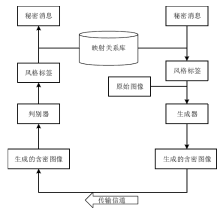
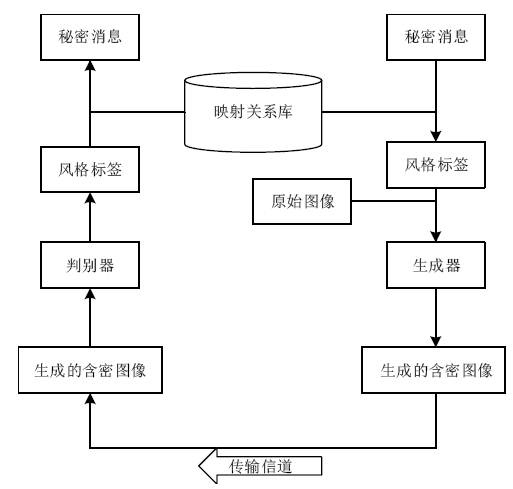
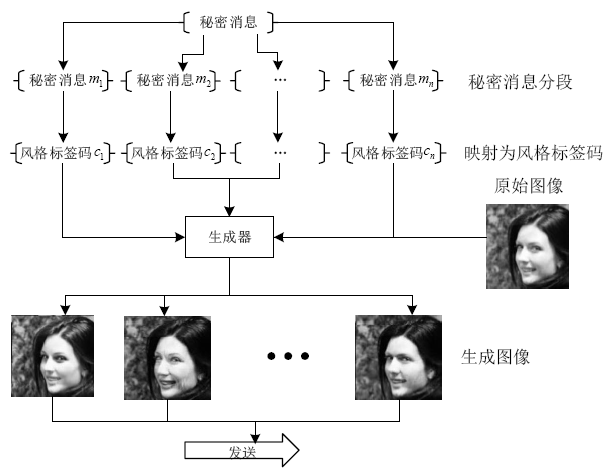
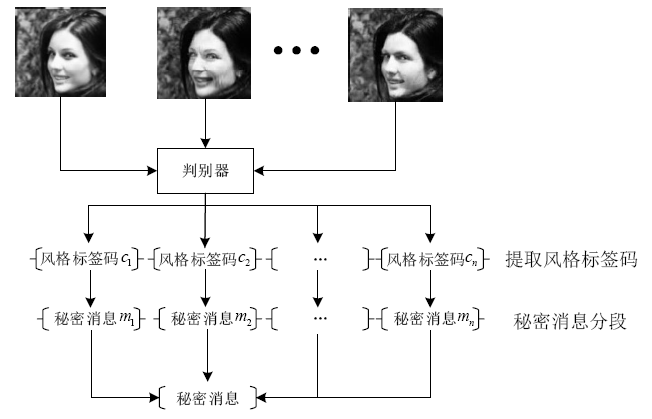
| [1] |
LUO Weiqi, HUANG Fangjun, HUANG Jiwu. Edge Adaptive Image Steganography Based on LSB Matching Revisited[J]. IEEE Transactions on Information Forensics & Security, 2010,5(2):201-214.
|
| [2] |
FILLER T, JUDAS J, FRIDRICH J. Minimizing Additive Distortion in Steganography Using Syndrome-Trellis Codes[J]. IEEE Transactions on Information Forensics & Security, 2011,6(3):920-935.
|
| [3] |
GOODFELLOW I J, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[EB/OL]. https://arxiv.org/abs/1406.2661, 2014-06-10.
|
| [4] |
ZHANG Zhu, LIU Jia, KE Yan, et al. Generative Steganography by Sampling[J]. IEEE Access, 2019,19(7):118586-118597.
|
| [5] |
HUSSAIN I, ZENG Jishen, TAN Sunquan. A Survey on Deep Convolutional Neural Networks for Image Steganographyand Steganalysis[J]. KSII Trans on Internet and Information Systems, 2020,14(3):1228-1248.
|
| [6] |
VOLKHONSKIY D, BORISENKO B, BURNAEV E. Generative Dversarial Networks for Image Steganography[EB/OL]. https://openreview.net/pdf?id=H1hoFU9xe, 2020-08-09.
|
| [7] |
ZHU Junyan, PARK T, ISOLA P, et al. Unpaired Image-to-Image Translation Using Cycle-Consistent Adversarial Networks[C]// IEEE. Proceedings of the IEEE International Conference on Computer Vision, October 22-29, 2017, Venice, Italy. NJ: IEEE, 2017: 2223-2232.
|
| [8] |
HAYES J, DANEZIS G. Generating Steganographic Images via Adversarial Training[EB/OL]. https://arxiv.org/abs/1703.00371, 2014-7-13.
|
| [9] |
HU Donghui, WANG Liang, JIANG Wenjie, et al. A Novel Image Steganography Method via Deep Convolutional Generative Adversarial Networks[J]. IEEE Access, 2018,18(6):38303-38314.
|
| [10] |
ZHANG Zhuo, FU Guangyuan, NI Rongrong, et al. A Generative Method for Steganography by Cover Synjournal with Auxiliary Semantics[J]. Tsinghua Science and Technology, 2020,25(4):516-527.
doi: 10.1109/TST.5971803
URL
|
| [11] |
TANG Weixuan, TAN Shunquan, LI Bin, et al. Automatic Steganographic Distortion Learning Using a Generative Adversarial Network[J]. IEEE Signal Processing Letters, 2017,24(10):1547-1551.
doi: 10.1109/LSP.2017.2745572
URL
|
| [12] |
YANG Jianhua, LIU Kai, KANG Xiangui, et al. Spatial Image Steganography Based on Generative Adversarial Network[EB/OL]. https://arxiv.org/abs/1804.07939, 2018-04-21.
|
| [13] |
RONNEBERGER O, FISCHER P, BROX T. U-net: Convolutional Networks for Biomedical Image Segmentation[C]// TUM & FAU. International Conference on Medical Image Computing and Computer-assisted Intervention, October 5-9, 2015, Munich, Germany. Cham: Springer, 2015: 234-241.
|
| [14] |
HOLUB V, FRIDRICH J, DENEMARK T. Universal Distortion Function for Steganography in an Arbitrary Domain[J]. EURASIP Journal on Information Security, 2014,14(1):1.
|
| [15] |
CHOI Y, CHOI M, KIM M, et al. Stargan: Unified Generative Adversarial Networks for Multi-Domain Image-to-Imagetranslation[C]// IEEE. Proc of the IEEE Conference on Computer Vision and Pattern Recognition, June 18-22, 2018, Salt Lake City, Utah, USA. NJ: IEEE, 2018: 8789-8797.
|
| [16] |
PERARNAU G, VAN D J, RADUCANU B, et al. Invertible Conditional Gans for Image Editing[EB/OL]. https://arxiv.org/abs/1611.06355, 2016-11-19.
|
| [17] |
LIU Jia, KE Yan, ZHANG Zhuo, et al. Recent Advances of Image Steganography with Generative Adversarial Networks[J]. IEEE Access, 2020,20(8):60575-60597.
|
| [18] |
HICSONMEZ S, SAMET N, AKBAS E, et al. GANILLA: Generative Adversarial Networks for Image to Illustration Translation[EB/OL]. https://arxiv.org/abs/2002.05638, 2020-02-14.
|
| [19] |
ISOLA P, ZHU Junyan, ZHOU Tinghui, et al. Image-to-Image Translation with Conditional Adversarial Networks[C]// IEEE. Proc of The IEEE Conference on Computer Visionan Dpattern Recognition, July 21-26, 2017, Honolulu, Hawaii, USA. NJ: IEEE, 2017: 1125-1134.
|
| [20] |
HEUSEL M, RAMSAUER H, UNTERTHINER T, et al. Gans Trainedbya Two Time-Scale Update Rule Converge to ALocal Nash Equilibrium[EB/OL]. https://arxiv.org/abs/1706.08500v6, 2018-01-12.
|
| [21] |
KE Yan, LIU Jia, ZHANG Minqing, et al. Steganography Security: Princip leand Practice[J]. IEEE Access, 2018,18(6):73009-73022.
|
 ), HUANG Siyuan1
), HUANG Siyuan1