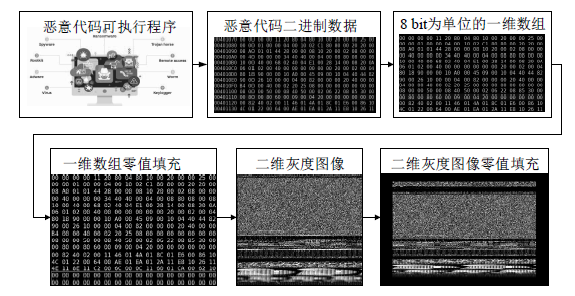
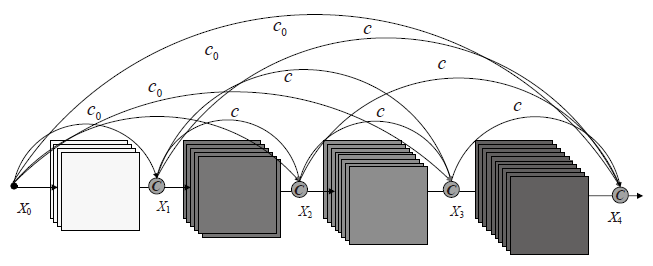
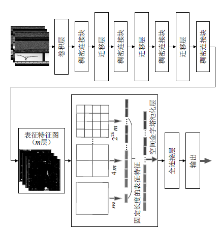
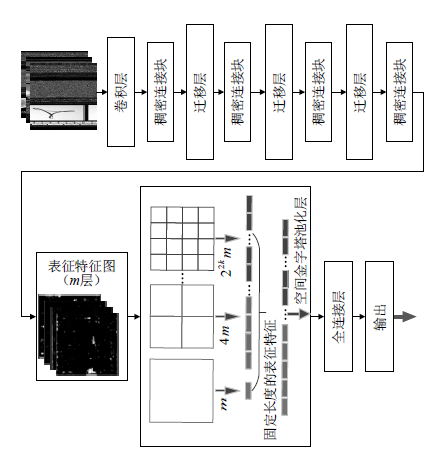
| [1] |
CNCERT/CC. Analysis Report on China's Internet Network Security Monitoring Data in the First Halfof 2021[EB/OL]. (2021-07-31)[2022-06-15]. https://www.cert.org.cn/publish/main/upload/File/first-half%20%20year%20cyberseurity%20report%202021.pdf.
|
|
国家计算机网络应急技术处理协调中心. 2021年上半年我国互联网网络安全监测数据分析报告[EB/OL]. (2021-07-31)[2022-06-15]. https://www.cert.org.cn/publish/main/upload/File/first-half%20%20year%20cyberseurity%20report%202021.pdf.
|
| [2] |
KIM D, SHIN G, HAN M. Analysis of Feature Importance and Interpretation for Malware Classification[J]. Computers, Materials & Continua, 2020, 65(3): 1891-1904.
|
| [3] |
LIU Liu, WANG Baosheng, YU Bo, et al. Automatic Malware Classification and New Malware Detection Using Machine Learning[J]. Frontiers of Information Technology & Electronic Engineering, 2016, 18(9): 1336-1347.
|
| [4] |
RAFF E, SYLVESTER J, NICHOLAS C. Learning the PE Header, Malware Detection with Minimal Domain Knowledge[C]// ACM. The 10th ACM Workshop on Artificial Intelligence and Security(AISec’17). New York: ACM, 2017: 121-132.
|
| [5] |
DAI Yusheng, LI Hui, QIAN Yekui, et al. SMASH: A Malware Detection Method Based on Multi-Feature Ensemble Learning[J]. IEEE Access, 2019, 7: 112588-112597.
|
| [6] |
FUJINO A, MURAKAMI J, MORI T. Discovering Similar Malware Samples Using Api Call Topics[C]// IEEE. 12th Annual IEEE Consumer Communications and Networking Conference(CCNC). New York: IEEE, 2015: 1-8.
|
| [7] |
LIM H, YAMAGUCHI Y, SHIMADA H, et al. Malware Classification Method Based on Sequence of Traffic Flow[C]// ACM. International Conference on Information Systems Security and Privacy(ICISSP). New York: ACM, 2015: 1-8.
|
| [8] |
TOBIYAMA S, YAMAGUCHIi Y, SHIMADA H, et al. Malware Detection with Deep Neural Network Using Process Behavior[C]// IEEE. 40th IEEE Annual Computer Software and Applications Conference. New York: IEEE, 2016: 577-582.
|
| [9] |
NATARAJ L, KARTHIKEYAN S, JACOB G, et al. Malware Images: Visualization and Automatic Classification[C]// ACM. The 8th International Symposium on Visualization for Cyber Security. New York: ACM, 2011: 1-7.
|
| [10] |
HAN Xiaoguang, QU Wu, YAO Xuanxia, et al. Research on Malicious Code Variants Detection Based on Texture Fingerprint[J]. Journal on Communications, 2014, 35(8): 125-136.
|
| [11] |
GUPTA S, BANSAL P, KUMAR S. ULBP-RF: A Hybrid Approach for Malware Image Classification[C]// IEEE. 2018 International Conference on Parallel, Distributed and Grid Computing(PDGC). New York: ACM, 2018: 115-119.
|
| [12] |
ZHAO Yuntao, XU Chunyu, BO Bo, et al. Maldeep: A Deep Learning Classification Framework Against Malware Variants Based on Texture Visualization[EB/OL]. (2019-04-01)[2022-06-15].https://doi.org/10.1155/2019/4895984.
|
| [13] |
YAKURA H, SHINOZAKI S, NISHIMURA R, et al. Malware Analysis of Imaged Binary Samples by Convolutional Neural Network with Attention Mechanism[C]// ACM. 8th ACM Conference on Data and Application Security and Privacy. New York: ACM, 2018: 127-134.
|
| [14] |
CHEN Bingcai, REN Zhongru, YU Chao, et al. Adversarial Examples for CNN-Based Malware Detectors[J]. IEEE Access, 2019, 7: 54360-54371.
|
| [15] |
FAN Zhipeng, LI Jun, LIU Yuqiang, et al. Classification of Malware Based on Gray Texture Fingerprint[J]. Science Technology and Engineering, 2020, 20(29): 12014-12020.
|
|
范志鹏, 李军, 刘宇强, 等. 基于灰度纹理指纹的恶意代码分类[J]. 科学技术与工程, 2020, 20(29):12014-12020.
|
| [16] |
HUANG Gao, LIU Zhuang, VAN DER MAATEN L, et al. Densely Connected Convolutional Networks[C]// IEEE. IEEE Conference on Computer Vision and Pattern Recognition(CVPR). New York: IEEE, 2017: 4700-4708.
|
| [17] |
RONEN R, RADU M, FEUERSTEIN C, et al. Microsoft Malware Classification Challenge[EB/OL]. (2018-02-22)[2022-07-18]. https://arxiv.org/abs/1802.10135.
|
| [18] |
TAN Ruhan, ZUO Liming, LIU Ergen, et al. Malicious Code Detection Based on Image Feature Fusion[J]. Netinfo Security, 2021, 21(10): 90-95.
|
|
谭茹涵, 左黎明, 刘二根, 等. 基于图像特征融合的恶意代码检测[J]. 信息网络安全, 2021, 21(10): 91-95.
|
| [19] |
QIAO Yanchen, JIANG Qingshan, GU Liang, et al. Malware Classification Method Based on Word Vector of Assembly Instruction and CNN[J]. Netinfo Security, 2019, 19(4): 20-28.
|
|
乔延臣, 姜青山, 古亮, 等. 基于汇编指令词向量与卷积神经网络的恶意代码分类方法研究[J]. 信息网络安全, 2019, 19(4):20-28.
|
| [20] |
CHEN Xiaohan, WEI Shuning, QIN Zhengze. Malware Family Classification Based on Deep Learning Visualization[J]. Computer Engineering and Applications, 2021, 57(22): 131-138.
|
|
陈小寒, 魏书宁, 覃正泽. 基于深度学习可视化的恶意软件家族分类[J]. 计算机工程与应用, 2021, 57(22):131-138.
|
 ), MA Zhuo1,2,3, XIA Lingling1,2,3
), MA Zhuo1,2,3, XIA Lingling1,2,3