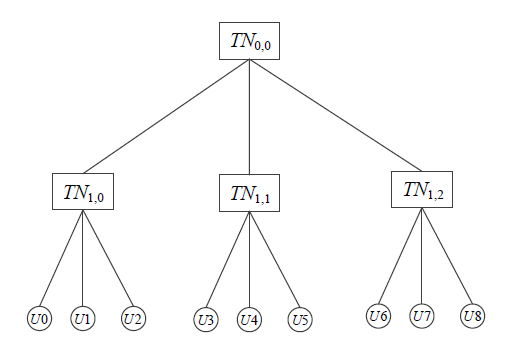
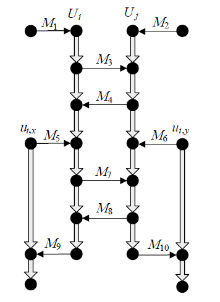
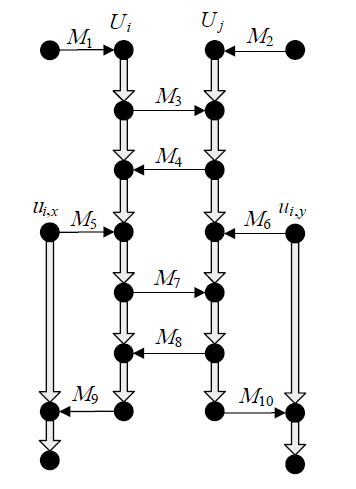
| [1] |
ZHANG Jiani, HE Debiao, LI Li. Blockchain-Based Key Agreement Protocol for Internet of Things[J]. ZTE Technology Journal, 2018, 24(6): 27-31.
|
|
张佳妮, 何德彪, 李莉. 基于区块链的物联网密钥协商协议[J]. 中兴通讯技术, 2018, 24(6): 27-31.
|
| [2] |
XIE Tao, TENG Jikai. Traitor Traceability of Asymmetric Group Key Agreement[J]. Communications Technology, 2019, 52(5): 1210-1213.
|
|
谢涛, 滕济凯. 非对称群组密钥交换协议的叛逆追踪性[J]. 通信技术, 2019, 52(5): 1210-1213.
|
| [3] |
TENG Jikai, WU Chuankun. A Collusion Attack on Asymmetric Group Key Exchange[J]. Security and Communication Networks, 2015, 8(13): 2189-2193.
doi: 10.1002/sec.1163
URL
|
| [4] |
ZHANG Lei, WU Qianhong, QIN Bo, et al. Identity-Based Authenticated Asymmetric Group Key Agreement Protocol[C]// Springer. Proceedings of COCOON 2010. Berlin: Springer, 2010: 510-519.
|
| [5] |
SHAN Chun, HU Kangwen, XUE Jingfeng, et al. Improved Pairing-Free Constant Round Certificateless Authenticated Group Key Agreement Protocol[J]. Journal of Tsinghua University(Science and Technology), 2017, 57(6): 581-585.
|
|
单纯, 胡康文, 薛静锋, 等. 改进的无线性对固定轮数无证书群组密钥协商协议[J]. 清华大学学报(自然科学版), 2017, 57(6): 581-585.
|
| [6] |
ZHANG Qikun, GAN Yong, WANG Ruifang, et al. Inter-Cluster Asymmetric Group Key Agreement[J]. Journal of Computer Research and Development, 2018, 55(12): 69-81.
|
|
张启坤, 甘勇, 王锐芳, 等. 簇间非对称群组密钥协商协议[J]. 计算机研究与发展, 2018, 55(12): 69-81.
|
| [7] |
ZHANG Zijian, ZHOU Qi, ZHANG Chuan, et al. New Low-Earth Orbit Satellites Authentication and Group Key Agreement Protocol[J]. Journal on Communications, 2018, 39(6): 146-153.
|
|
张子剑, 周琪, 张川, 等. 新的低轨星座组网认证与群组密钥协商协议[J]. 通信学报, 2018, 39(6): 146-153.
|
| [8] |
WEI Yongshuang, CHEN Jianhua, WEI Yongmei. Security Authentication Protocol for RFID/NFC Based on Elliptic Curve Cryptography[J]. Netinfo Security, 2019, 12(12): 68-70.
|
|
韦永霜, 陈建华, 韦永美. 基于椭圆曲线密码的RFID/NFC安全认证协议[J]. 信息网络安全, 2019, 12(12): 68-70.
|
| [9] |
YAO Mengmeng, TANG Li, LING Yongxing, et al. Formal Analysis of Security Protocol Based on Strand Space[J]. Netinfo Security, 2020, 20(1): 30-36.
|
|
姚萌萌, 唐黎, 凌永兴, 等. 基于串空间的安全协议形式化分析研究[J]. 信息网络安全, 2020, 20(1): 30-36.
|
| [10] |
YAO Mengmeng, ZHU Ye, TANG Li. Research on Formal Analysis Method of Computational Soundness Based on Strand Space[C]// ACM. Proceeding of ICMAI 2019. New York: ACM, 2019: 141-145.
|
| [11] |
FABREGA F J T, HERZOG J C, GUTTMAN J D. Strand S&Paces: Why is a Security Protocol Correct?[C]// IEEE. Proceedings of the 1998 IEEE Symposium on Security and Privacy. New York: IEEE, 1998: 160-171.
|
| [12] |
YANG Haomiao, SUN Shixin, LI Hongwei. Research on Bilinear Diffie-Hellman Problem[J]. Journal of Sichuan University, 2006, 38(2): 137-140.
|
|
杨浩淼, 孙世新, 李洪伟. 双线性Diffie-Hellman问题研究[J]. 四川大学学报:工程科学版, 2006, 38(2): 137-140.
|