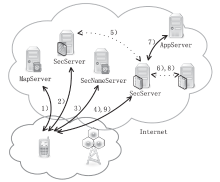
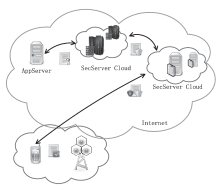
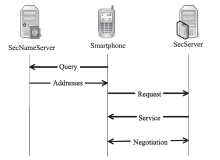
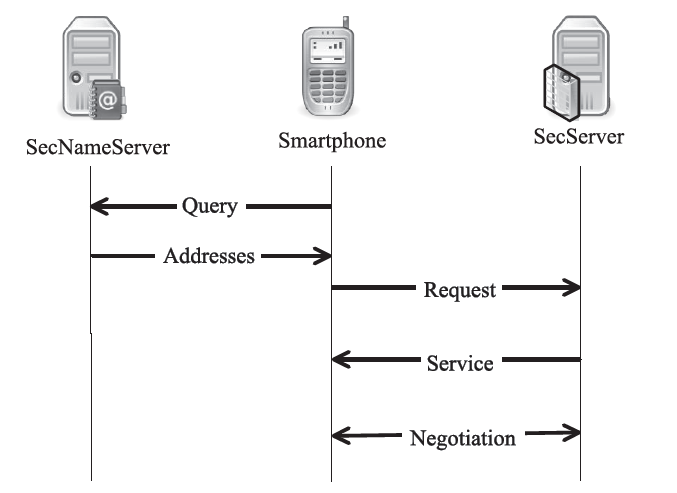
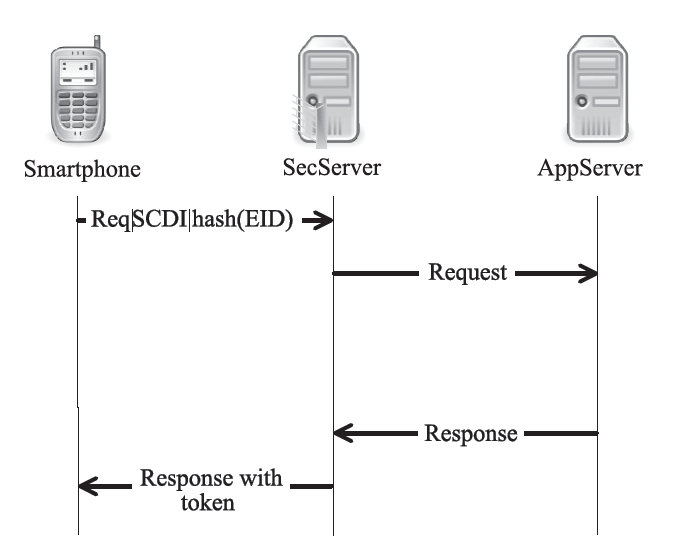
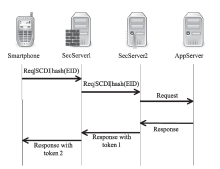
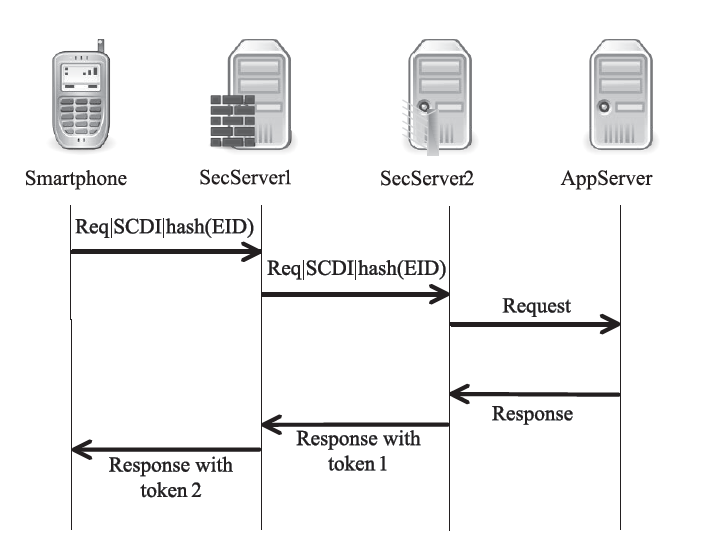
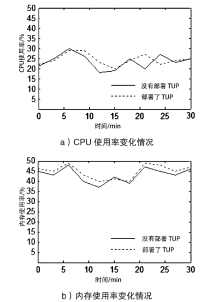
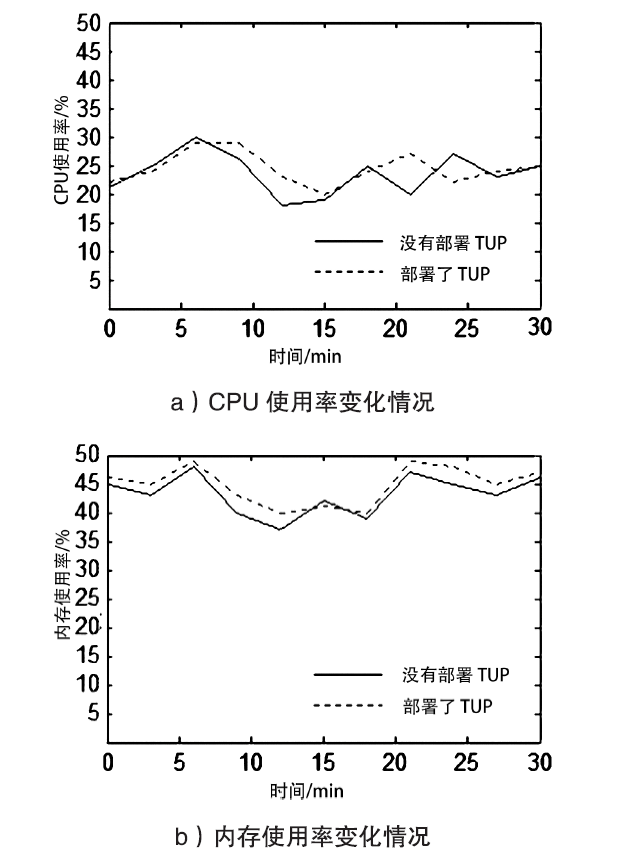
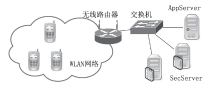
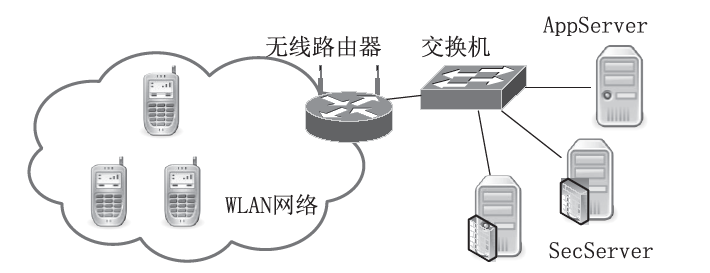
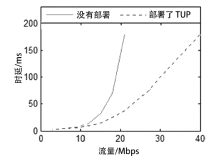
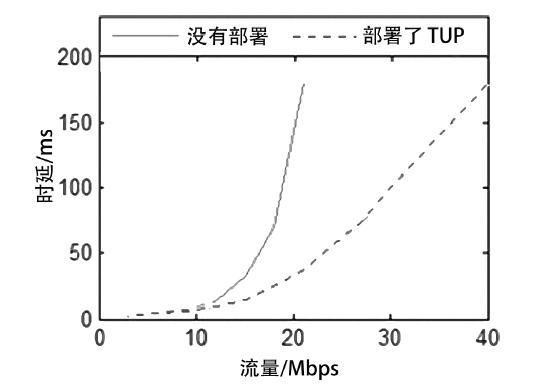
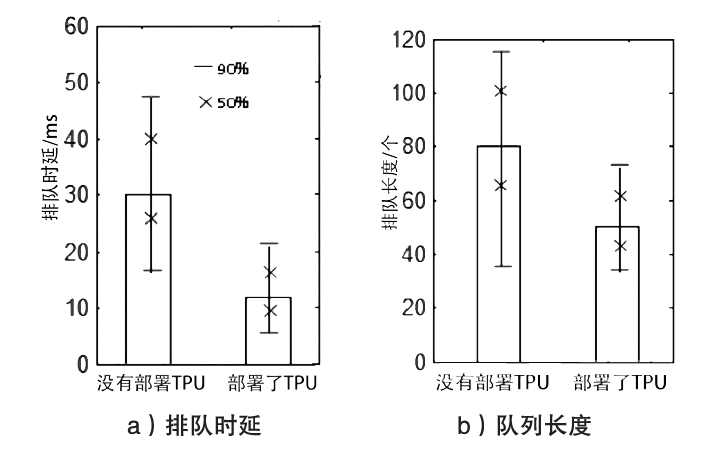
| [1] |
PORTOKAILIDIS G, HOMBURG P C, ANAGNOSTAKIS K, et al. Paranoid Android: Versatile Protection for Smartphones[EB/OL]. , 2019-10-10.
|
| [2] |
BECHER M, FREILING F C, HOFFMANN J, et al.Mobile Security Catching Up? Revealing the Nuts and Bolts of the Security of Mobile Devices[C]//IEEE. 2011 IEEE Symposium on Security and Privacy(SP’11), May 22-25, 2011, Berkeley, CA, USA. NJ: IEEE, 2011: 96-111.
|
| [3] |
LUO Junzhou, WU Wenjia, YANG Ming.Mobile Internet: Terminal Devices, Networks and Services[J]. Chinese Journal of Computers, 2011, 34(11): 2029-2051.
|
|
罗军舟,吴文甲,杨明.移动互联网:终端、网络与服务[J].计算机学报,2011,34(11):2029-2051.
|
| [4] |
OBERHEIDE J, COOKE E, JAHANIAN F. CloudAV: N-version Antivirus in the Network Cloud[EB/OL]. , 2019-10-10.
|
| [5] |
WU Bin, LIN Xing, LI Weidong, et al.Smartphone Malware Detection Model Based on Artificial Immune System in Cloud Computing[J]. Journal of Beijing University of Posts and Telecommunications, 2015,38(4):33-37.
|
|
武斌,林幸,李卫东,等.云计算下手机人工免疫恶意代码检测模型[J].北京邮电大学学报,2015,38(4):33-37.
|
| [6] |
LI Jun.Research on a Mobile Malicious Code Management and Control Method Based on Cloud-Pipeline-Terminal[J]. Telecommunications Science, 2013, 8: 156-167.
|
|
李俊. 一种基于云一管一端的移动互联网恶意程序管控方案研究[J].电信科学,2013,8:156-167.
|
| [7] |
JOSEPH D A, TAVAKOLI A, STOICA I, A Policy-aware Switching Layer for Data Centers[J]. ACM SIGCOMM Computer Communication Review, 2008, 38(4): 51-62.
|
| [8] |
CASADO M, FREEDMAN M, PETTIT J, et al.Ethane: Taking Control of the Enterprise[J]. Computer Communication Review, 2007, 37(4): 1-12.
|
| [9] |
WALFISH M, STRIBLING J, KROHN M, et al. Middleboxes No Longer Considered Harmful[EB/OL]. ,2019-10-10.
|
| [10] |
JIANG Guoqing.The Study on Security of Data in Intelligent Mobile Based on Cloud Computing[J]. Software Engineer, 2015,18(11): 22-23.
|
|
蒋国清. 基于云计算的智能移动终端的数据安全性研究[J].软件工程师,2015,18(11):22-23.
|
| [11] |
ZHAO Yu, ZHANG Kecheng.Implementation of Mobile Internet Security Solutions Based on Mobile Core Network[J]. Communications Technology, 2018, 51(1): 205-209.
|
|
赵宇,张科程.基于移动核心网的手机信息安全系统实现[J].通信技术,2018,51(1):205-209.
|
| [12] |
GUHA S, FRANCIS P.An End-middle-end Approach to Connection Establishment[J]. Computer Communication Review, 2007, 37(4): 193-204.
|
| [13] |
MUTHUKRISHNAN C, PAXSON V, ALLMAN M, et al.Using Strongly Typed Networking to Architect for Tussle[C]//ACM. The 9th ACM SIGCOMM Workshop on Hot Topics in Networks, October 20-21, 2010, Monterey, California, USA. New York: ACM, 2010: 1-6.
|
| [14] |
ERIKSSON A, FODOR G.A Middlebox Control Plane Framework for Wireless and Mobile IP Networks[C]//IEEE. The 2004 International Conference on Parallel Processing Workshops, August 18, 2004, Montreal, QC, Canada. NJ: IEEE, 2004: 322-329.
|
| [15] |
DOGAR F R, STEENKISTE P. M2: Using Visible Middleboxes to Serve Pro-active Mobile-hosts[EB/OL]. ,2019-10-10.
|
| [16] |
ROCHA B P S, COSTA D N O, MOREIRA R A, et al. Adaptive Security Protocol Selection for Mobile Computing[J]. Journal of Network and Computer Applications, 2010, 33(5): 569-587.
|
| [17] |
PANJA B, MADRIA S K, BHARGAVA B.A Role-based Access in a Hierarchical Sensor Network Architecture to Provide Multilevel Security[J]. Computer Communications, 2008, 31(4): 793-806.
|
| [18] |
WANG Hui, WANG Rui, HU Zhaohua.Future Development Direction of Terminal Security Protection[J]. Communications Technology, 2019, 52(2): 455-459.
|
|
王慧,王锐,胡兆华.未来终端安全防护的发展方向[J].通信技术,2019,52(2):455-459.
|
| [19] |
ANDERSEN D, BALAKRISHNAN H, FEAMSTER N, et al.Accountable Internet Protocol(AIP)[J]. Computer Communication Review, 2008, 38(4): 339-350.
|
| [20] |
SESKAR I, NAGARAJA K, NELSON S, et al.MobilityFirst Future Internet Architecture Project[C]//SIGCOMM. The 7th Asian Internet Engineering Conference, November 9-11, 2011, Bangkok, Thailand. New York: ACM, 2011: 1-3.
|
| [21] |
ClearFoundationg. Application Layer Packet Classifier for Linux[EB/OL]. , 2019-10-10.
|