Netinfo Security ›› 2023, Vol. 23 ›› Issue (4): 20-29.doi: 10.3969/j.issn.1671-1122.2023.04.003
Previous Articles Next Articles
Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning
ZHAO Caidan1, CHEN Jingqian1, WU Zhiqiang2,3( )
)
- 1. School of Information Science and Technology, Xiamen University, Xiamen 361000, China
2. School of Information Science and Technology, Tibet University, Lhasa 850000, China
3. Peking University Institute for Artificial Intelligence, Beijing 100871, China
-
Received:2022-11-17Online:2023-04-10Published:2023-04-18 -
Contact:WU Zhiqiang E-mail:lightnesstibet@163.com
CLC Number:
Cite this article
ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning[J]. Netinfo Security, 2023, 23(4): 20-29.
share this article
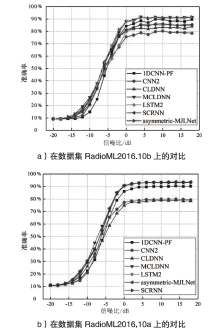
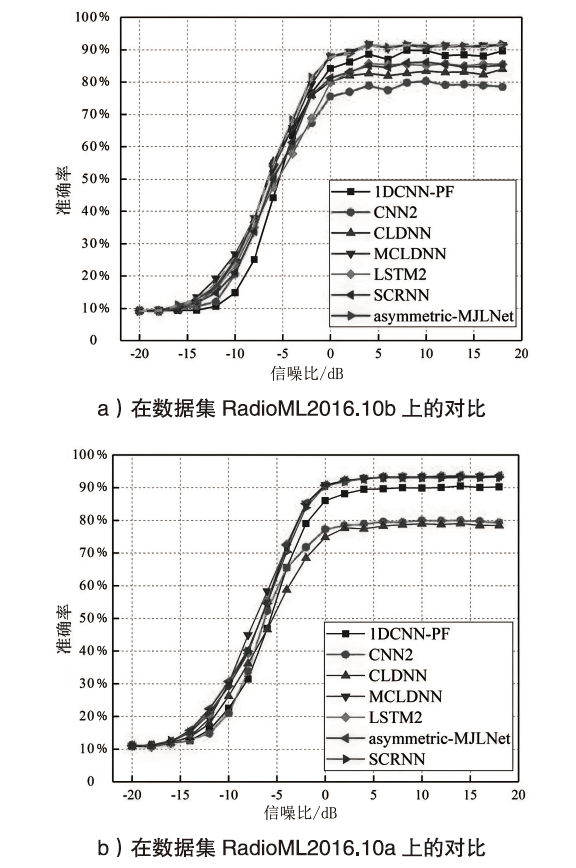
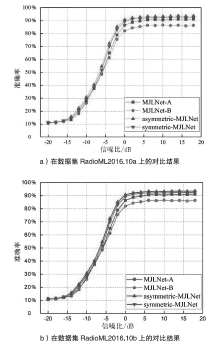
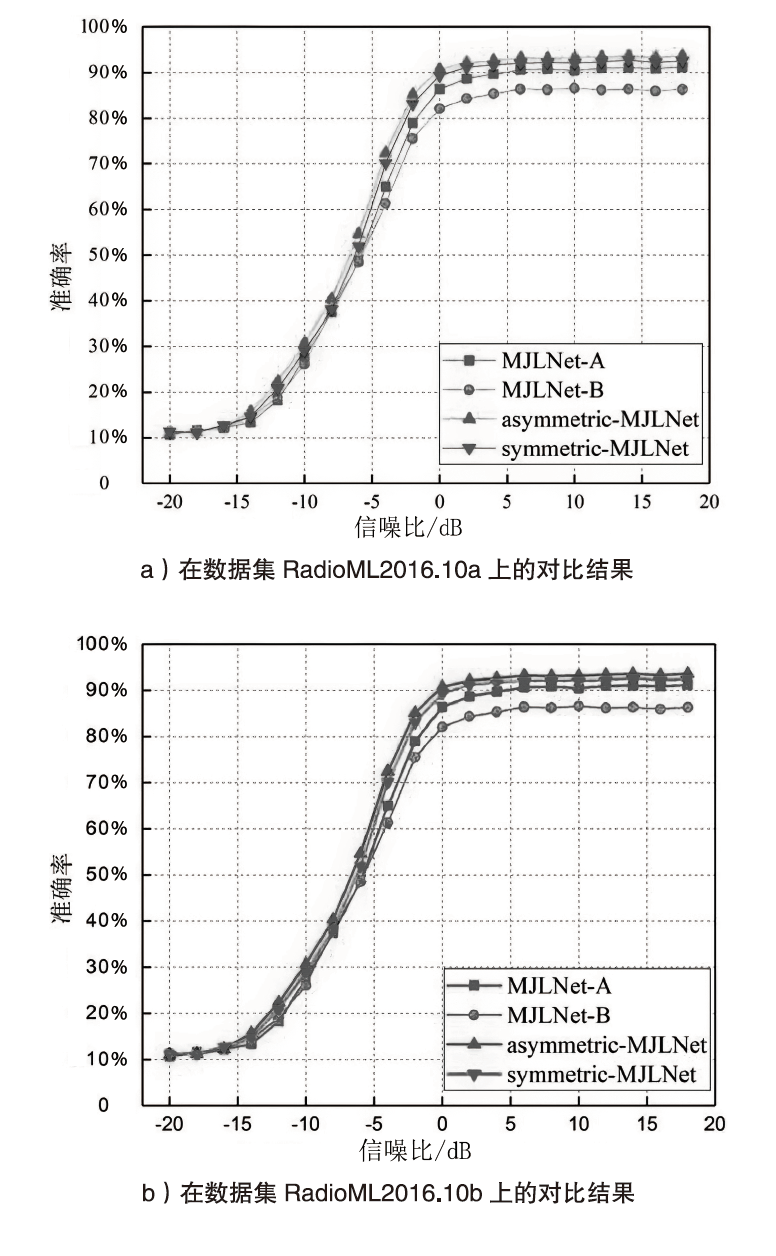
| 网络 调制 方式 | SCRNN | 1DCNN-PF | CNN2 | CLDNN | MCLDNN | LSTM2 | SCRNN | asymmetric-MJLNet |
|---|---|---|---|---|---|---|---|---|
| 8PSK | 84% | 80% | 77% | 82% | 86% | 73% | 84% | 89% |
| AM-DSB | 86% | 99% | 99% | 87% | 89% | 93% | 86% | 90% |
| AM-SSB | 97% | 98% | 95% | 94% | 92% | 95% | 97% | 93% |
| BPSK | 99% | 98% | 98% | 99% | 99% | 94% | 99% | 99% |
| CPFSK | 100% | 100% | 98% | 96% | 100% | 99% | 100% | 100% |
| GFSK | 99% | 94% | 94% | 93% | 99% | 97% | 99% | 97% |
| PAM4 | 98% | 98% | 98% | 97% | 98% | 96% | 98% | 98% |
| QAM16 | 52% | 83% | 40% | 40% | 81% | 76% | 52% | 83% |
| QAM64 | 55% | 71% | 59% | 63% | 86% | 48% | 55% | 81% |
| QPSK | 82% | 95% | 40% | 74% | 96% | 86% | 82% | 97% |
| WBFM | 39% | 29% | 24% | 43% | 41% | 33% | 39% | 38% |
| [1] |
GUPTA A, JHA R K. A Survey of 5G Network: Architecture and Emerging Technologies[J]. IEEE Access, 2015, 3: 1206-1232.
doi: 10.1109/ACCESS.2015.2461602 URL |
| [2] |
WANG Qun, SUN Haijian, HU R Q Y, et al. When Machine Learning Meets Spectrum Sharing Security: Methodologies and Challenges[J]. IEEE Open Journal of the Communications Society, 2022, 3: 176-208.
doi: 10.1109/OJCOMS.2022.3146364 URL |
| [3] |
LANZOLLA G, ANDERSON J A. Digital Transformation[J]. Business Strategy Review, 2008, 19(2): 72-76.
doi: 10.1111/j.1467-8616.2008.00539.x URL |
| [4] |
ZHANG Lin, XIAO Ming, WU Gang, et al. A Survey of Advanced Techniques for Spectrum Sharing in 5G Networks[J]. IEEE Wireless Communications, 2017, 24(5): 44-51.
doi: 10.1109/MWC.2017.1700069 URL |
| [5] | ALARBI A, ALKISHRIWO O A S. Modulation Classification Based on Statistical Features and Artificial Neural Network[C]// IEEE. 2021 IEEE 1st International Maghreb Meeting of the Conference on Sciences and Techniques of Automatic Control and Computer Engineering MI-STA. New York: IEEE, 2021: 748-751. |
| [6] | KIM K, POLYDOROS A. Digital Modulation Classification: The BPSK Versus QPSK Case[C]// IEEE. MILCOM 88, 21st Century Military Communications Conference. New York: IEEE, 1988: 431-436. |
| [7] |
JIANG Yuhan, ZOU Yulong, OUYANG Jian, et al. Secrecy Energy Efficiency Optimization for Artificial Noise Aided Physical-Layer Security in OFDM-Based Cognitive Radio Networks[J]. IEEE Transactions on Vehicular Technology, 2018, 67(12): 11858-11872.
doi: 10.1109/TVT.2018.2876062 URL |
| [8] | LI Xiaofan, DONG Fangwei, ZHANG Sha, et al. A Survey on Deep Learning Techniques in Wireless Signal Recognition[J]. Wireless Communications and Mobile Computing, 2019, 179: 1-12. |
| [9] |
WALENCZYKOWSKA M, KAWALEC A. Type of Modulation Identification Using Wavelet Transform and Neural Network[J]. Bulletin of the Polish Academy of Sciences Technical Sciences, 2016, 64(1): 257-261.
doi: 10.1515/bpasts-2016-0028 URL |
| [10] |
SWAMI A, SADLER B M. Hierarchical Digital Modulation Classification Using Cumulants[J]. IEEE Transactions on Communications, 2000, 48(3): 416-429.
doi: 10.1109/26.837045 URL |
| [11] | VUCIC D, VUKOTIC S, ERIC M. Cyclic Spectral Analysis of OFDM/OQAM Signals[J]. AEU-International Journal of Electronics and Communications, 2017, 73: 139-143. |
| [12] |
OTTER D W, MEDINA J R, KALITA J K. A Survey of the Usages of Deep Learning for Natural Language Processing[J]. IEEE Transactions on Neural Networks and Learning Systems, 2021, 32(2): 604-624.
doi: 10.1109/TNNLS.5962385 URL |
| [13] |
KHAN M, SAJJAD M, KWON S. Clustering-Based Speech Emotion Recognition by Incorporating Learned Features and Deep BiLSTM[J]. IEEE Access, 2020, 8: 79861-79875.
doi: 10.1109/Access.6287639 URL |
| [14] | O’SHEA T J, CORGAN J, CLANCY T C. Convolutional Radio Modulation Recognition Networks[C]// Springer. International Conference on Engineering Applications of Neural Networks. Berlin:Springer, 2016: 213-226. |
| [15] | WEST N E, O'SHEA T. Deep Architectures for Modulation Recognition[C]// IEEE. 2017 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN). New York: IEEE, 2017: 1-7. |
| [16] |
RAJENDRAN S, MEERT W, GIUSTINIANO D, et al. Deep Learning Models for Wireless Signal Classification with Distributed Low-Cost Spectrum Sensors[J]. IEEE Transactions on Cognitive Communications and Networking, 2018, 4(3): 433-445.
doi: 10.1109/TCCN.2018.2835460 URL |
| [17] | PERENDA E, RAJENDRAN S, POLLIN S. Automatic Modulation Classification Using Parallel Fusion of Convolutional Neural Networks[C]// BalkanCom. Third International Balkan Conference on Communications and Networking. Istanbul: BalkanCom, 2019: 469-478. |
| [18] |
XU Jialang, LUO Chunbo, PARR G, et al. A Spatiotemporal Multi-Channel Learning Framework for Automatic Modulation Recognition[J]. IEEE Wireless Communications Letters, 2020, 9(10): 1629-1632.
doi: 10.1109/LWC.5962382 URL |
| [19] |
LIAO Kaisheng, ZHAO Yaodong, GU Jie, et al. Sequential Convolutional Recurrent Neural Networks for Fast Automatic Modulation Classification[J]. IEEE Access, 2021, 9: 27182-27188.
doi: 10.1109/Access.6287639 URL |
| [20] |
HUYNH-THE T, PHAM Q V, NGUYEN T V, et al. Automatic Modulation Classification: A Deep Architecture Survey[J]. IEEE Access, 2021, 9: 142950-142971.
doi: 10.1109/ACCESS.2021.3120419 URL |
| [21] | LIU Minhao, ZENG Ailing, LAI Q, et al. Time Series is a Special Sequence: Forecasting with Sample Convolution and Interaction[EB/OL]. (2021-10-19)[2022-11-05]. https://www.xueshufan.com/publication/3171665133. |
| [22] | O'SHEA T J, WEST N. Radio Machine Learning Dataset Generation with GNU Radio[EB/OL]. (2016-09-06)[2022-11-05]. https://pubs.gnuradio.org/index.php/grcon/article/view/11. |
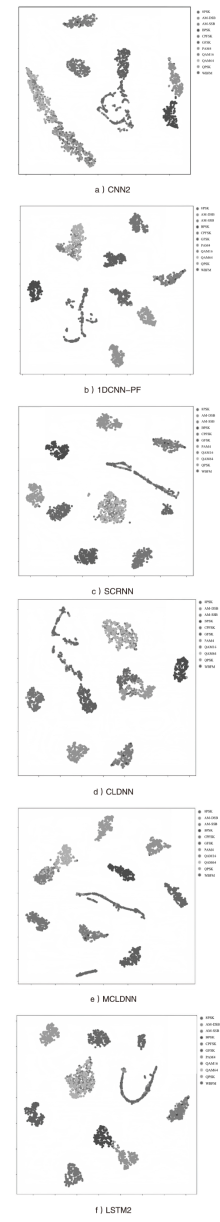
| [23] | LAURENS V D M, GEOFFREY H. Visualizing Data Using t-SNE[J]. Journal of Machine Learning Research, 2008, 9(11): 2579-2625. |
| [1] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| [2] | XU Zhanyang, CHENG Luofei, CHENG Jianchun, XU Xiaolong. A Scheme of Optimizing Deep Learning Model Using Bi-ADMM [J]. Netinfo Security, 2023, 23(2): 54-63. |
| [3] | CHEN Depeng, LIU Xiao, CUI Jie, ZHONG Hong. Research on Membership Inference Attack Method Based on Double Threshold Function [J]. Netinfo Security, 2023, 23(2): 64-75. |
| [4] | JIA Fan, KANG Shuya, JIANG Weiqiang, WANG Guangtao. Vulnerability Similarity Algorithm Evaluation Based on NLP and Feature Fusion [J]. Netinfo Security, 2023, 23(1): 18-27. |
| [5] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [6] | ZHENG Yaohao, WANG Liming, YANG Jing. A Defense Method against Adversarial Attacks Based on Neural Architecture Search [J]. Netinfo Security, 2022, 22(3): 70-77. |
| [7] | GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder [J]. Netinfo Security, 2022, 22(12): 7-15. |
| [8] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [9] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [10] | ZHU Xintong, TANG Yunqi, GENG Pengzhi. Detection Algorithm of Tamper and Deepfake Image Based on Feature Fusion [J]. Netinfo Security, 2021, 21(8): 70-81. |
| [11] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [12] | MA Rui, CAI Manchun, PENG Shufan. A Deep Forgery Video Detection Model Based on Improved Xception Network [J]. Netinfo Security, 2021, 21(12): 109-117. |
| [13] | PAN Xiaoqin, DU Yanhui. Forged Voice Identification Method Based on Feature Fusion and Multi-channel GRU [J]. Netinfo Security, 2021, 21(10): 1-7. |
| [14] | XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM [J]. Netinfo Security, 2021, 21(10): 41-47. |
| [15] | WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model [J]. Netinfo Security, 2020, 20(9): 6-11. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||