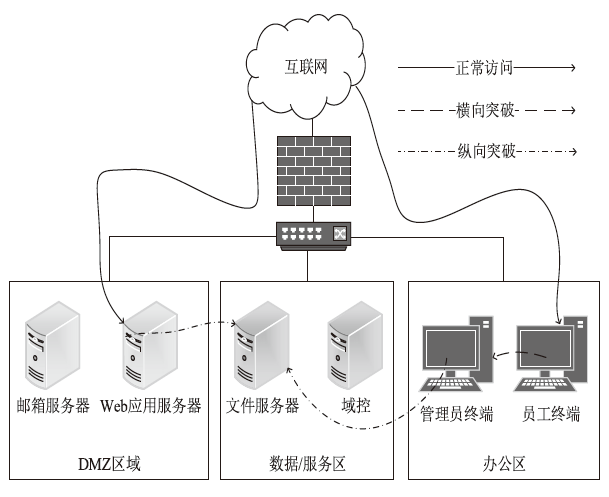
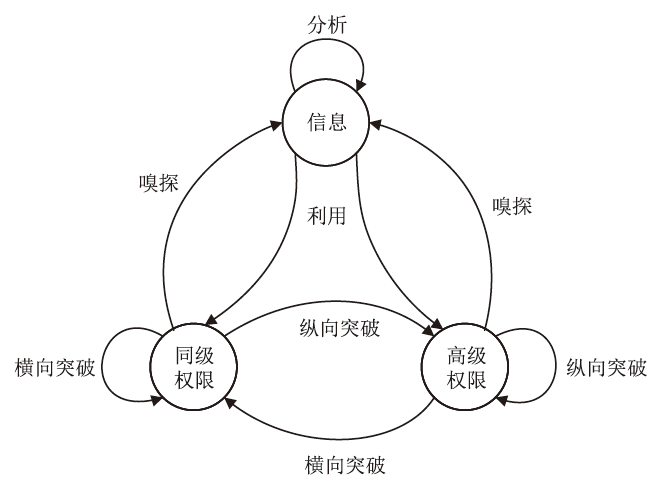
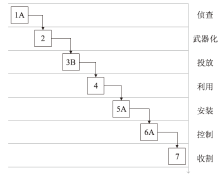
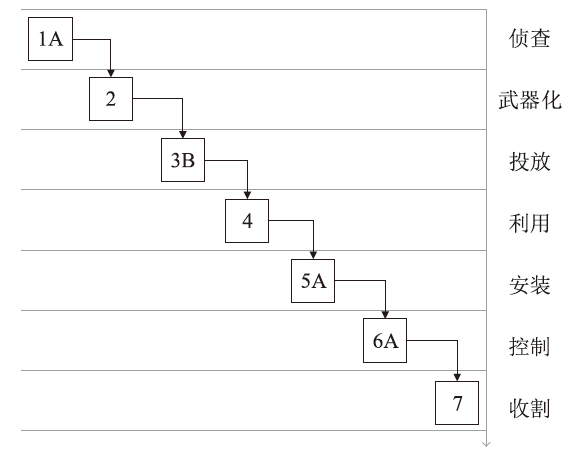
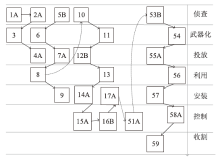
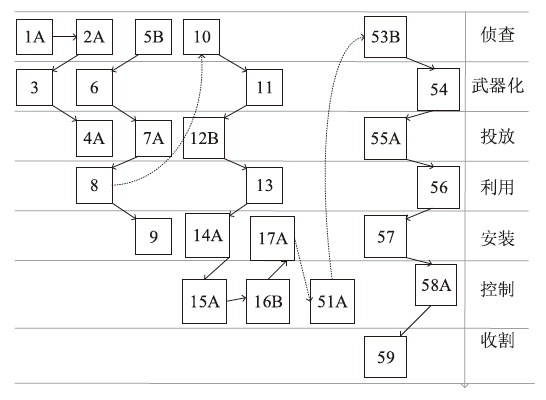
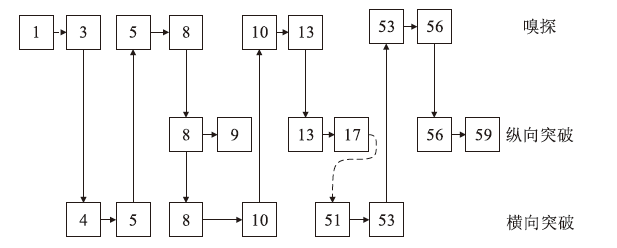
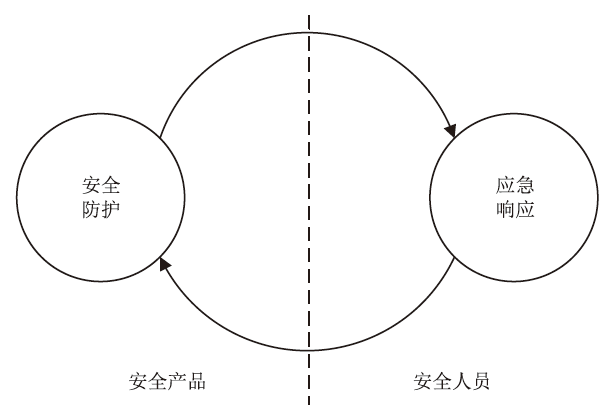
Netinfo Security ›› 2024, Vol. 24 ›› Issue (7): 1122-1128.doi: 10.3969/j.issn.1671-1122.2024.07.013
Previous Articles Next Articles
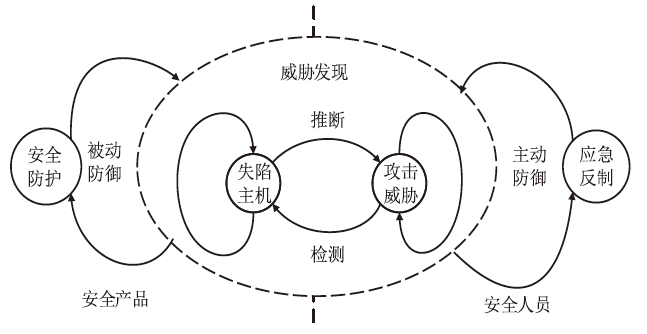
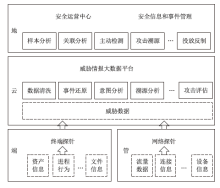
Research on APT Attack Defense System Based on Threat Discovery
ZHAO Xinqiang1,2, FAN Bo1( ), ZHANG Dongju1
), ZHANG Dongju1
- 1. China Electronic Standardization Institute, Beijing 100007, China
2. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100085, China
-
Received:2024-03-06Online:2024-07-10Published:2024-08-02
CLC Number:
Cite this article
ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery[J]. Netinfo Security, 2024, 24(7): 1122-1128.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.07.013
| [1] | DALY M K. Advanced Persistent Threat[J]. USENIX, 2009, 4(4): 2013-2016. |
| [2] | GUI Changni. General Situation, Typical Methods and Trend Analysis of Global Advanced Persistent Threats[J]. China Information Security, 2023(6): 85-90. |
| 桂畅旎. 全球高级持续性威胁总体态势、典型手法及趋势研判[J]. 中国信息安全, 2023(6):85-90. | |
| [3] | National Computer Virus Emergency Response Center. Report on the Investigation of Northwestern Polytechnical University’s Network Attack by the US NSA(Part One)[EB/OL]. (2022-09-05)[2024-02-26]. https://www.cverc.org.cn/head/zhaiyao/news20220905-NPU.htm. |
| 国家计算机病毒应急处理中心. 西北工业大学遭美国NSA网络攻击事件调查报告(之一)[EB/OL]. (2022-09-05)[2024-02-26]. https://www.cverc.org.cn/head/zhaiyao/news20220905-NPU.htm. | |
| [4] | National Computer Virus Emergency Response Center. Report on the Investigation of Northwestern Polytechnical University’s Network Attack by the US NSA(Part Two)[EB/OL]. (2022-09-27)[2024-02-26]. https://www.cverc.org.cn/head/zhaiyao/news20220927-NPU2.htm. |
| 国家计算机病毒应急处理中心. 西北工业大学遭美国NSA网络攻击事件调查报告(之二)[EB/OL]. (2022-09-27)[2024-02-26]. https://www.cverc.org.cn/head/zhaiyao/news20220927-NPU2.htm. | |
| [5] | BENCSÁTH B, PÉK G, BUTTYÁN L, et al. The Cousins of Stuxnet: Duqu, Flame, and Gauss[J]. Future Internet, 2012, 4(4): 971-1003. |
| [6] | China Information Technology Security Evaluation Center. Global Advanced Persistent Threat(APT) Situation Report[EB/OL]. (2023-04-25)[2024-02-26]. https://mp.weixin.qq.com/s/4MKJLbOiTBIbfVsLhV20zQ. |
| 中国信息安全测评中心. 全球高级持续性威胁(APT)态势报告[EB/OL]. (2023-04-25)[2024-02-26]. https://mp.weixin.qq.com/s/4MKJLbOiTBIbfVsLhV20zQ. | |
| [7] | Qianxin. Global Advanced Persistent Threats(APT) 2023 Annual Report[EB/OL]. (2024-02-02)[2024-02-26]. https://www.qianxin.com/threat/reportdetail?report_id=310. |
| 奇安信. 全球高级持续性威胁(APT)2023年度报告[EB/OL]. (2024-02-02)[2024-02-26]. https://www.qianxin.com/threat/reportdetail?report_id=310. | |
| [8] | 360 Threat Intelligence Center. 2023 Global Advanced Persistent Threat Research Report[EB/OL]. (2024-01-30)[2024-02-26]. https://mp.weixin.qq.com/s/NupRstKjdGUHHxQK2bz_MQ. |
| 360威胁情报中心. 2023全球高级持续性威胁研究报告[EB/OL][EB/OL]. (2024-01-30)[2024-02-26]. https://mp.weixin.qq.com/s/NupRstKjdGUHHxQK2bz_MQ. | |
| [9] | YAO Xingkun, ZHENG Xianwei. Full Packet Capture and Retrospective Forensics Combined with APT Modeling and Analysis Technology[J]. Journal of Fuzhou University (Natural Science Edition), 2023, 51(5): 639-646. |
| 姚星昆, 郑先伟. 全流量回溯结合APT建模分析技术[J]. 福州大学学报(自然科学版), 2023, 51(5):639-646. | |
| [10] | LUO Hanxin, WANG Jinshuang, WU Wenchang. Detecting Advanced Persistent Threats through Provenance Graph in Node Level[J]. Cyber Security and Data Governance, 2022, 41(10): 49-55. |
| 罗汉新, 王金双, 伍文昌. 基于溯源图节点级别的APT检测[J]. 网络安全与数据治理, 2022, 41(10):49-55. | |
| [11] | HUTCHINS E, CLOPPERT M, AMIN R. Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains[J]. Leading Issues in Information Warfare & Security Research, 2011, 1(1): 113-125. |
| [12] | LI Shufu, LI Xue, WANG Chao. Analysis of Typical APT Attack Cases[J]. Netinfo Security, 2016(S1): 85-88. |
| 李术夫, 李薛, 王超. 典型APT攻击事件案例分析[J]. 信息网络安全, 2016(S1): 85-88. | |
| [13] | Anquanke. 2046Lab Team APT Report: “Harvest Action”(DX-APT1)[EB/OL]. (2016-08-08)[2024-02-26]. https://www.anquanke.com/post/id/84353. |
| 安全客. 2046Lab团队APT报告:“丰收行动”(DX-APT1)[EB/OL]. (2016-08-08)[2024-02-26]. https://www.anquanke.com/post/id/84353. | |
| [14] |
LI Yuancheng, LUO Hao, WANG Xinyu, et al. Construction of Advanced Persistent Threat Attack Detection Model Based on Provenance Graph and Attention Mechanism[J]. Journal on Communications, 2024, 45(3): 117-130.
doi: 10.11959/j.issn.1000-436x.2024039 |
|
李元诚, 罗昊, 王欣煜, 等. 基于溯源图和注意力机制的APT攻击检测模型构建[J]. 通信学报, 2024, 45(3):117-130.
doi: 10.11959/j.issn.1000-436x.2024039 |
|
| [15] |
LI Yuancheng, LIN Yukun. APT Attack Threat-Hunting Network Model Based on Hypergraph Transformer[J]. Journal on Communications, 2024, 45(2): 106-114.
doi: 10.11959/j.issn.1000-436x.2024043 |
| [1] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [2] | GUO Zimeng, ZHU Guangjie, YANG Yijie, SI Qun. Research on Railway Network Security Performance Based on APT Characteristics [J]. Netinfo Security, 2024, 24(5): 802-811. |
| [3] | SUN Junfeng, LI Chenghai, SONG Yafei. ACCQPSO: An Improved Quantum Particle Swarm Optimization Algorithm and Its Applications [J]. Netinfo Security, 2024, 24(4): 574-586. |
| [4] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [5] | GAO Qingguan, ZHANG Bo, FU Anmin. An Advanced Persistent Threat Detection Method Based on Attack Graph [J]. Netinfo Security, 2023, 23(12): 59-68. |
| [6] | SHEN Chuanxin, WANG Yongjie, XIONG Xinli. DNS Covert Channel Detection Based on Graph Attention Network [J]. Netinfo Security, 2023, 23(1): 73-83. |
| [7] | LI Jiyu, FU Zhangjie, ZHANG Yubin. An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation [J]. Netinfo Security, 2023, 23(1): 93-102. |
| [8] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [9] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [10] | LIU Xin, WANG Jiayin, YANG Haorui, ZHANG Ruisheng. An Internet of Vehicles Authentication Protocol Based on Blockchain and secGear Framework [J]. Netinfo Security, 2022, 22(1): 27-36. |
| [11] | CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology [J]. Netinfo Security, 2021, 21(4): 39-48. |
| [12] | YU Qing, ZHENG Chonghui, DU Ye. Research on Key Technologies of Security Situation Assessment for the Virtual Layer of Cloud Platform [J]. Netinfo Security, 2020, 20(7): 53-59. |
| [13] | LIU Jing, ZHANG Xueqian, LIU Quanming. Research on Captcha Recognition of Lightweight Convolutional Neural Network with Gabor [J]. Netinfo Security, 2020, 20(7): 77-84. |
| [14] | ZHANG Xinyue, HU Anlei, LI Jurong, FENG Yanchun. A Method of Adaptive Abnormal Network Traffic Detection [J]. Netinfo Security, 2020, 20(12): 28-32. |
| [15] | Quanming LIU, Jie FENG, Yinnan LI, Shasha SU. A HIBE Scheme of Differentiates the Number of Identity Layers [J]. Netinfo Security, 2019, 19(11): 14-23. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||