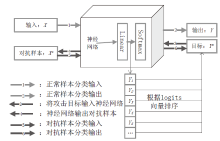
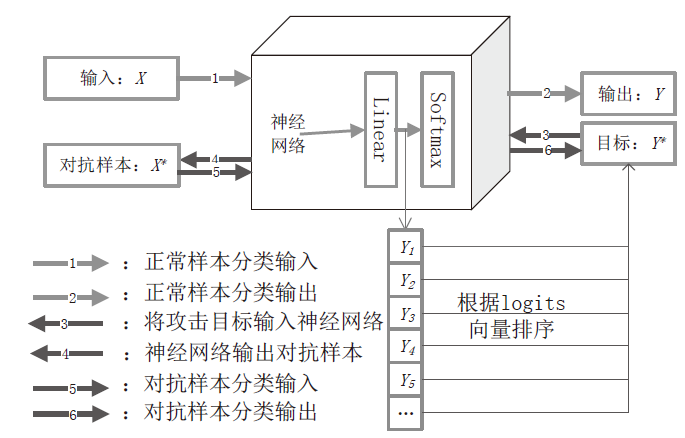
| [1] |
ZHANG Shun, GONG Yihong, WANG Jinjun. The Development of Convolutional Neural Network and its Applications in Computer Vision[J]. Journal of Computer Science, 2019, 42(3):453-482.
|
|
张顺, 龚怡宏, 王进军. 深度卷积神经网络的发展及其在计算机视觉领域的应用[J]. 计算机学报, 2019, 42(3):453-482.
|
| [2] |
JAWAD H A. Handwritten Arabic Digit Recognition Using Convolutional Neural Network[J]. International Journal of Communication Networks and Information Security, 2020, 12(3):411-416.
|
| [3] |
TAIGMAN Y, MING Y, RANZATO M, et al. DeepFace: Closing the Gap to Human-level Performance in Face Verification [C]//IEEE. IEEE Conference on Computer Vision & Pattern Recognition, June 23-28, 2014, Columbus, OH, USA. New York: IEEE, 2014: 1701-1708.
|
| [4] |
XI Xuefeng, ZHOU Guodong. Research on Deep Learning for Natural Language Processing[J] Journal of Aautomation, 2016, 42(10):1445-1465
|
|
奚雪峰, 周国栋. 面向自然语言处理的深度学习研究[J]. 自动化学报, 2016, 42(10):1445-1465.
|
| [5] |
WANG Xiaoguo, YI Zhichao, WU Hao. Research and Improvement of Internet Financial Anti-fraud Rules Based on Information Gain and Support[J]. Journal of Physics: Conference Series, 2018 (1):1-7.
|
| [6] |
GEORG C, FALKO D, RICHARD A, et al. Network Attack Detection and Defense-manifesto of the Dagstuhl Perspective Workshop[J]. Computer Science Research and Development, 2009, 23(1):15-25.
doi: 10.1007/s00450-009-0055-y
URL
|
| [7] |
WANG Jinqiang, HUANG Hang, ZHI Peng, et al. Review of Development and Key Ttechnologies in Aautomatic Ariving[J]. Application of Electronic Technology, 2019, 45(6):28-36.
|
|
王金强, 黄航, 郅朋, 等. 自动驾驶发展与关键技术综述[J]. 电子技术应用, 2019, 45(6):28-36.
|
| [8] |
ZHANG Sisi, ZUO Xin, LIU Jianwei. Confrontation Sample Problem in Deep Learning[J]. Journal of Computer Science, 2019, 42(8):1886-1904.
|
|
张思思, 左信, 刘建伟. 深度学习中的对抗样本问题[J]. 计算机学报, 2019, 42(8):1886-1904.
|
| [9] |
WANG Shuwei, ZHOU Gang, JU Xinghai, et al. Overview of Malware Countermeasure Sample Generation Based on Network[J] Journal of University of Information Engineering, 2019, 20(5):616-621.
|
|
王树伟, 周刚, 巨星海, 等. 基于生成对抗网络的恶意软件对抗样本生成综述[J]. 信息工程大学学报, 2019, 20(5):616-621.
|
| [10] |
LIU Hui, ZHAO Bo, GUO Jiabao, et al. Overview of Counter Attack against Deep Learning[J] Journal of Cryptography, 2021, 8(2):202-214.
|
|
刘会, 赵波, 郭嘉宝, 等. 针对深度学习的对抗攻击综述[J]. 密码学报, 2021, 8(2):202-214.
|
| [11] |
IAN J, JONATHON S, CHRISTIAN S. Explaining and Harnessing Adversarial Examples[EB/OL]. http://arxiv.org/abs/1412.6572, 2021-08-02.
|
| [12] |
CHRISTIAN S, WOJCIECH Z, ILYA S, et al. Intriguing Properties of Neural Networks[EB/OL]. http://arxiv.org/abs/1312.6199, 2021-08-02.
|
| [13] |
MOOSAVIDEZFOOLI S, FAWZI A, FROSSARD P, et al. DeepFool: A Simple and Accurate Method to Fool Deep Neural Networks [C]// IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition, June 27-30, 2016, Las Vegas, NV, USA. New York: IEEE, 2016: 2574-2582.
|
| [14] |
PAPERNOT N, MCDANIEL P, JHA S, et al. The limitations of Deep Learning in Adversarial Settings [C]//IEEE. 2016 IEEE European Symposium on Security and Privacy, March 21-24, 2016, Saarbruecken, Germany. New York: IEEE, 2016: 372-387.
|
| [15] |
CARLINI N, WAGNER D. Towards Evaluating the Robustness of Neural Networks[C]//IEEE. 2017 IEEE Symposium on Security and Privacy, May 22-26, 2017, San Jose, CA, US. New York: IEEE, 2017: 39-57.
|
| [16] |
WIYATNO R, XU A. Maximal Jacobian-based Saliency Map Attack[EB/OL]. http://arxiv.org/abs/1808.07945, 2021-08-16.
|
| [17] |
COMBEY T, LOISON A, FAUCHER M, et al. Probabilistic Jacobian-based Saliency Maps Attacks[EB/OL]. https://arxiv.org/abs/2007.06032, 2021-08-18.
|
| [18] |
SU Jiawei, VARGAS D V, SAKURAI K. One Pixel Attack for Fooling Deep Neural Networks[J]. IEEE Transactions on Evolutionary Computation, 2019, 23(5):828-841.
doi: 10.1109/TEVC.4235
URL
|
 ), FU Wei
), FU Wei