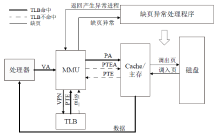
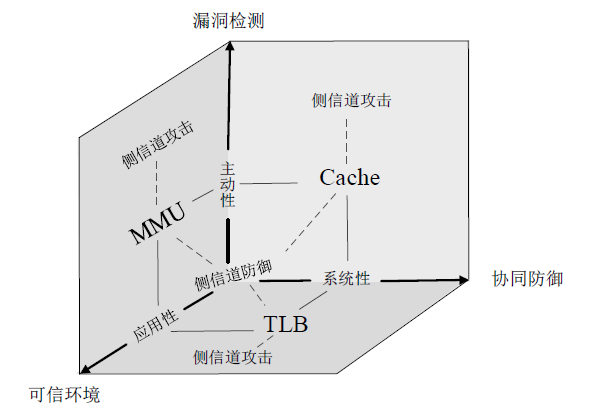
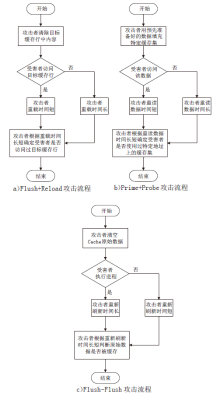
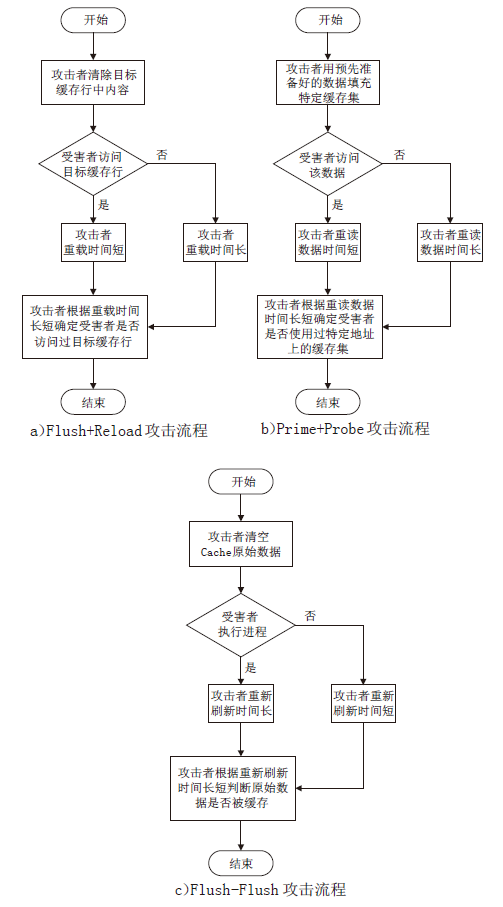
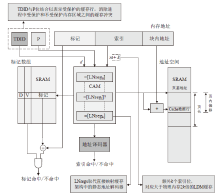
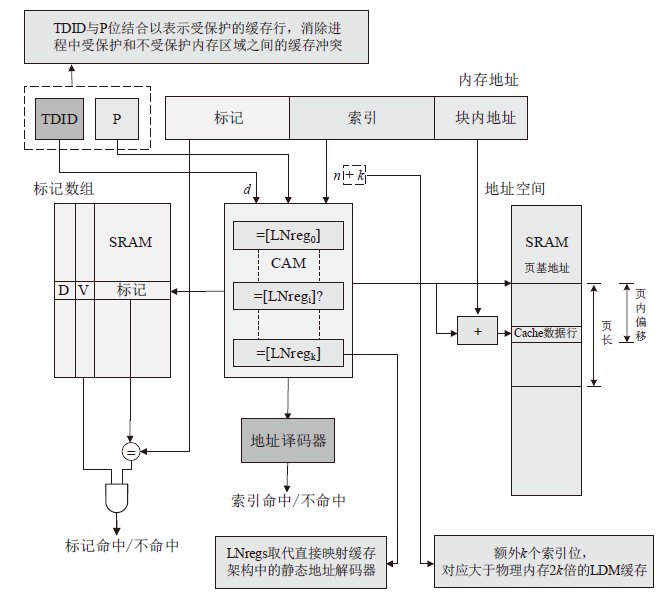
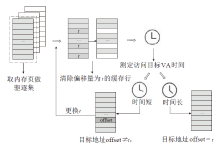
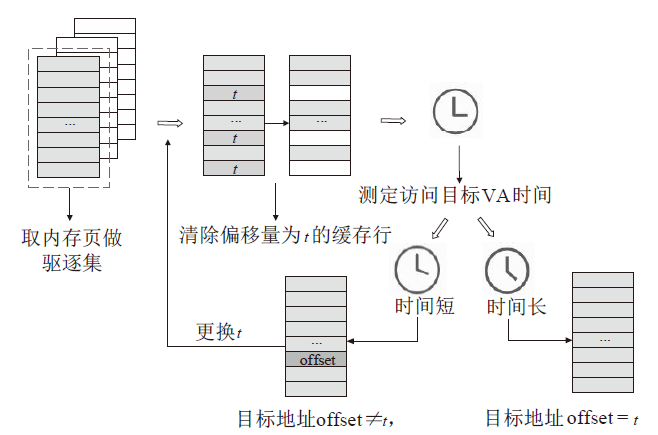
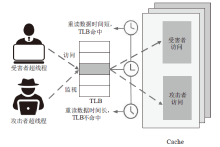
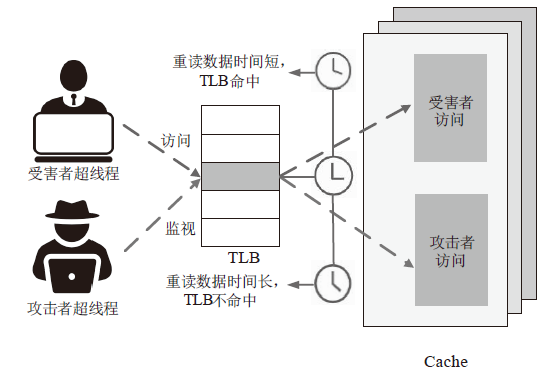
| [1] |
KOCHER P, HORN J, FOGH A, et al. Spectre Attacks: Exploiting Speculative Execution[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York:IEEE, 2019: 1-19.
|
| [2] |
LIPP M, SCHWARZ M, GRUSS D, et al. Meltdown: Reading Kernel Memory from User Space[C]// USENIX. 27th USENIX Security Symposium. Berkeley: USENIX, 2018: 973-990.
|
| [3] |
QIN Leihua, WU Fei, MO Zhengkun. Principle of Computer Composition[M]. Beijing: Tsinghua University Publishing House, 2011.
|
|
秦磊华, 吴非, 莫正坤. 计算机组成原理[M]. 北京: 清华大学出版社, 2011.
|
| [4] |
WANG Chong, WEI Shuai, ZHANG Fan, et al. A Survey of Cache-Based Side Channel Countermeasure[J]. Journal of Computer Research and Development, 2021, 58(4): 794-810.
|
|
王崇, 魏帅, 张帆, 等. 缓存侧信道防御研究综述[J]. 计算机研究与发展, 2021, 58(4): 794-810.
|
| [5] |
YAROM Y, FALKNER K. Flush+Reload: A High Resolution, Low Noise, L3 Caches-Channel Attack[C]// USENIX. 23rd USENIX Security Symposium. Berkeley: USENIX, 2014: 719-732.
|
| [6] |
RISTENPART T, TROMER E, SHACHAM H, et al. Hey, You, Get off of My Cloud: Exploring Information Leakage in Third-Party Compute Clouds[C]// ACM. 16th ACM Conference on Computer and Communications Security. New York: ACM, 2009: 199-212.
|
| [7] |
GRUSS D, MAURICE C, WAGNER K, et al. Flush+Flush: A Fast and Stealthy Cache Attack[C]// Springer. 2016 International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment. Heidelberg: Springer, 2016: 279-299.
|
| [8] |
GALLAIS J, KIZHVATOV I, TUNSTALL M. Improved Trace-Driven Cache-Collision Attacks against Embedded AES Implementations[C]// Springer. 2010 International Workshop on Information Security Applications. Heidelberg: Springer, 2010: 243-257.
|
| [9] |
CHEN Caisen, WANG Tao, GUO Shize, et al. Research on Trace Driven Data Cache Timing Attack against RSA[J]. Chinese Journal of Computers, 2014, 37(5): 1039-1051.
|
|
陈财森, 王韬, 郭世泽, 等. 针对RSA算法的踪迹驱动数据Cache计时攻击研究[J]. 计算机学报, 2014, 37(5): 1039-1051.
|
| [10] |
ZHU Jialiang, WEI Yongzhuang. Trace Driven Cache Attack on LBlock Algorithm[J]. Computer Engineering, 2015, 41(5): 153-158.
|
|
朱嘉良, 韦永壮. 针对LBlock算法的踪迹驱动Cache攻击[J]. 计算机工程, 2015, 41(5): 153-158.
|
| [11] |
LOU Xiaoxuan, ZHANG Fan, HUANG Jing, et al. Research on Trace Driven Cache Analysis on SM4[J]. Journal of Cryptologic Research, 2018, 5(4): 430-441.
|
| [12] |
WANG Zhenghong, LEE R B. New Cache Designs for Thwarting Software Cache-Based Side Channel Attacks[J]. ACM SIGARCH Computer Architecture News, 2007, 35(2): 494-505.
doi: 10.1145/1273440.1250723
URL
|
| [13] |
LIU Fangfei, WU Hao, LEE R B. Can Randomized Mapping Secure Instruction Caches from Side-Channel Attacks?[C]// ACM. 4th Workshop on Hardware and Architectural Support for Security and Privacy. New York: ACM, 2015: 41-48.
|
| [14] |
LIU Fangfei, WU Hao, MAI K, et al. Newcache: Secure Cache Architecture Thwarting Cache Side-Channel Attacks[J]. IEEE Micro, 2016, 36(5): 8-16.
|
| [15] |
DOMNITSER L, JALEEL A, LOEW J, et al. Non-Monopolizable Caches: Low-Complexity Mitigation of Cache Side Channel Attacks[J]. ACM Transactions on Architecture and Code Optimization, 2012, 8(4): 1-21.
|
| [16] |
WERNER M, UNTERLUGGAUER T, GINER L, et al. ScatterCache: Thwarting Cache Attacks via Cache Set Randomization[C]// USENIX. 28th USENIX Security Symposium. Berkeley: USENIX, 2019: 675-692.
|
| [17] |
QURESHI M K. CEASER: Mitigating Conflict-Based Cache Attacks via Encrypted-Address and Remapping[C]// IEEE. 2018 51st Annual IEEE/ACM International Symposium on Microarchitecture (MICRO). New York:IEEE, 2018: 775-787.
|
| [18] |
QURESHI M K. New Attacks and Defense for Encrypted-Address Cache[C]// ACM. 2019 ACM/IEEE 46th Annual International Symposium on Computer Architecture (ISCA). New York:ACM, 2019: 360-371.
|
| [19] |
TAN Qinhan, ZENG Zhihua, BU Kai, et al. PhantomCache: Obfuscating Cache Conflicts with Localized Randomization[EB/OL]. (2021-03-13) [2021-11-01]. https://list.zju.edu.cn/kaibu/phantomcache.pdf.
|
| [20] |
YAN Mengjia, GOPIREDDY, SHULL, et al. Secure Hierarchy-Aware Cache Replacement Policy (SHARP): Defending against Cache-Based Side Channel Atacks[C]// ACM. 2017 ACM/IEEE 44th Annual International Symposium on Computer Architecture (ISCA). New York:ACM, 2017: 347-360.
|
| [21] |
COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2017-02-21) [2021-10-22]. https://eprint.iacr.org/2016/086.pdf.
|
| [22] |
ARM. ARM Architecture Reference Manual ARMv7-A and ARMv7-R Edition[EB/OL]. (2018-03-29) [2020-05-20]. https://developer.arm.com/documentation/ddi0406/cd/.
|
| [23] |
LIPP M, GRUSS D, SPREITZER R, et al. ARMageddon: Cache Attacks on Mobile Devices[C]// USENIX. 25th USENIX Security Symposium. Berkeley: USENIX, 2016: 549-564.
|
| [24] |
YANG Fan, ZHANG Qianying, SHI Zhiping, et al. Survey on Software Side-Channel Attacks in Trusted Execution Environment[EB/OL]. (2021-10-20) [2021-12-27]. http://www.jos.org.cn/jos/article/abstract/6501.
|
|
杨帆, 张倩颖, 施智平, 等. 可信执行环境软件侧信道攻击研究综述[EB/OL]. (2021-10-20) [2021-12-27]. http://www.jos.org.cn/jos/article/abstract/6501.
|
| [25] |
WANG Shuai, BAO Yuyan, LIU Xiao, et al. Identifying Cache-Based Side Channels through Secret-Augmented Abstract Interpretation[C]// USENIX. 28th USENIX Security Symposium. Berkeley: USENIXA, 2019: 657-674.
|
| [26] |
DOYCHEV G, KÖPF B, MAUBORGNE L, et al. CacheAudit: A Tool for the Static Analysis of Cache Side Channels[J]. ACM Transactions on Information and System Security, 2015, 18(1): 1-32.
|
| [27] |
IRAZOQUI G, CONG Kai, GUO Xiaofei, et al. Did We Learn from LLC Side Channel Attacks? A Cache Leakage Detection Tool for Crypto Libraries[EB/OL]. (2017-09-05) [2021-11-23]. https://arxiv.org/abs/1709.01552.
|
| [28] |
BROTZMAN R, LIU Shen, ZHANG Danfeng, et al. CaSym: Cache Aware Symbolic Execution for Side Channel Detection and Mitigation[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York:IEEE, 2019: 505-521.
|
| [29] |
GRAS B, RAZAVI K, BOSMAN E, et al. ASLR on the Line: Practical Cache Attacks on the MMU[EB/OL]. (2017-12-28) [2021-08-23]. https://download.vusec.net/papers/anc_ndss17.pdf.
|
| [30] |
SCHAIK S, RAZAVI K, GRAS B, et al. RevAnC: A Framework for Reverse Engineering Hardware Page Table Caches[C]// ACM. 10th European Workshop on Systems Security. New York: ACM, 2017: 1-6.
|
| [31] |
GRAS B, RAZAVI K, BOS H, et al. Translation Leak-Aside Buffer: Defeating Cache Side-Channel Protections with TLB Attacks[C]// USENIX. 27th USENIX Conference on Security Symposium. Berkeley: USENIX, 2018: 955-972.
|
| [32] |
RALF H, CARSTEN W, THORSTEN H. Practical Timing Side Channel Attacks against Kernel Space ASLR[C]// IEEE. 2013 IEEE Symposium on Security and Privacy, New York: IEEE, 2013: 191-205.
|
| [33] |
YUAN Fengkai, HOU Rui. Processor Time-Based Microarchitecture Side Channels, Attacks and Defenses[J]. Journal of Guangzhou University, 2020, 19(2): 24-34.
|
|
苑风凯, 侯锐. 处理器微体系结构时间侧信道攻击与防御[J]. 广州大学学报, 2020, 19(2): 24-34.
|
| [34] |
COSTAN V, LEBEDEV I A, DEVADAS S. Sanctum: Minimal Hardware Extensions for Strong Software Isolation[C]// USENIX. 25th USENIX Security Symposium. Berkeley: USENIX, 2016: 857-874.
|
| [35] |
YAN Mengjia, CHOI J, SKARLATOS D, et al. InvisiSpec: Making Speculative Execution Invisible in the Cache Hierarchy[C]// IEEE. 2018 51st Annual IEEE/ACM International Symposium on Microarchitecture (MICRO). New York:IEEE, 2018: 428-441.
|
| [36] |
DENG Shuwen, XIONG Wenjie, SZEFER J. Secure TLBs[C]// IEEE. 2019 ACM/IEEE 46th Annual International Symposium on Computer Architecture (ISCA). New York:IEEE, 2019: 346-359.
|
| [37] |
GRAS B. Anc-VUSec[EB/OL]. (2021-12-01) [2021-12-28]. https://www.vusec.net/projects/anc/.
|
 ), LI Lei3, YUAN Yidong3, GAO Xinyan4
), LI Lei3, YUAN Yidong3, GAO Xinyan4