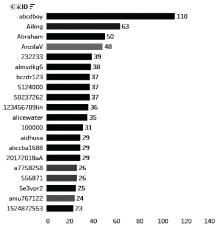
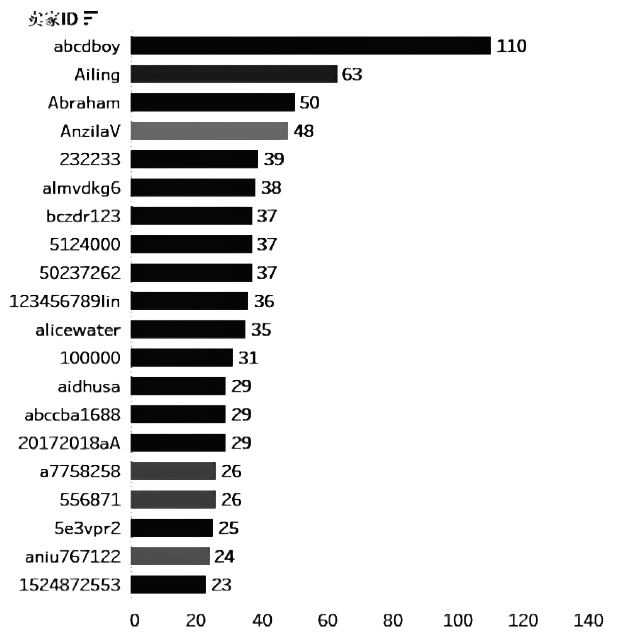
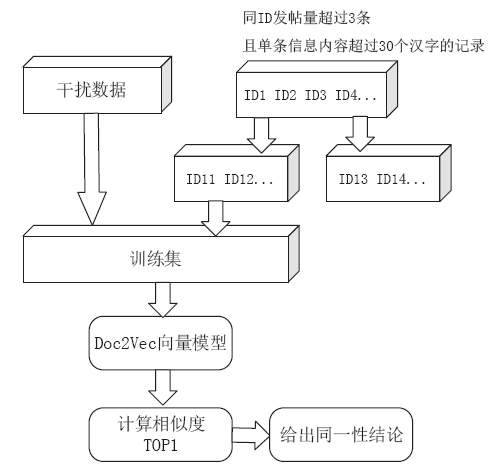
Netinfo Security ›› 2020, Vol. 20 ›› Issue (12): 47-53.doi: 10.3969/j.issn.1671-1122.2020.12.007
Previous Articles Next Articles
Virtual Identity Identification Based on Semantic for Network Trading Platform
ZHANG Xuan1,2, YUAN Deyu1, JIN Bo3( )
)
- 1. School of Information Network Security, People’s Security University of China, Beijing 100038, China
2. Department of Investigation, Shandong Police College, Jinan 250014, China
3. The Third Research Institute ofMinistry of Public Security, Shanghai 201204, China
-
Received:2020-09-19Online:2020-12-10Published:2021-01-12 -
Contact:JIN Bo E-mail:jinbo@stars.org.cn
CLC Number:
Cite this article
ZHANG Xuan, YUAN Deyu, JIN Bo. Virtual Identity Identification Based on Semantic for Network Trading Platform[J]. Netinfo Security, 2020, 20(12): 47-53.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.12.007
| [1] | GUAN Haotian. Research on Virtual Identity Mapping Algorithm for Network Sapce Entity[D]. Harbin: Harbin Institute of Technology, 2019. |
| 关皓天. 网络空间主体虚拟身份映射算法研究[D]. 哈尔滨:哈尔滨工业大学, 2019. | |
| [2] | ZHANG Yiming, XIONG Qi, FAN Yujie, et al. Your Style Your Identity: Leveraging Writing and Photography Styles for Drug Trafficker Identification in Darknet Markets over Attributed Heterogeneous Information Network[C]// WWW. 19th The World Wide Web Conference, May 2019, New York, NY, USA. San Francisco: Association for Computing Machinery, 2019: 3448-3454. |
| [3] | LI Cong. Research on Virtual Identity Tracing and Forensics[D]. Chongqing: Chongqing University of Posts and Telecommunications, 2018. |
| 李葱. 虚拟身份追踪与取证研究[D]. 重庆:重庆邮电大学, 2018. | |
| [4] | DING Xiang. Research and Implementation of Tor Darknet Content Discovery and Analysis Technology[D]. Nanjing: Southeast University of China, 2019. |
| 丁翔. Tor暗网内容发现与分析技术的研究和实现[D]. 南京:东南大学, 2019. | |
| [5] | YANG Yi. Darknet Resource Exploring Technology Research Based on Tor[D]. Shanghai: Shanghai Jiao Tong University, 2018. |
| 杨溢. 基于Tor的暗网空间资源探测技术研究[D]. 上海:上海交通大学, 2018. | |
| [6] | KADOGUCHI M, HAYASHI S, HANSHIMOTO, et al. Exploring the Dark Web for Cyber Threat Intelligence Using Machine Leaning[C]// IEEE. 2019 IEEE International Conference on Intelligence and Security Informatics (ISI). Shenzhen, China, IEEE, 2019: 200-202. |
| [7] | ZHANG Shusen, LIANG Xun, MI Baotong, et al. Content-Based Social Network User Identification Methods[J]. Chinese Journal of Computers, 2019,42(8):1739-1754. |
| 张树森, 梁循, 弭宝瞳, 等. 基于内容的社交网络用户身份识别方法[J]. 计算机学报, 2019,42(8):1739-1754. | |
| [8] | XU Qian, CHEN Hongchang, WU Zheng, et al. User Identification Method Across Social Networks Based on Weighted Hypergraph[J]. Journal of Computer Applications, 2017, 37(12): 3435-3441+3471. |
| 徐乾, 陈鸿昶, 吴铮, 等. 基于带权超图的跨网络用户身份识别方法[J]. 计算机应用, 2017, 37(12): 3435-3441+3471. | |
| [9] | SITIKHU P, PAHI K, THPAPA P, et al. A Comparison of Semantic Similarity Methods for Maximum Human Interpretability[C]// IEEE. Artificial Intelligence for Transforming Business and Society (AITB). November 2019, Kathmandu, Nepal. New York: IEEE, 2019: 5-5 |
| [10] | LIN Dekang. An Information-theoretic Definition of Similarity[C]// ICML. The 15th International Conference on Machine Learning. July 1998, San Francisco, CA, USA. Morgan Kaufmann Publishers Inc., 1998: 296-304. |
| [11] | CHEN Erjing, JIANG Enbo. Review of Studies on Text Similarity Measures[J]. Data Analysis and Knowledge Discovery, 2017,1(6):1-11. |
| 陈二静, 姜恩波. 文本相似度计算方法研究综述[J]. 数据分析与知识发现, 2017,1(6):1-11. | |
| [12] | WANG Chunliu, YANG Yonghui, DENG Fei, et al. A Review of Text Similarity Approaches[J]. Information Science, 2019,37(3):158-168. |
| 王春柳, 杨永辉, 邓霏, 等. 文本相似度计算方法研究综述[J]. 情报科学, 2019,37(3):158-168. | |
| [13] | ZHANG Shuang, ZHENG Xuefeng, HU Chuangjun. Survey of Semantic Similarity and its Application to Social Network Analysis[C]// IEEE. 2015 IEEE International Conference on Big Data (Big Data), January 2020, Santa Clara, CA, USA. New York: IEEE, 2015: 2362-2367 |
| [14] | HAN Chengcheng, LI Lei, LIU Tingting, et al. Approaches for Semantic Textual Similarity[J]. Journal of East China Normal University(Natural Science), 2020(5):95-112. |
| 韩程程, 李磊, 刘婷婷, 等. 语义文本相似度计算方法[J]. 华东师范大学学报(自然科学版), 2020(5):95-112. | |
| [15] | YANG Cheng. Research on Semantic Similarity Calculation of Short Text Based on Neural Network[D]. Chengdu: University of Electronic Science and Technology of China, 2020. |
| 杨晨. 基于神经网络的短文本语义相似度计算方法研究[D]. 成都:电子科技大学, 2020. | |
| [16] | QUOC L, TOMAS M. Distributed Representations of Sentences and Documents[C]// ACM. In Proceedings of the 31st International Conference on International Conference on Machine Learning, June 2014, Beijing, China. New York: JMLR. org, 2014: 1188-1196. |
| [17] | YVES P. Comparing Sentence Similarity Methods[EB/OL]. http://nlp.town/blog/sentence-similarity/, 2018-05-02. |
| [18] | WANG Xiangwen, PENG Peng, WANG Chun, et al. You are Your Photographs: Detecting Multiple Identities of Vendors in the Darknet Marketplaces[C]// ACM. ASIA CCS '18: ACM Asia Conference on Computer and Communications Security, June 2018, Incheon Republic of Korea. New York: Association for Computing Machinery, 2018: 431-442. |
| [19] | SUN Junyi, WANG Dingyuan, XIANG Chao, et al. "Jieba"Chinese Word Segmentation[EB/OL]. https://github.com/fxsjy/jieba, 2020-10-20. |
| [20] | LUO Ruixuan, XU Jingjing, REN Xuancheng. Pkuseg[EB/OL]. https://github.com/lancopku/pkuseg-python, 2020-06-21. |
| [21] | RADIM R, PETR S. Genism[EB/OL]. https://radimrehurek.com/gensim/index.html 2019-11-01. |
| [1] | JIN Zhigang, WANG Xinjian, LI Gen, YUE Shunmin. The Generation Method of Network Defense Strategy Combining with Attack Graph and Game Model [J]. Netinfo Security, 2021, 21(1): 1-9. |
| [2] | YOU Weijing, LIU Limin, MA Yue, HAN Dong. An Intel SGX-based Proof of Encryption in Clouds [J]. Netinfo Security, 2020, 20(12): 1-8. |
| [3] | HE Jingsha, HAN Song, ZHU Nafei, GE Jiake. Research and Optimization of Intrusion Detection Based on Improved V-detector Algorithm [J]. Netinfo Security, 2020, 20(12): 19-27. |
| [4] | ZHANG Xinyue, HU Anlei, LI Jurong, FENG Yanchun. A Method of Adaptive Abnormal Network Traffic Detection [J]. Netinfo Security, 2020, 20(12): 28-32. |
| [5] | ZHAO Guofeng, ZHOU Wentao, XU Chuan, XU Lei. A Secure Identity Authentication Scheme for Space-ground Integrated Network Based on Bilinear Pairing [J]. Netinfo Security, 2020, 20(12): 33-39. |
| [6] | FENG Yan, LIU Nian, XIE Sijiang. A Bi-directional Use Scheme of Quantum Key Pool [J]. Netinfo Security, 2020, 20(12): 40-46. |
| [7] | XU Guotian, SHEN Yaotong. A Malware Detection Method Based on XGBoost and LightGBM Two-layer Model [J]. Netinfo Security, 2020, 20(12): 54-63. |
| [8] | BI Xinliang, YANG Haibin, YANG Xiaoyuan, HUANG Siyuan. Generative Steganography Scheme Based on StarGAN [J]. Netinfo Security, 2020, 20(12): 64-71. |
| [9] | TAN Yang, LIU Jiayong, ZHANG Lei. Malware Familial Classification of Deep Auto-encoder Based on Mixed Features [J]. Netinfo Security, 2020, 20(12): 72-82. |
| [10] | WANG Changjie, LI Zhihua, ZHANG Ye. A Threat Intelligence Generation Method for Malware Family [J]. Netinfo Security, 2020, 20(12): 83-90. |
| [11] | YU Beiyuan, LIU Jianwei, ZHOU Ziyu. Research on Node Authentication Mechanism in Self-organizing Network Environment [J]. Netinfo Security, 2020, 20(12): 9-18. |
| [12] | ZHANG Zheng, ZHA Daren, LIU Yanan, FANG Xuming. PUF-based Kerberos Extension Protocol with Formal Analysis [J]. Netinfo Security, 2020, 20(12): 91-97. |
| [13] | DUAN Xiaowei, HAN Yiliang, WANG Chao, LI Zhe. Analysis and Improvement of Public Key Reuse for A RLWE Key Exchange Protocol [J]. Netinfo Security, 2020, 20(11): 87-94. |
| [14] | JIANG Nan, WANG Weiqi, WANG Jian. Research on Personal Information Protection Method Based on Smart Contract [J]. Netinfo Security, 2020, 20(11): 22-31. |
| [15] | WEN Weiping, CHEN Xiarun, YANG Fachang. Malicious Code Forensics Method Based on Hidden Behavior Characteristics of Rootkit on Linux [J]. Netinfo Security, 2020, 20(11): 32-42. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||