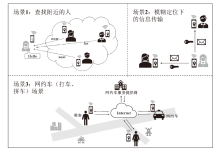
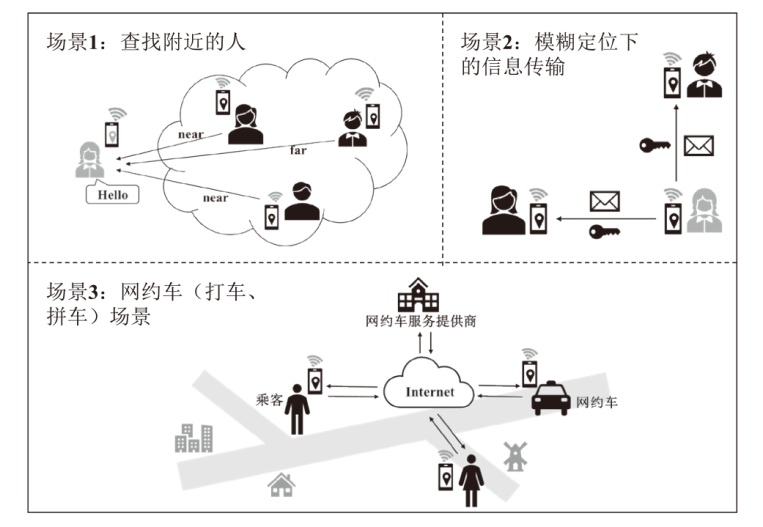
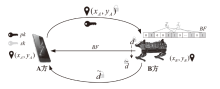
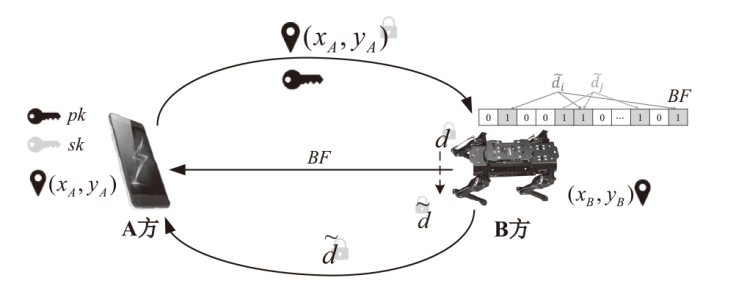
| [1] |
WHITTAKER Z. A Leaky Database Spilled 2FA Codes for the World’s Tech Giants | TechCrunch[EB/OL]. (2024-02-29)[2024-04-15]. https://techcrunch.com/2024/02/29/leaky-database-two-factor-codes/.
|
| [2] |
CHENG R, ZHANG Yu, BERTINO E, et al. Preserving User Location Privacy in Mobile Data Management Infrastructures[C]// Springer. International Workshop on Privacy Enhancing Technologies. Heidelberg: Springer, 2006: 393-412.
|
| [3] |
SIKSNYS L, THOMSEN J R, SALTENIS S, et al. A Location Privacy Aware Friend Locator[C]// Springer. International Symposium on Advances in Spatial & Temporal Databases. Heidelberg: Springer, 2009: 405-410.
|
| [4] |
ZHENG Yao, LI Ming, LOU Wenjing, et al. Location Based Handshake and Private Proximity Test with Location Tags[J]. IEEE Transactions on Dependable & Secure Computing, 2017, 14(4): 406-419.
|
| [5] |
PAILLIER P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[J]. Advances in Cryptology Leurocrypt, 1999, 1592: 223-238.
|
| [6] |
DAMGAARD I, GEISLER M, KROIGAARD M. A Correction to 'Efficient and Secure Comparison for on-Line Auctions'[J]. International Journal of Applied Cryptography, 2009, 1(4): 323-324.
|
| [7] |
ELGAMAL T. A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms[J]. lEEE Transactions on Information Theory, 1985, 31(4): 469-472.
|
| [8] |
NARAYANAN A, THIAGARAJAN N, LAKHANI M, et al. Location Privacy via Private Proximity Testing[C]// The Internet Society. Network and Distributed System Security Symposium. San Diego: The Internet Society, 2011: 381-386.
|
| [9] |
ZHONG Ge, GOLDBERG I, HENGARTNER U. Louis, Lester and Pierre: Three Protocols for Location Privacy[C]// Springer. International Conference on Privacy Enhancing Technologies. Heidelberg: Springer, 2007: 62-76.
|
| [10] |
SEDENKA J, GASTI P. Privacy-Preserving Distance Computation and Proximity Testingon Earth, Done Right[C]// ACM. ACM Asia Conference on Computer and Communications Security. New York: ACM, 2014: 99-110.
|
| [11] |
ERKIN Z, FRANZ M, GUAJARDO J, et al. Privacy-Preserving Face Recognition[C]// Springer. Privacy Enhancing Technologies. Heidelberg: Springer, 2009: 235-253.
|
| [12] |
KOLESNIKOV V, SADEGHI A, SCHNEIDER T. Improved Garbled Circuit Building Blocks and Applications to Auctions and Computing Minima[C]// Springer. International Conference on Cryptology and Network Security. Heidelberg: Springer, 2009: 1-20.
|
| [13] |
HALLGREN P, OCHOA M, SABELFELD A. A Parallelizable Decentralized Privacy-Preserving Location Proximity Protocol[C]// IEEE. Privacy, Security & Trust. New York: IEEE, 2015: 1-6.
|
| [14] |
ZHU Hui, WANG Fengwei, LU Rongxing, et al. Efficient and Privacy-Preserving Proximity Detection Schemes for Social Applications[J]. IEEE Internet of Things Journal, 2018, 5(4): 2947-2957.
|
| [15] |
JARVINEN K, KISS A, SCHNEIDER T, et al. Faster Privacy-Preserving Location Proximity Schemes[C]// Springer. Cryptology and Network Security. Heidelberg: Springer, 2018: 3-22.
|
| [16] |
DEMMLER D, SCHNEIDER T, ZOHNER M. ABY-A Framework for Efficient Mixed-Protocol Secure Two-Party Computation[EB/OL]. (2015-02-01)[2024-04-15]. https://api.semanticscholar.org/CorpusID:14639818.
|
| [17] |
JARVINEN K, KISS A, SCHNEIDER T, et al. Faster Privacy-Preserving Location Proximity Schemes for Circles and Polygons[J]. IET Information Security, 2020, 14(3): 254-265.
|
| [18] |
ALOUFI A, HU Peizhao, LIU Hang, et al. Universal Location Referencing and Homomorphic Evaluation of Geospatial Query[EB/OL]. (2021-03-01)[2024-04-15]. https://doi.org/10.1016/j.cose.2020.102137.
|
| [19] |
BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V. (Leveled) Fully Homomorphic Encryption without Bootstrapping[J]. ACM Transactions on Computation Theory, 2014, 6(3): 1-36.
|
| [20] |
MASCETTI S, FRENI D, BETTINI C, et al. Privacy in Geo-Social Networks: Proximity Notification with Untrusted Service Providers and Curious Buddies[J]. VLDB Journal, 2011, 20(4): 541-566.
|
| [21] |
FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[EB/OL]. (2012-03-22)[2024-04-15]. https://eprint.iacr.org/2012/144.
|
| [22] |
BLOOM B H. Space/Time Trade-Offs in Hash Coding with Allowable Errors[J]. Communications of ACM, 1970, 13(7): 422-426.
|
| [23] |
PAGH A, PAGH R, RAO S S. An Optimal Bloom Filter Replacement[C]// SIAM. Proceedings of the Sixteenth Annual ACM SIAM Symposium on Discrete Algorithms. Vancouver: SIAM, 2005: 823-829.
|
 )
)