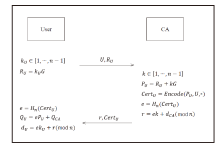
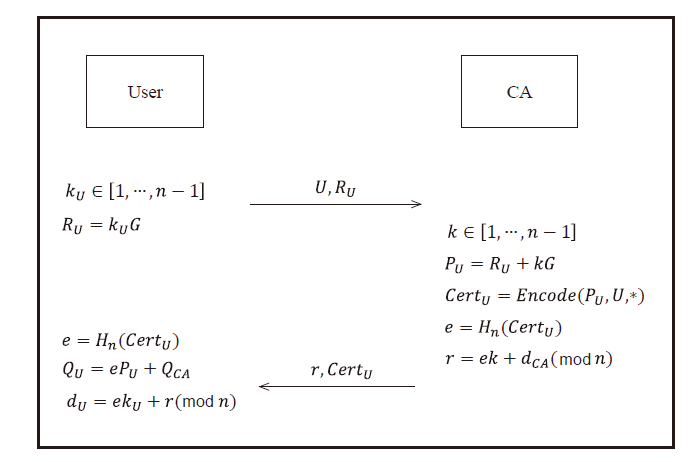
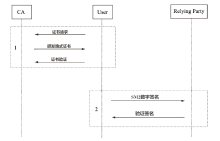
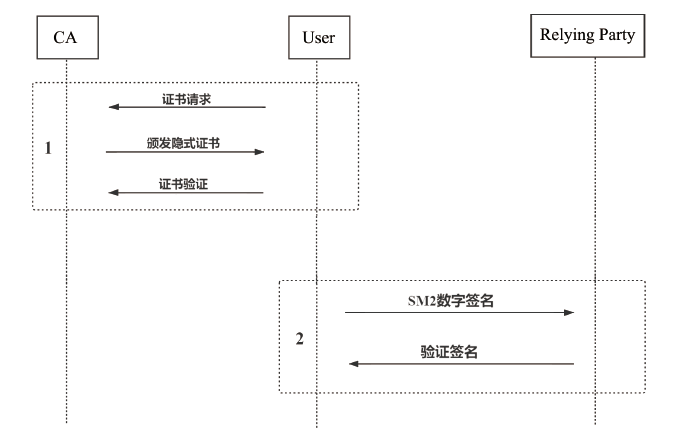
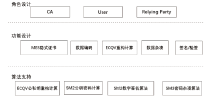
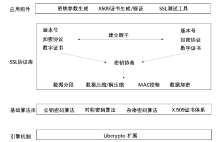
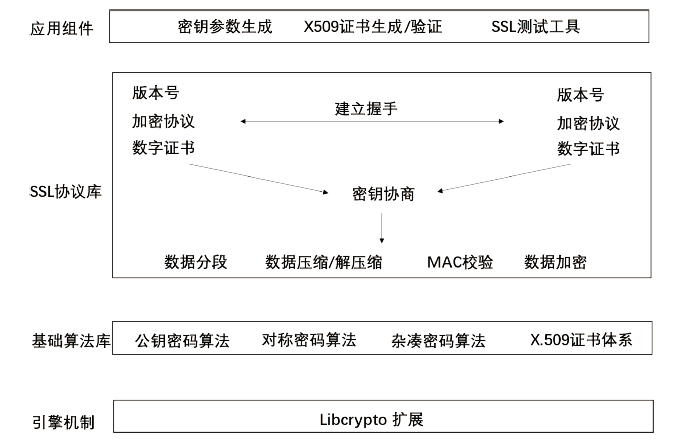
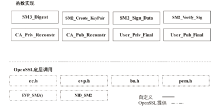
| [1] |
FARAZ I K, SUFIAN H. Understanding Security Requirements and Challenges in Internet of Things (IoT): A Review[J]. Journal of Computer Networks and Communications, 2019,19(1):14-15.
|
| [2] |
PANAGIOTIS R G, PANAGIOTIS G. Sarigiannidis, IOANNIS D. Moscholios. Securing the Internet of Things: Challenges, Threats and Solutions[J]. Internet of Things, 2019,5(3):41-70.
doi: 10.1016/j.iot.2018.11.003
URL
|
| [3] |
HA D A, NGUYEN K T, ZAO J K. Efficient Authentication of Resource-constrained IoT Devices Based on ECQV Implicit Certificates and Datagram Transport Layer Security Protocol[C]// SoICT. Proceedings of the Seventh Symposium on Information and Commun ication Technology, December 8-9, 2016, New York, USA. New York: Association for Computing Machinery, 2016: 173-179.
|
| [4] |
AKESTORIDIS D G, HARISHANKAR M, WEBER M, et al. Zigator: Analyzing the Security of Zigbee-enabled Smart Homes[C]// WiSec. Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks, July 8-10, 2020, New York, USA. New York: Association for Computing Machinery, 2020: 77-88.
|
| [5] |
WASEF A, JIANG Yixin, SHEN Xuemin. DCS: An Efficient Distributed-certificate-service Scheme for Vehicular Networks[J]. IEEE. Transactions on Vehicular Technology, 2009,59(2):533-549.
doi: 10.1109/TVT.2009.2028893
URL
|
| [6] |
VAN T, HENK C, SUSHIL J. Encyclopedia of Cryptography and Security[M]. Berlin: Springer Science & Business Media, 2014.
|
| [7] |
ERGEN S C. ZigBee/IEEE 802.15.4 Summary[J]. UC Berkeley. 2004,10(17):10-11.
|
| [8] |
U.S. Department of Transportation. Security Credential Management System[EB/OL]. https://www.its.dot.gov/resources/scms.htm, 2020-12-15.
|
| [9] |
China Industrial Development Research Institute. Industrial Internet of Things Information Security Protection Technology[EB/OL]. http://www.zfcyy.com.cn/, 2019-06-03.
|
|
中国产业发展研究院. 工业物联网信息安全防护技术[EB/OL]. http://www.zfcyy.com.cn/, 2019-06-03.
|
| [10] |
CHRISTOPH G GÜNTHER. , An Identity-based Key-exchange Protocol[EB/OL]. https://link.sprin ger.com/content/pdf/10.1007%2F3-540-46885-4_5.pdf, 2002-10-26.
|
| [11] |
BROWN DANIEL R L, GALLANT ROBERT P, VANSTONE SCOTT A. Provably Secure Implicit Certificate Schemes[C]// FC. In Proceedings of the 5th International Conference on Financial Cryptography, February 19-22, 2002, Verlag, Berlin. Heidelberg: Springer, 2002: 156-165.
|
| [12] |
RABAD I, NADER M. Anonymous Group Implicit Certificate Scheme[EB/OL]. http://citeseerx.ist.psu.edu/viewdoc/download? doi=10.1.1.32.2221&rep=rep1&type=pdf, 2020-10-26.
|
| [13] |
LI Wenhao, LI Haibo, CHEN Haibo, et al. AdAttester: Secure Online Mobile Advertisement Attestation Using Trustzone[EB/OL]. https://www.trustkernel.org/uploads/pubs/AdAttester_MobiSys15.pdf, 2015-05-01.
|
| [14] |
CAMPAGNA M. SEC 4: Elliptic Curve Qu-vanstone Implicit Certificate Scheme (ECQV)[EB/OL]. https://www.secg.org/draft-sec4-1.1.pdf, 2013-11-06.
|
| [15] |
MELNIKOV A, CHUANG W. Internationalized Email Addresses in X. 509 Certificates[EB/OL]. https://www.rfceditor.org/info/rfc8 398, 2018-05-01.
|
| [16] |
HOUSLEY R, POLK W, FORD W, et al. RFC3280: Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile[EB/OL]. https://tools.ietf.org/html/rfc3280, 2020-12-28.
|
| [17] |
GM/T0003-2012. SM2 Elliptic Curve Public Key Cryptographic Algorithm[S]. Beijing: State Cryptography Administration, 2012.
|
|
GM/T0003-2012. SM2椭圆曲线公钥密码算法[S]. 北京:国家密码管理局, 2012.
|
| [18] |
GM/T0004-2012. SM3 cryptographic hash algorithm[S]. Beijing: State Cryptography Administration, 2012.
|
|
GM/T0004-2012. SM3密码杂凑算法[S]. 北京:国家密码管理局, 2012.
|
 ), WANG Wei2
), WANG Wei2