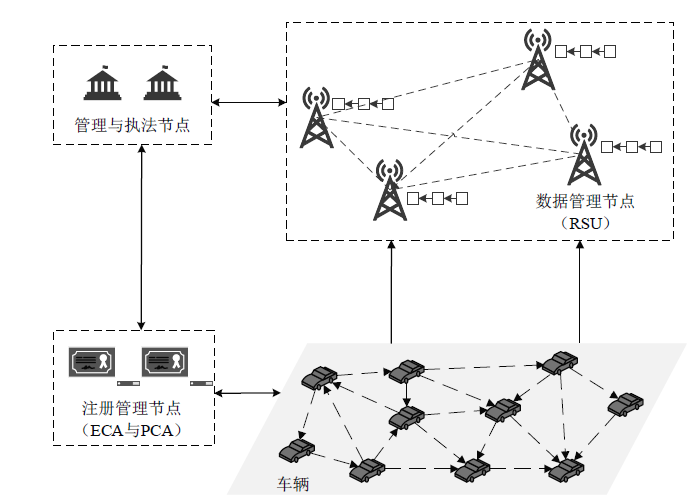
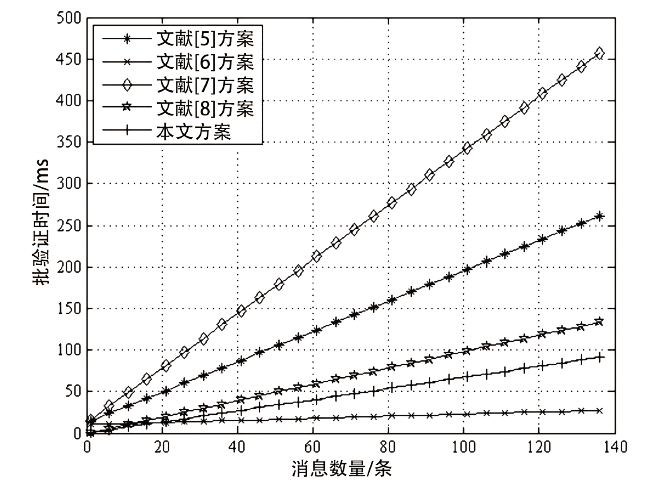
| [1] |
RAYA M, PAPADIMITRATOS P, HUBAUX J P. Securing Vehicular Networks[J]. IEEE Wireless Communication Special Issue on Inter-vehicular Communications, 2006,13(5):8-15.
|
| [2] |
LIN Xiaodong, SUN Xiaoting, HO P H, et al. GSIS: A Secure and Privacy Preserving Protocol for Vehicular Communications[J]. IEEE Trans, 2007,56(6):3442-3456.
|
| [3] |
LU Rongxing, LIN Xiaodong, ZHU Haojin, et al. ECPP: Efficient Conditional Privacy Preservation Protocol for Secure Vehicular Communications[C]// IEEE. 27th IEEE International Conference on Computer Communications, April 13-18, 2008, Phoenix, AZ, USA. New Jersey: IEEE, 2008: 1229-1237.
|
| [4] |
HUANG Dijiang, MISRA S, VERMA M. PACP: An Efficient Pseudonymous Authentication-based Conditional Privacy Protocol for VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2011,12(3):736-746.
doi: 10.1109/TITS.2011.2156790
URL
|
| [5] |
SHIM K A. CAPS: An Efficient Conditional Privacy-preserving Authentication Scheme for Vehicular Sensor Networks[J]. Vehicular Technology IEEE Transactions on, 2012,61(4):1874-1883.
doi: 10.1109/TVT.2012.2186992
URL
|
| [6] |
HORNG S J, TZENG S F, LI T, et al. Enhancing Security and Privacy for Identity-based Batch Verification Scheme in VANETs[J]. Vehicular Technology, IEEE Transactions, 2017,66(4):3235-3248.
doi: 10.1109/TVT.2015.2406877
URL
|
| [7] |
BAYAT M, BARMSHOORY M, RAHIMI M, et al. A Secure Authentication Scheme for VANETs with Batch Verification[J]. Wireless Networks, 2015,21(5):1733-1743.
doi: 10.1007/s11276-014-0881-0
URL
|
| [8] |
GAYATHRI N B, GOWRI T, VASUDEVA R P, et al. Efficient Pairing-free Certificateless Authentication Scheme with Batch Verification for Vehicular Ad-Hoc Networks[J]. IEEE Access, 2018,2(6):31808-31819.
|
| [9] |
ALANAZI F, SHAREEDA A, OZGUNER F. An Efficient Cppa Scheme for Intelligent Transportation Networks[J]. Pervasive and Mobile Computing, 2019,59(8):1-16.
|
| [10] |
GUO Song, ZENG Deze, XIANG Yang. Chameleon Hashing for Secure and Privacy-preserving Vehicular Communications[J]. Parallel & Distributed Systems IEEE Transactions on, 2014,25(11):2794-2803.
|
| [11] |
MICHELIN R A, DORRI A, LUNARDI R C, et al. SpeedyChain: A Framework for Decoupling Data from Blockchain for Smart Cities[EB/OL]. https://www.researchgate.net/publication/326222959_SpeedyChain_A_framework_for_decoupling_data_from_blockchain_for_smart_cities, 2020-05-12.
|
| [12] |
LIU J K, YUEN T H, AU M H, et al. Improvements on An Authentication Scheme for Vehicular Sensor Networks[J]. Expert Systems with Applications, 2014,41(5):2559-2564.
doi: 10.1016/j.eswa.2013.10.003
URL
|
| [13] |
POINTCHEVAL D, STERN J. Security Proofs for Signature Schemes[C]// Springer. 1996 International Conference on the Theory and Application of Cryptographic Techniques, May 12-16, 1996, Saragossa, Spain. Heidelberg: Springer, 1996: 387-398.
|
 ), ZHAO Manli1,2, CHEN Zhihao3, SHI Bo3
), ZHAO Manli1,2, CHEN Zhihao3, SHI Bo3