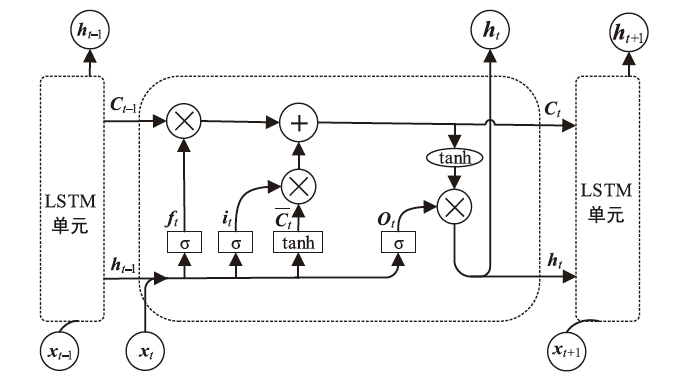
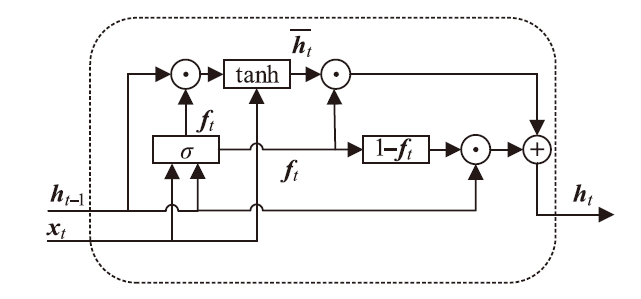
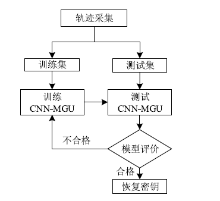
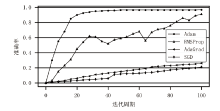
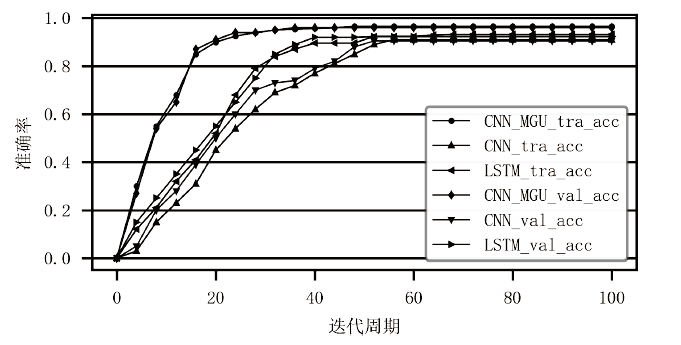
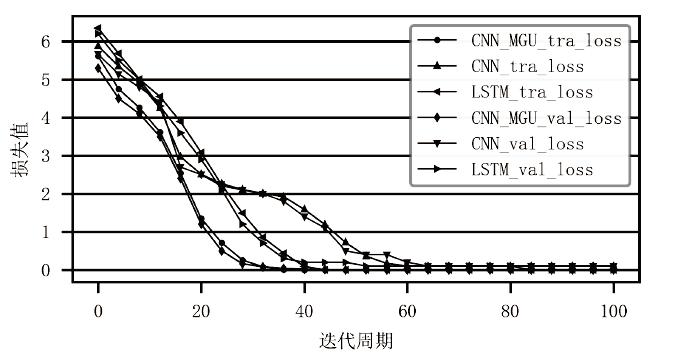
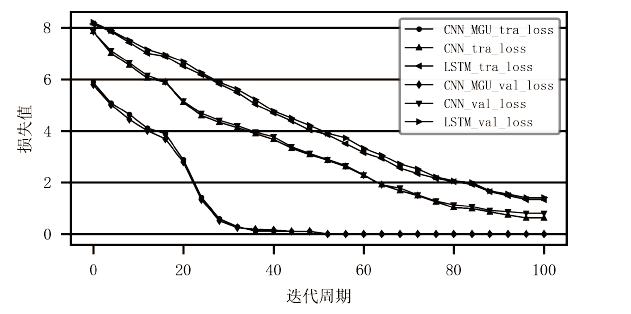
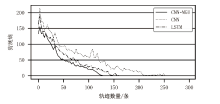
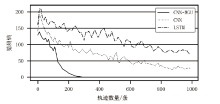
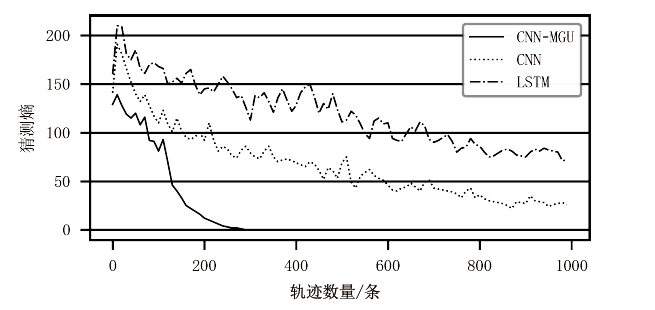
Netinfo Security ›› 2022, Vol. 22 ›› Issue (8): 55-63.doi: 10.3969/j.issn.1671-1122.2022.08.007
Previous Articles Next Articles
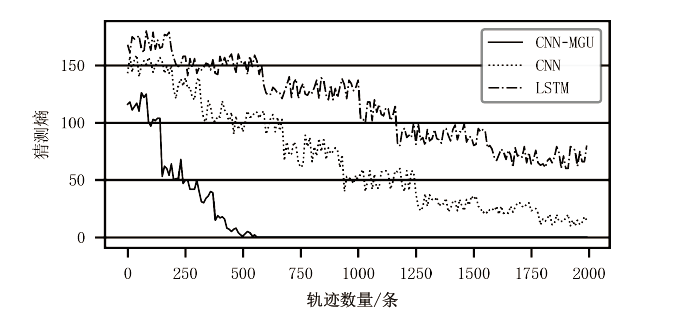
Research on Side Channel Attack Based on CNN-MGU
GAO Bo1,2( ), CHEN Lin1, YAN Yingjian1
), CHEN Lin1, YAN Yingjian1
- 1. Information Engineering University, Zhengzhou 450001, China
2. 92957 Troops of PLA, Zhoushan 316000, China
-
Received:2022-03-18Online:2022-08-10Published:2022-09-15 -
Contact:GAO Bo E-mail:xxgcdxgaobo@126.com
CLC Number:
Cite this article
GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU[J]. Netinfo Security, 2022, 22(8): 55-63.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.08.007
| [1] | KOCHER P, JAFFE J, JUN B. Differential Power Analysis[C]//Springer. Annual International Cryptology Conference. Heidelberg: Springer, 1999: 388-397. |
| [2] | KOCHER P C. Timing Attacks on Implementations of Diffie-Hellman, RSA, DES, and other Systems[C]//Springer. 16th Annual International Cryptology Conference. Heidelberg: Springer, 1996: 104-113. |
| [3] | MARTINASEK Z, ZEMAN V. Innovative Method of the Power Analysis[J]. Radio Engineering, 2013, 22(2): 586-594. |
| [4] | MAGHREBI H, PORTIGLIATTI T, PROUFF E. Breaking Cryptographic Implementations Using Deep Learning Techniques in Security, Privacy, and Applied Cryptography Engineering [C]//Springer. Security, Privacy, and Applied Cryptography Engineering (SPACE 2016). Heidelberg: Springer, 2016: 3-26. |
| [5] | CAGLI E, DUMAS C, PROUFF E. Convolutional Neural Networks with Data Augmentation against Jitter-Based Countermeasures[C]//Springer. 19th International Conference (CHES 2017), Heidelberg: Springer, 2017: 45-68. |
| [6] |
SAMIOTIS I P. Side-Channel Attacks Using Convolutional Neural Networks: A Study on the Performance of Convolutional Neural Networks on Side-Channel Data[J]. Frontiers in Artificial Intelligence, 2018, 3(1): 73-88.
doi: 10.3389/frai.2020.00073 URL |
| [7] |
WANG Kai, YAN Yingjian, GUO Pengfei, et al. Research on Power Analysis Attack Based on Improved Residual Network and Data Augmentation Technology[J]. Journal of Cryptologic Research, 2020, 7(4): 551-564.
doi: 10.13868/j.cnki.jcr.000389 |
|
王恺, 严迎建, 郭朋飞, 等. 基于改进残差网络和数据增强技术的能量分析攻击研究[J]. 密码学报, 2020, 7(4): 551-564.
doi: 10.13868/j.cnki.jcr.000389 |
|
| [8] | CHEN Ping, WANG Ping, DONG Gaofeng, et al. SincNet-Based Side Channel Attack[J]. Journal of Cryptography, 2020, 7(5): 583-594. |
|
陈平, 汪平, 董高峰, 等. 基于SincNet的侧信道攻击[J]. 密码学报, 2020, 7(5): 583-594.
doi: 10.13868/j.cnki.jcr.000391 |
|
| [9] | WANG Junnian, ZHU Bin, YU Wenxin, et al. Side Channel Analysis Based on Deep Learning LSTM[J]. Journal of Computer Engineering, 2021, 47(10): 140-146. |
| 王俊年, 朱斌, 于文新, 等. 基于深度学习LSTM的侧信道分析[J]. 计算机工程, 2021, 47(10): 140-146. | |
| [10] | WANG Ping, ZHENG Mengce, NAN Jiehui, et al. A Novel Method for Profiling Side Channel Attacks against Imbalanced Data[J]. Journal of Cryptologic Research, 2021, 8(4): 549-559. |
| 汪平, 郑梦策, 南杰慧, 等. 一种针对侧信道建模攻击中数据不平衡的新方法[J]. 密码学报, 2021, 8(4): 549-559. | |
| [11] | DUAN Xiaoyi, LI You, LINGHU Yunxing, et al. Research on the Method of Side Channel Attack Based on RF Algorithm[J]. Netinfo Security, 2022, 22(1): 19-26. |
| 段晓毅, 李邮, 令狐韫行, 等. 基于RF算法的侧信道攻击方法研究[J]. 信息网络安全, 2022, 22(1): 19-26. | |
| [12] | CAO Jiahua, WU Zhen, WANG Yi, et al. Side Channel Attack of S-Box Power Randomization Based on CNN-BPR[J]. Journal of Chengdu University of Information Technology, 2022, 37(1): 16-20. |
| 曹家华, 吴震, 王燚, 等. 基于CNN-BPR的S-Box功耗随机化侧信道攻击[J]. 成都信息工程大学学报, 2022, 37(1): 16-20. | |
| [13] | ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, et al. Insider Threat Detection Model Based on LSTM-Attention[J]. Netinfo Security, 2022, 22(2): 1-10. |
| 张光华, 闫风如, 张冬雯, 等. 基于LSTM-Attention的内部威胁检测模型[J]. 信息网络安全, 2022, 22(2): 1-10. | |
| [14] | XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM[J]. Netinfo Security, 2021, 21(10): 41-47. |
| 徐国天, 盛振威. 基于融合CNN与LSTM的DGA恶意域名检测方法[J]. 信息网络安全, 2021, 21(10): 41-47. | |
| [15] | ZHOU Guobing, WU Jianxin, ZHANG Chenlin, et al. Minimal Gated Unit for Recurrent Neural Networks[J]. International Journal of Automation & Computing, 2016(13): 226-234. |
| [16] | STANDAERT F X, MALKIN T G, YUNG M. A Unified Framework for the Analysis of Side-Channel Key Recovery Attacks[C]//Springer. 28th Annual International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2009), Heidelberg: Springer, 2009: 443-461. |
| [17] | BENADJILA R, PROUFF E, STRULLU R, et al. Deep Learning for Side-Channel Analysis and Introduction to ASCAD Database[J]. Journal of Cryptographic Engineering, 2020(10): 163-188. |
| [18] | WANG Huanyu, BRISFORS M, FORSMARK S, et al. How Diversity Affects Deep-Learning Side-Channel Attacks[C]//IEEE. 2019 IEEE Nordic Circuits and Systems Conference (NORCAS): NORCHIP and International Symposium of System-on-Chip (SoC). New York: IEEE, 2019:1-16. |
| [1] | HONG Sheng, LI Lei, YUAN Yidong, GAO Xinyan. Research on Cooperative Security Technology of Side Channel in Processor Microarchitecture Storage System [J]. Netinfo Security, 2022, 22(6): 26-37. |
| [2] | ZHENG Yaohao, WANG Liming, YANG Jing. A Defense Method against Adversarial Attacks Based on Neural Architecture Search [J]. Netinfo Security, 2022, 23(3): 70-77. |
| [3] | DUAN Xiaoyi, LI You, LINGHU Yunxing, HU Ronglei. Research on the Method of Side Channel Attack Based on RF Algorithm [J]. Netinfo Security, 2022, 22(1): 19-26. |
| [4] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [5] | ZHU Xintong, TANG Yunqi, GENG Pengzhi. Detection Algorithm of Tamper and Deepfake Image Based on Feature Fusion [J]. Netinfo Security, 2021, 21(8): 70-81. |
| [6] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [7] | MA Rui, CAI Manchun, PENG Shufan. A Deep Forgery Video Detection Model Based on Improved Xception Network [J]. Netinfo Security, 2021, 21(12): 109-117. |
| [8] | PAN Xiaoqin, DU Yanhui. Forged Voice Identification Method Based on Feature Fusion and Multi-channel GRU [J]. Netinfo Security, 2021, 21(10): 1-7. |
| [9] | YANG Ming, ZHANG Jian. Static Detection Model of Malware Based on Image Recognition [J]. Netinfo Security, 2021, 21(10): 25-32. |
| [10] | XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM [J]. Netinfo Security, 2021, 21(10): 41-47. |
| [11] | WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model [J]. Netinfo Security, 2020, 20(9): 6-11. |
| [12] | WANG Wenhua, HAO Xin, LIU Yan, WANG Yang. The Safety Evaluation and Defense Reinforcement of the AI System [J]. Netinfo Security, 2020, 20(9): 87-91. |
| [13] | ZHANG Leihua, HUANG Jin, ZHANG Tao, WANG Shengyu. Portrait Intelligent Analysis Application and Algorithm Optimization in Video Investigation [J]. Netinfo Security, 2020, 20(5): 88-93. |
| [14] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [15] | BI Xinliang, YANG Haibin, YANG Xiaoyuan, HUANG Siyuan. Generative Steganography Scheme Based on StarGAN [J]. Netinfo Security, 2020, 20(12): 64-71. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||