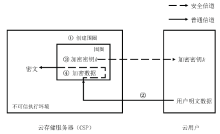
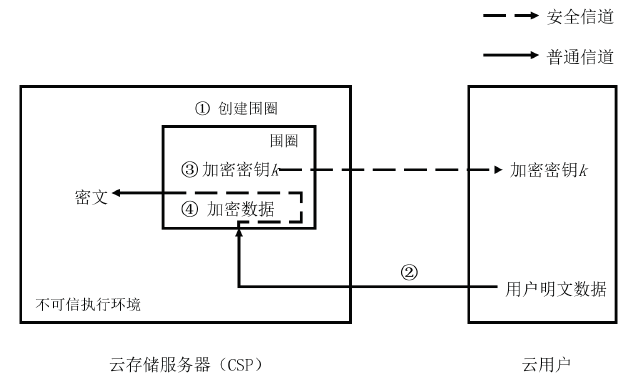
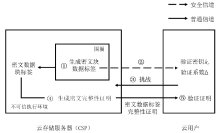
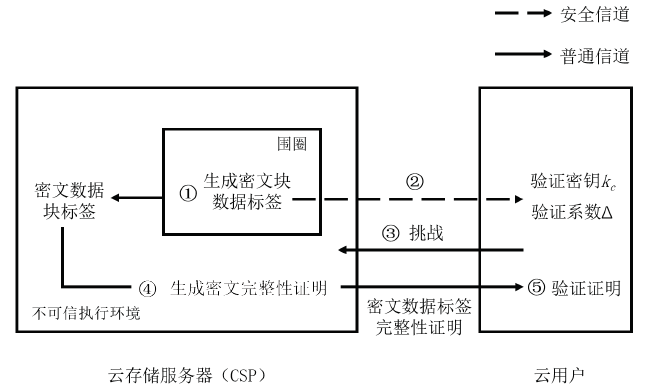
| [1] |
REINSEL D, GANTZ J, RYDING J. Digital Age 2025: The Digitization of the World-from Edge to Core[EB/OL]. https://www.seagate.com/cn/zh/our-story/data-age-2025/, 2018-11-03.
|
| [2] |
VAN DIJK M, JUELS A, OPREA A, et al. Hourglass schemes: How to Prove That Cloud Files are Encrypted[C]// ACM. Proceedings of the 19th ACM conference on Computer and communications security (ACM CCS), October 16-18, 2012, Raleigh, NC, USA. New York: ACM, 2012: 265-280.
|
| [3] |
HU Keji, ZHANG Wensheng. Efficient Verification of Data Encryption on Cloud Servers[C]// IEEE. 2014 Twelfth Annual International Conference on Privacy, Security and Trust (PST), July 23-24, 2014, Toronto, ON, Canada. New York: IEEE, 2014: 314-321.
|
| [4] |
FANG Jinxia, LIU Llimin, LIN Jingqiang. Practical Verification of Data Encryption for Cloud Storage Services[C]// Springer. 16th International Conference on Services Computing (SCC), June 25-30, 2019, Diego, CA, USA. Nature Switzerland AG: Springer, 2019: 16-31.
|
| [5] |
Intel. Intel® Software Guard Extensions[EB/OL]. https://software.intel.com/zh-cn/sgx. 2020-09-09.
|
| [6] |
Microsoft. Microsoft Azure[EB/OL]. http://www.windowsazure.cn/?fb=002, 2020-09-09.
|
| [7] |
Dropbox. Dropbox[EB/OL]. https://www.dropbox.com, 2020-09-09.
|
| [8] |
Intel. Intel® Software Guard Extensions (Intel® SGX) SDK for Windows* OS[EB/OL]. https://software.intel.com/sites/default/files/managed/47/19/sgx-sdk-developer-reference-for-windows-os.pdf, 2020-06-24.
|
| [9] |
Intel. Remote Attestation in Intel® Software Guard Extensions[EB/OL]. https://github.com/intel/sgx-ra-sample, 2020-10-02.
|
| [10] |
KURNIKOV A, PAVERD A, MANNAN M, et al. Keys in the Clouds: Auditable Multi-device Access to Cryptographic Credentials[C]// ACM. Proceedings of the 13rd International Conference on Availability, Reliability and Security, August 27-30, 2018, Hamburg, Germany. New York: ACM, 2018: 1-10.
|
| [11] |
YOU Weijing, CHEN Bo. Proofs of Ownership on Encrypted Cloud Data via Intel SGX[C]// Springer. The 1st ACNS Workshop on Secure Cryptographic Implementation (SCI '20) (in conjunction with ACNS '20). October 19-22, 2020, Rome, Italy. Nature Switzerland AG: Springer, 2020: 400-416.
|
| [12] |
HE Yun, XU Yihua, JIA Xiaoqi, et al. EnclavePDP: A General Framework to Verify Data Integrity in Cloud Using Intel SGX[C]// Springer. Proceedings of the 23rd International Symposium on Research in Attacks, Intrusions and Defenses (RAID). October 14-16, 2020, Donostia, San Sebastian, Spain. Nature Switzerland AG: Springer, 2020: 195-208.
|
| [13] |
ATENIESE G, BURNS R, CURTMOLA R, et al. Provable Data Possession at Untrusted Stores[C]// ACM. Proceedings of the 14th ACM Conference on Computer and Communications Security (ACM CCS). October 29-November 2, 2007, Alexandria, Virginia, USA. New York: ACM, 2007: 598-609.
|
| [14] |
JURELS A KALISKI JR B S. Pors: Proofs of Retrievability for Large Files[C]// ACM. Proceedings of the 14th ACM Conference on Computer and Communications Security (ACM CCS). October 29-November 2, 2007, Alexandria, Virginia, USA. New York: ACM, 2007: 598-609.
|
| [15] |
SHACHAM H, WATERS B. Compact Proofs of Retrievability[J]. Journal of Cryptology, 2013,26(3):442-483.
doi: 10.1007/s00145-012-9129-2
URL
|
| [16] |
HALEVI S, HARNIK D, PINKAS B, et al. Proofs of Ownership in Remote Storage Systems[C]// ACM. Proceedings of the 18th ACM Conference on Computer and Communications Security (ACM CCS). October 17-21, 2011, Chicago, Illinois, USA. New York: ACM, 2011: 491-500.
|
| [17] |
YOU Weijing, CHEN Bo, LIU Limin, et al. Deduplication-friendly Watermarking for Multimedia Data in Public Clouds[C]// Springer. Proceedings of the 25th European Symposium on Research in Computer Security (ESORICS). September 14-18, 2020, Guildford, UK. Nature Switzerland AG: Springer, 2020: 67-87.
|
| [18] |
LYNN B. The Pairing-based Cryptography Library[EB/OL]. https://crypto.stanford.edu/pbc/, 2020-09-09.
|
 )
)