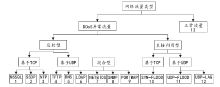
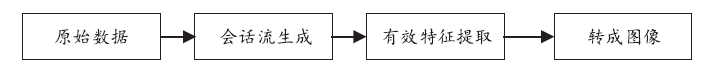
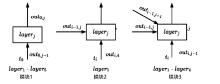
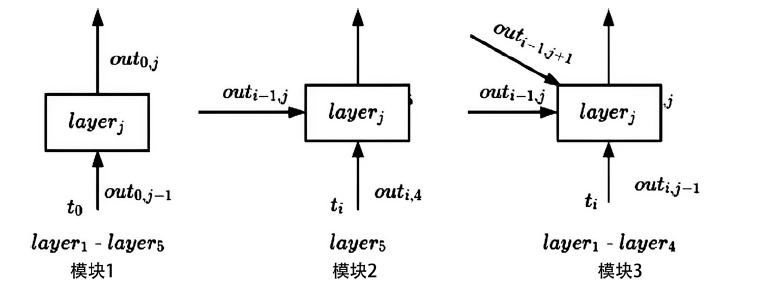
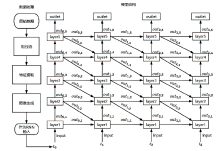
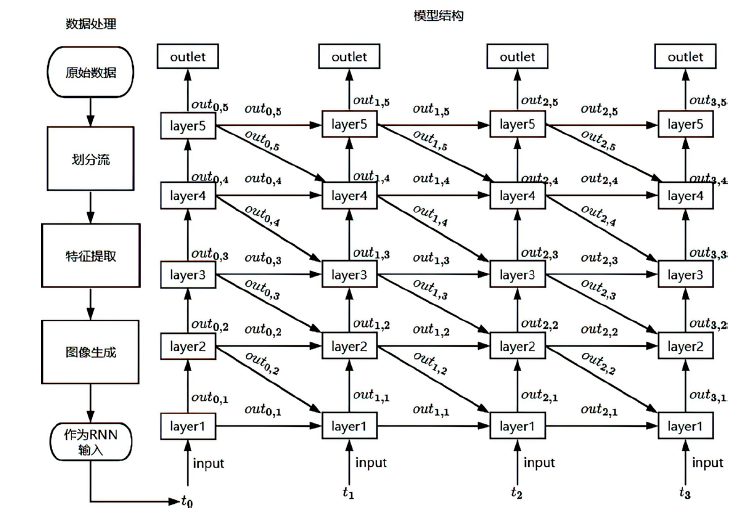
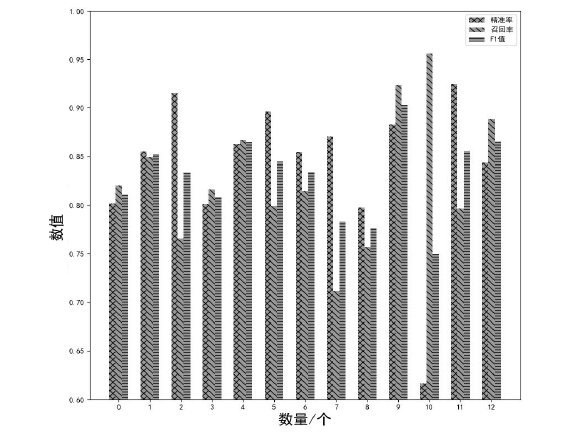
| [1] |
KELLI Young. Cyber Case Study: The Mirai DDoS Attack on Dyn[EB/OL]. (2016-11-30)[2022-04-01]. https://coverlink.com/case-study/mirai-ddos-attack-on-dyn/.
|
| [2] |
WANG Yichuan, MA Jianfeng, LU Di, et al. Game Optimization for Internal DDoS Attack Detection in Cloud Computing[J]. Journal of Computer Research and Development, 2015(8): 1873-1882.
|
|
王一川, 马建峰, 卢笛, 等. 面向云环境内部DDoS攻击检测的博弈论优化[J]. 计算机研究与发展, 2015(8):1873-1882.
|
| [3] |
LI Panhui, DING Wei, REN Wentao, et al. Authenticity Analysis on DDoS Attack Detection for IDS[J]. Journal of Southeast University(Natural Science Edition), 2017(47): 9-13.
|
|
李盼辉, 丁伟, 任文韬, 等. 面向IDS的DDoS攻击检测真实性分析[J]. 东南大学学报(自然科学版), 2017(47):9-13.
|
| [4] |
ZHANG Yongzheng, XIAO Jun, YUN Xiaochun, et al. DDoS Attacks Detection and Control Mechanisms[J]. Journal of Software, 2012, 23(8): 2058-2072.
doi: 10.3724/SP.J.1001.2012.04237
URL
|
|
张永铮, 肖军, 云晓春, 等. DDoS攻击检测和控制方法[J]. 软件学报, 2012(8):2058-2072.
|
| [5] |
MAZGAR J A, UMAR F, HAFIZ M A B, et al. Real-Time DDoS Attack Detection System Using Big Data Approach, Sustainability[EB/OL]. (2022-01-10)[2022-04-01]. https://doi.org/10.3390/su131910743.
|
| [6] |
TONG A T, HOANG V L, LE H S, et al. Performance Evaluation of Botnet DDoS Attack Detection Using Machine Learning, Evolutionary Intelligence[EB/OL]. (2021-09-10)[2022-04-01]. https://doi.org/10.1007/s12065-019-00310-w.
|
| [7] |
PRASAD M D, PRASANTA B V, AMARNATH C. Machine Learning DDoS Detection Using Stochastic Gradient Boosting[EB/OL]. (2021-12-10)[2022-04-01]. https://doi.org/10.26438/ijcse/v7i4.157166.
|
| [8] |
DORIGUZZI C R, SIRACUSA D. Lucid: A Practical, Lightweight Deep Learning Solution for DDoS Attack Detection[J]. IEEE Transactions on Network and Service Management, 2020, 2(17): 876-889.
|
| [9] |
NANDI S, PHADIKAR S, MAJUMDER K. Detection of DDoS Attack and Classification Using a Hybrid Approach[J]. 2020 Third ISEA Conference on Security and Privacy (ISEA-ISAP), 2020(1): 41-47.
|
| [10] |
CIC. DDoS Evaluation Dataset (CIC-DDoS2019))[EB/OL]. (2021-09-10)[2022-04-01]. https://www.unb.ca/cic/datasets/ddos-2019.html.
|
| [11] |
SHARAFALDIN I, LASHKARI H A, HAKAK S, et al. Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy[C]// IEEE. IEEE 53rd International Carnahan Conference on Security Technology. New York: IEEE, 2019: 1-8.
|
| [12] |
NETRESEC. SplitCap[EB/OL]. (2021-09-10)[2022-04-01]. https://www.netresec.com/?page=SplitCap.
|
| [13] |
ARASH H L. CIC Flow Meter[EB/OL]. (2021-09-10) [2022-04-02] https://github.com/ahlashkari/CICFlowMeter.
|
| [14] |
POTLURI S, AHMED S, DIEDRICH C. Convolutional Neural Networks for Multi-Class Intrusion Detection System[C]// Springer. Mining International Conference on Mining Intelligence and Knowledge Exploration. Heidelberg: Springer, 2018: 225-238.
|
| [15] |
ODENA A. Deconvolution and Checkerboard Artifacts[EB/OL]. (2022-03-27)[2022-04-01]. https://distill.pub/2016/deconv-checkerboard/.
|
| [16] |
KRIZHEVSKY A, SUTSKEVER I, HINTON E G. Image Net Classification with Deep Convolutional Neural Networks[J]. Communications of the ACM, 2017(6): 84-90.
|
| [17] |
SZEGEDY C, LIU Wei, JIA Yangqing, et al. Going Deeper with Convolutions[C]// IEEE. 2015 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2015: 1-9.
|
| [18] |
HE Kaiming, ZHANG Xiangyu, REN Jiansun, et al. Deep Residual Learning for Image Recognition[C]// IEEE. IEEE Computer Society. New York: IEEE, 2016: 770-778.
|