| [1] |
CHAUM D, HEYST E V.Group Signatures[C]//ACM. EUROCRYPT ’91 Proceedings of the 10th Annual International Conference on Theory and Application of Cryptographic Techniques, April 8-11, 1991. Brighton, UK. Heidelberg :Springer Berlin Heidelberg, 1991:257-265.
|
| [2] |
CHEN L,PEDERSEN T P.New Group Signature Schemes[M]// Advances in Cryptology -EUROCRYPT'94.Heidelberg :Springer Berlin Heidelberg,1995:171-181.
|
| [3] |
CAMENISCH J.Efficient and Generalized Group Signatures[M]//Advances in Cryptology - EUROCRYPT ’97. Heidelberg :Springer Berlin Heidelberg,1997:465-479.
|
| [4] |
CAMENISCH J, STADLER M.Efficient Group Signature Schemes for Large Groups[M]// Advances in Cryptology - CRYPTO '97. Heidelberg :Springer Berlin Heidelberg, 1997:410-424.
|
| [5] |
ATENIESE G, CAMENISCH J, JOYE M, et al.A Practical and Provably Secure Coalition-Resistant Group Signature Scheme[M]// Advances in Cryptology - CRYPTO 2000.Heidelberg :Springer Berlin Heidelberg,2000:255-270.
|
| [6] |
SHAMIR A.Identity-Based Cryptosystems and Signature Schemes[M]//Advances in Cryptology. Heidelberg :Springer Berlin Heidelberg,1985:47-53.
|
| [7] |
PARK S,KIM S,WON D.ID-based Group Signature[J].Electronics Letters,1997,33(19):1616-1617.
|
| [8] |
矢敏,叶伟伟,欧庆于. 不需双线性对的基于身份的认证密钥协商协议[J]. 信息网络安全,2016(10):21-27.
|
| [9] |
AL-RIYAMI S S,PATERSON K G.Certificateless Public Key Cryptography[M]//Advances in Cryptology - ASIACRYPT 2003. Heidelberg :Springer Berlin Heidelberg,2003:452-473.
|
| [10] |
ZHANG Lei,ZHANG Futai,WU Wei.A Provably Secure Ring Signature Scheme in Certificateless Cryptography[C]//ACM. ProvSec'07 Proceedings of the 1st International Conference on Provable Security, November 1 - 2, 2007. Wollongong, Australia. Heidelberg: Springer Berlin Heidelberg, 2007:103-121.
|
| [11] |
GONG Zheng,LONG Yu,HONG Xuan,et al.Two Certificateless Aggregate Signatures from Bilinear Maps[C]//IEEE. SNPD '07 Proceedings of the Eighth ACIS International Conference on Software Engineering, Artificial Intelligence, Networking, and Parallel/Distributed Computing, July 30 - August 1, 2007. Washington, DC, USA.NJ:IEEE,2007:188-193.
|
| [12] |
YUAN Hong, ZHANG Futai, HUANG Xinyi, et al.Certificateless Threshold Signature Scheme from Bilinear Maps[J]. Information Sciences, 2010, 180(23):4714-4728.
|
| [13] |
张言胜,汪学明,仇各各. 一种新的动态门限数字签名方案研究[J]. 信息网络安全,2016(6):62-67.
|
| [14] |
梁红梅, 黄慧, 吴晨煌,等. 无证书多重签名[J]. 集美大学学报:自然科学版, 2008, 13(2):127-131.
|
| [15] |
ZHANG Guoyan, WANG Shaohui.A Certificateless Signature and Group Signature Schemes against Malicious PKG[C]//IEEE.International Conference on Advanced Information NETWORKING and Applications. March 25 - 28, 2008 . Washington, DC, USA.NJ: IEEE, 2008:334-341.
|
| [16] |
赵洋,岳峰,熊虎,等. 一种强指定验证者环签名和签密体制[J]. 信息网络安全,2015(10):8-13.
|
| [17] |
CHENG Xiangguo, ZHOU Shaojie, YU Jia, et al.A Practical ID-based Group Signature Scheme[J]. Journal of Computers, 2012, 7(11):842-849.
|
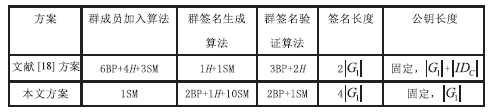
| [18] |
CHEN Hu,SONG Rushun,SHI Feng.Provably Security Certificateless Group Signature Scheme[J].Computer Engineering and Applications,2009,45(19):87-91.
|
 ), Shuo WANG2, Ming GAO2
), Shuo WANG2, Ming GAO2