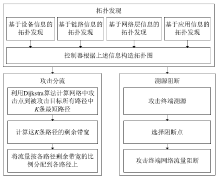
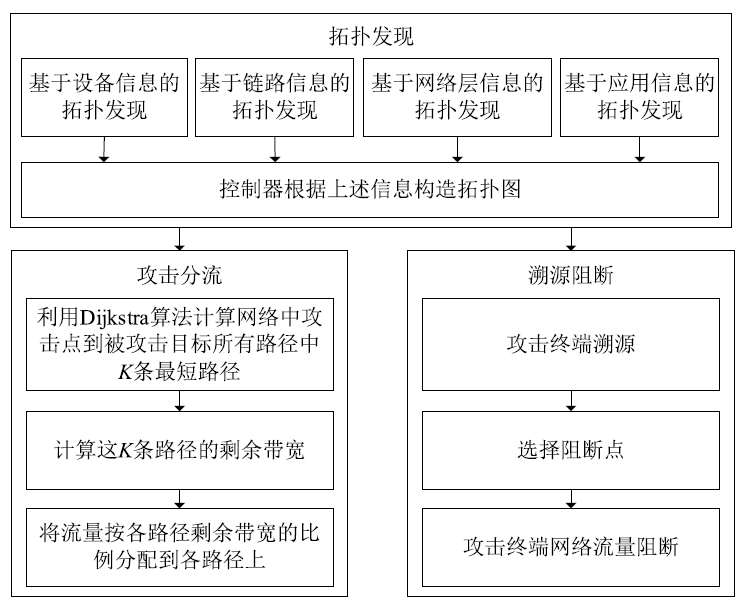
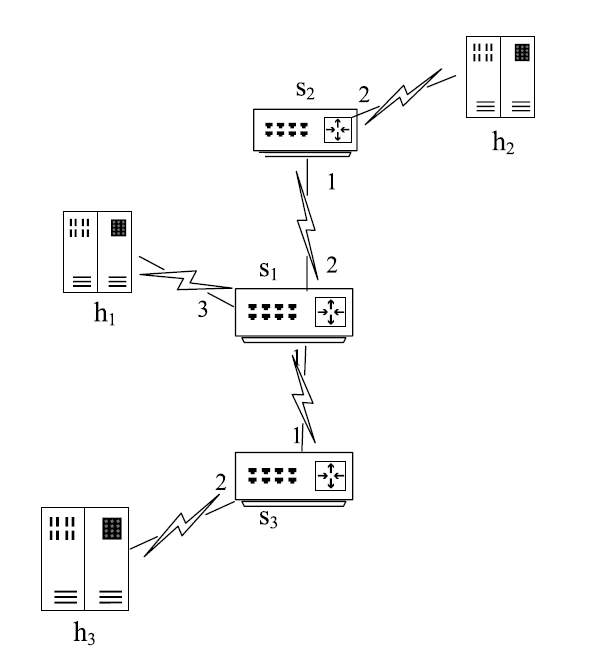
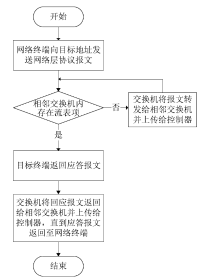
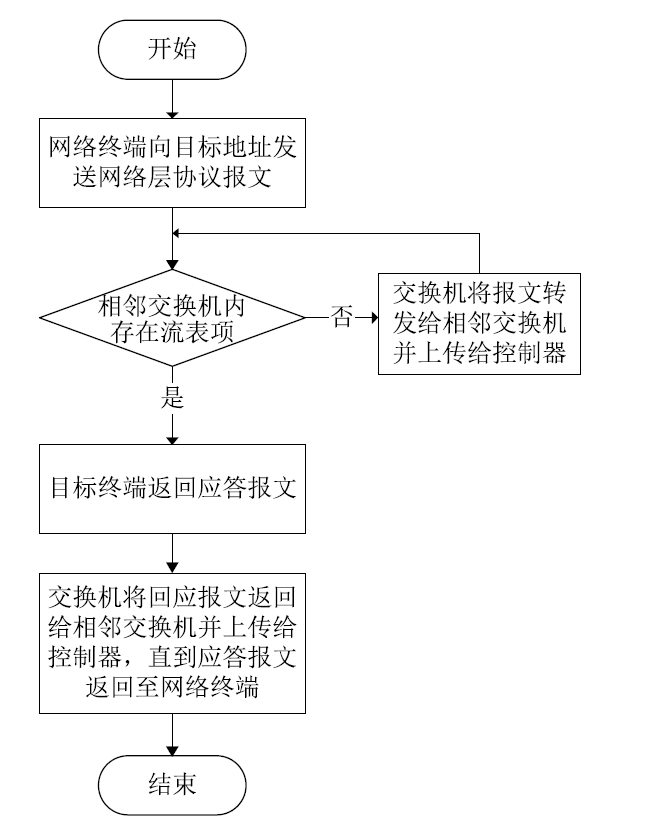
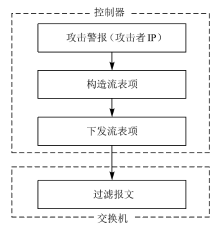
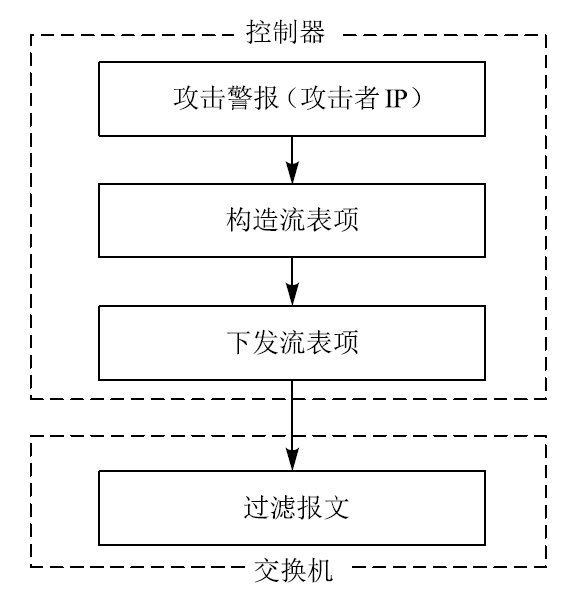
Netinfo Security ›› 2020, Vol. 20 ›› Issue (3): 9-17.doi: 10.3969/j.issn.1671-1122.2020.03.002
Previous Articles Next Articles
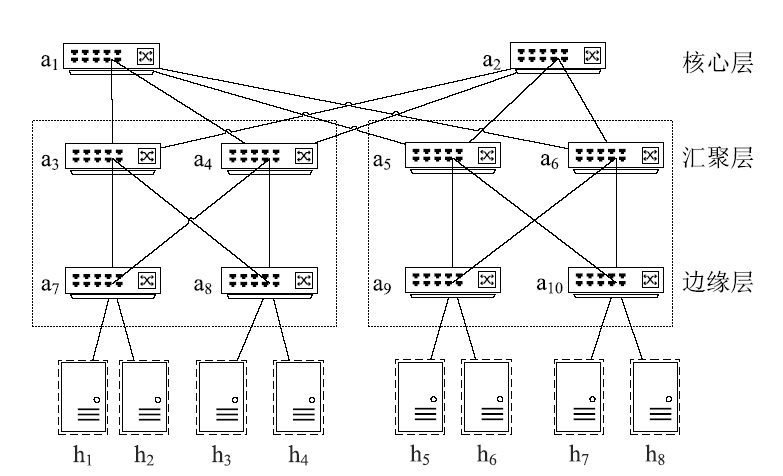
Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis
SONG Yubo1,2,3( ), FAN Ming1,2,3, YANG Junjie1,2,3, HU Aiqun1,2,3
), FAN Ming1,2,3, YANG Junjie1,2,3, HU Aiqun1,2,3
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Jiangsu Key Laboratory of Computer Networking Technology, Nanjing 211189, China
3. Network Communication and Security Purple Mountain Laboratory, Nanjing 211189, China
-
Received:2019-11-20Online:2020-03-10Published:2020-05-11
CLC Number:
Cite this article
SONG Yubo, FAN Ming, YANG Junjie, HU Aiqun. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis[J]. Netinfo Security, 2020, 20(3): 9-17.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.03.002
| [1] | CNCERT. Internet Security Situation in China in the First Half of 2019[EB/OL]. , 2018-8-13. |
| 国家互联网应急中心. 2019 年上半年我国互联网网络安全态势[EB/OL]. , 2018-8-13. | |
| [2] | YAN Qiao, YU F R, GONG Qingxiang, et al.Software-defined Networking(SDN) and Distributed Denial of Service(DDoS) Attacks in cloud Computing Environments: A Survey, Some Research Issues, and Challenges[J]. IEEE Communications Surveys & Tutorials, 2015, 18(1): 602-622. |
| [3] | CUI Yunhe, YAN Lianshan, LI Saifei, et al. SD-Anti-DDoS: Fast and Efficient DDoS Defense in Software-defined Networks[EB/OL]. , 2019-9-11. |
| [4] | WANG Xiulei, CHEN Ming, XING Changyou.SDSNM: a Software-defined Security Networking Mechanism to Defend Against DDoS Attacks[C]//IEEE. 9th International Conference on Frontier of Computer Science and Technology, August 26-28, 2015, Dalian, China. New Jersey: IEEE, 2015: 115-121. |
| [5] | BURAGOHAIN C, MEDHI N.FlowTrApp: An SDN Based Architecture for DDoS Attack Detection and Mitigation in Data Centers[C]//IEEE. 3rd International Conference on Signal Processing and Integrated Networks, February 11-12, 2016, Noida, India. New Jersey: IEEE, 2016: 519-524. |
| [6] | SARWAR M A, HUSSAIN M, ANWAR M U, et al. FlowJustifier: An Optimized Trust-based Request Prioritization Approach for Mitigation of SDN Controller DDoS Attacks in the IoT Paradigm[EB/OL]. , 2019-9-10. |
| [7] | RAHMAN O, QURAISHI M A G, LUNG C H. DDoS Attacks Detection and Mitigation in SDN Using Machine Learning[EB/OL]. , 2019-9-10. |
| [8] | SAHAY R, BLANC G, ZHANG Zonghua, et al. Towards Autonomic DDoS Mitigation Using Software Defined Networking[EB/OL]. , 2019-9-10. |
| [9] | VON AHN L, BLUM M, HOPPER N J, et al.CAPTCHA: Using Hard AI Problems for Security[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 4-8, Warsaw, Poland. Heidelberg: Springer, 2003: 294-311. |
| [10] | CHUNG C J, KHATKAR P, XING Tianyi, et al.NICE: Network Intrusion Detection and Countermeasure Selection in Virtual Network Systems[J]. IEEE Transactions on Dependable and Secure Computing, 2013, 10(4): 198-211. |
| [11] | XING Tianyi, HUANG Dijiang, XU Le, et al.Snortflow: A Openflow-based Intrusion Prevention System in Cloud Environment[C]//IEEE. 2nd GENI Research and Educational Experiment Workshop, March 20-22, 2013, Salt Lake City, UT, USA. New Jersey: IEEE, 2013: 89-92. |
| [12] | CONTI M, GANGWAL A, GAUR M S.A Comprehensive and Effective Mechanism for DDoS Detection in SDN[C]//IEEE. 13th International Conference on Wireless and Mobile Computing, Networking and Communications, October 9-11, 2017, Rome, Italy. New Jersey: IEEE, 2017: 1-8. |
| [13] | DA SILVA A S, WICKBOLDT J A, GRANVILLE L Z, et al. ATLANTIC: A Framework for Anomaly Traffic Detection, Classification, and Mitigation in SDN[C]//IEEE. NOMS 2016-2016 IEEE/IFIP Network Operations and Management Symposium, April 25-29, 2016, Istanbul, Turkey. New Jersey: IEEE, 2016: 27-35. |
| [14] | BARKI L, SHIDLING A, METI N, et al.Detection of Distributed Denial of Service Attacks in Software Defined Networks[C]//IEEE. 2016 International Conference on Advances in Computing, Communications and Informatics, September 21-24, 2016, Jaipur, India. New Jersey: IEEE, 2016: 2576-2581. |
| [15] | ABUBAKAR A, PRANGGONO B.Machine Learning Based Intrusion Detection System for Software Defined Networks[C]//IEEE. 7th International Conference on Emerging Security Technologies, September 6-8, 2017, Canterbury, UK. New Jersey: IEEE, 2017: 138-143. |
| [16] | BRAGA R, MOTA E, PASSITO A.Lightweight DDoS Flooding Attack Detection Using NOX/OpenFlow[C]//IEEE. IEEE Local Computer Network Conference, October 10-14, 2010, Denver, CO, USA. New Jersey: IEEE, 2010: 408-415. |
| [1] | ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector [J]. Netinfo Security, 2020, 20(9): 107-111. |
| [2] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [3] | XIA Tianyu, GU Yijun. A Dynamic Link Prediction Method Based on Improved Dynamic Triad Model [J]. Netinfo Security, 2020, 20(9): 97-101. |
| [4] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [5] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| [6] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [7] | WU Zenan, TIAN Liqin, CHEN Nan. Research on Quantitative Analysis of System Security Based on Stochastic Petri Net [J]. Netinfo Security, 2020, 20(9): 27-31. |
| [8] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| [9] | WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model [J]. Netinfo Security, 2020, 20(9): 6-11. |
| [10] | YU Xiaojun, WU Yabiao, ZHANG Yuqing. Research on the Design of Cloud Security Architecture [J]. Netinfo Security, 2020, 20(9): 62-66. |
| [11] | LIU Wenmao, YOU Yang. Shifting Security Protection Mindset and Mechanisms for Novel 5G Infrastructures [J]. Netinfo Security, 2020, 20(9): 67-71. |
| [12] | BI Qinbo, ZHAO Chengdong. Research and Application of 5G Cybersecurity Threat Modeling Based on STRIDE-LM [J]. Netinfo Security, 2020, 20(9): 72-76. |
| [13] | YU Guo, WANG Chonghua, CHEN Xuehong, LI Jun. Industrial Internet Identifier Resolution Security from the Perspective of Authentication [J]. Netinfo Security, 2020, 20(9): 77-81. |
| [14] | LIU Hong, XIE Yongheng, WANG Guowei, JIANG Shuai. Ontology-based Cross-domain Security Analysis [J]. Netinfo Security, 2020, 20(9): 82-86. |
| [15] | WANG Wenhua, HAO Xin, LIU Yan, WANG Yang. The Safety Evaluation and Defense Reinforcement of the AI System [J]. Netinfo Security, 2020, 20(9): 87-91. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||