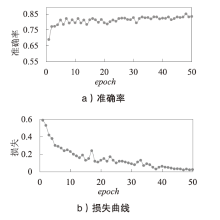
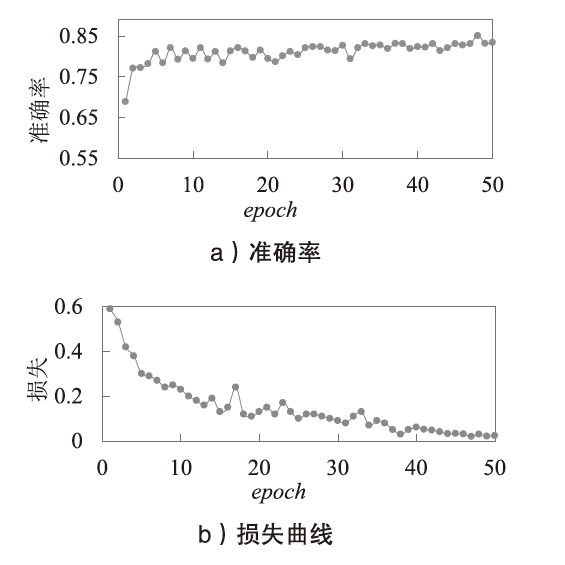
| [1] |
SCHOLLMEIER R. A Definition of Peer-to-Peer Networking for the Classification of Peer-to-Peer Architectures and Applications[C]//IEEE. 1st International Conference on Peer-to-Peer Computing. New York: IEEE, 2001: 101-102.
|
| [2] |
SlowMist. The Total Amount of Money Lost[EB/OL]. (2021-07-05) [2021-08-05]. https://hacked.slowmist.io/?c=ETH%20DApp.
|
| [3] |
BUTERIN V. ETHEREUM: A Next-Generation Cryptocurrency and Decentralized Application Platform[EB/OL]. (2015-07-14)[2021-09-18]. https://blockchainlab.com/pdf/Ethereum_white_paper-a_next_generation_smart_contract_and_decentralized_application_platform-vitalik-buterin.pdf.
|
| [4] |
MEHAR M I, SHIER C L, GIAMBATTISTA A, et al. Understanding A Revolutionary and Flawed Grand Experiment in Blockchain: The DAO Attack[J]. Journal of Cases on Information Technology(JCIT), 2019, 21(1): 19-32.
|
| [5] |
WANG Bin, LIU Han, LIU Chao, et al. Blockeye: Hunting for Defi Attacks on Blockchain[C]//IEEE. 2021 IEEE/ACM 43rd International Conference on Software Engineering:Companion Proceedings(ICSE-Companion). New York: IEEE, 2021: 17-20.
|
| [6] |
JIANG Bo, LIU Ye, CHAN W K. ContractFuzzer: Fuzzing Smart Contracts for Vulnerability Detection[C]//ACM. 33rd ACM/IEEE International Conference on Automated Software Engineering. New York: ACM, 2018: 259-269.
|
| [7] |
ZHANG Qingzhao, WANG Yizhuo, LI Juanru, et al. Ethploit: From Fuzzing to Efficient Exploit Generation against Smart Contracts[C]//IEEE. 27th International Conference on Software Analysis, Evolution and Reengineering(SANER). New York: IEEE, 2020: 116-126.
|
| [8] |
LUU L, CHU D H, OLICKEL H, et al. Making Smart Contracts Smarter[C]//ACM. 2016 ACM SIGSAC Conference on Computer and Communications Security(CCS). New York: ACM, 2016: 254-269.
|
| [9] |
PRECHTEL D, GROS T, MÜLLER T. Evaluating Spread of ‘Gasless Send’ in Ethereum Smart Contracts[C]//IEEE. 2019 10th IFIP International Conference on New Technologies, Mobility and Security(NTMS). New York: IEEE, 2019: 1-6.
|
| [10] |
BHARGAVAN K, DELIGNAT-LAVAUD A, FOURNET C, et al. Formal Verification of Smart Contracts: Short Paper[C]//ACM. 2016 ACM Workshop on Programming Languages and Analysis for Security(PLAS). New York: ACM, 2016: 91-96.
|
| [11] |
TSANKOV P, DAN A, DRACHSLER-COHEN D, et al. Securify: Practical Security Analysis of Smart Contracts[C]//ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security(CCS). New York: ACM, 2018: 67-82.
|
| [12] |
TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I, et al. SmartCheck: Static Analysis of Ethereum Smart Contracts[C]//ACM. 1st International Workshop on Emerging Trends in Software Engineering for Blockchain. New York: ACM, 2018: 9-16.
|
| [13] |
FEIST J, GRIECO G, GROCE A. Slither: A Static Analysis Framework for Smart Contracts[C]//IEEE. 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain(WETSEB). New York: IEEE, 2019: 8-15.
|
| [14] |
GORI M, MONFARDINI G, SCARSELLI F. A New Model for Learning in Graph Domains[C]//IEEE. 2005 IEEE International Joint Conference on Neural Networks. New York: IEEE, 2005: 729-734.
|
| [15] |
CHANG R Y, PODGURSKI A, YANG J. Discovering Neglected Conditions in Software by Mining Dependence Graphs[J]. IEEE Transactions on Software Engineering, 2008, 34(5): 579-596.
doi: 10.1109/TSE.2008.24
URL
|
| [16] |
LI Yujia, GU Chenjie, DULLIEN T, et al. Graph Matching Networks for Learning the Similarity of Graph Structured Objects[EB/OL]. (2019-07-12)[2021-09-18]. http://proceedings.mlr.press/v97/li19d.html.
|
| [17] |
ZHUANG Yuan, LIU Zhenguang, QIAN Peng, et al. Smart Contract Vulnerability Detection Using Graph Neural Network[EB/OL]. (2020-05-08)[2021-09-18]. https://www.ijcai.org/Proceedings/2020/0454. pdf.
|
| [18] |
GILMER J, SCHOENHOLZ S S, RILEY P F, et al. Neural Message Passing for Quantum Chemistry[EB/OL]. (2017-09-13)[2021-09-18]. https://proceedings.mlr.press/v70/gilmer17a.html.
|
| [19] |
FERREIRA J F, CRUZ P, DURIEUX T, et al. SmartBugs: A Frameworkto Analyze Solidity Smart Contracts[C]//IEEE. 35th IEEE/ACM International Conference on Automated Software Engineering. New York: IEEE, 2020: 1349-1352.
|
 ), LIU Daifu1, TONG Fei1,2
), LIU Daifu1, TONG Fei1,2