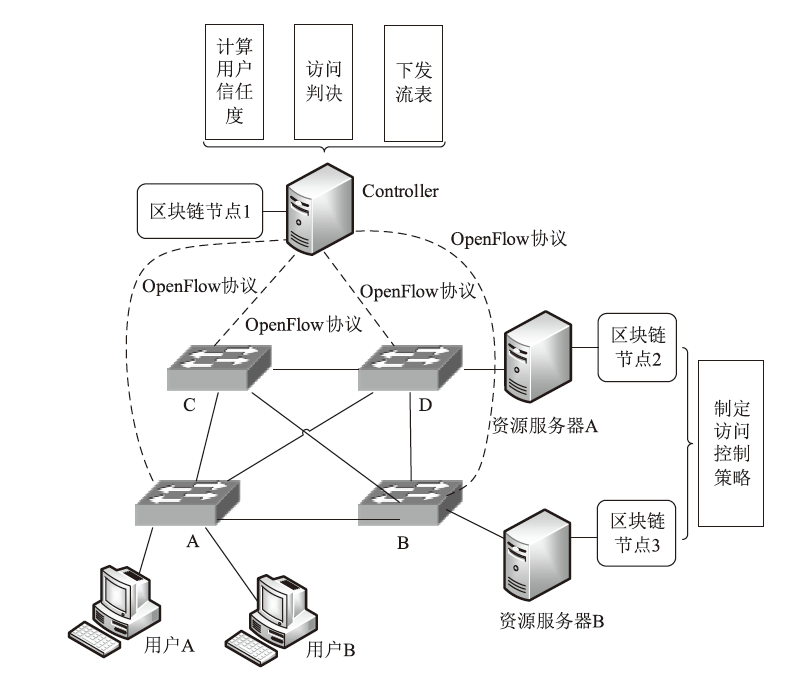
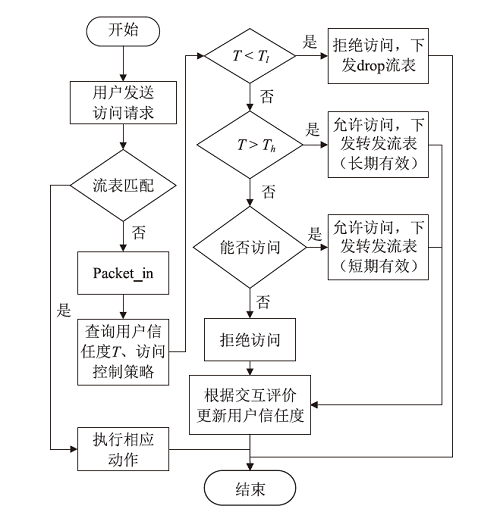
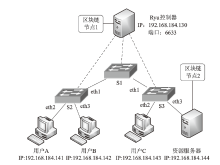
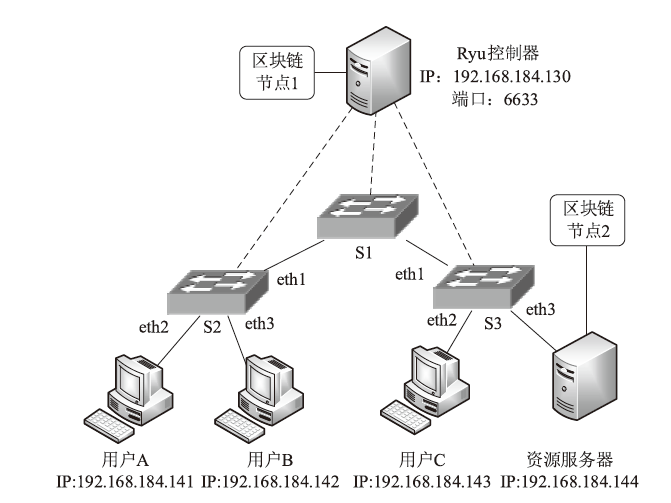
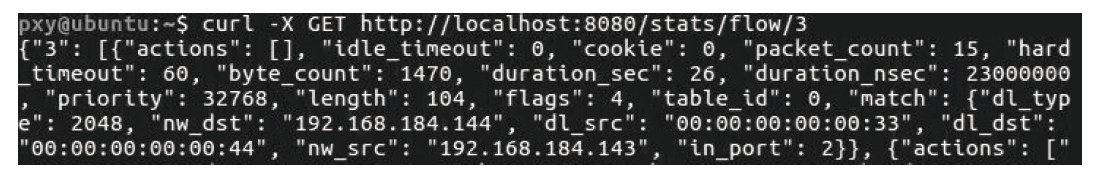
Netinfo Security ›› 2021, Vol. 21 ›› Issue (10): 33-40.doi: 10.3969/j.issn.1671-1122.2021.10.005
Previous Articles Next Articles
Resource Access Control Scheme Based on User Credit in SDN
WEI Zhanzhen, PENG Xingyuan, ZHAO Hong( )
)
- Beijing Electronic Science and Technology Institute, Beijing 100070, China
-
Received:2021-04-12Online:2021-10-10Published:2021-10-14 -
Contact:ZHAO Hong E-mail:zh@besti.edu.cn
CLC Number:
Cite this article
WEI Zhanzhen, PENG Xingyuan, ZHAO Hong. Resource Access Control Scheme Based on User Credit in SDN[J]. Netinfo Security, 2021, 21(10): 33-40.
share this article
| [1] | WANG Mengmeng, LIU Jianwei, CHEN Jie, et al. Software Defined Networking: Security Model, Threats and Mechanism[J]. Journal of Software, 2016, 27(4):969-992. |
| 王蒙蒙, 刘建伟, 陈杰, 等. 软件定义网络:安全模型、机制及研究进展[J]. 软件学报, 2016, 27(4):969-992. | |
| [2] | WANG Tao, CHEN Hongchang, CHENG Guozhen. Research on Software-defined Network and the Security Defense Technology[J]. Journal on Communications, 2017, 38(11):133-160. |
| 王涛, 陈鸿昶, 程国振. 软件定义网络及安全防御技术研究[J]. 通信学报, 2017, 38(11):133-160. | |
| [3] | LIU Zhigang, XIAO Qinghui, DING Xuefei, et al. Software Defined Network User Dynamic Access Control Model Simulation[J]. Computer Simulation, 2019, 36(1):308-311, 396. |
| 刘治纲, 肖庆汇, 丁雪非, 等. 软件定义网络用户动态访问控制模型仿真[J]. 计算机仿真, 2019, 36(1):308-311,396. | |
| [4] | KATAOKA K, GANGWAR S, PODILI P. Trust List: Internet-wide and Distributed IoT Traffic Management Using Blockchain and SDN[EB/OL]. https://ieeexplore.ieee.org/document/8355139, 2018-02-22. |
| [5] | PAILLISSE J, SUBIRA J, LOPEZ A, et al. Distributed Access Control with Blockchain[EB/OL]. https://arxiv.org/pdf/1901.03568.pdf, 2019-07-16. |
| [6] |
NOVO O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT[J]. IEEE Internet of Things Journal, 2018, 5(2):1184-1195.
doi: 10.1109/JIOT.2018.2812239 URL |
| [7] | ZHANG Jiale, ZHANG Guiling, ZHANG Xiufang. Network Access Control Model Based on Real-Time Behavior Trusted Measurement[J]. Computer Applications and Software, 2017, 34(7):32-38. |
| 张佳乐, 张桂玲, 张秀芳. 基于实时行为可信度量的网络访问控制模型[J]. 计算机应用与软件, 2017, 34(7):32-38. | |
| [8] | OUADDAH A, ELKALAM A A, OUAHMAN A A. FairAccess: A New Blockchain-based Access Control Framework for the Internet of Things[J]. Security & Communication Networks, 2016, 9(18):5943-5964. |
| [9] | OUADDAH A, MOUSANNIF H, ELKALAM A A, et al. Access Control in the Internet of Things: Big Challenges and New Opportunities[EB/OL]. https://linkinghub.elsevier.com/retrieve/pii/S1389128616303735, 2017-01-20. |
| [10] | OUADDAH A, ELKALAM A A, OUAHMAN A A. Towards a Novel Privacy-preserving Access Control Model Based on Blockchain Technology in IoT[EB/OL]. https://doi.org/10.1007/978-3-319-46568-5_53, 2016-09-12. |
| [11] | DU Ruizhong, LIU Yan, TIAN Junfeng. An Access Control Method Using Smart Contract for Internet of Things[J]. Journal of Computer Research and Development, 2019, 56(10):2287-2298. |
| 杜瑞忠, 刘妍, 田俊峰. 物联网中基于智能合约的访问控制方法[J]. 计算机研究与发展, 2019, 56(10):2287-2298. | |
| [12] | PUTRA G D, DEDEOGLU V, KANHERE S S, et al. Trust Management in Decentralized IoT Access Control System[EB/OL]. https://export.arxiv.org/pdf/1912.10247, 2020-12-20. |
| [13] | LIU Aodi, DU Xuehui, WANG Na, et al. Blockchain-based Access Control Mechanism for Big Data[J]. Journal of Software, 2019, 30(9):2636-2654. |
| 刘敖迪, 杜学绘, 王娜, 等. 基于区块链的大数据访问控制机制[J]. 软件学报, 2019, 30(9):2636-2654. | |
| [14] | MA Mingxin, SHI Guozhen, LI Fenghua. Privacy-oriented Blockchain-based Distributed Key Management Architecture for Hierarchical Access Control in the IoT Scenario[EB/OL]. https://ieeexplore.ieee.org/document/8664491, 2020-12-20. |
| [15] | SHI Jinshan, LI Ru, SONG Tingting. Blockchain-based Access Control Framework for Internet of Things[J]. Journal of Computer Applications, 2020, 40(4):931-941. |
| 史锦山, 李茹, 松婷婷. 基于区块链的物联网访问控制框架[J]. 计算机应用, 2020, 40(4):931-941. | |
| [16] | WANG Xiuli, JIANG Xiaozhou, LI Yang. Model for Data Access Control and Sharing Based on Blockchain[J]. Journal of Software, 2019, 30(6):1661-1669. |
| 王秀利, 江晓舟, 李洋. 应用区块链的数据访问控制与共享模型[J]. 软件学报, 2019, 30(6):1661-1669. | |
| [17] | YANG Bo, ZHANG Yun, WANG Xin. A Network Access Control Method Based on Cloud Computing[J]. Software Engineering, 2017, 20(2):50-53. |
| 杨波, 张云, 王欣. 一种基于云计算的网络访问控制方法[J]. 软件工程, 2017, 20(2):50-53. | |
| [18] | BAO Yulong, ZHU Xueyang, ZHANG Wenhui, et al. Formal Verification of Smart Contract for Access Control in IoT Applications[J]. Chinese Journal of Computers, 2021, 41(4):930-938. |
| 包玉龙, 朱雪阳, 张文辉, 等. 物联网应用中访问控制智能合约的形式化验证[J]. 计算机应用, 2021, 41(4):930-938. | |
| [19] | AKIMICHI, NAOKI M, ATSUSHI I. Mastering TCP/IP OpenFlow[M]. LI Zhanjun, XUE Wenling. Beijing: Posts & Telecom Press, 2016. |
| 晃通, 宫永直树, 岩田淳. 图解OpenFlow[M]. 李战军, 薛文玲,译.北京:人民邮电出版社, 2016. | |
| [20] | XU Ke, LING Sitong, LI Qi, et al. Research Progress of Network Security Architecture and Key Technologies Based on Blockchain[J]. Chinese Journal of Computers, 2021, 44(1):55-83. |
| 徐恪, 凌思通, 李琦, 等. 基于区块链的网络安全体系结构与关键技术研究进展[J]. 计算机学报, 2021, 44(1):55-83. |
| [1] | JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning [J]. Netinfo Security, 2021, 21(8): 52-61. |
| [2] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [3] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [4] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [5] | WU Yunkun, JIANG Bo, PAN Ruixuan, LIU Yuling. A SDN Access Control Mechanism Based on Zero Trust [J]. Netinfo Security, 2020, 20(8): 37-46. |
| [6] | WANG Jian, WANG Yujie, HAN Lei. DDoS Attack Detection Based on Catastrophe Theory in SDN Environment [J]. Netinfo Security, 2020, 20(5): 11-20. |
| [7] | DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [8] | LIU Peng, HE Qian, LIU Wangyang, CHENG Xu. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [9] | YU Lu, LUO Senlin. A Method of Internal Intrusion Detection of Database in RBAC Mode [J]. Netinfo Security, 2020, 20(2): 83-90. |
| [10] | XU Shengwei, WANG Feijie. Attribute-based Encryption Scheme Traced Under Multi-authority [J]. Netinfo Security, 2020, 20(1): 33-39. |
| [11] | Jinmiao WANG, Guowei WANG, Mei WANG, Ruijin ZHU. Achieving Privacy Preserving and Flexible Access Control in Fog Computing [J]. Netinfo Security, 2019, 19(9): 41-45. |
| [12] | A-yong YE, Junlin JIN, Lingyu MENG, Ziwen ZHAO. Research on Access Control for Privacy Protection of Mobile Terminals [J]. Netinfo Security, 2019, 19(8): 51-60. |
| [13] | Zhongyuan QIN, Yin HAN, Qunfang ZHANG, Xuejin ZHU. An Improved Scheme of Multi-PKG Cloud Storage Access Control [J]. Netinfo Security, 2019, 19(6): 11-18. |
| [14] | Fangbo CAI, Jingsha HE, Nafei ZHU, Song HAN. Research on Cascading Failure of Nodes in Distributed Access Control Model [J]. Netinfo Security, 2019, 19(12): 47-52. |
| [15] | Xiangquan SHI, Jing TAO, Baokang ZHAO. A Network Access Control System in Virtualized Environments [J]. Netinfo Security, 2019, 19(10): 1-9. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||