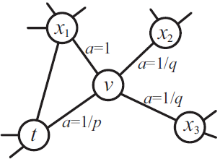
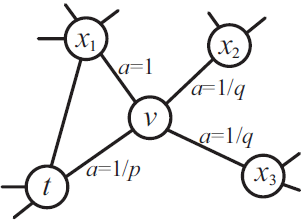
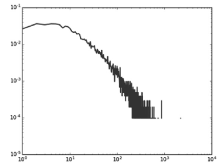
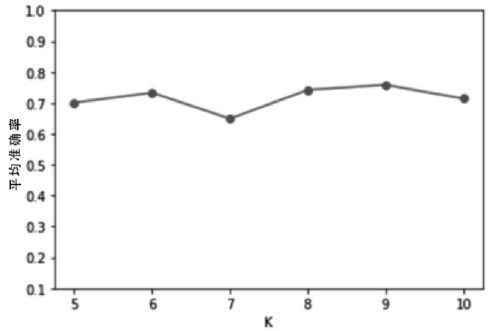
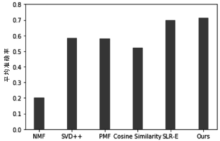
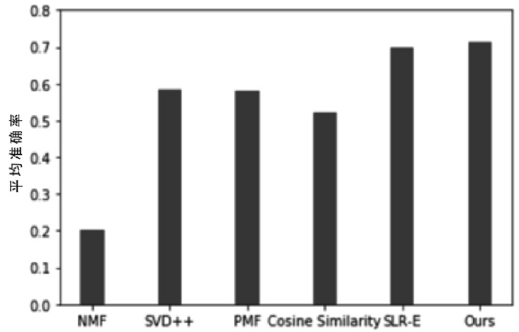
| [1] |
秦锐. 中国社交网络的兴起与发展[J]. 赤峰学院学报:自然科学版,2016(17):267-268.
|
| [2] |
温俊伟. 面向Twitter的分析系统研究[J]. 信息网络安全,2016(9):234-239.
|
| [3] |
冯泽奇. 大数据时代网络隐私问题研究:从权利保护到个人选择[D].长春:吉林大学,2016.
|
| [4] |
刘奇飞. 基于兴趣的微博用户关系分析原型系统研究[J]. 信息网络安全,2016(9):240-245.
|
| [5] |
RAO D,YAROWSKY D.Classifying Latent User Attributes in Twitter[C]//ACM.Association for Computing Machinery,October 30 , 2010,Toronto,Canada .New York: ACM,2010:37-44.
|
| [6] |
MISLOVE A,VISWANATH B,GUMMANDI K P.You Are Who You Know : Inferring User Profiles in Online Social Networks[C]// ACM.Association for Computing Machinery,February 4 - 6, 2010, New York, USA. New York: ACM ,2010:251-260.
|
| [7] |
COSCIA M,ROSSETI G,GIANNOTTI F.DEMON: A Localfirst Discovery Method for Overlapping Communities[C]// ACM .18th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining,August 12-16,Beijing,China. New York: ACM,2012:615–623.
|
| [8] |
PETER D H, ADRIAN E R, MARK. S H.Latent Space Approaches to Social Network Analysis[J].American Statistical Association, 2002,97(460):1090-1098.
|
| [9] |
GROVER A, LESKOVEC J.Node2vec: Scalable Feature Learning for Networks[C]// ACM.Association for Computing Machinery,ACM SIGKDD International Conference,August 13-17, 2016, San Francisco, California ,USA.New York:ACM, 2016:855-864.
|
| [10] |
李乐, 章毓晋. 非负矩阵分解算法综述[J]. 电子学报, 2008, 36(4):737-743.
|
| [11] |
EGGERT J, KORNER E.Sparse Coding and NMF[C]// IEEE .IEEE International Joint Conference on Neural Networks, 2004,July 25-29 ,2004 ,Budapest, Hungary . New York:IEEE, 2004:2529-2533.
|
| [12] |
JIA Y, ZHANG C, LU Q.Users' Brands Preference Based on SVD++ in Recommender Systems[C]// IEEE .IEEE Workshop on Advanced Research and Technology in Industry Applications,September 29-30 ,2014 ,Ottawa, ON, Canada . New York:IEEE, 2014:1175-1178.
|
| [13] |
CAO J, HU H, LUO T. Distributed Design and Implementation of SVD++ Algorithm for E-commerce Personalized Recommender System[EB/OL]. .
|
| [14] |
KUMAR R, KUMAR V B, SUNDER R S.Social Popularity Based SVD++ Recommender System[J]. International Journal of Computer Applications, 2014, 87(14):33-37.
|
| [15] |
LIAO L, HO Q, JIANG J.SLR: A Scalable Latent Role Model for Attribute Completion and Tie Prediction in Social Networks[C]// IEEE, International Conference on Data Engineering,May 16-20, 2016,Helsinki, Finland. New York:IEEE, 2016:1062-1073.
|
| [16] |
YIN X,WU B,LIN X.A Unified Framework for Predicting Attributes and Links in Social Networks[C]//IEEE International Conference on Big Data, December 23,2013,Silicon Valley, CA, USA. New York: IEEE,2013:153-160.
|
| [17] |
丁宇新,肖骁,吴美晶,等. 基于半监督学习的社交网络用户属性预测[J]. 通信学报,2014,(8):15-22.
|
| [18] |
王锐,吴玲玲,石川,等. 基于社团结构的链接预测和属性推断联合解决方法[J]. 电子学报,2016,(9):2062-2067.
|
| [19] |
徐丽萍,郝文江. 美国政企网络威胁情报现状及对我国的启示[J]. 信息网络安全,2016(9):278-284.
|