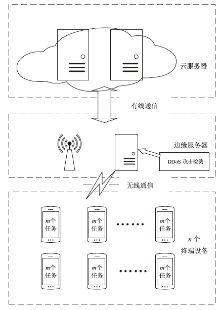
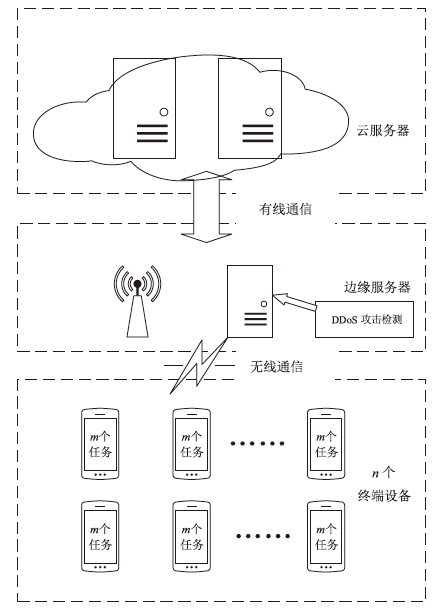
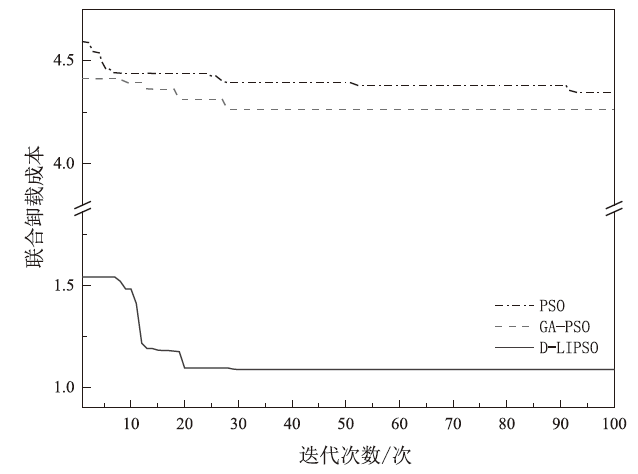
Netinfo Security ›› 2024, Vol. 24 ›› Issue (7): 1110-1121.doi: 10.3969/j.issn.1671-1122.2024.07.012
Previous Articles Next Articles
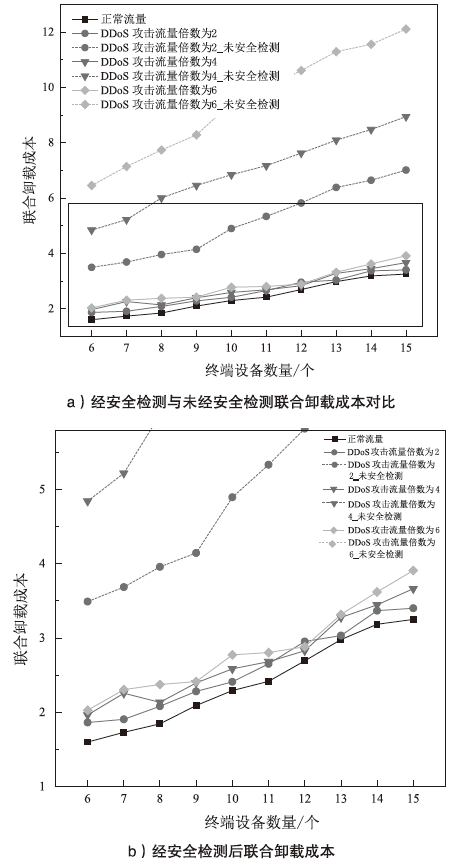
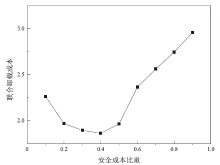
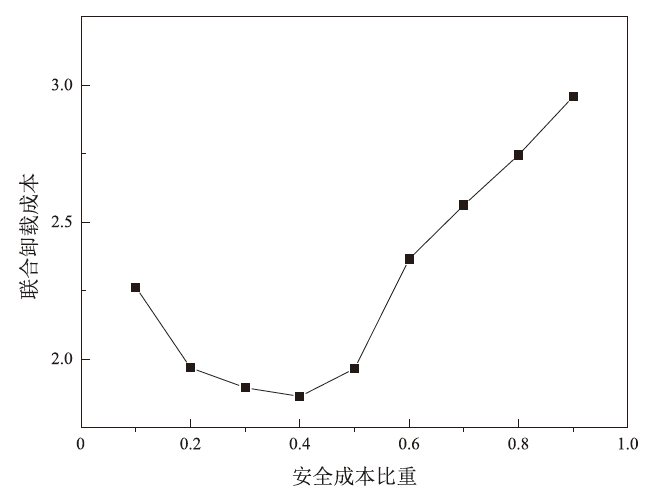
Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security
- Information and Navigation School, Air Force Engineering University, Xi’an 710077, China
-
Received:2024-03-26Online:2024-07-10Published:2024-08-02
CLC Number:
Cite this article
SHEN Xiuyu, JI Weifeng. Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security[J]. Netinfo Security, 2024, 24(7): 1110-1121.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.07.012
| [1] | LI Yiyang, FANG Yuan, QIU Ling. Joint Computation Offloading and Communication Design for Secure UAV-Enabled MEC Systems[C]// IEEE. 2021 IEEE Wireless Communications and Networking Conference (WCNC). New York: IEEE, 2021: 1-6. |
| [2] | SHI Weisong, SUN Hui, CAO Jie, et al. Edge Computing-An Emerging Computing Model for the Internet of Everything Era[J]. Journal of Computer Research and Development, 2017, 54(5): 907-924. |
| 施巍松, 孙辉, 曹杰, 等. 边缘计算:万物互联时代新型计算模型[J]. 计算机研究与发展, 2017, 54(5): 907-924. | |
| [3] | ZHANG Bingjie, YANG Yanhong, CAO Shaozhong. Review of Computing Offloading Schemes for Multi-Access Edge Computing[J]. Journal of Frontiers of Computer Science and Technology, 2023, 17(9): 2030-2046. |
|
张冰洁, 杨彦红, 曹少中. 面向多接入边缘计算的计算卸载方案研究综述[J]. 计算机科学与探索, 2023, 17(9): 2030-2046.
doi: 10.3778/j.issn.1673-9418.2301068 |
|
| [4] | ZHANG Yilin, LIANG Yuzhu, YIN Mujun, et al. Survey on the Methods of Computation Offloading in Mobile Edge Computing[J]. Chinese Journal of Computers, 2021, 44(12): 2406-2430. |
| 张依琳, 梁玉珠, 尹沐君, 等. 移动边缘计算中计算卸载方案研究综述[J]. 计算机学报, 2021, 44(12): 2406-2430. | |
| [5] |
XIE Renchao, LIAN Xiaofei, JIA Qingmin, et al. Survey on Computation Offloading in Mobile Edge Computing[J]. Journal on Communications, 2018, 39(11): 138-155.
doi: 10.11959/j.issn.1000-436x.2018215 |
|
谢人超, 廉晓飞, 贾庆民, 等. 移动边缘计算卸载技术综述[J]. 通信学报, 2018, 39(11): 138-155.
doi: 10.11959/j.issn.1000-436x.2018215 |
|
| [6] | ZHU Sifeng, ZHAO Mingyang, CHAI Zhengyi, et al. Computing Offloading Scheme Based on Particle Swarm Optimization Algorithm in Edge Computing Scene[J]. Journal of Jilin University (Engineering and Technology Edition), 2022, 52(11): 2698-2705. |
| 朱思峰, 赵明阳, 柴争义, 等. 边缘计算场景中基于粒子群优化算法的计算卸载[J]. 吉林大学学报(工学版), 2022, 52(11): 2698-2705. | |
| [7] | ZHOU Tianqing, ZENG Xinliang, HU Haiqin. Computation Offloading Cost Optimization Based on Hybrid Particle Swarm Optimization Algorithm[J]. Journal of Electronics & Information Technology, 2022, 44(9): 3065-3074. |
| 周天清, 曾新亮, 胡海琴. 基于混合粒子群算法的计算卸载成本优化[J]. 电子与信息学报, 2022, 44(9): 3065-3074. | |
| [8] | PAN Meini, LI Zhihua. Multi-User Computation Offloading Algorithm for Mobile Edge Computing[C]// ISAC. 2021 2nd International Conference on Electronics, Communications and Information Technology (CECIT). New York: IEEE, 2021: 771-776. |
| [9] | CHEN Lu, TANG Hongbo, YOU Wei, et al. Research on Security Defense of Mobile Edge Computing[J]. Chinese Journal of Network and Information Security, 2021, 7(1): 130-142. |
| [10] | HE Qiang, WANG Cheng, CUI Guangming, et al. A Game-Theoretical Approach for Mitigating Edge DDoS Attack[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(4): 2333-2348. |
| [11] | LIAN Xiaofei, XIE Renchao, HUANG Tao. Security-Based Computation Offloading Scheme in Edge Computing Network[J]. ZTE Technology Journal, 2019, 25(2): 41-46, 56. |
| 廉晓飞, 谢人超, 黄韬. 基于安全保障的边缘计算卸载方案[J]. 中兴通讯技术, 2019, 25(2): 41-46, 56. | |
| [12] | ZHOU Yi, YEOH P L, PAN Cunhua, et al. Offloading Optimization for Low-Latency Secure Mobile Edge Computing Systems[J]. IEEE Wireless Communication Letters, 2019, 9(4): 480-484. |
| [13] | PHAM Q V, NGUYEN H T, HAN Zhu, et al. Coalitional Games for Computation Offloading in NOMA-Enabled Multi-Access Edge Computing[J]. IEEE Transactions on Vehicular Technology, 2020, 69(2): 1982-1993. |
| [14] | ZHOU Tianqing, HU Haiqin, ZENG Xinliang. Cooperative Computation Offloading and Resource Management Based on Improved Genetic Algorithm in NOMA-MEC Systems[J]. Journal of Electronics & Information Technology, 2022, 44(9): 3014-3023. |
| 周天清, 胡海琴, 曾新亮. NOMA-MEC系统中基于改进遗传算法的协作式计算卸载与资源管理[J]. 电子与信息学报, 2022, 44(9): 3014-3023. | |
| [15] |
LI Shun, GE Haibo, LIU Linhuan, et al. Collaborative Computing Offloading Strategy in Mobile Edge Computing[J]. Computer Engineering and Applications, 2022, 58(21): 83-90.
doi: 10.3778/j.issn.1002-8331.2201-0015 |
|
李顺, 葛海波, 刘林欢, 等. 移动边缘计算中的协同计算卸载策略[J]. 计算机工程与应用, 2022, 58(21): 83-90.
doi: 10.3778/j.issn.1002-8331.2201-0015 |
|
| [16] | DAI Yueyue, XU Du, MAHARJAN S, et al. Joint Computation Offloading and User Association in Multi-Task Mobile Edge Computing[J]. IEEE Trans on Vehicular Technology, 2018, 67(12): 12313-12325. |
| [17] | YOU Jing, SHANGGUAN Jinglun, XU Shoukun, et al. Distributed Dynamic Trust Management Model Based on Trust Reliability[J]. Journal of Software, 2017, 28(9): 2354-2369. |
| 游静, 上官经伦, 徐守坤, 等. 考虑信任可靠度的分布式动态信任管理模型[J]. 软件学报, 2017, 28(9): 2354-2369. | |
| [18] |
SHEN Xiuyu, JI Weifeng, LI Yingqi, et al. TCA1C DDoS Detection Model for Edge Computing[J]. Computer Engineering, 2024, 50(1): 198-205.
doi: 10.19678/j.issn.1000-3428.0067572 |
|
申秀雨, 姬伟峰, 李映岐, 等. 面向边缘计算的TCA1C DDoS检测模型[J]. 计算机工程, 2024, 50(1): 198-205.
doi: 10.19678/j.issn.1000-3428.0067572 |
|
| [19] | ZHAO Guosheng, WANG Tiantian, WANG Jian. A Dynamic Trust Evaluation Model for Edge Devices[J]. Computer Engineering & Science, 2021, 43(9): 1574-1583. |
| 赵国生, 王甜甜, 王健. 一种边缘设备动态信任度的评估模型[J]. 计算机工程与科学, 2021, 43(9): 1574-1583. | |
| [20] | LI Xingqi, GAO Xiaohong. Study on Dimensionless Methods for Data Obeying Different Distributions[J]. Statistics & Decision, 2022, 38(10): 31-36. |
| 李兴奇, 高晓红. 服从不同分布数据的无量纲化方法研究[J]. 统计与决策, 2022, 38(10): 31-36. | |
| [21] | GUO Fengxian, ZHANG Heli, JI Hong, et al. An Efficient Computation Offloading Management Scheme in the Densely Deployed Small Cell Networks with Mobile Edge Computing[J]. IEEE/ACM Transactions on Networking, 2018, 26(6): 2651-2664. |
| [22] | SHI Yuhui, EBERHART R. A Modified Particle Swarm Optimizer[C]// IEEE. 1998 IEEE International Conference on Evolutionary Computation Proceedings. New York: IEEE, 1998: 69-73. |
| [23] |
WU Xuewen, LIAO Jingxian. Game-Based Resource Allocation and Task Offloading Scheme in Collaborative Cloud-Edge Computing System[J]. Journal of System Simulation, 2022, 34(7): 1468-1481.
doi: 10.16182/j.issn1004731x.joss.21-0077 |
|
吴学文, 廖婧贤. 云边协同系统中基于博弈论的资源分配与任务卸载方案[J]. 系统仿真学报, 2022, 34(7): 1468-1481.
doi: 10.16182/j.issn1004731x.joss.21-0077 |
|
| [24] | ZHAO Xiaolin, ZHAO Bin, ZHAO Jingjing, et al. Research on Network Security Measurement Method Based on Attack Identification[J]. Netinfo Security, 2021, 21(11): 17-27. |
| 赵小林, 赵斌, 赵晶晶, 等. 基于攻击识别的网络安全度量方法研究[J]. 信息网络安全, 2021, 21(11): 17-27. |
| [1] | CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website [J]. Netinfo Security, 2024, 24(7): 1088-1097. |
| [2] | WANG Jian, CHEN Lin, WANG Kailun, LIU Jiqiang. Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network [J]. Netinfo Security, 2024, 24(4): 509-519. |
| [3] | SUN Junfeng, LI Chenghai, SONG Yafei. ACCQPSO: An Improved Quantum Particle Swarm Optimization Algorithm and Its Applications [J]. Netinfo Security, 2024, 24(4): 574-586. |
| [4] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [5] | FAN Mingyu, LI Ke. A Method to Distinguish DDoS Attack Types Based on RNN [J]. Netinfo Security, 2022, 22(7): 1-8. |
| [6] | SONG Yulong, WANG Lei, WU Xinrong, ZENG Weijun. Research on WSN Topological Invulnerability Based on Adaptive Simulated Annealing Particle Swarm Optimization Algorithm [J]. Netinfo Security, 2021, 21(6): 89-96. |
| [7] | LUO Wenhua, CHENG Jiaxing. Hybrid DDoS Attack Distributed Detection System Based on Hadoop Architecture [J]. Netinfo Security, 2021, 21(2): 61-69. |
| [8] | WANG Jian, WANG Yujie, HAN Lei. DDoS Attack Detection Based on Catastrophe Theory in SDN Environment [J]. Netinfo Security, 2020, 20(5): 11-20. |
| [9] | Ke ZHANG, Youjie WANG, Shaoyin CHENG, Lidong WANG. Intrusion Collaborative Disposal Method of Spoofed IP Address in DDoS Attacks [J]. Netinfo Security, 2019, 19(5): 22-29. |
| [10] | Zhibin YU, Cheng MA, Siqi LI, Miao WANG. Research on DDoS Attack Model Based on Web Application Layer [J]. Netinfo Security, 2019, 19(5): 84-90. |
| [11] | Donghui MEI, Hongling LI. Research on Load Balancing of Virtual Machine Based on Multiple Objective Hybrid Particle Swarm Optimization [J]. Netinfo Security, 2018, 18(2): 78-83. |
| [12] | ZHANG Xuebo, LIU Jinghao, FU Xiaomei. Design and Implementation of Anti Web DDoS Attack Model Based on Improved Logistic Regression Algorithm [J]. 信息网络安全, 2017, 17(6): 62-67. |
| [13] | Jie LI, Xin XU, Yu CHEN, Ding-wen ZHANG. Research on Cloud Forensics Model under the Simulation DDoS Attack Scenarios [J]. Netinfo Security, 2015, 15(6): 67-72. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||