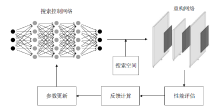
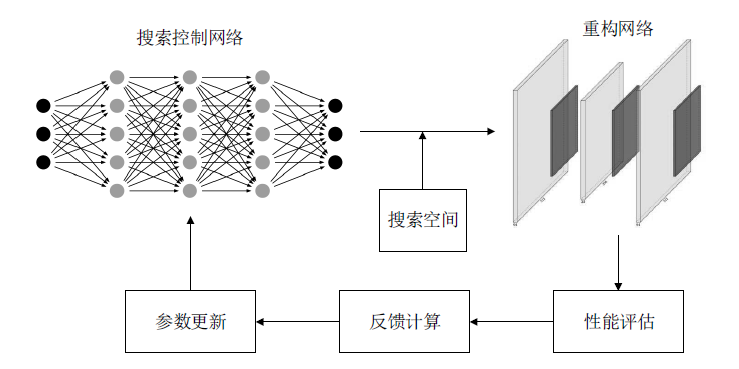
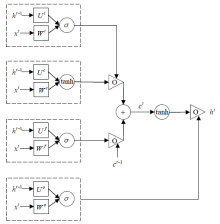
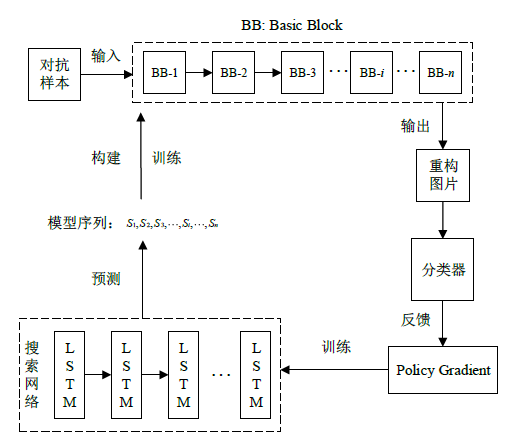
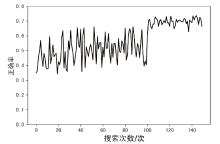
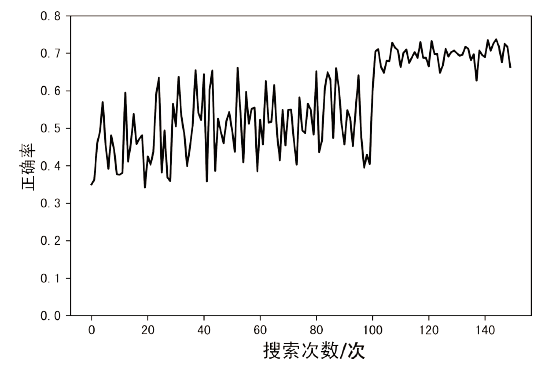
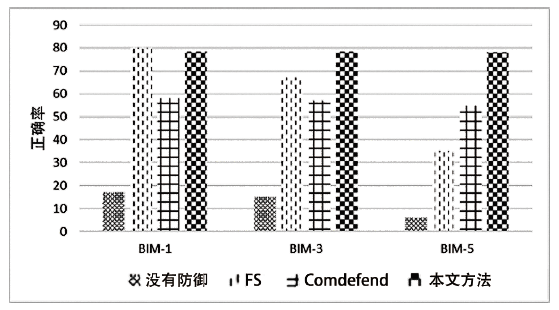
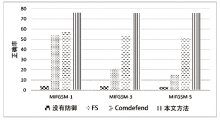
| [1] |
TRAMÈ R F, KURAKIN A, PAPERNOT N, et al. Ensemble Adversarial Training: Attacks and Defenses[EB/OL]. https://arxiv.org/abs/1705.07204, 2017-05-19.
|
| [2] |
LU Jiajun, ISSARANON T, FORSYTH D A. SafetyNet: Detecting and Rejecting Adversarial Examples Robustly [C]//IEEE. IEEE International Conference on Computer Vision, October 22-29, 2017, Venice, Italy. New York: IEEE, 2017: 446-454.
|
| [3] |
JIA Xiaojun, WEI Xingxing, CAO Xiaochun, et al. ComDefend: An Efficient Image Compression Model to Defend Adversarial Examples[C]//IEEE. IEEE Conference on Computer Vision and Pattern Recognition, June 16-20, 2019, Long Beach, CA, USA. New York: IEEE, 2019: 6084-6092.
|
| [4] |
SONG Yang, KIM T, NOWOZIN S, et al. PixelDefend: Leveraging Generative Models to Understand and Defend against Adversarial Examples[EB/OL]. https://arxiv.org/abs/1710.10766, 2017-10-30.
|
| [5] |
ZOPH B, LE Q V. Neural Architecture Search with Reinforcement Learning[EB/OL]. https://arxiv.org/abs/1611.01578, 2016-11-05.
|
| [6] |
ZOPH B, VASUDEVAN V, SHLENS J, et al. Learning Transferable Architectures for Scalable Image Recognition [C]//IEEE. IEEE Conference on Computer Vision and Pattern Recognition, June 18-22, 2018, Salt Lake City, UT, USA. New York: IEEE, 2018: 8697-8710.
|
| [7] |
GOODFELLOW I J, SHLENS J, SZEGEDY C. Explaining and Harnessing Adversarial Examples[EB/OL].https://arxiv.org/abs/1412.6572, 2014-12-20.
|
| [8] |
KURAKIN A, GOODFELLOW I J, BENGIO S. Adversarial Machine Learning at Scale[EB/OL]. , 2016-11-04.
|
| [9] |
DONG Yinpeng, LIAO Fangzhou, PANG Tianyu, et al. Boosting Adversarial Attacks with Momentum [C]//IEEE. 2018 IEEE Conference on Computer Vision and Pattern Recognition, June 18-22, 2018, Salt Lake City, UT, USA. New York: IEEE, 2018: 9185-9193.
|
| [10] |
PAPERNOT N, MCDANIEL P D, JHA S, et al. The Limitations of Deep Learning in Adversarial Settings [C]//IEEE. IEEE European Symposium on Security and Privacy, March 21-24, 2016, Saarbrücken, Germany. New York: IEEE, 2016: 372-387.
|
| [11] |
XU Weilin, EVANS D, QI Yanjun. Feature Squeezing: Detecting Adversarial Examples in Deep Neural Networks[EB/OL]. https://arxiv.org/abs/1704.01155, 2017-04-04.
|
| [12] |
WILLIAMS R J. Simple Statistical Gradient-following Algorithms for Connectionist Reinforcement Learning[J]. Mach Learn, 1992(8):229-256.
|
| [13] |
HE Kaiming, KRIZHEVSKY A N V, HINTON G. Cifar-10[EB/OL]. http://www.cs.toronto.edu/kriz/cifar.html, 2021-08-09.
|
| [14] |
HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition [C]//IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition, June 27-30, 2016, Las Vegas, NV, USA. New York: IEEE, 2016: 770-778.
|
| [15] |
DENG Jia, DONG Wei, SOCHER R, et al. ImageNet: A Large-scale Hierarchical Image Database [C]//IEEE. 2009 IEEE Computer Society Conference on Computer Vision and Pattern Recognition, June 20-25, 2009, Miami, Florida, USA. New York: IEEE, 2009: 248-255.
|
| [16] |
SZEGEDY C, VANHOUCKE V, IOFFE S, et al. Rethinking the Inception Architecture for Computer Vision [C]//IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition, June 27-30, 2016, Las Vegas, NV, USA. New York: IEEE, 2016: 2818-2826.
|
 ), YANG Jing1
), YANG Jing1