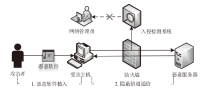
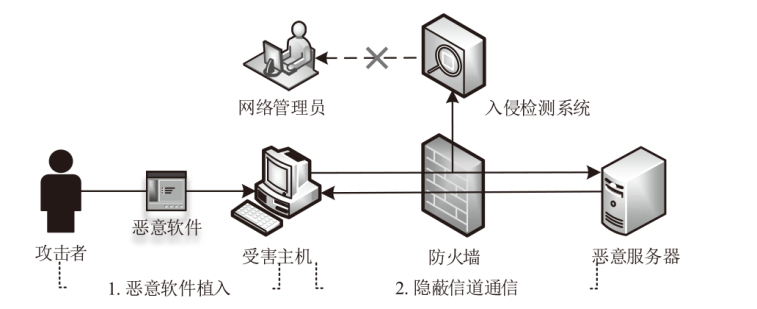
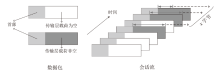
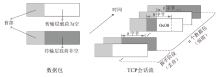
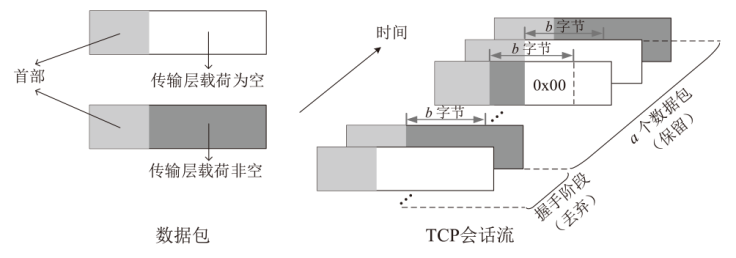
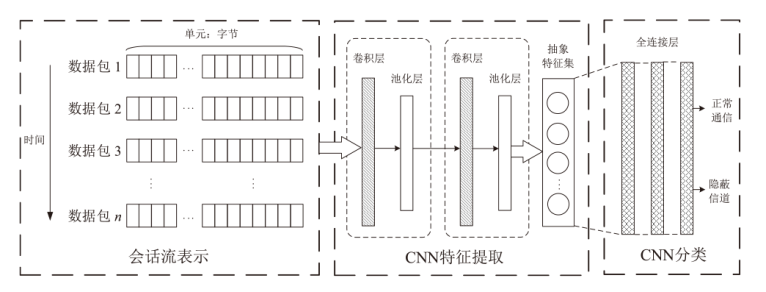
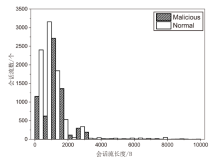
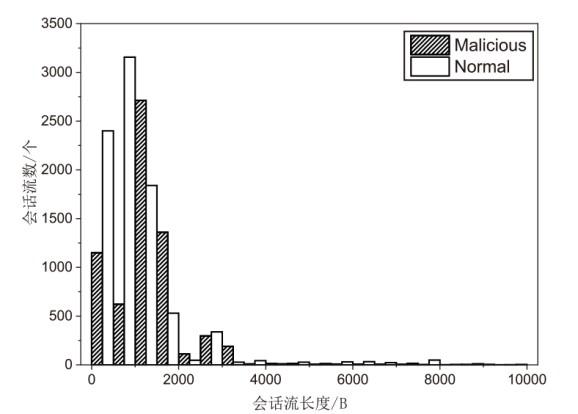
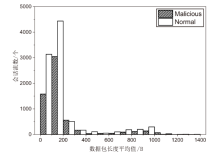
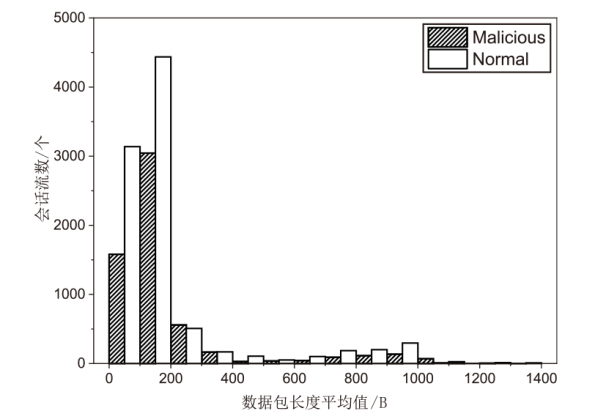
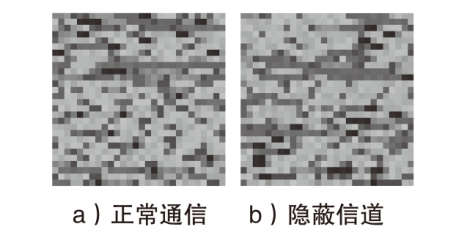
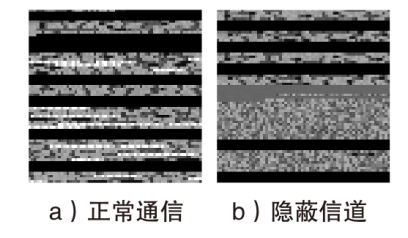
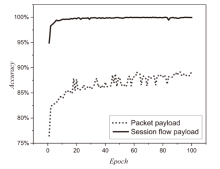
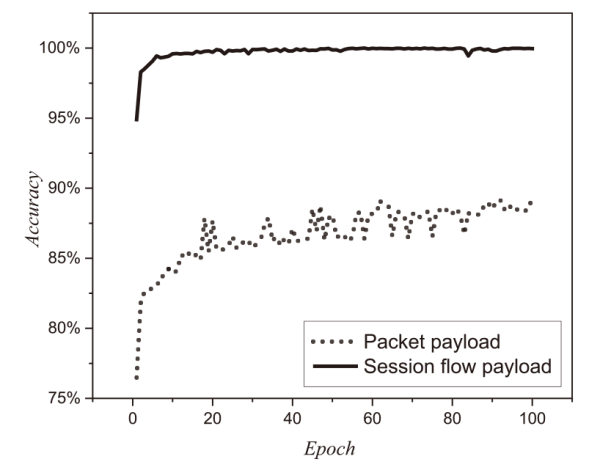
Netinfo Security ›› 2023, Vol. 23 ›› Issue (7): 53-63.doi: 10.3969/j.issn.1671-1122.2023.07.006
Previous Articles Next Articles
HTTP Payload Covert Channel Detection Method Based on Deep Learning
YUAN Wenxin1,2, CHEN Xingshu1,2( ), ZHU Yi1,2, ZENG Xuemei2
), ZHU Yi1,2, ZENG Xuemei2
- 1. School of Cyber Science and Engineering, Sichuan University, Chengdu 610065, China
2. Cyber Science Research Institute, Sichuan University, Chengdu 610207, China
-
Received:2023-03-30Online:2023-07-10Published:2023-07-14
CLC Number:
Cite this article
YUAN Wenxin, CHEN Xingshu, ZHU Yi, ZENG Xuemei. HTTP Payload Covert Channel Detection Method Based on Deep Learning[J]. Netinfo Security, 2023, 23(7): 53-63.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.07.006
| [1] |
LAMPSON BW. A Note on the Confinement Problem[J]. Communications of the ACM, 1973, 16(10): 613-615.
doi: 10.1145/362375.362389 URL |
| [2] | MITRE ATT&CK. Application Layer Protocol: Web Protocols[EB/OL]. (2020-03-26) [2023-03-20]. https://attack.mitre.org/techniques/T1071/001/. |
| [3] | LIU Fang, LI Dongdong, ZHAO Yuntao, et al. The Covert Communication Detection Model Based on Key Field of Header in HTTP Protocol[J]. Fire Control & Command Control, 2018, 43(11): 38-43. |
| 刘芳, 李东东, 赵运弢, 等. HTTP 协议报文头域关键字段的隐蔽通信检测模型[J]. 火力与指挥控制, 2018, 43(11): 38-43. | |
| [4] |
SHEN Guoliang, ZHAI Jiangtao, DAI Yuewei. HTTP Parameter Sorting Covert Channel Detection Method Based on Markov Model[J]. Computer Engineering, 2020, 46(2): 154-158, 169.
doi: 10.19678/j.issn.1000-3428.0053783 |
|
沈国良, 翟江涛, 戴跃伟. 基于Markov模型的HTTP参数排序隐蔽信道检测方法[J]. 计算机工程, 2020, 46(2): 154-158,169.
doi: 10.19678/j.issn.1000-3428.0053783 |
|
| [5] | WU Jiahong, YANG Zhenguo, LIU Wenyin. Multiscale Feature Fusion for Malicious HTTP Request Detection[J]. Application Research of Computers, 2021, 38(3): 871-874+880. |
| 巫家宏, 杨振国, 刘文印. 基于多尺度特征融合的恶意HTTP请求检测方法[J]. 计算机应用研究, 2021, 38(3):871-874,880. | |
| [6] | DARWISH O, Al-FUQAHA A, BRAHIM G B, et al. Using Hierarchical Statistical Analysis and Deep Neural Networks to Detect Covert Timing Channels[EB/OL]. (2019-09-20) [2023-03-20]. https://doi.org/10.1016/j.asoc.2019.105546. |
| [7] |
Al-EIDI S, DARWISH O, CHEN Yuanzhu. Covert Timing Channel Analysis Either as Cyber Attacks or Confidential Applications[J]. Sensors, 2020, 20(8): 2417-2431.
doi: 10.3390/s20082417 URL |
| [8] |
AL-EIDI S, DARWISH O, CHEN Yuanzhu, et al. SnapCatch: Automatic Detection of Covert Timing Channels Using Image Processing and Machine Learning[J]. IEEE Access, 2020, 9: 177-191.
doi: 10.1109/Access.6287639 URL |
| [9] | WANG Yifei, YANG Yalei, RAO Mengliang. Research of HTTP Tunnel Detecting Technique Based on C4.5[J]. Computer Engineering and Design, 2012, 33(2): 493-497. |
| 王宜菲, 杨亚磊, 饶孟良. 基于C4.5的HTTP隧道检测技术研究[J]. 计算机工程与设计, 2012, 33(2):493-497. | |
| [10] | LI Wei, LI Lihui, LI Jia, et al. Characteristics Analysis of Traffic Behavior of Remote Access Trojan in Three Communication Phases[J]. Netinfo Security, 2015, 15(5): 10-15. |
| 李巍, 李丽辉, 李佳, 等. 远控型木马通信三阶段流量行为特征分析[J]. 信息网络安全, 2015, 15(5): 10-15. | |
| [11] | CHEN Xingshu, CHEN Jinghan, SHAO Guolin, et al. A Covert Communication Behavior Detection Method Based on Session Flow Aggregation[J]. Journal of University of Electronic Science and Technology of China, 2019, 48(3): 388-396. |
| 陈兴蜀, 陈敬涵, 邵国林, 等. 基于会话流聚合的隐蔽性通信行为检测方法[J]. 电子科技大学学报, 2019, 48(3): 388-396. | |
| [12] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717. |
| [13] | LIN S Z, SHI Yong, XUE Zhi. Character-Level Intrusion Detection Based On Convolutional Neural Networks[C]// IEEE. 2018 International Joint Conference on Neural Networks (IJCNN). New York: IEEE, 2018: 1-8. |
| [14] | MARÍN G, CAASAS P, CAPDEHOURAT G. Deepmal-Deep Learning Models for Malware Traffic Detection and Classification[C]// Springer. Data Science-Analytics and Applications:Proceedings of the 3rd International Data Science Conference-IDSC2020. Berlin:Springer, 2021: 105-112. |
| [15] |
WANG Shanshan, YAN Qiben, CHEN Zhenxiang, et al. Detecting Android Malware Leveraging Text Semantics of Network Flows[J]. IEEE Transactions on Information Forensics and Security, 2017, 13(5): 1096-1109.
doi: 10.1109/TIFS.2017.2771228 URL |
| [16] | NIU Weina, XIE Jiao, ZHANG Xiaosong, et al. HTTP-Based APT Malware Infection Detection Using URL Correlation Analysis[J]. Security and Communication Networks, 2021, 21: 1-12. |
| [17] | YUN Xiaochun, XIE Jiang, LI Shuhao, et al. Detecting Unknown HTTP-Based Malicious Communication Behavior via Generated Adversarial Flows and Hierarchical Traffic Features[EB/OL]. (2022-07-16) [2023-03-20]. https://doi.org/10.1016/j.cose.2022.102834. |
| [18] | FIELDING R, RESCHKE J. Hypertext Transfer Protocol (HTTP/1.1): Message Syntax and Routing[R]. New York: Internet Engineering Task Force (IETF), ISSN: 2070-1721, 2014. |
| [19] | KASUYA M. Threat Spotlight: Amadey Bot Targets Non-Russian Users[EB/OL]. (2020-01-08) [2023-03-20]. https://blogs.blackberry.com/en/2020/01/threat-spotlight-amadey-bot. |
| [20] | DUNCAN B. Evolution of Valak, from Its Beginnings to Mass Distribution[EB/OL]. (2020-07-24) [2023-03-20]. https://unit42. paloaltonetworks.com/valak-evolution/. |
| [21] | SHANNON C E. A Mathematical Theory of Communication[J]. ACM SIGMOBILE Mobile Computing and Communications Review, 2001, 5(1): 3-55. |
| [22] | SUN Zhongjun, ZHAI Jiangtao, DAI Yuewei. An Encrypted Traffic Identification Method Based on DPI and Load Randomness[J]. Journal of Applied Sciences, 2019, 37(5): 711-720. |
| 孙中军, 翟江涛, 戴跃伟. 一种基于DPI和负载随机性的加密流量识别方法[J]. 应用科学学报, 2019, 37(5): 711-720. | |
| [23] | AOUINI Z, PEKAR A. NFStream: A Flexible Network Data Analysis Framework[EB/OL]. (2022-02-26) [2023-03-20]. https://doi.org/10.1016/j.comnet.2021.108719. |
| [24] |
SHIRAVI A, SHIRAVI H, TAVALLAEE M, et al. Toward Developing a Systematic Approach to Generate Benchmark Datasets for Intrusion Detection[J]. Computers & Security, 2012, 31(3): 357-374.
doi: 10.1016/j.cose.2011.12.012 URL |
| [25] | WRAD D. Malware-Traffic-Analysis.net[EB/OL]. [2023-03-20]. https://malware-traffic-analysis.net/. |
| [26] | MONTAZERISHATOORI M, DAVIDSON L, KAUR G, et al. Detection of DoH Tunnels Using Time-Series Classification of Encrypted Traffic[C]// IEEE. IEEE International Symposium on Dependable, Autonomic and Secure Computing (DASC). New York: IEEE, 2020: 17-22. |
| [1] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [2] | ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning [J]. Netinfo Security, 2023, 23(5): 1-10. |
| [3] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [4] | SHEN Chuanxin, WANG Yongjie, XIONG Xinli. DNS Covert Channel Detection Based on Graph Attention Network [J]. Netinfo Security, 2023, 23(1): 73-83. |
| [5] | LIU Guangjie, DUAN Kun, ZHAI Jiangtao, QIN Jiayu. Mobile Traffic Application Recognition Based on Multi-Feature Fusion [J]. Netinfo Security, 2022, 22(7): 18-26. |
| [6] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [7] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [8] | LIN Faxin, ZHANG Jian. Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform [J]. Netinfo Security, 2022, 22(11): 62-67. |
| [9] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [10] | GAO Changfeng, XIAO Yanhui, TIAN Huawei. Image Camera Fingerprint Extraction Algorithm Based on MPRNet [J]. Netinfo Security, 2022, 22(10): 15-23. |
| [11] | LIU Jiayin, LI Fujuan, MA Zhuo, XIA Lingling. Malware Classification Method Based on Multi-Scale Convolutional Neural Network [J]. Netinfo Security, 2022, 22(10): 31-38. |
| [12] | LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm [J]. Netinfo Security, 2021, 21(9): 59-66. |
| [13] | SONG Yubo, MA Wenhao, HU Aiqun, WANG Junbo. A Covert Channel Communication Method Based on Pixel Offset Encoding and Decoding Technique [J]. Netinfo Security, 2021, 21(4): 31-38. |
| [14] | XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM [J]. Netinfo Security, 2021, 21(10): 41-47. |
| [15] | MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model [J]. Netinfo Security, 2021, 21(10): 69-75. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||