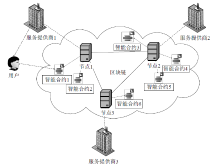
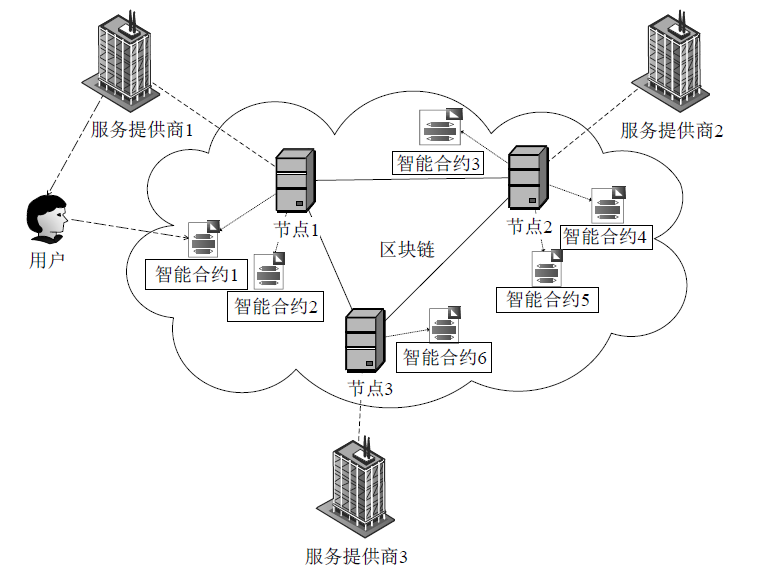
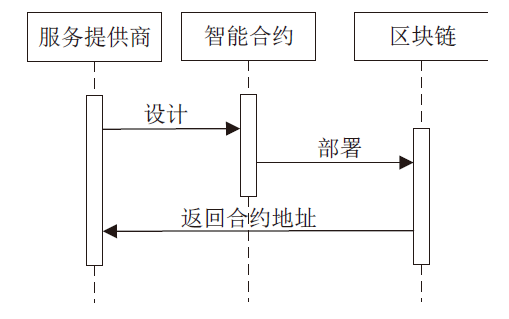
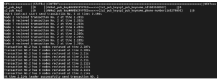
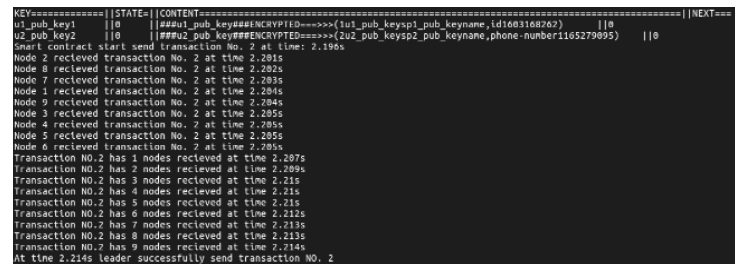
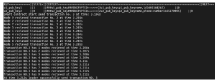
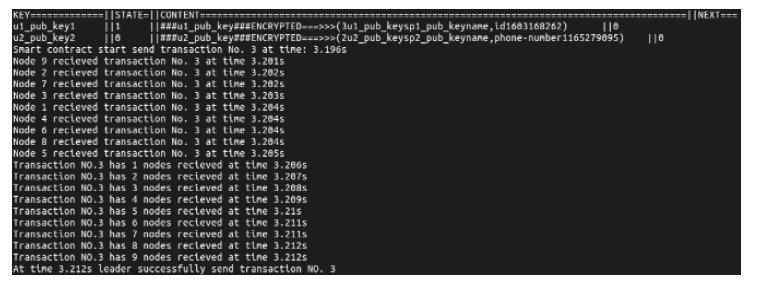
| [1] |
SWINHOE D. The 15 Biggest Data Breaches of the 21st Century[EB/OL]. https://www.csoonline.com/article/2130877/the-biggest-data-breaches-of-the-21st-century.html, 2020-4-17.
|
| [2] |
WINDER D. Unsecured Facebook Databases Leak Data of 419 Million Users[EB/OL]. http://www.forbes.com/sites/daveywinder/2019/09/05/facebook-security-snafu-exposes-419-million-user-phone, 2019-9-5.
|
| [3] |
PATTERSON D, KATES G. We Found Our Personal Data on the Dark Web. Is Yours There, Too?[EB/OL]. https://www.cbsnews.com/news/we-found-our-personal-data-on-thedark-web-is-yours-there-too, 2019-3-25.
|
| [4] |
ARMSTRONG D. My Three Years in Identity Theft Hell[EB/OL]. https://www.bloomberg.com/news/articles/2017-09-13/my-three-years-in-identity-theft-hell, 2017-9-13.
|
| [5] |
CNNIC. The 44th China Statistical Report on Internet Development[R]. Beijing: China Internet Information Center, 1124938750, 2019-8-30.
|
|
中国互联网信息中心. 第44次中国互联网络发展状况统计报告[R]. 北京:中国互联网络信息中心,1124938750, 2019-8-30.
|
| [6] |
WANG Xueqi. Personal Privacy Information Leaked by Mobile Phone Apps, Just the Tip of the Iceberg, Exposed on March 15[EB/OL]. http://finance.sina.com.cn/consume/puguangtai/2019-03-17/doc-ihrfqzkc4361467.shtml, 2019-3-16.
|
|
王雪琦. 3·15晚会曝光手机APP泄露个人隐私信息,这只是冰山一角[EB/OL]. http://finance.sina.com.cn/consume/puguangtai/2019-03-17/doc-ihrfqzkc4361467.shtml, 2019-3-16.
|
| [7] |
NAKAMOTO S. Bitcoin: A Peer-to-peer Electronic Cash System[EB/OL]. https://bitco.in/pdf/bitcoin.pdf, 2008-11-1.
|
| [8] |
BAE S H, KIM J. Personal Information Protection Model Based on Mobile Agent[C]//IEEE. 7th International Conference on Information Technology: New Generations, April 12-14, 2010, Las Vegas, Nevada, USA. New York: IEEE, 2010: 719-724.
|
| [9] |
DE MONTJOYE Y A, SHMUELI E, WANG S S, et al. openPDS: Protecting the Privacy of Metadata through Safeanswers[EB/OL]. https://journals.plos.org/plosone/article/file?id=10.1371/journal.pone. 0098790& type=printable, 2020-2-11.
|
| [10] |
REAGLE J, CRANOR L F. The Platform for Privacy Preferences[J]. Communications of the ACM, 1999,42(2):48-55.
|
| [11] |
ASHLEY P, HADA S, KARJOTH G, et al. Enterprise Privacy Authorization Language(EPAL)[J]. IBM Research, 2003,1(1):30-31.
|
| [12] |
ANDERSON A, NADALIN A, PARDUCCI B, et al. Extensible Access Control Markup Language(xacml) Version 1.0[EB/OL]. https://www.oasis-open.org/committees/download.php/2406/oasis-xacml-1.0.pdf, 2003-2-18.
|
| [13] |
KO H G, KIM S H, JIN S H. Usability Enhanced Privacy Protection System Based on Users’ Responses[C]//IEEE. 2007 IEEE International Symposium on Consumer Electronics, June 20-23, 2007, Irving, Texas, USA. New York: IEEE, 2007: 1-6.
|
| [14] |
BEKARA K, LAURENT M. Enabling User Privacy in Identity Management Systems[C]//IEEE. 2010 IEEE International Conference on Information Theory and Information Security, December 17-19, 2010, Beijing, China. New York: IEEE, 2010: 514-520.
|
| [15] |
ARUNKUMAR S, RAGHAVENDRA A, WEERASINGHE D, et al. Policy Extension for Data Access Control[C]//IEEE. 6th IEEE Workshop on Secure Network Protocols, October. 5, 2010, Kyoto, Japan. New York: IEEE, 2010: 55-60.
|
| [16] |
ZYSKIND G, NATHAN O. Decentralizing Privacy: Using Blockchain to Protect Personal Data[C]//IEEE. 2015 IEEE Security and Privacy Workshops, May 21-22, 2015, San Jose, CA, USA. New York: IEEE, 2015: 180-184.
|
| [17] |
RAHMADIKA S, RHEE K H. Blockchain Technology for Providing an Architecture Model of Decentralized Personal Health Information[EB/OL]. https://www.onacademic.com/detail/journal_1000040485092010_cd21.html, 2020-2-11.
|
| [18] |
JI Y, BEA S, SHIN Y A. Personal Information Management Using Blockchain[C]//IEEE. 2019 International Conference on Information Networking(ICOIN), January 9-11, 2019, Kuala Lumpur, Malaysia, Malaysia. New York: IEEE, 2019: 489-493.
|
| [19] |
SZABO N. Smart Contracts: Building Blocks for Digital Markets[EB/OL]. https://kameir.com/smart-contracts. 2020-2-14.
|
| [20] |
RICHARD GENDAL BROWN. A Simple Model for Smart Contracts[EB/OL]. https://gendal.me/2015/02/10/a-simple-model-for-smart-contracts/, 2015-2-10.
|
| [21] |
MERKLE R C. Protocols for Public Key Cryptosystems[C]//IEEE. 1980 IEEE Symposium on Security and Privacy, April 14-16, 1980, Oakland, CA, USA. New York: IEEE, 1980: 122.
|
| [22] |
CASTRO M, LISKOV B. Practical Byzantine Fault Tolerance and Proactive Recovery[J]. ACM Transactions on Computer Systems(TOCS), 2002,20(4):398-461.
|
| [23] |
LAMPORT L. The Part-time Parliament[J]. ACM Transactions on Computer Systems, 1998,16(2):133-169.
|
| [24] |
LAMPORT L. Paxos Made Simple[J]. ACM Sigact News, 2001,32(4):18-25.
|
| [25] |
ONGARO D, OUSTERHOUT J. In Search of an Understandable Consensus Algorithm[C]// USENIX. 2014 USENIX Annual Technical Conference, June 19-20, 2014, Philadelphia, PA. California: USENIX, 2014: 305-319.
|
 ), WANG Weiqi1, WANG Jian4,5
), WANG Weiqi1, WANG Jian4,5