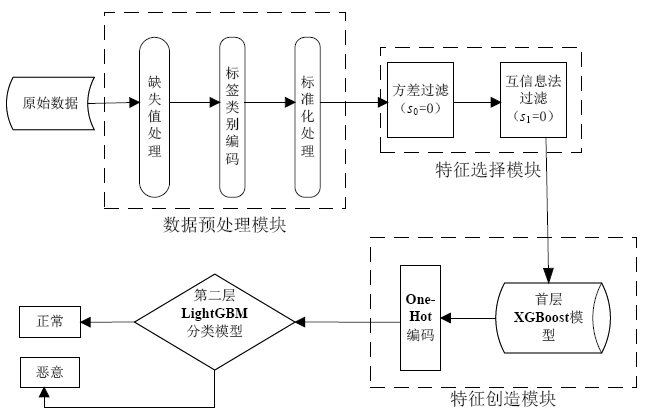
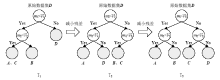
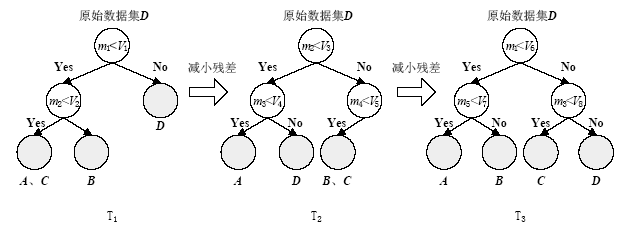
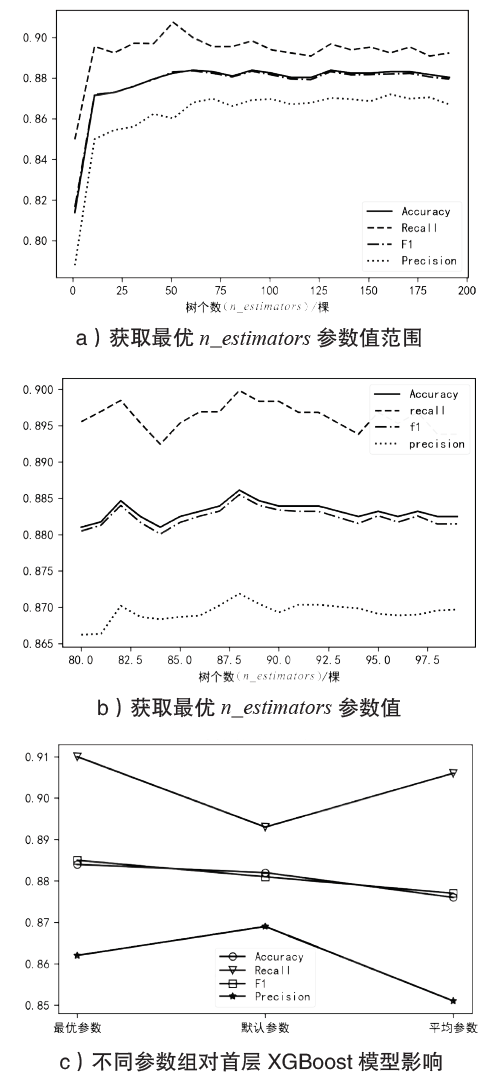
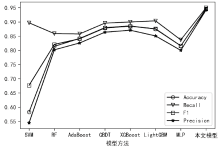
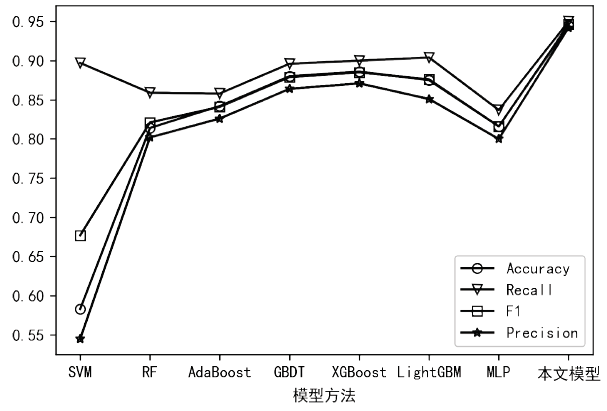
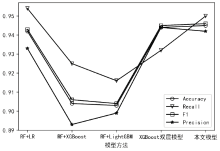
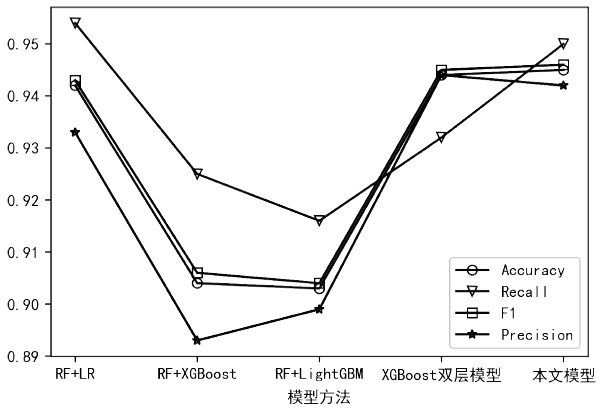
| [1] |
CUI Yanpeng, YAN Bo, HU Jianwei. Android Malware Detection Method Based on Abstract API Call Sequence[J]. Computer Applications and Software, 2019,36(9):321-326.
|
|
崔艳鹏, 颜波, 胡建伟. 基于抽象API调用序列的Android恶意软件检测方法[J]. 计算机应用与软件, 2019,36(9):321-326.
|
| [2] |
HOU Liuyang, LUO Senlin, PAN Limin, et al. Multi-feature Android Malware Detection Method[J]. Netinfo Security, 2020,20(1):67-74.
|
|
侯留洋, 罗森林, 潘丽敏, 等. 融合多特征的Android恶意软件检测方法[J]. 信息网络安全, 2020,20(1):67-74.
|
| [3] |
ZHANG Zhen, CAO Tianjie. Detecting Android Malware Based on Matching Sequence of Behavioral Characteristic Value[J]. Computer Engineering and Applications, 2018,54(24):97-102.
|
|
张震, 曹天杰. 行为特征值序列匹配检测Android恶意应用[J]. 计算机工程与应用, 2018,54(24):97-102.
|
| [4] |
ZHANG Chaoqin, HU Guangwu, WANG Zhenlong, et al. A Novel SVM-Based Detection Method For Android Malware[J]. Computer Applications and Software, 2018,35(10):292-298.
|
|
张超钦, 胡光武, 王振龙, 等. 一种基于支持向量机的安卓恶意软件新型检测方法[J]. 计算机应用与软件, 2018,35(10):292-298.
|
| [5] |
LI Hao, MA Kun, CHEN Zhenxiang, et al. Unknown Malware Detection Based on Network Traffic Analysis[J]. Journal of Jinan University, 2019,33(6):500-505.
|
|
李浩, 马坤, 陈贞翔, 等. 基于网络流量分析的未知恶意软件检测[J]. 济南大学学报(自然科学版), 2019,33(6):500-505.
|
| [6] |
WANG Shuwei, ZHANG Linjie, JIA Zhe, et al. Android Malware Recognition Based on Network Traffic[J]. Radio Engineering, 2020,50(7):612-618.
|
|
王澍玮, 张林杰, 贾哲, 等. 基于网络流量的安卓恶意软件识别[J]. 无线电工程, 2020,50(7):612-618.
|
| [7] |
PENG Guojun, LI Jingwen, SUN Runkang, et al. Android Malware Detection Research and Development[J]. Journal of Wuhan University (Science Edition), 2015,61(1):21-33.
|
|
彭国军, 李晶雯, 孙润康, 等. Android恶意软件检测研究与进展[J]. 武汉大学学报(理学版), 2015,61(1):21-33.
|
| [8] |
LI Zhanshan, LIU Zhaogeng. Feature Selection Algorithm Based on XGBoost[J]. Journal on Communications, 2019,40(10):101-108.
|
|
李占山, 刘兆赓. 基于XGBoost的特征选择算法[J]. 通信学报, 2019,40(10):101-108.
|
| [9] |
WANG Shengwu, CHEN Hongmei. Feature Selection Method Based on Rough Sets and Improved Whale Optimization Algorithm[J]. Computer Science, 2020,47(2):44-50.
|
|
王生武, 陈红梅. 基于粗糙集和改进鲸鱼优化算法的特征选择方法[J]. 计算机科学, 2020,47(2):44-50.
|
| [10] |
BIAN Lingyu, ZHANG Linlin, ZHAO Kai, et al. Ethereum Malicious Account Detection Method Based on LightGBM[J]. Netinfo Security, 2020,20(4):73-80.
|
|
边玲玉, 张琳琳, 赵楷, 等. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020,20(4):73-80.
|
| [11] |
HE X R, PAN J F, JIN O, et al. Practical Lessons from Predicting Clicks on Ads at Facebook[C]// ACM SIGKDD. The 8th International Workshop on Data Mining for Online Advertising, August 24, 2014, New York,USA. New York:ACM SIGKDD, 2014: 1-9.
|
| [12] |
WANG Yao, LI Wei, WU Kehe, et al. Application of Fusion Model of GBDT and LR in Encrypted Traffic Identification[J]. Computer and Modernization, 2020(3):93-98.
|
|
王垚, 李为, 吴克河, 等. GBDT与LR融合模型在加密流量识别中的应用[J]. 计算机与现代化, 2020(3):93-98.
|
| [13] |
LAYA T H, ANDI F A, ARASH H L. Extensible Android Malware Detection and Family Classification Using Network-flows and API-calls[J]. The IEEE(53rd) International Carnahan Conference on Security Technology, 2019,4(1):26-30.
|