Netinfo Security ›› 2015, Vol. 15 ›› Issue (1): 12-15.doi: 10.3969/j.issn.1671-1122.2015.01.003
Previous Articles Next Articles
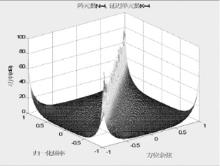
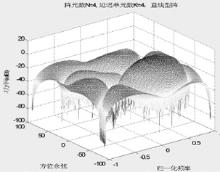
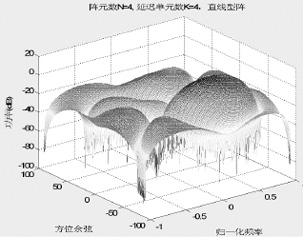
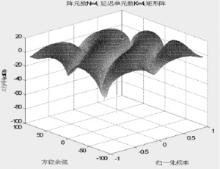
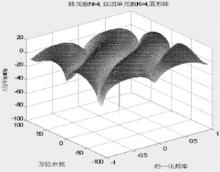
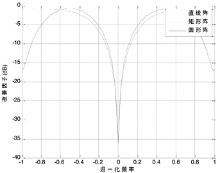
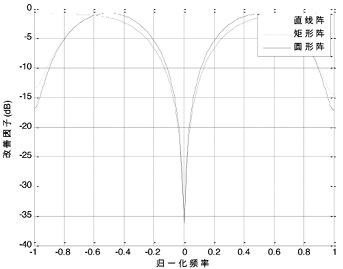
Study on Selection of the Antenna Array in Compass Navigation System
LIU Bao-guo1, XU Ling-wei1( ), ZHANG Hao1,2, GULLIVER T A2
), ZHANG Hao1,2, GULLIVER T A2
- 1. Department of Information Science and Engineering, Ocean University of China, Qingdao Shandong 266100, China
2. Department of Electrical and Computer Engineering, University of Victoria, Victoria V8W 3P6, Canada
-
Received:2014-12-04Online:2015-01-10Published:2015-07-05
CLC Number:
Cite this article
LIU Bao-guo, XU Ling-wei, ZHANG Hao, GULLIVER T A. Study on Selection of the Antenna Array in Compass Navigation System[J]. Netinfo Security, 2015, 15(1): 12-15.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2015.01.003
| [1] | UPTON D M, UPADAISY T N, MARCHESE J.Commercial-Off-The Shelf (COTS) GPS interference canceler and test results[C]//ION Navigation Conference, 1998. |
| [2] | CAPOZZA P T, HOLLAND B J, HOPKINS T M .A Single Chip narrow band frequency domain excisor for a global positioning system (GPS) receiver[J]. IEEE Journal of Solid State Circuits, 2000, 35(3): 40-41. |
| [3] | ZOLTOWSKI M D, GECAN A S.Advanced adaptive null steering concepts for GPS[C]// IEEE MILCOM’95, West Lafayette, IN,USA, 1995. |
| [4] | FANTE R L, VACCARO J J.Wideband cancellation of interference in a GPS receive array[J]. IEEE Trans. on Aerospace and Electronic Systems, 2000, 36(2): 549-564. |
| [5] | 张琳,初海彬,张乃通. 卫星导航用户机空时滤波抗干扰技术[J]. 北京航空航天大学学报,2007,(1): 76-80. |
| [6] | 王艺,段哲民,杨阳. 基于空时自适应处理的多波束抗干扰改进算法[J]. 计算机工程与应用,2013,49(17):221-225. |
| [7] | MOHAMED E A,王永芳,谈展中. 用于GPS接收机的自适应算法抗干扰性能比较[J]. 北京航空航天大学学报,2006,32(5):561-565. |
| [8] | 卢昕,熊昌仑,郑建生,等. 基于DSP技术的GPS接收机天线自适应抗干扰模块的设计与实现[J]. 武汉大学学报(信息科学版),2005,30(7):654-657. |
| [9] | STILES J, SINHA V, NANDA A P.Space-Time Transmit Signal Construction for Multi-Mode Radar[C] //IEEE Conference on Radar. 2006. |
| [10] | 郭艺,张尔扬. 空时自适应滤波抗干扰分析[J]. 航天电子对抗,2007,23(3):54-56. |
| [11] | BRENNAN L E, MALLET J D, REED I S. Adaptive arrays in airborne MTI radar[J]. IEEE Trans. Antennas Propagation, 1976, AP-24(5):607-615. |
| [12] | 何振亚. 自适应信号处理[M]. 北京:科学出版社,2002. |
| [13] | GRIFFITHS L J, IM C W. An alternative approach to linearly constrained adaptive beamforming[J]. IEEE Trans on Antennas Propagation, 1982, AP-30(1): 27-34. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems [J]. Netinfo Security, 2024, 24(7): 1015-1026. |
| [3] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [4] | ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies [J]. Netinfo Security, 2024, 24(7): 1038-1049. |
| [5] | DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism [J]. Netinfo Security, 2024, 24(7): 1050-1061. |
| [6] | ZHOU Shucheng, LI Yang, LI Chuanrong, GUO Lulu, JIA Xinhong, YANG Xinghua. Context-Based Abnormal Root Cause Algorithm [J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| [7] | REN Changyu, ZHANG Ling, JI Hangyuan, YANG Liqun. Research on TTP Extraction Method Based on Pre-Trained Language Model and Chinese-English Threat Intelligence [J]. Netinfo Security, 2024, 24(7): 1076-1087. |
| [8] | CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website [J]. Netinfo Security, 2024, 24(7): 1088-1097. |
| [9] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [10] | SHEN Xiuyu, JI Weifeng. Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security [J]. Netinfo Security, 2024, 24(7): 1110-1121. |
| [11] | ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery [J]. Netinfo Security, 2024, 24(7): 1122-1128. |
| [12] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [13] | LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET [J]. Netinfo Security, 2024, 24(7): 983-992. |
| [14] | LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication [J]. Netinfo Security, 2024, 24(7): 993-1005. |
| [15] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||