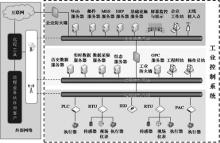
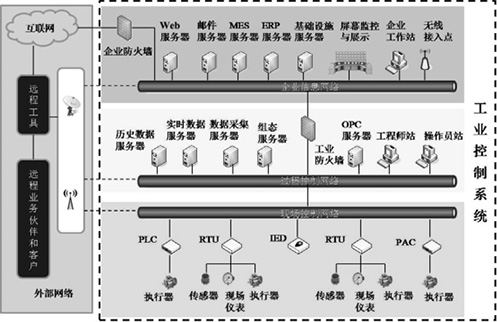
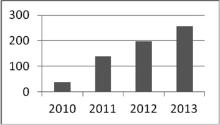
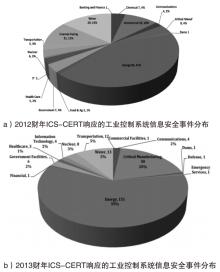
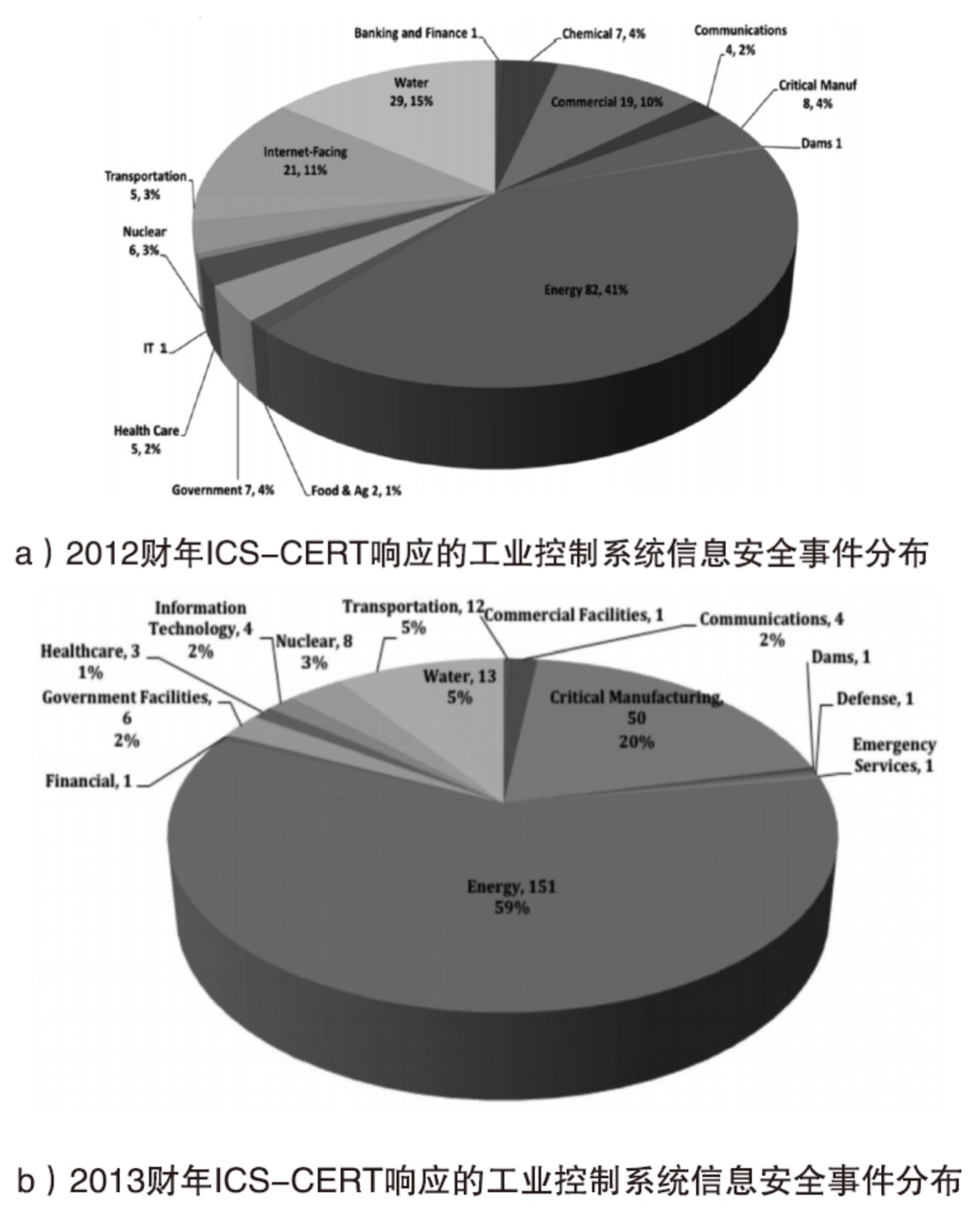
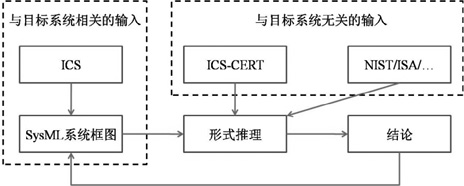
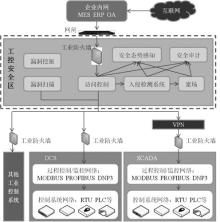
| [1] |
北京神州绿盟信息安全科技股份有限公司. 2013工业控制系统及其安全性研究报告[EB/OL]., 2014-10-10.
|
| [2] |
ICS-CERT. ICS-CERT Monitor October/November/December2012[EB/OL]., 2014-10-10.
|
| [3] |
ICS-CERT. ICS-CERT Monitor April/May/June2013[EB/OL]. , 2014-10-10.
|
| [4] |
Michael Robinson.The SCADA threat landscape[C]// Proceedings of 1st International Symposium for ICS &SCADA Cyber Security Research, 2013:33-41.
|
| [5] |
Yasakethu S.L.P., Jiang J. Intrusion detection via machine learning for SCADA system protection[C]// Proceedings of 1st International Symposium for ICS &SCADA Cyber Security Research, 2013:101-105.
|
| [6] |
Provos N.A virtual honeypot framework[C]// Proceedings of the 13th Conference on USENIX Security Symposium, 2004:1-14.
|
| [7] |
Paul Baecher, Markus Koetter, Thorsten Holz, et al.The Nepenthes platform: An efficient approach to collect malware[C]//Proceedings of 9th International Symposium on Recent Advances in Intrusion Detection (RAID 2006), 2006:165-184.
|
| [8] |
Nepenthes Development Team. Dionaea[EB/OL]. , 2011-05-15.
|
| [9] |
Kieran McLaughlin, Sakir Sezer, Paul Smith, et al. PRECYSE: Cyber-attack detection and response for industrial control systems[C]// Proceedings of the 2nd International Symposium for ICS &SCADA Cyber Security Research, 2014:67-71.
|
| [10] |
Laurens Lemaire, Jorn Lapon, Bart De Decker, et al.A SysML extension for security analysis of industrial control systems [C]//Proceedings of the 2nd International Symposium for ICS &SCADA Cyber Security Research, 2014: 1-9.
|
| [11] |
Robert Oates, Fran Thom, Graham Herries.Security-aware, model-based systems engineering with SysML[C]// Proceedings of the 1st International Symposium for ICS &SCADA Cyber Security Research, 2013:78-87.
|
| [12] |
Ivan Cibrario Bertolotti, Luca Durante, Tingting Hu, et al.A Model for the Analysis of Security Policies in Industrial Networks[C]// Proceedings of the 1st International Symposium for ICS &SCADA Cyber Security Research, 2013: 66-77.
|
| [13] |
Andrew John Charles Blyth. Role logic and its application to the analysis of process control systems from the Socio—Technical system perspective [C]//Proceedings of the 1st International Symposium for ICS &SCADA Cyber Security Research, 2013:42-47.
|
| [14] |
Benjamin Green, Daniel Prince, Utz Roedig, et al.Socio-Technical security analysis of industrial control systems (ICS)[C]//Proceedings of the 2nd International Symposium for ICS & SCADA Cyber Security Research, 2014:10-14.
|
 ), SUN Li-min1
), SUN Li-min1