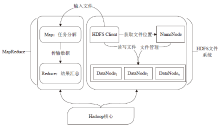
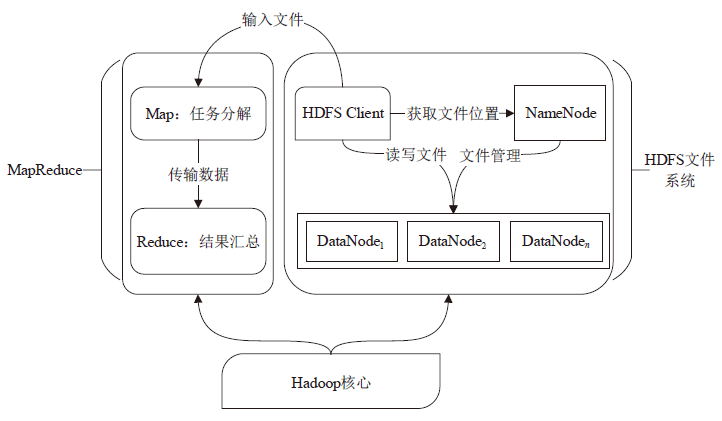
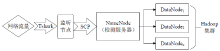
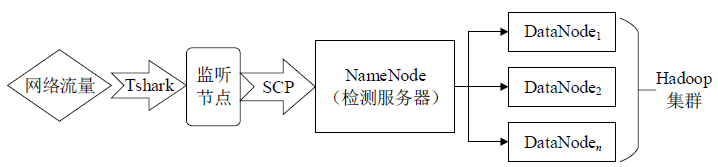
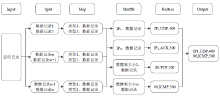
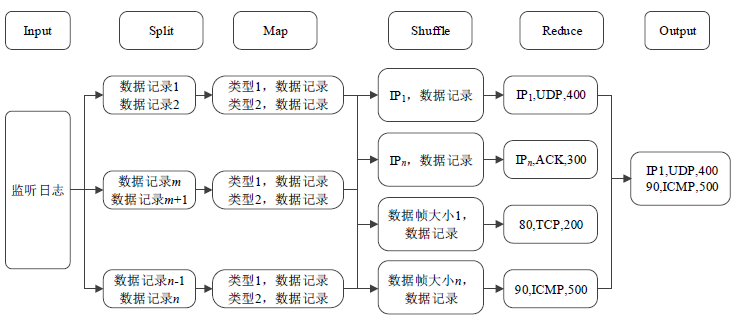
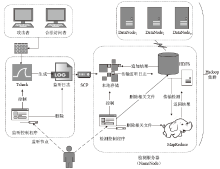
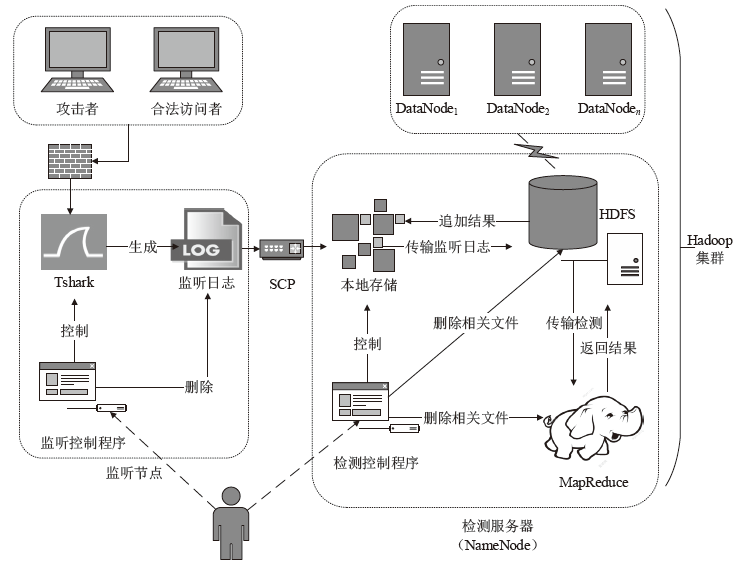
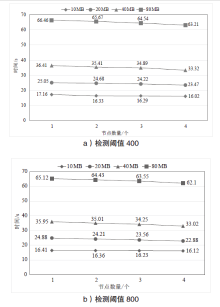
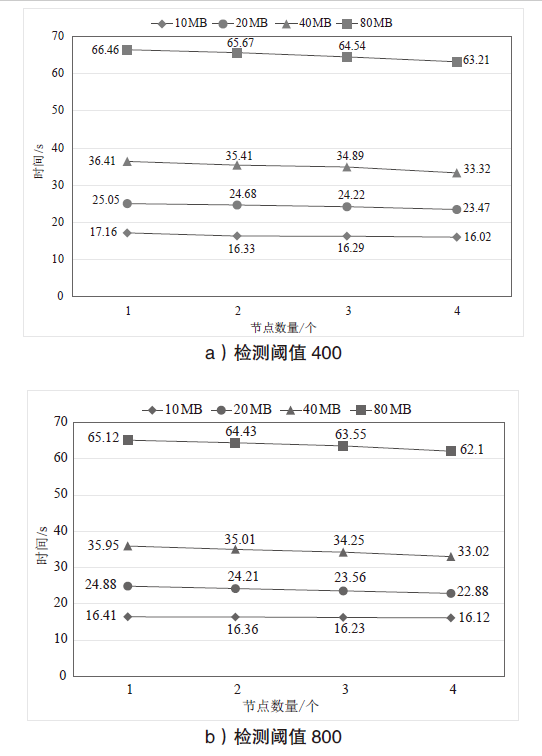
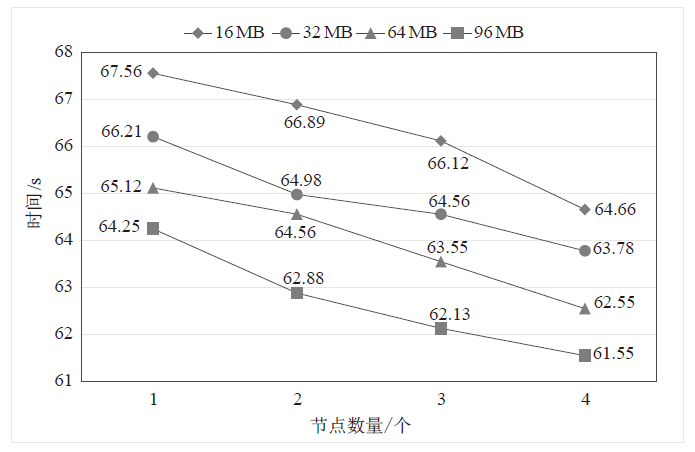
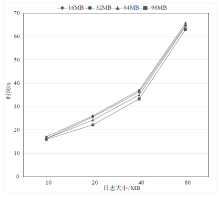
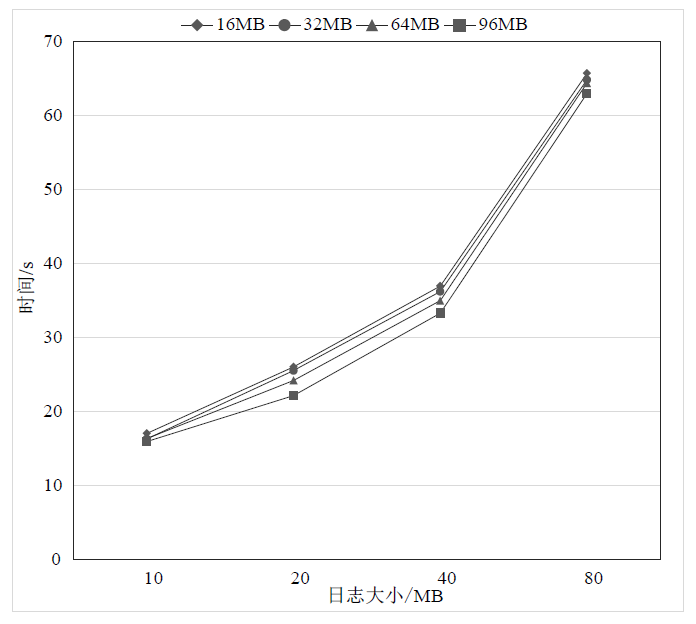
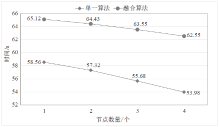
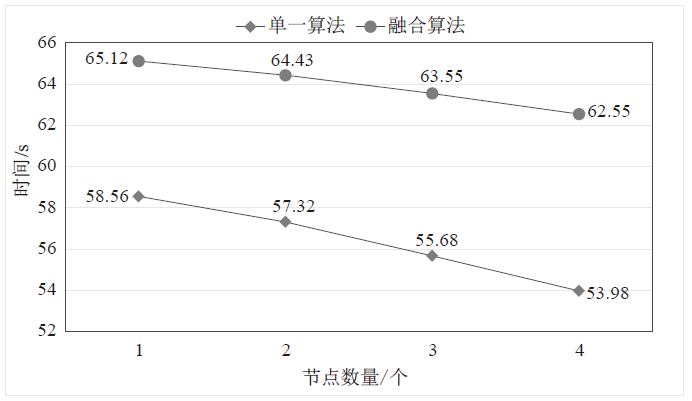
| [1] |
LIU Jiwei, LI Ruinan, ZHANG Yu, et al. Application of Incremental GHSOM Algorithm in DDoS Attack Detection[J]. Journal of Nanjing University of Posts and Telecommunications(Natural Science Edition), 2020,40(3): 82-88.
|
|
刘纪伟, 李睿楠, 张玉, 等. 一种增量式GHSOM算法在DDoS攻击检测中的应用[J]. 南京邮电大学学报(自然科学版), 2020,40(3): 82-88.
|
| [2] |
LUO Wenhua, XU Caidian. Using Improved DBSCAN Clustering to Implement Multi-step Network Intrusion Detection[J]. Mini-micro Systems, 2020,41(8): 1725-1731.
|
|
罗文华, 许彩滇. 利用改进DBSCAN聚类实现多步式网络入侵类别检测[J]. 小型微型计算机系统, 2020,41(8): 1725-1731.
|
| [3] |
LEE Y, LEE Y. Detecting DDoS Attacks with Hadoop[C]//ACM. Co-NEXT’11: Conference on Emerging Networking Experiments and Technologies, December 6-9, 2011, Tokyo, Japan. New York: ACM, 2011: 51-63.
|
| [4] |
WU Xiaoqin, HUANG Wenpei. Hadoop Security and Attack Detection Methods[J]. Journal of Computer Applications, 2020,40(S1): 118-123.
|
|
吴晓琴, 黄文培. Hadoop安全及攻击检测方法[J]. 计算机应用, 2020,40(S1): 118-123.
|
| [5] |
LI Zhongwen, WU Chengbin, XU Xiaochen. Research on DDoS Intrusion Detection System Based on Linux High Speed Packet Capturing Platform[J]. Computer Science, 2014,41(4): 159-162.
|
|
黎忠文, 吴成宾, 许晓晨. 基于Linux高速报文捕获平台的DDoS入侵检测系统的研究[J]. 计算机科学, 2014,41(4): 159-162.
|
| [6] |
WANG Wentao, LI Shumei, TANG Jie, et al. DDoS Attack Detection Method Based on Probability Graph Model and DNN[EB/OL]. https://kns.cnki.net/kcms/detail/11.2127.TP.20200702.1553.014.html, 2020-08-11.
|
|
王文涛, 李树梅, 汤婕, 等. 结合概率图模型与DNN的DDoS攻击检测方法[EB/OL]. https://kns.cnki.net/kcms/detail/11.2127.TP.20200702.1553.014.html, 2020-08-11.
|
| [7] |
PI Jianyong, GONG Mingshu, LIU Xinsong, et al. Host Anomaly Intrusion Detection Model Based on Access Control[J]. Application Research of Computers, 2009,26(2): 726-729, 732.
|
|
皮建勇, 巩明树, 刘心松, 等. 基于访问控制的主机异常入侵检测模型[J]. 计算机应用研究, 2009,26(2): 726-729, 732.
|
| [8] |
DONG Ruihong, YAN Houhua, ZHANG Qiuyu, et al. Distributed WSN Intrusion Detection Model Based on Deep Forest Algorithm[J]. Journal of Lanzhou University of Technology, 2020,46(4): 103-109.
|
|
董瑞洪, 闫厚华, 张秋余, 等. 基于深度森林算法的分布式WSN入侵检测模型[J]. 兰州理工大学学报, 2020,46(4): 103-109.
|
| [9] |
JIN Guodong, BIAN Haoqi, CHEN Yueguo, et al. Survey on Storage and Optimization Techniques of HDFS[J]. Journal of software, 2020,31(1): 137-161.
|
|
金国栋, 卞昊穹, 陈跃国, 等. HDFS存储和优化技术研究综述[J]. 软件学报, 2020,31(1): 137-161.
|
| [10] |
WEI Qi, WU Yong, JIANG Yiwei, et al. Algorithm for Two-stage Hybrid Flow Shop in MapReduce Systems[J]. Systems Engineering-theory & Practice, 2020,40(5): 1255-1265.
|
|
魏麒, 吴用, 蒋义伟, 等. MapReduce系统中的两阶段混合流水作业调度算法[J]. 系统工程理论与实践, 2020,40(5): 1255-1265.
|
| [11] |
DEAN J, GHEMAWAT S. MapReduce: Simplified Data Processing on Large Clusters[J]. Operatin Systems Design and Implementation(OSDI), 2004,51(1): 107-113.
|
| [12] |
KAVULYA S, TAN J, GANDHI R, et al. An Analysis of Traces From a Production MapReduce Cluster[C]// IEEE. 10th IEEE/ACM International Conference on Cluster, Cloud and Grid Computing, June 24, 2010, Melbourne, VIC, Australia. New Jersey: IEEE, 2010: 94-103.
|
| [13] |
HAMEED S, ALI U. HADEC: Hadoop-based live DDoS detection framework[J]. Information Security, 2018,18(1): 1-19.
|
| [14] |
LUO Wenhua, ZHANG Yan. Using the Improved Major Clust Algorithm to Realize Unusual User Behavior Orientation[J]. Mini-micro Systems, 2019,40(11): 2374-2379.
|
|
罗文华, 张艳. 利用改进的MajorClust算法实现异常用户行为定位[J]. 小型微型计算机系统, 2019,40(11): 2374-2379.
|
| [15] |
LIU Jia, XIAO Pengbin, YUAN Youhong. Distributed Multi-strategy CFAR Detection Algorithm Based on Adaptive Threshold Selection[J]. Electronics Optics & Control, 2020,27(9): 60-65.
|
|
刘佳, 肖鹏斌, 袁有宏. 基于自适应阈值选择的分布式多策略CFAR检测算法[J]. 电光与控制, 2020,27(9): 60-65.
|