Netinfo Security ›› 2024, Vol. 24 ›› Issue (7): 993-1005.doi: 10.3969/j.issn.1671-1122.2024.07.002
Previous Articles Next Articles
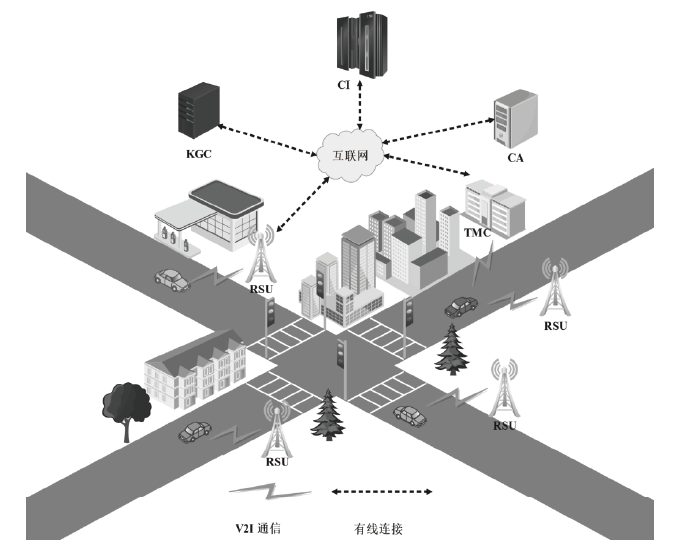
A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication
LUO Ming1( ), ZHAN Qibang1, QIU Minrong2
), ZHAN Qibang1, QIU Minrong2
- 1. School of Software, Nanchang University, Nanchang 330047, China
2. GongQing Institute of Science and Technology, Jiujiang 332020, China
-
Received:2024-03-26Online:2024-07-10Published:2024-08-02
CLC Number:
Cite this article
LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication[J]. Netinfo Security, 2024, 24(7): 993-1005.
share this article
| [1] | YUAN Xueliang, LIU Xin, ZUO Jian. The Development of New Energy Vehicles for a Sustainable Future: A Review[J]. Renewable and Sustainable Energy Reviews, 2015, 42: 298-305. |
| [2] | KENNEY J B. Dedicated Short-Range Communications (DSRC) Standards in the United States[J]. Proceedings of the IEEE, 2011, 99(7): 1162-1182. |
| [3] | JIN Chunhua. An Efficient Heterogeneous Signcryption for Smart Grid[EB/OL]. (2018-12-18)[2024-03-20]. https://doi.org/10.1371/journal.pone.0208311. |
| [4] | PAN Xiangyu, JIN Yuqiao, WANG Ziqing, et al. A Pairing-Free Heterogeneous Signcryption Scheme for Unmanned Aerial Vehicles[J]. IEEE Internet of Things Journal, 2022, 9(19): 19426-19437. |
| [5] | NIU Shufen, SHAO Honglin, HU Ying, et al. Privacy-Preserving Mutual Heterogeneous Signcryption Schemes Based on 5G Network Slicing[J]. IEEE Internet of Things Journal, 2022, 9(19): 19086-19100. |
| [6] | KANG Jiawen, YU Rong, HUANG Xumin, et al. Privacy-Preserved Pseudonym Scheme for Fog Computing Supported Internet of Vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2017, 19(8): 2627-2637. |
| [7] | QI Jiayu. A Pseudonym-Based Certificateless Privacy-Preserving Authentication Scheme for VANETs[EB/OL]. (2022-10-12)[2024-03-20]. https://doi.org/10.1016/j.vehcom.2022.100535. |
| [8] | GENC Y. ELCPAS: A New Efficient Lightweight Certificateless Conditional Privacy Preserving Authentication Scheme for IoV[EB/OL]. (2022-11-17)[2024-03-20]. https://doi.org/10.1016/j.vehcom.2022.100549. |
| [9] | GORDON S D, KATZ J, VAIKUNTANATHAN V. A Group Signature Scheme from Lattice Assumptions[C]// Springer. Advances in Cryptology-ASIACRYPT 2010: 16th International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2010: 395-412. |
| [10] | EZERMAN M F, LEE H T, LING San, et al. Provably Secure Group Signature Schemes from Code-Based Assumptions[J]. IEEE Transactions on Information Theory, 2020, 66(9): 5754-5773. |
| [11] | DEVIDAS S, RAO Y S, REKHA N R. A Decentralized Group Signature Scheme for Privacy Protection in a Blockchain[J]. International Journal of Applied Mathematics and Computer Science, 2021, 31(2): 353-364. |
| [12] | LIU J K, AU M H, SUSILO W, et al. Linkable Ring Signature with Unconditional Anonymity[J]. IEEE Transactions on Knowledge and Data Engineering, 2013, 26(1): 157-165. |
| [13] | ALBERTO T W A, STENINFELD R, SAKZAD A, et al. Post-Quantum One-Time Linkable Ring Signature and Application to Ring Confidential Transactions in Blockchain (Lattice RingCT v1. 0)[C]// Springer. Information Security and Privacy:23rd Australasian Conference, ACISP 2018. Heidelberg: Springer, 2018: 558-576. |
| [14] | YU Huifang. Certificateless Multi-Source Elliptic Curve Ring Signcryption for Cloud Computing[EB/OL]. (2023-03-07)[2024-03-20]. https://doi.org/10.1016/j.jisa.2023.103449. |
| [15] | YUAN Chao, ZHANG Wenfang, WANG Xiaomin. EIMAKP: Heterogeneous Cross-Domain Authenticated Key Agreement Protocols in the EIM System[J]. Arabian Journal for Science and Engineering, 2017, 42: 3275-3287. |
| [16] | JIANG Xin, LIU Mingzhe, YANG Chen, et al. A Blockchain-Based Authentication Protocol for WLAN Mesh Security Access[J]. Computers, Materials & Continua, 2019, 58(1): 45-59. |
| [17] | GONG Bei, ZHENG Guiping, WAQAS M, et al. LCDMA: Lightweight Cross-Domain Mutual Identity Authentication Scheme for Internet of Things[J]. IEEE Internet of Things Journal, 2023, 10(14): 12590-12602. |
| [18] | RIVEST R L, SHAMIR A, TAUMAN Y. How to Leak a Secret[C]// Springer. Advances in Cryptology—ASIACRYPT 2001: 7th International Conference on the Theory and Application of Cryptology and Information Security Gold Coast. Heidelberg: Springer, 2001: 552-565. |
| [19] | LIU D Y W, LIU J K, MU Yi, et al. Revocable Ring Signature[J]. Journal of Computer Science and Technology, 2007, 22: 785-794. |
| [20] | FUJISAKI E, SUZUKI K. Traceable Ring Signature[C]// Springer. International Workshop on Public Key Cryptography. Heidelberg: Springer, 2007: 181-200. |
| [21] | LIANG Weibiao. LRS_PKI: A Novel Blockchain-Based PKI Framework Using Linkable Ring Signatures[EB/OL]. (2023-09-25)[2024-03-20]. https://doi.org/10.1016/j.comnet.2023.110043. |
| [22] | HUANG Xinyi, SUSILO W, MU Yi, et al. Identity-Based Ring Signcryption Schemes: Cryptographic Primitives for Preserving Privacy and Authenticity in the Ubiquitous World[C]// IEEE. 19th International Conference on Advanced Information Networking and Applications (AINA'05) Volume 1 (AINA papers). New York: IEEE, 2005: 649-654. |
| [23] | LIU Feng, WANG Qi. IBRS: An Efficient Identity-Based Batch Verification Scheme for VANETs Based on Ring Signature[C]// IEEE. 2019 IEEE Vehicular Networking Conference (VNC). New York: IEEE, 2019: 1-8. |
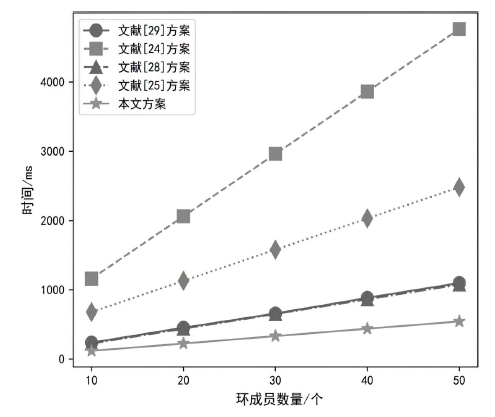
| [24] | CAI Ying, ZHANG Hao, FANG Yuguang. A Conditional Privacy Protection Scheme Based on Ring Signcryption for Vehicular Ad Hoc Networks[J]. IEEE Internet of Things Journal, 2020, 8(1): 647-656. |
| [25] | DU Hongzhen, WEN Qiaoyan, ZHANG Shanshan, et al. An Improved Conditional Privacy Protection Scheme Based on Ring Signcryption for VANETs[J]. IEEE Internet of Things Journal, 2023, 10(20): 17881-17892. |
| [26] | LUO Ming, ZHOU Yanzibo. An Efficient Conditional Privacy-Preserving Authentication Protocol Based on Generalized Ring Signcryption for VANETs[J]. IEEE Transactions on Vehicular Technology, 2022, 71(9): 10001-10015. |
| [27] | BOUAKKAZ S. A Certificateless Ring Signature Scheme with Batch Verification for Applications in VANET[EB/OL]. (2020-10-26)[2024-03-20]. https://doi.org/10.1016/j.jisa.2020.102669. |
| [28] | GUO Rui. An Efficient Certificateless Ring Signcryption Scheme with Conditional Privacy-Preserving in VANETs[EB/OL]. (2022-06-26)[2024-03-20]. https://doi.org/10.1016/j.sysarc.2020.102633. |
| [29] | LIU Shuanggen, LIU Zhentao, LIANG Jueqin, et al. Certificateless Ring Signcryption Scheme with Conditional Privacy Protection in Smart Grid[C]// Springer. International Conference on Frontiers in Cyber Security. Heidelberg: Springer, 2023: 189-204. |
| [30] | POINTCHEVAL D, STERN J. Security Arguments for Digital Signatures and Blind Signatures[J]. Journal of cryptology, 2000, 13: 361-396. |
| [31] | DE C A, IOVINO V. JPBC: Java Pairing Based Cryptography[C]// IEEE. 2011 IEEE Symposium on Computers and Communications (ISCC). New York: IEEE, 2011: 850-855. |
| [1] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [2] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [3] | LIU Jiqiang, WANG Xuewei, LIANG Mengqing, WANG Jian. A Hierarchical Federated Learning Framework Based on Shared Dataset and Gradient Compensation [J]. Netinfo Security, 2023, 23(12): 10-20. |
| [4] | LIU Longgeng. Research on Association Algorithm of Heterogeneous Network Security Monitoring [J]. Netinfo Security, 2022, 22(4): 58-66. |
| [5] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 22(3): 20-28. |
| [6] | WANG Sidie, MA Zhaofeng, LUO Shoushan, XU Danheng. Data Privacy-Preserving Scheme on Blockchain for Heterogeneous Multi-Chain [J]. Netinfo Security, 2022, 22(12): 67-75. |
| [7] | YU Xianrong, FAN Jiejie. Design of Collaborative Filtering Approach Recommendation Algorithm Based on Hadoop [J]. Netinfo Security, 2022, 22(10): 91-97. |
| [8] | WANG Jian, ZHAO Manli, CHEN Zhihao, SHI Bo. An Authentication Scheme for Conditional Privacy Preserving Based on Pseudonym in Intelligent Transportation [J]. Netinfo Security, 2021, 21(4): 49-61. |
| [9] | Yulei ZHANG, Guangping LUO, Huan WANG, Xiangzhen LIU. TPKC-CLPKC Heterogeneous Hybrid Signcryption Scheme under 5G Network [J]. Netinfo Security, 2019, 19(5): 30-37. |
| [10] | Suzhen CAO, Xiaoli LANG, Xiangzhen LIU, Fei WANG. New Heterogeneous Signcryption Scheme under 5G Network [J]. Netinfo Security, 2018, 18(11): 33-39. |
| [11] | Liu WANG, Zhenfu CAO, Xiaolei DONG. Research on Application of ID-based Designated Verifier Signature in Cross-domain Authentication [J]. Netinfo Security, 2017, 17(10): 63-68. |
| [12] | Weiwei YE, Qingyu OU, Xiaowu BAI. Research on Authentication Scheme of Cryptographic Service System Based on Service Architecture [J]. Netinfo Security, 2016, 16(5): 37-43. |
| [13] | Hai HUANG, Dong-qing XIE, Yi-zan SONG. Research on Authentication of WiFi-WiMAX Heterogeneous Wireless Network [J]. Netinfo Security, 2015, 15(6): 19-25. |
| [14] | . A Parallel Image Encryption Algorithm based on Chaotic and Bit Level Permutation [J]. , 2014, 14(4): 40-. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||