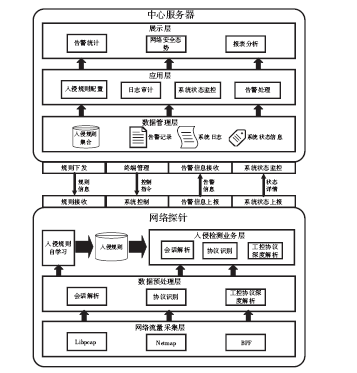
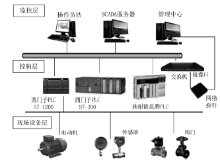
| [1] |
STOUFFER K A,FACLO J A,SCARFONE K A.Guide to Industrial Control Systems (ICS) Security - Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and other control system configurations such as Programmable Logic Controllers (PLC) [R]. Gaithersburg, Maryland, USA: National Institute of Standards and Technology (NIST), NIST SP - 800-82,2011.
|
| [2] |
PENG Y,JIANG C Q,XIE F,et al.Industrial Control System Cybersecurity Research[J]. Journal of Tsinghua University: Science and Technology, 2012, 52(10):1396-1408.
|
| [3] |
KNAPP E.Industrial Network Security—Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control Systems [M]. Translated by Zhou Qin, Guo Bingyi, He Huimin, et al. Beijing: National Defense Industry Press, 2014.
|
| [4] |
Office of the Press Secretary,The White House. Presidential Policy Directive -- Critical Infrastructure Security and Resilience [EB/OL]. https://obamawhitehouse.archives.gov/the-press-office/2013/02/12/presidential-policy-directive-critical-infrastructure-security-and-resil,2013-2-12.
|
| [5] |
Industrial Control Systems Cyber Emergency Response Team. ICS-CERT Year in Review2013, 13-50369[EB/OL].
|
| [6] |
LIND O, MANIC M, VOLLMER T, et al.Fuzzy Logic Based Anomaly Detection for Embedded Network Security Cyber Sensor[C]//IEEE.Proc of IEEE Symp on Computational Intelligence in Cyber Security,April 11-15, 2011,Paris, France. NJ: IEEE, 2011:202-209.
|
| [7] |
STAVROULAKIS P, STAMP M.Handbook of Information and Communication Security[M]. Berlin: Springer, 2010.
|
| [8] |
MITCHELL R, CHEN I R.A Survey of Intrusion Detection Techniques for Cyber Physical Systems[J]. ACM Computing Survey, 2014, 46(4):55-84.
|
| [9] |
PAN S Y, MORRIS T H, ADHIKARI U, et al.Causal Event Graphs Cyber-Physical System Intrusion Detection System[C]// ACM. CSIIRW '13 Proceedings of the Eighth Annual Cyber Security and Information Intelligence Research Workshop,January 8-10, 2013,Oak Ridge, Tennessee, USA. New York: ACM, 2013:40.
|
| [10] |
MORRIS T, VAUGHN R, DANDASS Y.A Retrofit Network Intrusion Detection System for MODBUS RTU and ASCII Industrial Control Systems[C]// IEEE. HICSS '12 Proceedings of the 2012 45th Hawaii International Conference on System Sciences,January 4-7, 2012,Maui, HI, USA. Piscataway, NJ: IEEE, 2012: 2338-2345.
|
| [11] |
LIN H,SLAGELL A,MARTINO C D, et al.Adapting Bro into SCADA: Building a Specification-based Intrusion Detection System for the DNP3 Protocol[C]// ACM. CSIIRW '13 Proceedings of the Eighth Annual Cyber Security and Information Intelligence Research Workshop. New York: ACM, 2013:1-4.
|
| [12] |
GOETZ E,SHENOI S.Critical Infrastructure Protection[M].Boston: Springer, 2008:161-173.
|
| [13] |
YANG D Y, USYNIN A, HINES J W. Anomaly-based Intrusion Detection for SCADA Systems[EB/OL]. https://www.researchgate.net/publication/228595190_Anomaly-based_intrusion_detection_for_SCADA_systems,2015-6-24.
|
| [14] |
MORRIS T, VAUGHN R, DANDASS Y.A Retrofit Network Intrusion Detection System for MODBUS RTU and ASCII Industrial Control Systems[C]// IEEE. HICSS '12 Proceedings of the 2012 45th Hawaii International Conference on System Sciences,January 4 - 7, 2012,Maui, HI, USA. Piscataway, NJ: IEEE, 2012: 2338-2345.
|
| [15] |
陈晓兵,陈凯,徐震,等. 面向工业控制网络的安全监管方案[J]. 信息网络安全,2016(7):61-70.
|
| [16] |
YANG Y, MCLAUGHLIN K,LITTLER T,et al. Intrusion Detection System for IEC 60870-5-104 Based SCADA Networks [EB/OL]// https://www.researchgate.net/publication/259802840_Intrusion_Detection_System_for_IEC_60870-5-104_based_SCADA_networks,2013-7-15.
|
| [17] |
王友俊,张红旗,王津,等. 面向任务的网络空间故障定位模型[J]. 信息网络安全,2017(4):61-70.
|
 ), Limin SUN2,3
), Limin SUN2,3