Wenming WANG, Chongyang SHI, Yinghao WANG, Dejian WEI. Research on Transaction and Security Based on Blockchain Technology [J]. Netinfo Security, 2019, 19(5): 1-9. |
| [15] | Yiming HEI, Jianwei LIU, Zongyang ZHANG, Hui YU. Blockchain-based Distributed Cloud Storage System with Public Verification [J]. Netinfo Security, 2019, 19(3): 52-60. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||