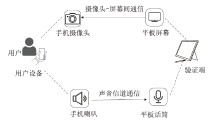
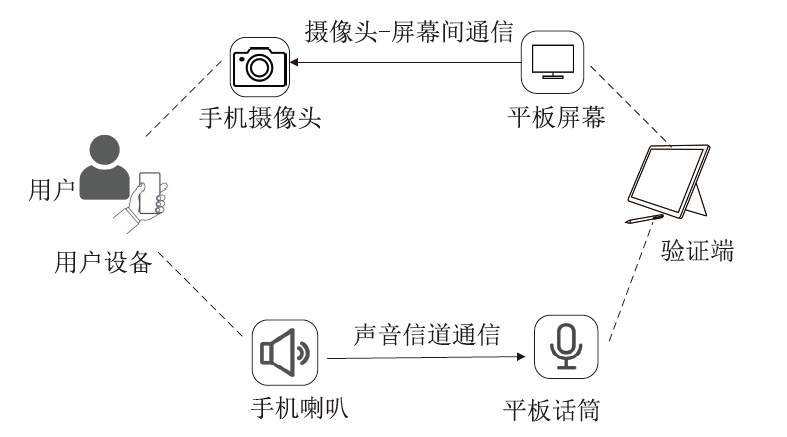
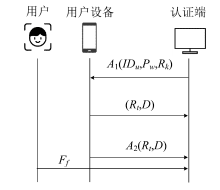
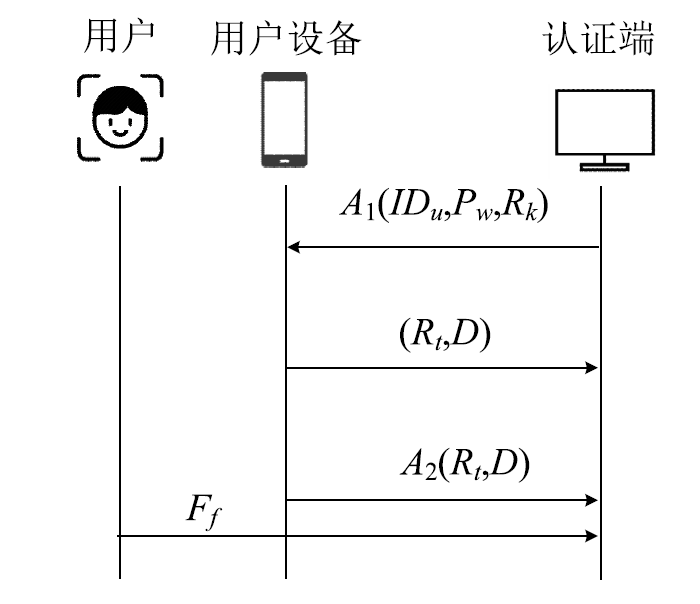
| [1] |
DENSO WAVE. What is a QR Code[EB/OL]. https://www.qrcode.com/en/about/, 2020-1-11.
|
| [2] |
YUAN Wenjia, DANA K, ASHOK A, et al. Dynamic and Invisible Messaging for Visual MIMO[C]// IEEE. 2012 IEEE Workshop on the Applications of Computer Vision(WACV), January 9-11, 2012, Breckenridge, CO, USA. New Jersey: IEEE, 2012: 345-352.
|
| [3] |
NANDAKUMAR R, CHINTALAPUDI K K, PADMANABHAN V, et al. Dhwani: Secure Peer-to-Peer Acoustic NFC[J]. ACM SIGCOMM Computer Communication Review, 2013,43(4):63-74.
doi: 10.1145/2534169.2486037
URL
|
| [4] |
LAMPORT L. Password Authentication with Insecure Communication[J]. Communications of the ACM, 1981,24(11):770-772.
|
| [5] |
GUNSON N, MARSHALL D, MORTON H, et al. User Perceptions of Security and Usability of Single-factor and Two-factor Authentication in Automated Telephone Banking[J]. Computers & Security, 2011,30(4):208-220.
|
| [6] |
NIMMY K, SANKARAN S, ACHUTHAN K. A Novel Multi-factor Authentication Protocol for Smart Home Environments[C]// Springer. International Conference on Information Systems Security, ICISS 2018, December 17-19, 2018, Bengaluru, India. New York: Springer, 2018: 44-63.
|
| [7] |
FERNANDES E, JUNG J, PRAKASH A. Security Analysis of Emerging Smart Home Applications[C]// IEEE. 2016 IEEE Symposium on Security and Privacy(SP), May 23-25, 2016, FAIRMONT, SAN JOSE, CA. New Jersey: IEEE, 2016: 636-654.
|
| [8] |
WANG Anran, LI Zhuoran, PENG Chunyi, et al. InFrame++ Achieve Simultaneous Screen-Human Viewing and Hidden Screen-Camera Communication[C]// SIGMOBILE. The 13th Annual International Conference on Mobile Systems, Applications, and Services, MobiSys’15, May 18-22, 2015, Florence, Italy. New York: Association for Computing Machinery, 2015: 181-195.
|
| [9] |
ZHANG Xiao, LIU Jiqiang, CHEN Si, et al. PriWhisper+: An Enhanced Acoustic Short-range Communication System for Smartphones[J]. IEEE Internet of Things Journal, 2018,6(1):614-627.
|
| [10] |
YU Yi, HE Jingsha, ZHU Nafei, et al. A New Method for Identity Authentication Using Mobile Terminals[EB/OL]. https://doi.org/10.1007/978-3-030-22277-2_31, 2020-1-1.
|
| [11] |
SARKAR A, SINGH B K. A Novel Session Key Generation and Secure Communication Establishment Protocol Using Fingerprint Biometrics[M]. Switzerland: Springer, Cham, 2020.
|
| [12] |
SUN Jianguo, ZHONG Qi, KOU Liang, et al. A Lightweight Multi-factor Mobile User Authentication Scheme[C]// IEEE. INFOCOM 2018-IEEE Conference on Computer Communications Workshops(INFOCOM WKSHPS), April 15-19, 2018, Honolulu, HI, USA. New Jersey: IEEE, 2018: 831-836.
|
| [13] |
BHUVANESWARI M, PARAMASIVAN B, ALDABBAS H. A Two-Level Authentication Protocol for Vehicular Adhoc Networks[C]// Springer. Intelligent Computing Paradigm and Cutting-edge Technologies: Proceedings of the First International Conference on Innovative Computing and Cutting-edge Technologies(ICICCT 2019), April 29-30, 2019, Namakkal, Tamil Nadu, India. New York: Springer, 2019: 139-147.
|
| [14] |
CHALLA S, DAS A K, ODELU V, et al. An Efficient ECC-based Provably Secure Three-factor User Authentication and Key Agreement Protocol for Wireless Healthcare Sensor Networks[EB/OL]. http://www.socolar.com/Article/Index?aid=100056319114&jid=100000003579, 2020-2-10.
|
| [15] |
CAPROLU M, SCIANCALEPORE S, DI PIETRO R, Short-range Audio Channels Security: Survey of Mechanisms, Applications,Research Challenges[EB/OL]. https://arxiv.org/abs/2001.02877, 2020-2-10.
|
| [16] |
BA Zhongjie, QIN Zhan, FU Xinwen, et al. CIM: Camera in Motion for Smartphone Authentication[J]. IEEE Transactions on Information Forensics and Security, 2019,14(11):2987-3002.
|
| [17] |
CHEN Dajiang, ZHANG Ning, QIN Zhiguang, et al. S2M: A Lightweight Acoustic Fingerprints-based Wireless Device Authentication Protocol[J]. IEEE Internet of Things Journal, 2016,4(1):88-100.
|
| [18] |
PALANISWAMY B, CAMTEPE S, FOO E, et al. Continuous Authentication for VANET[EB/OL]. https://doi.org/10.1016/j.vehcom.2020.100255, Vehicular Communications, 2020-4-16.
|
| [19] |
FENG Huan, FAWAZ K, SHIN K G. Continuous Authentication for Voice Assistants[C]// ACM. 23rd Annual International Conference on Mobile Computing and Networking, October 16-20, 2017, Snowbird, Utah, USA. New York: ACM, 2017: 343-355.
|
| [20] |
BURROWS M, ABADI M, NEEDHAM R M. A Logic of Authentication[J]. ACM Transactions on Computer System, 1990,8(1):18-36.
|