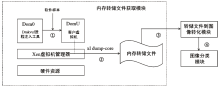
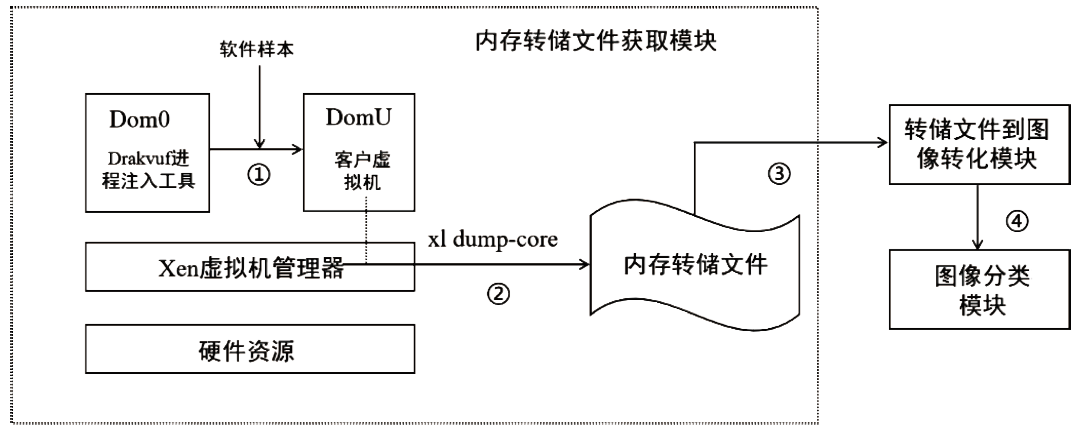
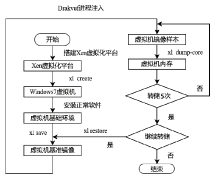
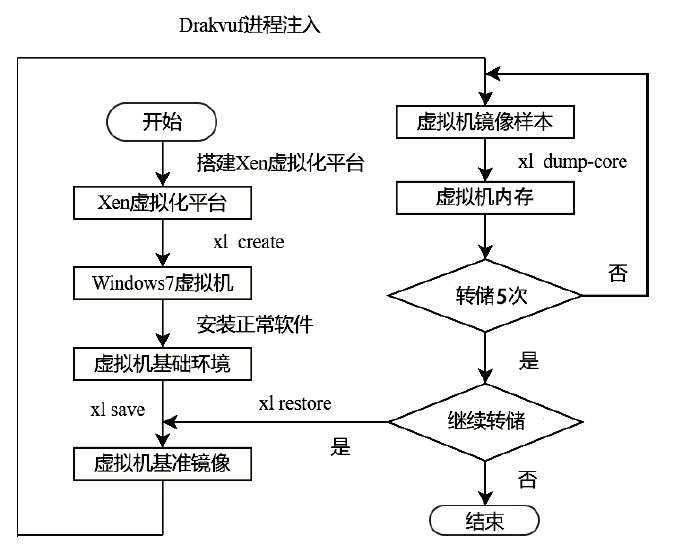
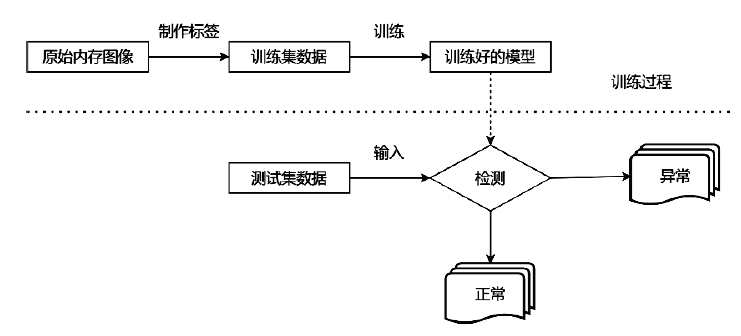
Netinfo Security ›› 2022, Vol. 22 ›› Issue (11): 62-67.doi: 10.3969/j.issn.1671-1122.2022.11.008
Previous Articles Next Articles
Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform
- 1. College of Cyber Science, Nankai University, Tianjin 300350, China
2. Tianjin Key Laboratory of Network and Data Security Technology, Tianjin 300350, China
-
Received:2022-07-10Online:2022-11-10Published:2022-11-16 -
Contact:ZHANG Jian E-mail:zhang.jian@nankai.edu.cn
CLC Number:
Cite this article
LIN Faxin, ZHANG Jian. Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform[J]. Netinfo Security, 2022, 22(11): 62-67.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.11.008
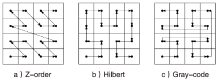
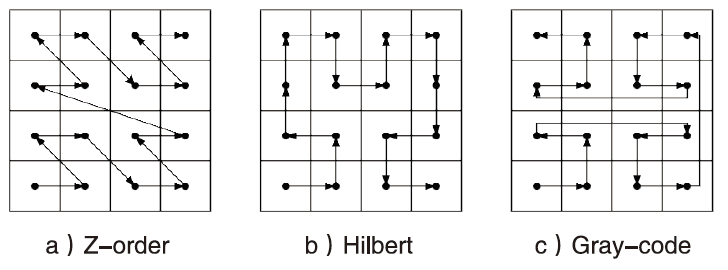
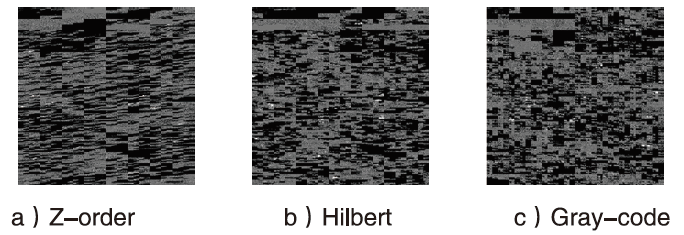
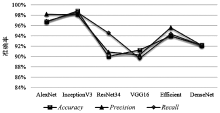
| Model | Hilbert | Z-order | Gray-code | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Accuracy | Precision | Recall | Accuracy | Precision | Recall | Accuracy | Precision | Recall | |
| AlexNet | 96.68% | 98.17% | 96.83% | 94.26% | 96.55% | 95.37% | 92.43% | 94.59% | 92.11% |
| InceptionV3 | 98.78% | 98.12% | 98.57% | 97.28% | 97.12% | 97.66% | 96.26% | 96.22% | 96.38% |
| ResNet34 | 90.03% | 90.87% | 94.57% | 89.68% | 90.17% | 88.25% | 88.16% | 89.18% | 88.09% |
| VGG16 | 91.25% | 90.29% | 89.66% | 88.31% | 87.64% | 89.42% | 90.17% | 90.33% | 90.59% |
| Efficient | 93.96% | 95.61% | 94.38% | 92.79% | 92.74% | 92.52% | 91.06% | 90.78% | 91.78% |
| DenseNet | 92.18% | 92.14% | 92.18% | 89.55% | 89.72% | 88.48% | 91.39% | 90.45% | 92.96% |
| [1] |
MANSOURI Y, BABAR M A. A Review of Edge Computing: Features and Resource Virtualization[J]. Journal of Parallel and Distributed Computing, 2021, 150: 155-183.
doi: 10.1016/j.jpdc.2020.12.015 URL |
| [2] | UEKI K, KOURAI K. Fine-Grained Autoscaling with In-VM Containers and VM Introspection[C]//IEEE. 2020 IEEE/ACM 13th International Conference on Utility and Cloud Computing (UCC). New York:IEEE, 2020: 155-164. |
| [3] | GARFINKEL T, ROSENBLUM M. A Virtual Machine Introspection Based Architecture for Intrusion Detection[EB/OL]. [2022-06-08]. |
| [4] | CONTI G, DEAN E, SINDA M, et al. Visual Reverse Engineering of Binary and Data Files[C]// Springer. International Workshop on Visualization for Computer Security. Heidelberg: Springer, 2008: 1-17. |
| [5] | NATARAJ L, KARTHIKEYAN S, JACOB G, et al. Malware Images: Visualization and Automatic Classification[C]// ACM. Proceedings of the 8th International Symposium on Visualization for Cyber Security. New York: ACM, 2011: 1-7. |
| [6] | LUO J S, LO D C T. Binary Malware Image Classification Using Machine Learning with Local Binary Pattern[C]// IEEE. 2017 IEEE International Conference on Big Data (Big Data). New York:IEEE, 2017: 4664-4667. |
| [7] | LE Q, BOYDELL O, MAC NAMEE M B, et al. Deep Learning at the Shallow End: Malware Classification for Non-Domain Experts[J]. Digital Investigation, 2018, 26: 118-126. |
| [8] | QIAO Yanchen, JIANG Qingshan, JIANG Zhenchao, et al. A Multi-Channel Visualization Method for Malware Classification Based on Deep Learning[C]//IEEE. 2019 18th IEEE International Conference On Trust, Security And Privacy in Computing and Communications/13th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE). New York:IEEE, 2019: 757-762. |
| [9] |
PINHERO A, ANUPAMA M L, VINOD P, et al. Malware Detection Employed by Visualization and Deep Neural Network[J]. Computers & Security, 2021, 105: 102247.
doi: 10.1016/j.cose.2021.102247 URL |
| [10] |
LIN W C, YEH Y R. Efficient Malware Classification by Binary Sequences with One-Dimensional Convolutional Neural Networks[J]. Mathematics, 2022, 10(4): 608.
doi: 10.3390/math10040608 URL |
| [11] |
O’SHAUGHNESSY S, SHERIDAN S. Image-Based Malware Classification Hybrid Framework Based on Space-Filling Curves[J]. Computers & Security, 2022, 116: 102660.
doi: 10.1016/j.cose.2022.102660 URL |
| [12] | O’SHAUGHNESSY S. Image-Based Malware Classification: A Space Filling Curve Approach[C]//IEEE. 2019 IEEE Symposium on Visualization for Cyber Security (VizSec). New York:IEEE, 2019: 1-10. |
| [13] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning[J]. Netinfo Security, 2020, 20(9): 92-96. |
| 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. | |
| [14] |
BASU K, KRISHNAMURTHY P, KHORRAMI F, et al. A Theoretical Study of Hardware Performance Counters-Based Malware Detection[J]. IEEE Transactions on Information Forensics and Security, 2019, 15: 512-525.
doi: 10.1109/TIFS.2019.2924549 URL |
| [15] | KUMAR R, PATI S, LAHIRI K. Darts: Performance-Counter Driven Sampling Using Binary Translators[C]//IEEE. 2017 IEEE International Symposium on Performance Analysis of Systems and Software(ISPASS). New York:IEEE, 2017: 131-132. |
| [16] | TRIPATHI S, GRIECO G, RAWAT S. Exniffer: Learning to Prioritize Crashes by Assessing the Exploitability from Memory Dump[C]//IEEE. 2017 24th Asia-Pacific Software Engineering Conference (APSEC). New York:IEEE, 2017: 239-248. |
| [1] | LIU Guangjie, DUAN Kun, ZHAI Jiangtao, QIN Jiayu. Mobile Traffic Application Recognition Based on Multi-Feature Fusion [J]. Netinfo Security, 2022, 22(7): 18-26. |
| [2] | YU Chengli, ZHANG Yang, JIA Shijie. Research on Data Security Threats and Protection of Key Technologies in Cloud Environment [J]. Netinfo Security, 2022, 22(7): 55-63. |
| [3] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [4] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [5] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [6] | GAO Changfeng, XIAO Yanhui, TIAN Huawei. Image Camera Fingerprint Extraction Algorithm Based on MPRNet [J]. Netinfo Security, 2022, 22(10): 15-23. |
| [7] | LIU Jiayin, LI Fujuan, MA Zhuo, XIA Lingling. Malware Classification Method Based on Multi-Scale Convolutional Neural Network [J]. Netinfo Security, 2022, 22(10): 31-38. |
| [8] | LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm [J]. Netinfo Security, 2021, 21(9): 59-66. |
| [9] | YOU Wenting, ZHANG Leyou, YE Yadi, LI Hui. Privacy-preserving Attribute-based Dynamic Broadcast Encryption Mechanism in Multi-user Communication System [J]. Netinfo Security, 2021, 21(4): 21-30. |
| [10] | XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM [J]. Netinfo Security, 2021, 21(10): 41-47. |
| [11] | MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model [J]. Netinfo Security, 2021, 21(10): 69-75. |
| [12] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [13] | LIU Jing, ZHANG Xueqian, LIU Quanming. Research on Captcha Recognition of Lightweight Convolutional Neural Network with Gabor [J]. Netinfo Security, 2020, 20(7): 77-84. |
| [14] | BIAN Manlin, WANG Liming. Analysis and Research on Vulnerability of Docker Container Isolation in Cloud Environment [J]. Netinfo Security, 2020, 20(7): 85-95. |
| [15] | RAN Jinpeng, WANG Xiang, ZHAO Shanghong, GAO Hanghang. Virtual SDN Network Embedding Algorithm Based on Fruit Fly Optimization [J]. Netinfo Security, 2020, 20(6): 65-74. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||