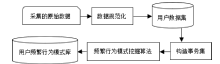
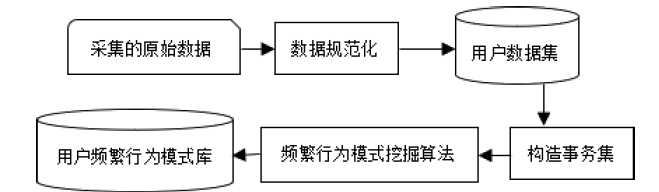
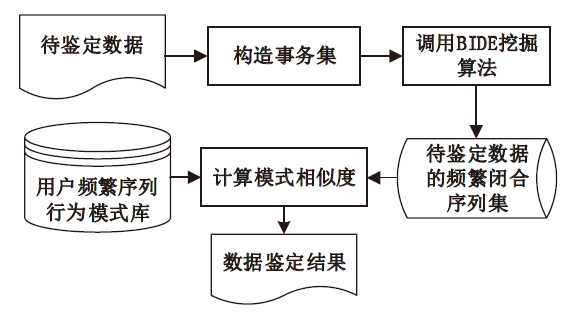
Netinfo Security ›› 2021, Vol. 21 ›› Issue (3): 44-52.doi: 10.3969/j.issn.1671-1122.2021.03.006
Previous Articles Next Articles
An Anonymous Data Authentication Method Based on User Behavior Pattern
LIU Yanhua1,2( ), LIU Zhihuang1,2
), LIU Zhihuang1,2
- 1. College of Mathematics and Computer Science, Fuzhou University, Fuzhou 350108, China
2. Fujian Provincial Key Laboratory of Network Computing and Intelligent Information Processing, Fuzhou 350108, China
-
Received:2020-10-12Online:2021-03-10Published:2021-03-16 -
Contact:LIU Yanhua E-mail:lyhwa@fzu.edu.cn
CLC Number:
Cite this article
LIU Yanhua, LIU Zhihuang. An Anonymous Data Authentication Method Based on User Behavior Pattern[J]. Netinfo Security, 2021, 21(3): 44-52.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.03.006
| 频繁闭合浏览序列行为模式 | 支持度 |
|---|---|
| 0.7 | |
| 0.6 | |
| 0.8 | |
| 0.683 | |
| 0.617 | |
| 0.85 | |
| 0.667 | |
| 0.65 | |
| 0.8 | |
| 0.6 | |
| 0.733 | |
| 0.617 |
| 频繁闭合浏览序列行为模式 | 支持度 |
|---|---|
| 0.7 | |
| 0.7833 | |
| 0.617 | |
| 0.8 | |
| 0.617 | |
| 0.617 | |
| 0.75 | |
| 0.767 | |
| 0.75 |
| 频繁闭合浏览序列行为模式 | 支持度 |
|---|---|
| 0.7 | |
| 0.75 | |
| 0.8 | |
| 0.833 | |
| 0.65 | |
| 0.65 | |
| 0.767 | |
| 0.617 | |
| 0.6 | |
| 0.733 |
| 频繁闭合浏览序列行为模式 | 支持度 |
|---|---|
| 0.8 | |
| 0.75 | |
| 0.6 | |
| 0.6 | |
| 0.7 | |
| 0.6167 | |
| 0.617 | |
| 0.833 | |
| 0.667 | |
| 0.75 | |
| 0.6 |
| 频繁闭合浏览序列行为模式 | 支持度 |
|---|---|
| 0.7 | |
| 0.8 | |
| 0.8667 | |
| 0.733 | |
| 0.667 | |
| 0.767 | |
| 0.633 | |
| 0.667 | |
| 0.767 | |
| 0.767 | |
| 0.633 | |
| 0.633 |
| 频繁闭合序列行为模式 | 支持度 |
|---|---|
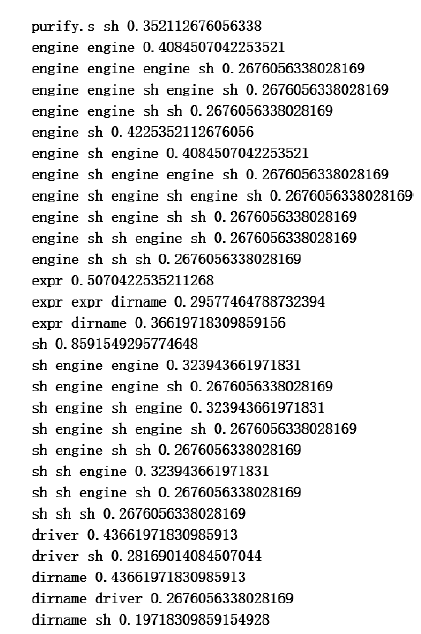
| fecc | 0.3257443082311734 |
| dirname | 0.425569176882662 |
| dirname fecc | 0.28896672504378285 |
| dirname driver | 0.22416812609457093 |
| be driver | 0.2224168126094571 |
| engine engine | 0.29947460595446584 |
| engine engine engine | 0.23992994746059546 |
| engine engine sh engine | 0.23992994746059546 |
| engine sh | 0.34851138353765326 |
| engine sh engine | 0.29947460595446584 |
| engine sh engine engine | 0.23992994746059546 |
| engine sh engine sh engine | 0.23992994746059546 |
| engine sh sh | 0.26970227670753066 |
| engine sh sh engine | 0.23992994746059546 |
| sh | 0.8108581436077058 |
| sh engine | 0.3345008756567426 |
| sh engine engine | 0.2714535901926445 |
| sh engine sh | 0.3274956217162872 |
| sh engine sh engine | 0.2714535901926445 |
| sh sh | 0.3922942206654991 |
| sh sh engine | 0.2714535901926445 |
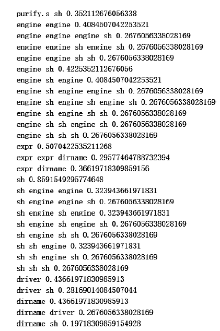
| purify.s sh | 0.36252189141856395 |
| expr | 0.4886164623467601 |
| expr expr dirname | 0.30998248686514884 |
| expr fecc | 0.23992994746059546 |
| expr dirname | 0.3712784588441331 |
| expr dirname fecc | 0.23992994746059546 |
| driver | 0.4273204903677758 |
| driver purify.s sh | 0.23467600700525393 |
| driver sh | 0.31523642732049034 |
| 测试用户 | 模式相似度结果 |
|---|---|
| TestUser1 | User1:TestUser1=0.75397 |
| User25:TestUser1=0.77365 | |
| User13:TestUser1=0.87397 | |
| TestUser2 | User2:TestUser2=2.81001 |
| User33:TestUser2=3.06237 | |
| User21:TestUser2=5.12606 | |
| TestUser3 | User42:TestUser3=0.79532 |
| User43:TestUser3=1.48108 | |
| User3:TestUser3=1.74253 | |
| TestUser4 | User4:TestUser4=2.14417 |
| User35:TestUser4=2.30406 | |
| User36:TestUser4=3.12642 | |
| TestUser5 | User5:TestUser5=0.50072 |
| User4:TestUser5=0.50144 | |
| User36:TestUser5=0.50427 | |
| User49:TestUser5=0.52199 | |
| User31:TestUser5=0.53318 | |
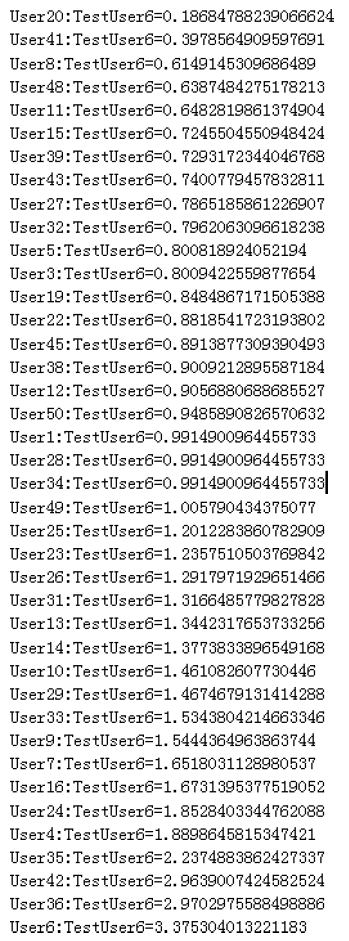
| TestUser6 | User42:TestUser6=2.96390 |
| User36:TestUser6=2.97029 | |
| User6:TestUser6=3.37530 | |
| TestUser7 | User7:TestUser7=1.04067 |
| User24:TestUser7=1.05313 | |
| User42:TestUser7=1.15876 | |
| User4:TestUser7=1.18531 | |
| User35:TestUser7=1.19581 | |
| User6:TestUser7=1.24769 | |
| User36:TestUser7=1.69913 | |
| TestUser8 | 与User1~User10的相似度均为0 |
| TestUser9 | User9:TestUser9=1.027552 |
| User24:TestUser9=1.07805 | |
| User35:TestUser9=1.18323 | |
| User4:TestUser9=1.22954 | |
| User42:TestUser9=1.25510 | |
| User6:TestUser9=1.35143 | |
| User36:TestUser9=1.62000 | |
| TestUser10 | User42:TestUser10=2.07083 |
| User6:TestUser10=2.19874 | |
| User10:TestUser10=2.23718 |
| 频繁闭合序列行为模式 | 支持度 |
|---|---|
| sh | 0.22591943957968477 |
| popper | 0.6094570928196147 |
| popper popper | 0.5569176882661997 |
| popper popper popper | 0.5166374781085814 |
| popper popper popper popper | 0.4973730297723292 |
| popper popper popper popper popper | 0.4868651488616462 |
| popper popper popper popper popper popper | 0.46935201401050786 |
| popper popper popper popper popper popper popper | 0.46409807355516636 |
| [1] | ALLIOUI Y E. Advanced Prediction of Learner's Profile Based on Felder-silverman Learning Styles Using Web Usage Mining Approach and Fuzzy c-means Algorithm[J]. International Journal of Computer Aided Engineering and Technology, 2019,11(4/5):495-512. |
| [2] | XIAO Yang. Research on Sequence Mining Algorithm and Its Application in User Behavior Analysis[D]. Beijing: Beijing University of Posts and Telecommunications, 2014. |
| 肖扬. 序列挖掘算法研究及其在用户行为分析中的应用[D]. 北京:北京邮电大学, 2014. | |
| [3] | LIU Huijun. Research on User Browsing Pattern Mining Method and Application[D]. Chongqing: Chongqing University, 2010. |
| 刘慧君. 用户浏览模式挖掘方法与应用研究[D]. 重庆:重庆大学, 2010. | |
| [4] | SHEN Qiangqiang. Research on Sequential Pattern Mining and Rule Matching Prediction Based on Improved Apriori Algorithm[D]. Beijing: Beijing University of Posts and Telecommunications, 2019. |
| 申嫱嫱. 基于改进Apriori算法的序列模式挖掘和规则匹配预测研究[D]. 北京:北京邮电大学, 2019. | |
| [5] | CHEN Jia. Design and Implementation of Closed Sequence Pattern Mobile Phone Virus Mining System Based on Spark[D]. Beijing: Beijing University of Posts and Telecommunications, 2019. |
| 陈佳. 基于Spark的闭合序列模式手机病毒挖掘系统的设计与实现[D]. 北京:北京邮电大学, 2019. | |
| [6] |
PIMUS I, PELEG M, SCHERTZ M. Sequence Mining of Comorbid Neurodevelopmental Disorders Using the SPADE Algorithm[J]. Methods of Information in Medicine, 2016,55(3):223-233.
doi: 10.3414/ME15-01-0142 URL pmid: 26848079 |
| [7] | LI Libo, BAI Shuren, CHEN Lei, et al. Mining Probabilistically Frequent Closed Sequential Patterns in Uncertain Databases[J]. Application Research of Computers, 2016,33(4):983-988. |
| 李立波, 白树仁, 陈磊, 等. 基于不确定数据的可能频繁闭序列模式挖掘[J]. 计算机应用研究, 2016,33(4):983-988. | |
| [8] | WANG Kechao, WANG Tiantian, SU Xiaohong, et al. Plagiarism Detection in Student Programs Based on Frequent Closed Sequence Mining[J]. Journal of Jilin University, 2015,45(4):1260-1265. |
| 王克朝, 王甜甜, 苏小红, 等. 基于频繁闭合序列模式挖掘的学生程序雷同检测[J]. 吉林大学学报, 2015,45(4):1260-1265. | |
| [9] | ZHANG Hongze, HONG Zheng, WANG Chen, et al. Unknown Protocol Format Inference Method Based on Closed Sequence Pattern Mining[J]. Computer Science, 2019,46(6):80-89. |
| 张洪泽, 洪征, 王辰, 等. 基于闭合序列模式挖掘的未知协议格式推断方法[J]. 计算机科学, 2019,46(6):80-89. | |
| [10] | ABBASI A, CHEN H. Writeprints: A Stylometric Approach to Identity-level Identification and Similarity Detection in Cyberspace[J]. ACM Transactions on Information Systems, 2008,26(2):67-96. |
| [11] | SONG Hongzheng. Research and Implementation of E-mail Classification Algorithm Based on User Behavior and Content[D]. Chengdu: University of Electronic Science and Technology of China, 2016. |
| 宋洪正. 基于用户行为关系和内容的邮件分类算法的研究与实现[D]. 成都:电子科技大学, 2016. | |
| [12] | NIZAMANI S, MEMON N. CEAI: CCM-based Email Authorship Identification Model[J]. Egyptian Informatics Journal, 2013,14(3):239-249. |
| [13] | NIZAMANI S, MEMON N, WIIL U K, et al. Modeling Suspicious Email Detection Using Enhanced Feature Selection[J]. International Journal of Modeling & Optimization, 2012,2(4):371-377. |
| [1] | ZHANG Xuan, YUAN Deyu, JIN Bo. Virtual Identity Identification Based on Semantic for Network Trading Platform [J]. Netinfo Security, 2020, 20(12): 47-53. |
| [2] | Hong CHEN, Yue XIAO, Chenglong XIAO, Jianhu CHEN. The Intrusion Detection Method of SMOTE Algorithm with Maximum Dissimilarity Coefficient Density [J]. Netinfo Security, 2019, 19(3): 61-71. |
| [3] | Hao LIU, Zhigang CHEN, Lianming ZHANG. A Secure Routing Algorithm of Mobile Social Network Based on Community [J]. Netinfo Security, 2017, 17(7): 25-31. |
| [4] | Zhenfei ZHOU, Binxing FANG, Xiang CUI, Qixu LIU. A Method of Malicious Code Detection in WordPress Theme Based on Similarity Analysis [J]. Netinfo Security, 2017, 17(12): 47-53. |
| [5] | Yang PEI, Xuexin QU, Xiaobo GUO, Dingyang DUAN. User Attribute Completion Attack in Social Networks Based on Node2vec [J]. Netinfo Security, 2017, 17(12): 67-72. |
| [6] | Dunhao ZHONG, Dongmei ZHANG, Yu ZHANG. A Method of Intrusion Detection in Wireless Sensor Network Based on Similarity Algorithm [J]. Netinfo Security, 2016, 16(2): 22-27. |
| [7] | Wei XU, Bo-gang LIN, Si-juan LIN, Yang YANG. Research on Community Detection Method for Social Networks Based on User Interaction and Similarity [J]. Netinfo Security, 2015, 15(7): 77-83. |
| [8] | Xu WU, Fang-yu GUO, Xia-qing XIE, Jin XU. A Text Similarity Evaluation Algorithm for Structured Data of Institutional Repository [J]. Netinfo Security, 2015, 15(5): 16-20. |
| [9] | Hua CHAI, Jian-yi LIU. Research on Improved Slope One Recommendation Algorithm [J]. Netinfo Security, 2015, 15(2): 77-81. |
| [10] | Si-juan LIN, Bo-gang LIN, Wei XU, Yang YANG. Research on Microblog Hot Topic Detection Method Based on Term Energy Change [J]. Netinfo Security, 2015, 15(10): 46-52. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||