Netinfo Security ›› 2023, Vol. 23 ›› Issue (7): 44-52.doi: 10.3969/j.issn.1671-1122.2023.07.005
Previous Articles Next Articles
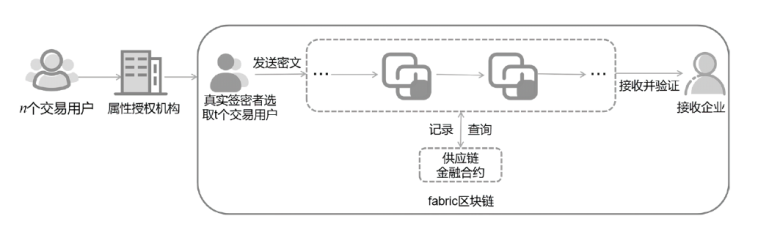
Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance
YU Huifang1( ), QIAO Yifan1, MENG Ru2
), QIAO Yifan1, MENG Ru2
- 1. School of Cyberspace Security, Xi’an University of Posts & Telecommunications, Xi’an 710121, China
2. School of Cyberspace Security, Jinan University, Guangzhou 510632, China
-
Received:2023-03-27Online:2023-07-10Published:2023-07-14
CLC Number:
Cite this article
YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance[J]. Netinfo Security, 2023, 23(7): 44-52.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.07.005
| [1] | CHAUM D. Blind Signatures for Untraceable Payments[C]// Springer. Advances in Cryptology: Proceedings of Crypto 82. Berlin:Springer, 1983: 199-203. |
| [2] | KUMAR M, KATTI C P, SAXENA P C. An Untraceable Identity-Based Blind Signature Scheme Without Pairing for E-Cash Payment System[C]// Springer.Ubiquitous Communications and Network Computing: First International Conference. Berlin: Springer, 2018: 67-78. |
| [3] | ZHUANG Lishuang, CHEN Jie, WANG Qiyu. Lattice-Based Linkable Threshold Ring Signature in e-Voting[J]. Journal of Cryptologic Research, 2021, 8(3): 402-416. |
|
庄立爽, 陈杰, 王启宇. 电子投票协议下的基于格的可链接门限环签名[J]. 密码学报, 2021, 8(3): 402-416.
doi: 10.13868/j.cnki.jcr.000447 |
|
| [4] | TIAN Guohua, HU Yunhan, CHEN Xiaofeng. A Survey on Attack and Defense of Block-Chain System[J]. Journal of Software, 2021, 32(5): 1495-1525. |
| 田国华, 胡云瀚, 陈晓峰. 区块链系统攻击与防御技术研究进展[J]. 软件学报, 2021, 32(5): 1495-1525. | |
| [5] | NIU Shufen, WANG Caifen. Homomorphic Signature Algorithm for Multi-Source Linear Network Coding[J]. Computer Engineering, 2012, 38(2): 126-128. |
|
牛淑芬, 王彩芬. 多源线性网络编码的同态签名算法[J]. 计算机工程, 2012, 38(2): 126-128.
doi: 10.3969/j.issn.1000-3428.2012.02.040 |
|
| [6] |
WANG Zhiwei, FAN Jiaxing. Flexible Threshold Ring Signature in Chronological Order for Privacy Protection in Edge Computing[J]. IEEE Transactions on Cloud Computing, 2020, 10(2): 1253-1261.
doi: 10.1109/TCC.2020.2974954 URL |
| [7] | SUN Yiru, ZHENG Weiming. An Identity-Based Ring Signcryption Scheme in Ideal Lattice[J]. Journal of Network Intelligence, 2018, 3(3): 152-161. |
| [8] | NAYAK S K, MOHANTY S, MAJHI B. CLB-ECC: Certificateless Blind Signature Using ECC[J]. Journal of Information Processing Systems, 2017, 13(4): 970-986. |
| [9] |
ISLAM S H, AMIN R, BISWAS G P, et al. Provably Secure Pairing-Free Identity-Based Partially Blind Signature Scheme and Its Application in Online e-Cash System[J]. Arabian Journal for Science and Engineering, 2016, 41: 3163-3176.
doi: 10.1007/s13369-016-2115-5 URL |
| [10] | AJTAI M, KUMAR R, SIVAKUMAR D. Sampling Short Lattice Vectors and the Closest Lattice Vector Problem[C]// IEEE. Proceedings 17th IEEE Annual Conference on Computational Complexity. New York: IEEE, 2002: 53-57. |
| [11] |
TIAN Juanhong, ZHANG Jianzhong, LI Yanping. A Quantum Multi-Proxy Blind Signature Scheme Based On Genuine Four-Qubit Entangled State[J]. International Journal of Theoretical Physics, 2016, 55(2): 809-816.
doi: 10.1007/s10773-015-2719-7 URL |
| [12] |
WANG Shanping, MA Rui, ZHANG Yaling, et al. Ring Signature Scheme Based on Multivariate Public Key Cryptosystems[J]. Computers & Mathematics with Applications, 2011, 62(10): 3973-3979.
doi: 10.1016/j.camwa.2011.09.052 URL |
| [13] |
LIU Xiaoqian, ZHAO Yiming. Variant Scheme of Ring Signature Based on Multivariate Public Key Cryptosystems[J]. Computer Engineering, 2015, 41(2): 96-99.
doi: 10.3969/j.issn.1000-3428.2015.02.019 |
| [14] | GUO Qiuling, XIANG Hong, CAI Bin, et al. Threshold Ring Signature Scheme Based on Multivariate Public Key Cryptosystems[J]. Journal of Cryptologic Research, 2018, 5(2): 140-150. |
|
郭秋玲, 向宏, 蔡斌, 等. 基于多变量公钥密码体制的门限环签名方案[J]. 密码学报, 2018, 5(2): 140-150.
doi: 10.13868/j.cnki.jcr.000226 |
|
| [15] | YU Huifang, YANG Bo. Low-Computation Certificateless Hybrid Signcryption Scheme[J]. Frontiers of Information Technology & Electronic Engineering, 2017, 18(7): 928-940. |
| [16] |
YU Huifang, WANG Weike, ZHANG Qi. Certificateless Anti-Quantum Ring Signcryption for Network Coding[J]. Knowledge-Based Systems, 2022, 235: 107655.
doi: 10.1016/j.knosys.2021.107655 URL |
| [17] | CHEN Hu, HU Yupu, LIAN Zhizhu, et al. Efficient Certificateless Encryption Schemes from Lattices[J]. Journal of Software, 2015, 27(11): 2884-2897. |
| 陈虎, 胡予濮, 连至助, 等. 有效的格上无证书加密方案[J]. 软件学报, 2015, 27(11): 2884-2897. | |
| [18] | YU Huifang, WANG Ning. Certificateless Network Coding Proxy Signatures from Lattice[J]. Frontiers of Computer Science, 2023, 17(5): 1-8. |
| [19] |
CAI Ying, ZHANG Hao, FANG Yuguang. A Conditional Privacy Protection Scheme Based on Ring Signcryption for Vehicular Ad Hoc Networks.[J]. IEEE Internet of Things Journal, 2020, 8(1): 647-656.
doi: 10.1109/JIoT.6488907 URL |
| [20] |
CHEN Zhen, ZHANG Wenfang, WANG Xiaomin. Attribute-Based Alterable Threshold Ring Signature Scheme with Conspiracy Attack Immunity[J]. Journal on Communications, 2015, 36(12): 212-222.
doi: 10.11959/j.issn.1000-436x.2015330 |
|
陈桢, 张文芳, 王小敏. 基于属性的抗合谋攻击可变门限环签名方案[J]. 通信学报, 2015, 36(12): 212-222.
doi: 10.11959/j.issn.1000-436x.2015330 |
|
| [21] | SUN Hua, WANG Aimin, ZHENG Xuefeng. Provably Secure Identity-Based Threshold Ring Signcryption Scheme in Standard Model[J]. Computer Science, 2013, 40(5): 131-135. |
| 孙华, 王爱民, 郑雪峰. 标准模型下可证安全的基于身份的门限环签密方案[J]. 计算机科学, 2013, 40(5): 131-135. |
| [1] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [2] | LI Zengpeng, WANG Mei, CHEN Mengjia. Research of New Forms of Pseudorandom Random Function [J]. Netinfo Security, 2023, 23(5): 11-21. |
| [3] | DU Weidong, LI Min, HAN Yiliang, WANG Xu’an. An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique [J]. Netinfo Security, 2023, 23(4): 51-60. |
| [4] | YIN Shu, CHEN Xingshu, ZHU Yi, ZENG Xuemei. Anonymous Domain Name Algorithm Based on Character Space Construction [J]. Netinfo Security, 2023, 23(4): 80-89. |
| [5] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [6] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [7] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [8] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [9] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 22(3): 78-84. |
| [10] | ZHANG Xuewang, YAO Yaning, LI Zhihong, ZHANG Hao. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm [J]. Netinfo Security, 2022, 22(11): 17-23. |
| [11] | LIANG Guangjun, XIN Jianfang, NI Xueli, MA Zhuo. Research on Smart Speaker Security and Forensics [J]. Netinfo Security, 2022, 22(10): 108-113. |
| [12] | GU Haiyan, JIANG Tong, MA Zhuo, ZHU Jipeng. Research of Improved k-Anonymity Algorithm and Its Application in Privacy Protection [J]. Netinfo Security, 2022, 22(10): 52-58. |
| [13] | XU Shuo, ZHANG Rui, XIA Hui. Privacy-preserving Strategies for Federated Learning Based on Data Attribute Modification [J]. Netinfo Security, 2022, 22(1): 55-63. |
| [14] | TAO Yunting, KONG Fanyu, YU Jia, XU Qiuliang. Survey of Number Theoretic Transform Algorithms for Quantum-resistant Lattice-based Cryptography [J]. Netinfo Security, 2021, 21(9): 46-51. |
| [15] | JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning [J]. Netinfo Security, 2021, 21(8): 52-61. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||