Netinfo Security ›› 2024, Vol. 24 ›› Issue (7): 983-992.doi: 10.3969/j.issn.1671-1122.2024.07.001
Previous Articles Next Articles
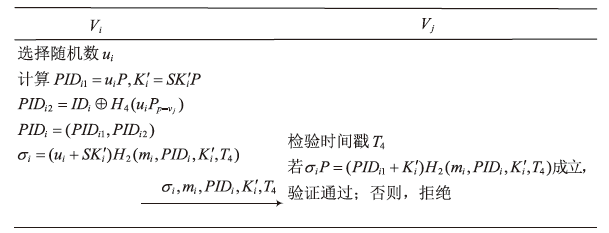
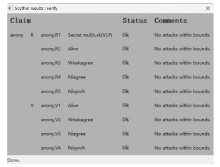
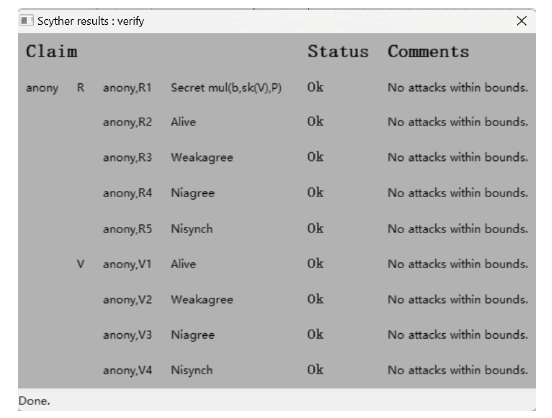
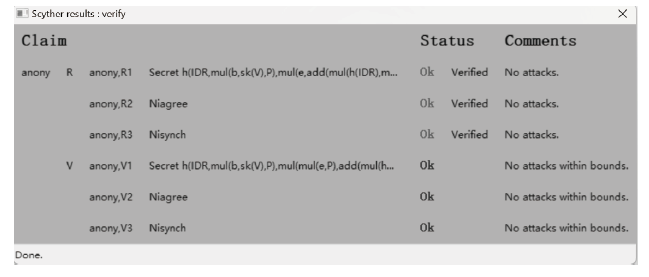
A Certificateless Anonymous Authentication Key Agreement Protocol for VANET
LIU Yidan, MA Yongliu( ), DU Yibin, CHENG Qingfeng
), DU Yibin, CHENG Qingfeng
- Institute of Cyberspace Security, Information Engineering University, Zhengzhou 450001, China
-
Received:2024-03-27Online:2024-07-10Published:2024-08-02
CLC Number:
Cite this article
LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET[J]. Netinfo Security, 2024, 24(7): 983-992.
share this article
| [1] | TAN Fuyuan. Research on Efficient and Secure Authentication Scheme in Vehicular Ad-Hoc Network[D]. Chongqing: Chongqing University of Posts and Telecommunications, 2018. |
| 谭富元. 车联网环境下高效安全认证方案的研究[D]. 重庆: 重庆邮电大学, 2018. | |
| [2] | RAYA M, HUBAUX J P. The Security of Vehicular Ad Hoc Networks[C]// ACM. The 3rd ACM Workshop on Security of Ad Hoc and Sensor Networks. New York: ACM, 2005: 11-21. |
| [3] | CALANDRIELLO G, PAPADIMITRATOS P, HUBAUX J P, et al. Efficient and Robust Pseudonymous Authentication in VANET[C]// ACM. The 4th ACM International Workshop on Vehicular Ad Hoc Networks. New York: ACM, 2007: 19-28. |
| [4] | ZHANG Chenxi, LU Rongxing, LIN Xiaodong, et al. An Efficient Identity-Based Batch Verification Scheme for Vehicular Sensor Networks[C]// IEEE. IEEE INFOCOM 2008-The 27th Conference on Computer Communications. New York: IEEE, 2008: 246-250. |
| [5] | LEE C C, LAI Yanming. Toward a Secure Batch Verification with Group Testing for VANET[J]. Wireless Networks, 2013, 19(6): 1441-1449. |
| [6] | BAYAT M, BARMSHOORY M, RAHIMI M, et al. A Secure Authentication Scheme for VANETs with Batch Verification[J]. Wireless Networks, 2015, 21(5): 1733-1743. |
| [7] | AL-RIYAMI S S, PATERSON K G. Certificateless Public Key Cryptography[C]// Springer. Advances in Cryptology-ASIACRYPT 2003. Heidelberg: Springer, 2003: 452-473. |
| [8] | HORNG S J, TZENG S F, HUANG P H, et al. An Efficient Certificateless Aggregate Signature with Conditional Privacy-Preserving for Vehicular Sensor Networks[J]. Information Sciences, 2015, 317: 48-66. |
| [9] | LI Jiguo, YUAN Hong, ZHANG Yichen. Cryptanalysis and Improvement of Certificateless Aggregate Signature with Conditional Privacy-Preserving for Vehicular Sensor Networks[J]. Networks, 2015, 317: 48-66. |
| [10] | YAO Yingying, CHANG Xiaolin, LI Lin. CLAM: A Lightweight Certificateless Anonymous Authentication Mechanism for Vehicular Cloud Services[J]. Cyber-Physical Systems, 2018, 4(1): 17-38. |
| [11] | WANG Daxing, TENG Jikai. Probably Secure Cetificateless Aggregate Signature Algorithm for Vehicular Ad Hoc Network[J]. Journal of Electronics & Information Technology, 2018, 40(1): 11-17. |
| 王大星, 滕济凯. 车载网中可证安全的无证书聚合签名算法[J]. 电子与信息学报, 2018, 40(1): 11-17. | |
| [12] | YANG Xiaodong, MA Tingchun, CHEN Chunlin, et al. Security Analysis and Improvement of Certificateless Aggregate Signature Scheme for Vehicular Ad Hoc Networks[J]. Journal of Electronics & Information Technology, 2019, 41(5): 1265-1270. |
| 杨小东, 麻婷春, 陈春霖, 等. 面向车载自组网的无证书聚合签名方案的安全性分析与改进[J]. 电子与信息学报, 2019, 41(5): 1265-1270. | |
| [13] | ALI I, GERVAIS M, AHENE E, et al. A Blockchain-Based Certificateless Public Key Signature Scheme for Vehicle-to-Infrastructure Communication in VANETs[EB/OL]. (2019-08-21)[2024-03-15]. https://www.sciencedirect.com/science/article/abs/pii/S1383762119302103. |
| [14] |
ZHONG Hong, HAN Shunshun, CUI Jie, et al. Privacy-Preserving Authentication Scheme with Full Aggregation in VANET[J]. Information Sciences, 2019, 476: 211-221.
doi: 10.1016/j.ins.2018.10.021 |
| [15] | KAMIL I A, OGUNDOYIN S O. On the Security of Privacy-Preserving Authentication Scheme with Full Aggregation in Vehicular Ad Hoc Network[J]. Security and Privacy, 2020, 3(3): 1-20. |
| [16] | CHEN Yulei, CHEN Jianhua. CPP-CLAS: Efficient and Conditional Privacy-Preserving Certificateless Aggregate Signature Scheme for VANETs[J]. IEEE Internet of Things Journal, 2022, 9(12): 10354-10365. |
| [17] | ZHOU Yanwei, XU Ran, QIAO Zirui, et al. An Anonymous and Efficient Multimessage and Multireceiver Certificateless Signcryption Scheme for VANET[J]. IEEE Internet of Things Journal, 2023, 10(24): 22823-22835. |
| [18] | WANG Zhaolong, ZHOU Yanwei, QIAO Zirui, et al. An Anonymous and Revocable Authentication Protocol for Vehicle-to-Vehicle Communications[J]. IEEE Internet of Things Journal, 2023, 10(6): 5114-5127. |
| [19] | LI Jiliang, CHOO K K R, ZHANG Weiguo, et al. EPA-CPPA: An Efficient, Provably-Secure and Anonymous Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks[J]. Vehicular Communications, 2018, 13: 104-113. |
| [20] | CSEH C. Architecture of the Dedicated Short-Range Communications (DSRC) Protocol[C]// IEEE. The 48th IEEE Vehicular Technology Conference. New York: IEEE, 2002: 2095-2099. |
| [21] | HUANG Xinyi, MU Yi, SUSILO W, et al. Certificateless Signature Revisited[C]// Springer. Proceedings of Australasian Conference on Information Security and Privacy. Heidelberg: Springer, 2007: 308-322. |
| [22] | POINTCHEVAL D, STERN J. Security Arguments for Digital Signatures and Blind Signatures[J]. Journal of Cryptology, 2000, 13(3): 361-396. |
| [23] | HE Debiao, ZEADALLY S, XU Baowen, et al. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(12): 2681-2691. |
| [24] | JIANG Shuo, CHEN Xue, CAO Yibo, et al. APKI: An Anonymous Authentication Scheme Based on PKI for VANET[C]// IEEE. 2022 7th International Conference on Computer and Communication Systems (ICCCS). New York: IEEE, 2022: 530-536. |
| [25] | MEI Qian, XIONG Hu, CHEN Jinhao, et al. Efficient Certificateless Aggregate Signature with Conditional Privacy Preservation in IoV[J]. IEEE Systems Journal, 2021, 15(1): 245-256. |
| [26] | WANG Shibin, YAO Nianmin. LIAP: A Local Identity-Based Anonymous Message Authentication Protocol in VANETs[J]. Computer Communications, 2017, 112: 154-164. |
| [1] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [2] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [3] | SHEN Yan, YAO Mengmeng. Research on Formal Analysis Based on Event of Group Key Agreement Protocol [J]. Netinfo Security, 2022, 22(5): 30-36. |
| [4] | WANG Yong, CHEN Lijie, ZHONG Meiling. Progress in Blockchain Solutions Based on Zero-Knowledge Proof [J]. Netinfo Security, 2022, 22(12): 47-56. |
| [5] | GU Haiyan, JIANG Tong, MA Zhuo, ZHU Jipeng. Research of Improved k-Anonymity Algorithm and Its Application in Privacy Protection [J]. Netinfo Security, 2022, 22(10): 52-58. |
| [6] | HE Jingsha, DU Jinhui, ZHU Nafei. Research on k-anonymity Algorithm for Personalized Quasi-identifier Attributes [J]. Netinfo Security, 2020, 20(10): 19-26. |
| [7] | Yilin LI, Zheng YAN, Haomeng XIE. Survey of Privacy Preservation in VANET [J]. Netinfo Security, 2019, 19(4): 63-72. |
| [8] | Yanan CHEN, Qian MEI, Hu XIONG, Weixiang XU. Certificateless Parallel Key-insulated Signature for Industrial Internet of Things [J]. Netinfo Security, 2018, 18(10): 1-9. |
| [9] | Juan QU, Yanping LI, Li LI. Cryptanalysis and Security Enhancement of an Efficient Secure Authentication Scheme with User Anonymity for Roaming User in Ubiquitous Networks [J]. Netinfo Security, 2018, 18(1): 73-79. |
| [10] | Hao WANG, Xiangfu SONG, Junming KE, Qiuliang XU. Blockchain and Privacy Preserving Mechanisms in Cryptocurrency [J]. Netinfo Security, 2017, 17(7): 32-39. |
| [11] | Yameng CHEN, Xiangguo CHENG, Shuo WANG, Ming GAO. Research on Certificateless Group Signature Scheme Based on Bilinear Pairings [J]. Netinfo Security, 2017, 17(3): 53-58. |
| [12] | Yuejian FANG, Jinzhong ZHU, Wen ZHOU, Tongliang LI. A Survey on Data Mining Privacy Protection Algorithms [J]. Netinfo Security, 2017, 17(2): 6-11. |
| [13] | Chunming TANG, Long GAO. Multi-parties Key Agreement Protocol in Block Chain [J]. Netinfo Security, 2017, 17(12): 17-21. |
| [14] | Shasha WU, Jinbo XIONG, Guohua YE, Zhiqiang YAO. Research on Location Privacy Protection Based on Dummy Locations in Mobile Internet Environment [J]. Netinfo Security, 2016, 16(10): 54-59. |
| [15] | Jian-hong ZHANG, Qiao-cui DONG. Research and Implementation on Anonymous Broadcast Encryption Scheme under the Mixing Mechanism [J]. Netinfo Security, 2015, 15(8): 8-13. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||