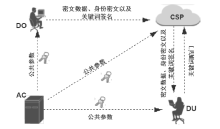
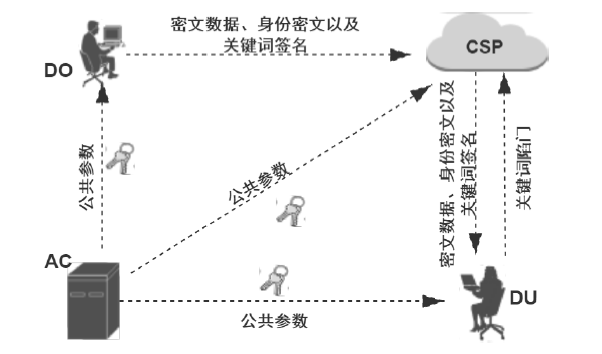
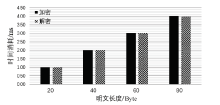
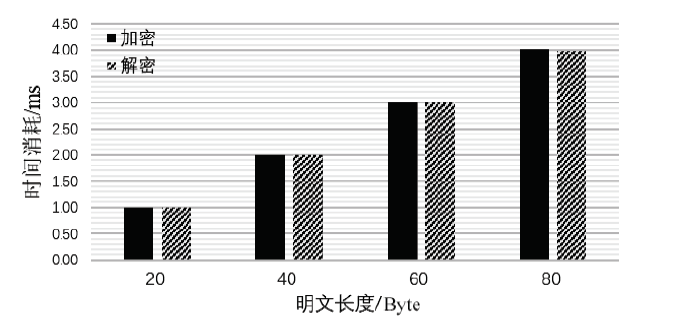
| [1] |
LI Jingwei, JIA Chunfu, LIU Zheli, et al.Survey on the Searchable Encryption[J]. Journal of Software, 2015, 26(1): 109-128.
|
|
李经纬,贾春福,刘哲理,等.可搜索加密技术研究综述[J].软件学报, 2015,26(1):109-128.
|
| [2] |
SONG D X, WAGNER D, PERRIG A.Practical Techniques for Searches on Encrypted Data[C]// IEEE. 2000 IEEE Symposium on Security and Privacy, May 14-17, 2000, Berkeley, CA, USA. NJ: IEEE, 2000: 44-55.
|
| [3] |
BONEH D, CRESCENZO G D, OSTROVSKY R, et al.Public Key Encryption with Keyword Search[M]//Springer. Advances in Cryptology-Eurocrypt 2004. Heidelberg: Springer, Berlin, 2004: 506-522.
|
| [4] |
LIU Pengliang, ZU Longhui, BAI Cuicui, et al.A Verifiable Public Key Searchable Encryption Scheme[J]. Computer Engineering, 2014, 40(11): 118-120.
|
|
刘鹏亮,俎龙辉,白翠翠,等.一种可验证的公钥可搜索加密方案[J].计算机工程,2014,40(11):118-120.
|
| [5] |
MIN S H, CHENG C L, SHIH T H.An ElGamal-like Secure Channel Free Public Key Encryption with Keyword Search Scheme[J]. International Journal of Foundations of Computer Science, 2019, 30(2): 255-273.
|
| [6] |
TSIOUNIS Y, YUNG M.On the Security of ElGamal-based Encryption[M]//Springer. Public Key Cryptography. Heidelberg: Springer, Berlin, 1998: 117-134.
|
| [7] |
KUO W C.On ElGamal Signature Scheme[C]// IEEE. Future Generation Communication & Networking, December 6-8, 2007, Jeju, South Korea. NJ: IEEE, 2007: 151-153.
|
| [8] |
BAO Yiqin. Manufacturing Technology of Diffie-Hellman Encryption Algorithm Based on Cipher Vector and Fibonacci Matrix: China, 201810119265. 1[P].2018-7-27.
|
|
包依勤,基于密码向量和斐波纳契矩阵的Diffie-Hellman加密算法制造技术:中国, 201810119265.1[P].2018-7-27.
|
| [9] |
JIANG Peng.Research on the Privacy of Key Words in Cloud Storage Ciphertext Retrieval[D]. Beijing: Beijing University of Posts and Telecommunications, 2017.
|
|
蒋芃. 云存储密文检索的关键字隐私性研究[D].北京:北京邮电大学,2017.
|
| [10] |
HUANG Qiong, LI Hongbo. An Efficient Public-key Searchable Encryption Scheme Secure against Inside Keyword Guessing Attacks[J]. Information Sciences, 2017, 403-404: 1-14.
|
| [11] |
YANG Haomiao, XU Chunxiang, ZHAO Hongtian.An Efficient Public Key Encryption with Keyword Scheme Not Using Pairing[C]//IEEE. The 1st International Conference on Instrumentation, Measurement, Computer, Communication and Control, October 21-23, 2011, Beijing, China. NJ: IEEE, 2011: 900-904.
|
| [12] |
BAEK J, SAFAVI-NAINI R, SUSILO W.Public Key Encryption with Keyword Search Revisited[M]// Springer. Computational Science and Its Applications-ICCSA 2008. Heidelberg: Springer, Berlin, 2008: 1249-1259.
|