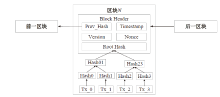
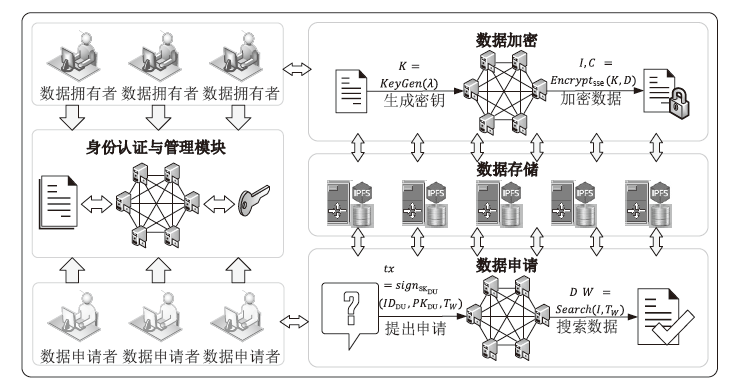
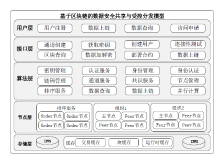
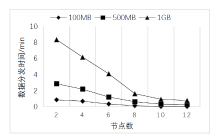
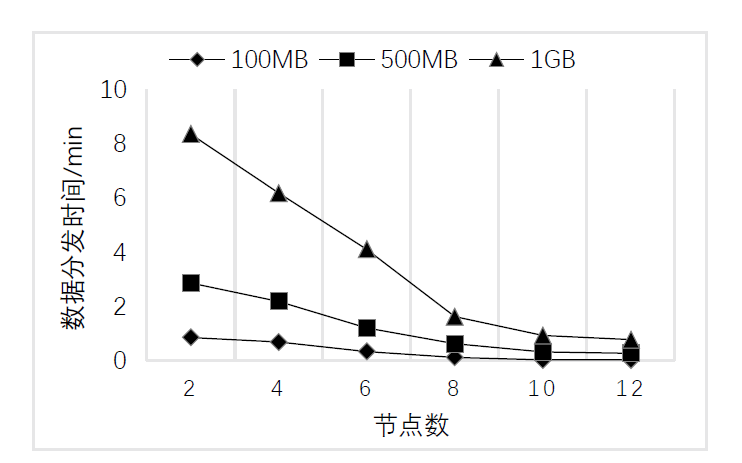
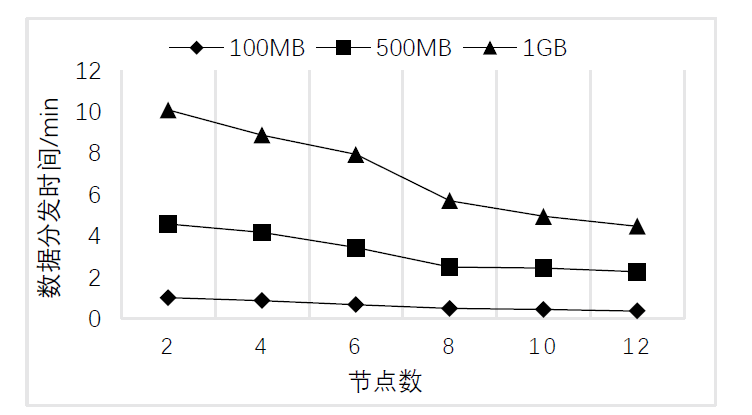
Netinfo Security ›› 2022, Vol. 22 ›› Issue (2): 55-63.doi: 10.3969/j.issn.1671-1122.2022.02.007
Previous Articles Next Articles
Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain
HOU Yutong, MA Zhaofeng( ), LUO Shoushan
), LUO Shoushan
- The School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing 100876, China
-
Received:2021-07-01Online:2022-02-10Published:2022-02-16 -
Contact:MA Zhaofeng E-mail:mzf@bupt.edu.cn
CLC Number:
Cite this article
HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain[J]. Netinfo Security, 2022, 22(2): 55-63.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.02.007
| 分类 | 字段 | 含义 | 值 |
|---|---|---|---|
| 区块 信息 | CurrentBlockHash | 区块哈希 | 1b5486745b2ddb82e9598574b9945f0dd7753a1c36f2944579d1c9632bb78590 |
| Peer | 上链节点 | peer0.org2.example.com | |
| BlockNumber | 区块高度 | 90 | |
| PreviousBlockHash | 前一区块 哈希 | 5144e8ca96387e19baf5bb85a0d9afd7ba950528c4301732371a849f7a5520e9 | |
| DataHash | 数据哈希 | ae58673b000393ff47d9b8889db5e6612e8d83aff59e11ff15f14096419ef09e | |
| TransactionCount | 交易数量 | 1 | |
| 交易 信息 | ChannelName | 通道名 | bupt |
| Payload | 交易内容 | [{"field1":"环境保护","field2":"+FHvcooP/yPPHxi06q6FMg==","field3":"2021-3-8","field4":"t4Nqt5825y5FRNRCE++eUw==","field5":"中国","field6":"PC端","field7":"环境保护","field8":"环境保护","dataHash":"45956d339a45f7003182663e56d85b559e8c024fc278b3aa92097d92e249fada"} ] | |
| TimeStamp | 时间戳 | 2021/03/08 11:21:02 | |
| TransactionID | 交易ID | 6ac91ff901b715d1591d888c898756e4b22a355978765aec64a953783c30c237 |
| 分类 | 字段 | 含义 | 值 |
|---|---|---|---|
| 区块信息 | CurrentBlockHash | 区块哈希 | c812d1fd38276dbb24475755075e7fed240895cb78320b069e427a55810e0a8d |
| Peer | 上链节点 | peer0.org2.example.com | |
| BlockNumber | 区块高度 | 91 | |
| PreviousBlockHash | 前一区块哈希 | 1b5486745b2ddb82e9598574b9945f0dd7753a1c36f2944579d1c9632bb78590 | |
| DataHash | 数据哈希 | 99b876aa82952a45954ef850d95d3a0d94b4aa897c512931282d4d25a407cd33 | |
| TransactionCount | 交易数量 | 4 | |
| 交易信息 | ChannelName | 通道名 | bupt |
| Payload | 交易内容 | "Name":”环境保护", "Size":”393.2MB", "Category":”数据共享测试", "HostIP":”192.168.1.106", "DownloadSpeed":”1.7MB", "UploadSpeed":”0B", "SourceIP":”252.85.53.133 | 37.66.94.1 | 27.54.83.229 | 116.33.172.225 | 149.102.206.151" | |
| TimeStamp | 时间戳 | 2021/03/08 11:25:08 | |
| TransactionID | 交易ID | cadadadb56e76faebd77c9083384ff68d732c48fb4c69081fe41ab63cf715b19 |
| [1] | LIU Mingda, CHEN Zuoling, SHI Yijuan, et al. Research Progress of Blockchain in Data Security[J] Chinese Journal of computers, 2021, 44(1):1-27. |
| 刘明达, 陈左宁, 拾以娟, 等. 区块链在数据安全领域的研究进展[J]. 计算机学报, 2021, 44(1):1-27. | |
| [2] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. https://bitcoin.org/bitcoin.pdf,https://bitcoin.org/bitcoin.pdf, 2021-06-12. |
| [3] | ZHANG Jian. Blockchain: Defining the New Pattern of Finance and Economy in the Future[M] Beijing: China Machine Press, 2016. |
| 张健. 区块链:定义未来金融与经济新格局[M]. 北京: 机械工业出版社, 2016. | |
| [4] |
SHEN Jian, ZHOU Tianqi, HE Debiao, et al. Block Design-based Key Agreement for Group Data Sharing in Cloud Computing[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 16(6):996-1010.
doi: 10.1109/TDSC.8858 URL |
| [5] | YANG Ruijun, HU Jinbo, CHENG Yan. Design of Data Sharing Module Based on Medical Block Chain[C]//IEEE. 2019 4th International Conference on Intelligent Informatics and Biomedical Sciences (ICIIBMS), November 21-24, 2019, Shanghai, China. New York: Springer, 2020: 149-152. |
| [6] | LIU Yansong, XIA Qi, LI Zhu, et al. Research on Data Security Sharing System on the Chain Based on Blockchain[J]. Big Data Research, 2020, 6(5):92-105. |
| 刘彦松, 夏琦, 李柱, 等. 基于区块链的链上数据安全共享体系研究[J]. 大数据, 2020, 6(5):92-105. | |
| [7] | SHRESTHA AK, VASSILEVA J. User Data Sharing Frameworks: A Blockchain-based Incentive Solution[C]// IEEE. 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), October 17-19, 2019, Columbia, CANADA. New York: IEEE, 2019: 360-366. |
| [8] | LIANG Yanli, LING Jie. Encrypted Data Sharing Scheme in Cloud Storage Based on Blockchain[J]. Computer Engineering and Applications, 2020, 56(17):41-47. |
| 梁艳丽, 凌捷. 基于区块链的云存储加密数据共享方案[J]. 计算机工程与应用, 2020, 56(17):41-47. | |
| [9] |
DOKU R, RAWAT D B, LIU Chunmei. On the Blockchain-based Decentralized Data Sharing for Event Based Encryption to Combat Adversarial Attacks[J]. IEEE Transactions on Network Science and Engineering, 2021, 8(2):1033-1043.
doi: 10.1109/TNSE.2020.2987919 URL |
| [10] |
YANG Xiaojing, LIU Jinshan, LI Xiaohe. Research and Analysis of Blockchain Data[J]. Journal of Physics: Conference Series, 2019, 1237(2):22084-22091.
doi: 10.1088/1742-6596/1237/2/022084 URL |
| [11] |
REN Wei, SUN Yan, LUO Hong, et al. SILedger: A Blockchain and ABE-based Access Control for Applications in SDN-IoT Networks[J]. IEEE Transactions on Network and Service Management, 2021, 18(4):4406-4419.
doi: 10.1109/TNSM.2021.3093002 URL |
| [12] | ZHANG Zhao, TIAN Jixin, JIN Cheqing. On-chain Witness and Off-chain Transmission Trustworthy Data Sharing Platform[J]. Big Data Research, 2020, 6(5):106-117. |
| 张召, 田继鑫, 金澈清. 链上存证、链下传输的可信数据共享平台[J]. 大数据, 2020, 6(5):106-117. | |
| [13] | LIU Wei, LI Yang, TIAN Zhao, et al. IDDS: Double-chain Structure Infectious Disease Data Sharing Blockchain Model[J]. Application Research of Computers, 2021, 38(3):675-679. |
| 刘炜, 李阳, 田钊, 等. IDDS:一种双链结构传染病数据共享区块链模型[J]. 计算机应用研究, 2021, 38(3):675-679. | |
| [14] | HU Shengshan, CAI Chengjun, WANG Qian, et al. Searching an Encrypted Cloud Meets Blockchain: A Decentralized, Reliable and Fair Realization[C]//IEEE. IEEE INFOCOM 2018-IEEE Conference on Computer Communications, April 16-19, 2018, Honolulu, HI, USA. New York: IEEE, 2018: 792-800. |
| [15] |
ZHANG Aiqing, LIN Xiaodong. Towards Secure and Privacy-preserving Data Sharing in E-health Systems via Consortium Blockchain[J]. Journal of Medical Systems, 2018, 42(8):140-148.
doi: 10.1007/s10916-018-0995-5 pmid: 29956061 |
| [16] | GUO Naiwang, NI Weidong. Privacy Protection Data Sharing Based on Blockchain[J]. Communications Technology, 2019, 52(8):1982-1986 |
| 郭乃网, 倪玮栋. 基于区块链的隐私保护数据共享[J]. 通信技术, 2019, 52(8):1982-1986. | |
| [17] | SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]//IEEE. Proceeding 2000 IEEE Symposium on Security and Privacy, May 14-17, 2000, Berkeley, CA, USA. New York: IEEE, 2002: 44-55. |
| [18] | LI Jingwei, JIA Chunfu, LIU Zheli, et al. Survey on the Searchable Encryption[J]. Journal of Software, 2015, 26(1):109-128. |
| 李经纬, 贾春福, 刘哲理, 等. 可搜索加密技术研究综述[J]. 软件学报, 2015, 26(1):109-128. | |
| [19] |
MA Zhaofeng, WANG Xiaochang, JAIN D K, et al. A Blockchain-based Trusted Data Management Scheme in Edge Computing[J]. IEEE Transactions on Industrial Informatics, 2020, 16(3):2013-2021.
doi: 10.1109/TII.9424 URL |
| [20] |
MA Zhaofeng, WANG Lingyun, WANG Xiaochang, et al. Blockchain-enabled Decentralized Trust Management and Secure Usage Control of IoT Big Data[J]. IEEE Internet of Things Journal, 2020, 7(5):4000-4015.
doi: 10.1109/JIoT.6488907 URL |
| [21] |
MA Zhaofeng, MENG Jialin, WANG Jihui, et al. Blockchain-based Decentralized Authentication Modeling Scheme in Edge and IoT Environment[J]. IEEE Internet of Things Journal, 2021, 8(4):2116-2123.
doi: 10.1109/JIoT.6488907 URL |
| [22] |
MA Zhaofeng, WANG Lingyun, ZHAO Weizhe. Blockchain-driven Trusted Data Sharing with Privacy-protection in IoT Sensor Network[J]. IEEE Sensors Journal, 2021, 21(22):25472-25479.
doi: 10.1109/JSEN.2020.3046752 URL |
| [1] | WANG Jian, ZHANG Yunjia, LIU Jiqiang, CHEN Zhihao. Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage [J]. Netinfo Security, 2022, 22(2): 21-31. |
| [2] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [3] | SUN Li. Research and Application of Information Protection Mechanism for Online Education Resource Alliance [J]. Netinfo Security, 2021, 21(9): 32-39. |
| [4] | CHEN Kaijie, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Formal Analysis Method of PoS Consensus Protocol Based on Byzantine Fault Tolerance [J]. Netinfo Security, 2021, 21(8): 35-42. |
| [5] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [6] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [7] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| [8] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [9] | ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme [J]. Netinfo Security, 2021, 21(5): 19-30. |
| [10] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [11] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [12] | ZHANG Yinghui, ZHU Tian, ZHENG Dong. Multi-keyword Fine-grained Searchable Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2021, 21(2): 34-44. |
| [13] | WANG Jian, YU Hang, HAN Zhen, HAN Lei. Access Control Methods of Data Sharing in Cloud Storage Based on Smart Contract [J]. Netinfo Security, 2021, 21(11): 40-47. |
| [14] | LI Kunchang, SHI Runhua, LI En. Survey on Data Aggregation and Privacy Protection of User Query in Smart Grid [J]. Netinfo Security, 2021, 21(11): 65-74. |
| [15] | YU Kechen, GUO Li, YAO Mengmeng. Design of Blockchain-based High-value Data Sharing System [J]. Netinfo Security, 2021, 21(11): 75-84. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||