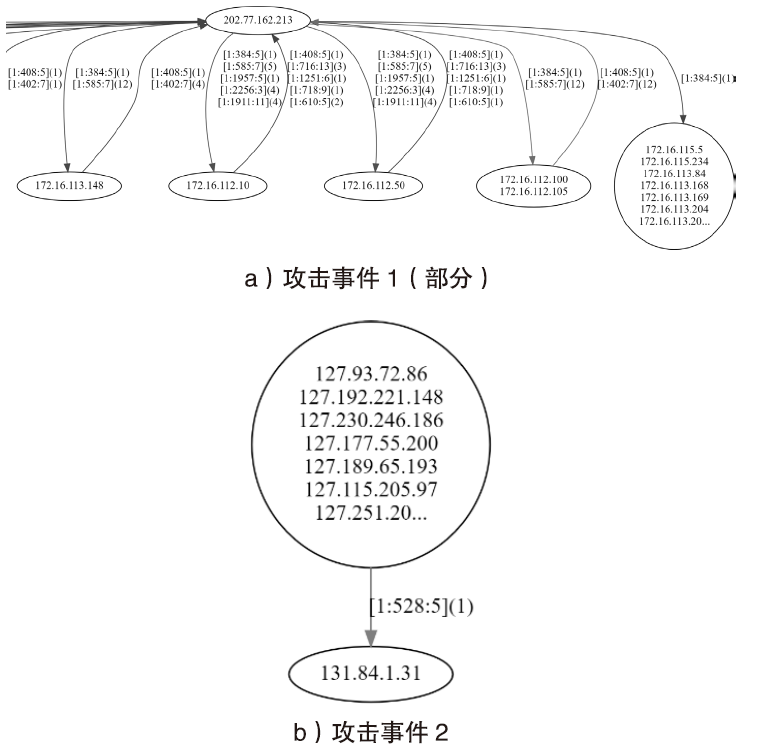
| [1] |
LIAO H J, LIN C H R, LIN Y C, et al. Intrusion Detection System: A Comprehensive Review[J]. Journal of Network & Computer Applications, 2013:36(1):16-24.
|
| [2] |
KIM J, SHIN N, JO S Y, et al. Method of Intrusion Detection Using Deep Neural Network[C]// IEEE. 2017 IEEE International Conference on Big Data and Smart Computing(BigComp), February 13-16, 2017, Jeju, South Korea. New Jersey: IEEE, 2017:313-316.
|
| [3] |
BENDOVSCHI A . Cyber-Attacks—Trends, Patterns and Security Countermeasures[EB/OL]. https://www.sciencedirect.com/science/article/pii/S2212567115010771, 2020-2-15.
|
| [4] |
TJHAI G C, PAPADAKI M, FURNELL S, et al. Investigating the Problem of IDS False Alarms: An Experimental Study Using Snort[C]// Springer. The IFIP TC 11 23rd International Information Security Conference, September 7-10, 2008, Milano, Italy. Heidelberg: Springer, 2008: 253-367.
|
| [5] |
NEHINBE J O. A Review of Technical Issues on IDS and Alerts[J]. Global Journal Of Computer Science And Technology, 2018,17(5):51-58.
|
| [6] |
PERDISCI R, GIACINTO G, ROLI F. Alarm Clustering for Intrusion Detection Systems in Computer Networks[J]. Machine Learning and Data Mining in Pattern Recognition, 2005,19(4):184-193.
|
| [7] |
KOTPALLIWAR M V, WAJGI R D. Classification of Attacks Using Support Vector Machine(SVM) on KDDCUP'99 IDS Database[C]// IEEE. 15th International Conference on Communication Systems and Network Technologies, April 4-6, 2015, Gwalior, India. New Jersey: IEEE, 2015: 987-990.
|
| [8] |
TEMPLETON S J, LEVITT K. A Requires/Provides Model for Computer Attacks[C]// ACM. The 2000 Workshop on New Security Paradigms, February 23-25, 2000, Ballycotton, County Cork, Ireland. New York: ACM, 2000: 31-38.
|
| [9] |
NING P, CUI Y, REEVES D S. Constructing Attack Scenarios through Correlation of Intrusion Alerts[EB/OL]. http://citeseer.ist.psu.edu/viewdoc/download;jsessionid=0C0DC8318D96FD659364FFFE6FFF5587?doi=10.1.1.57.8612&rep=rep1&type=pdf, 2020-2-11.
|
| [10] |
LIU Jianyi, LI Sida, ZHANG Ru. Algorithm of Reducing the False Positives in IDS Based on Correlation Analysis[EB/OL]. http://iopscience.iop.org/article/10.1088/1757-899X/322/6/062016/pdf, 2020-2-11.
|
| [11] |
ZALI Z, HASHEMI M R, SAIDI H. Real-Time Intrusion Detection Alert Correlation and Attack Scenario Extraction Based on the Prerequisite Consequence Approach[EB/OL]. https://www.researchgate.net/publication/276355385_REAL-TIME_INTRUSION_DETECTION_ALERT_CORRELATION_AND_ATTACK_SCENARIO_EXTRACTION_BASED_ON_THE_PREREQUISITE-CONSEQUENCE_APPROACH, 2020-2-11.
|
| [12] |
ALSERHANI F, AKHLAQ M, AWAN I U, et al. MARS: Multi-stage Attack Recognition System[C]// IEEE. 24th IEEE International Conference on Advanced Information Networking and Applications, April 20-13, 2010, Perth, Australia. New Jersey: IEEE, 2010: 753-759.
|
| [13] |
AZODI A, CHENG F, MEINEL C. Towards Better Attack Path Visualizations Based on Deep Normalization of Host/Network IDS Alerts[C]// IEEE. International Conference on Advanced Information Networking & Applications, March 23-25, 2016, Crans-Montana, Switzerland. New Jersey: IEEE, 2016: 1064-1071.
|
| [14] |
AZODI A, JAEGER D, CHENG F, et al. A New Approach to Building A Multi-tier Direct Access Knowledgebase for IDS/SIEM Systems[C]// IEEE. 11th International Conference on Dependable, Autonomic and Secure Computing, December 21-22, 2013, Chengdu, China. New Jersey: IEEE, 2013: 118-123.
|
| [15] |
WU Dong. Research on Key Technologies of Alert Correlation Based on Data Mining[D]. Guiyang: Guizhou University, 2019.
|
|
吴东. 基于数据挖掘的告警关联关键技术研究[D]. 贵阳:贵州大学, 2019.
|
| [16] |
LIU Bowen. Research on IDS Alert Log Scenario Mining Model Based on Neural Network and Bayesian Network Attack Graph[D]. Beijing: Beijing University of Posts and Telecommunications, 2019.
|
|
刘博文. 基于神经网络和贝叶斯网络攻击图的IDS告警日志场景挖掘模型研究[D]. 北京:北京邮电大学, 2019.
|
| [17] |
HAAS S, FISCHER M. GAC: Graph-based Alert Correlation for the Detection of Distributed Multi-step Attacks[C]// ACM. The 33rd Annual ACM Symposium on Applied Computing, April 21-23, 2018, New York, USA. New Jersey: ACM, 2018: 979-988.
|
| [18] |
SHAH S A R, ISSAC B. Performance Comparison of Intrusion Detection Systems and Application of Machine Learning to Snort System[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0167739X17323178, 2020-2-11.
|
 ), CUI Yaohui1, WANG Jian4,5, WU Jinchao1
), CUI Yaohui1, WANG Jian4,5, WU Jinchao1