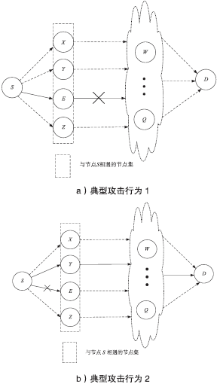
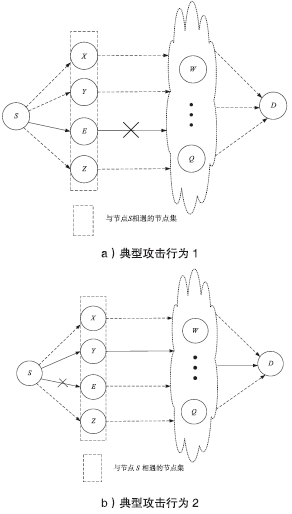
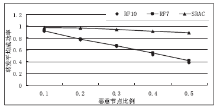
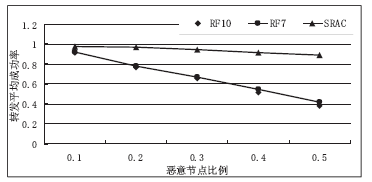
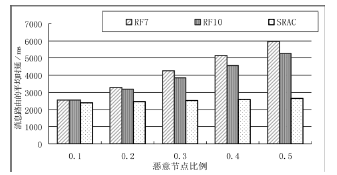
| [1] |
陆佃杰,张桂娟,郑向伟,等.移动Ad Hoc社交网络中的安全连通性分析[J].中国科学:信息科学,2015,45(1):97-110.
|
| [2] |
LIANG X H,LI X D,SHEN X S.Enabling Trustworthy Service Evaluation in Service Oriented Mobile Social Networks[J].IEEE Trans on Parallel and Distributed Systems,2014,25(2) : 310-320.
|
| [3] |
张涛,马建峰,习宁,等.面向服务移动社交网络中基于信任的分布式服务组合方法[J].电子学报, 2016,44(2):258-267.
|
| [4] |
张少波, MD Z A B,刘琴,等.移动社交网络中基于代理转发机制的轨迹隐私保护方法[J].电子与信息学报,2016,38(9): 2158-2164.
|
| [5] |
GUO B, ZHANG D Q, WANG Z, et al.Opportun-istic IoT: Exploring the Harmonious Interaction between Human and the Internet of Things[J]. Journal of Network and Computer Applications, 2013, 36(6): 1531-1539.
|
| [6] |
RESTA G, SANTI G.A Framework for Routing Performance Analysis in Delay Tolerant Networks with Application to non Cooperative Networks[J].IEEE Transac-tions on Parallel and Distributed Systems, 2011,23(1):2-10
|
| [7] |
彭颖,王淖,王高才,等.移动社交网络中基于社区的最优能效路由策略研究[J].通信学报, 2017, 38(5):128-144.
|
| [8] |
AMIN V, DAVID B.Epidemic routing for partially con-nected ad hoc networks . technical report, CS-2000-06[R]. Durham,North Carolina: Duke University, 2000: 1-16.
|
| [9] |
LINDGREN A, DORIA A, SCHELÉN O. Probabilistic Routing in Intermittently Connected Networks[J]. Lecture Notes in Computer Science, 2004, 3126(1): 252-259.
|
| [10] |
SHAGHAGHIAN S, COATES M.Optimal Forwarding in Opportunistic Delay Tolerant Networks with Meeting Rate Estimations[J]. IEEE Transactions on Signal and Information Processing over Networks, 2015, 1(2): 104-116.
|
| [11] |
SAHA B K, MISRA S, PAL S.Utility-based Exploration for Performance Enhancement in Opportunistic Mobile Networks[J]. IEEE Transactions on Computers, 2016, 65(4): 1310-1322.
|
| [12] |
李佳慧,王兴伟,李婕,等.基于社区移动社交网络的组播路由机制[J].华中科技大学学报(自然科学版), 2016, 44(S1):167-171.
|
| [13] |
张辉,王伟,郭栋. 一种基于微服务范式的桌面云构建框架[J]. 信息网络安全,2017(2):35-42.
|
| [14] |
李陟,张宏,刘凤玉.一种基于好友簇的社交网络中的时延容忍路由协议[J].计算机科学, 2012, 39(2):26-28.
|
| [15] |
刘期烈,胡春凤,朱德利,等.机会网络节点兴趣社区检测及路由策略[J].北京邮电大学学报, 2014, 37(3):62-66.
|
| [16] |
王博, 陈训逊. ad hoc网络中一种基于信任模型的机会路由算法[J].通信学报, 2013(9):92-104.
|
| [17] |
田俊峰,杜瑞忠,蔡红云. 可信计算与信任管理[M].北京: 科学出版社, 2014.
|
| [18] |
何金平,高全,施玉群.基于云模型的大坝安全多层次综合评价方法[J].系统工程理论与实践,2016,36(11):2977-2983.
|
| [19] |
李晴,叶阿勇,许力. 社交网络中基于定位欺骗的隐私攻击研究[J]. 信息网络安全,2017(5):51-56.
|
| [20] |
肖云鹏,姚豪豪,刘宴兵.一种基于云模型的WSNs节点信誉安全方案[J].电子学报, 2016, 44(1):168-175.
|
 ), Zhigang CHEN1, Lianming ZHANG3
), Zhigang CHEN1, Lianming ZHANG3