Netinfo Security ›› 2024, Vol. 24 ›› Issue (2): 229-238.doi: 10.3969/j.issn.1671-1122.2024.02.006
Previous Articles Next Articles
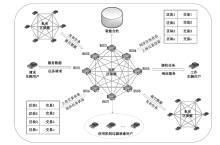
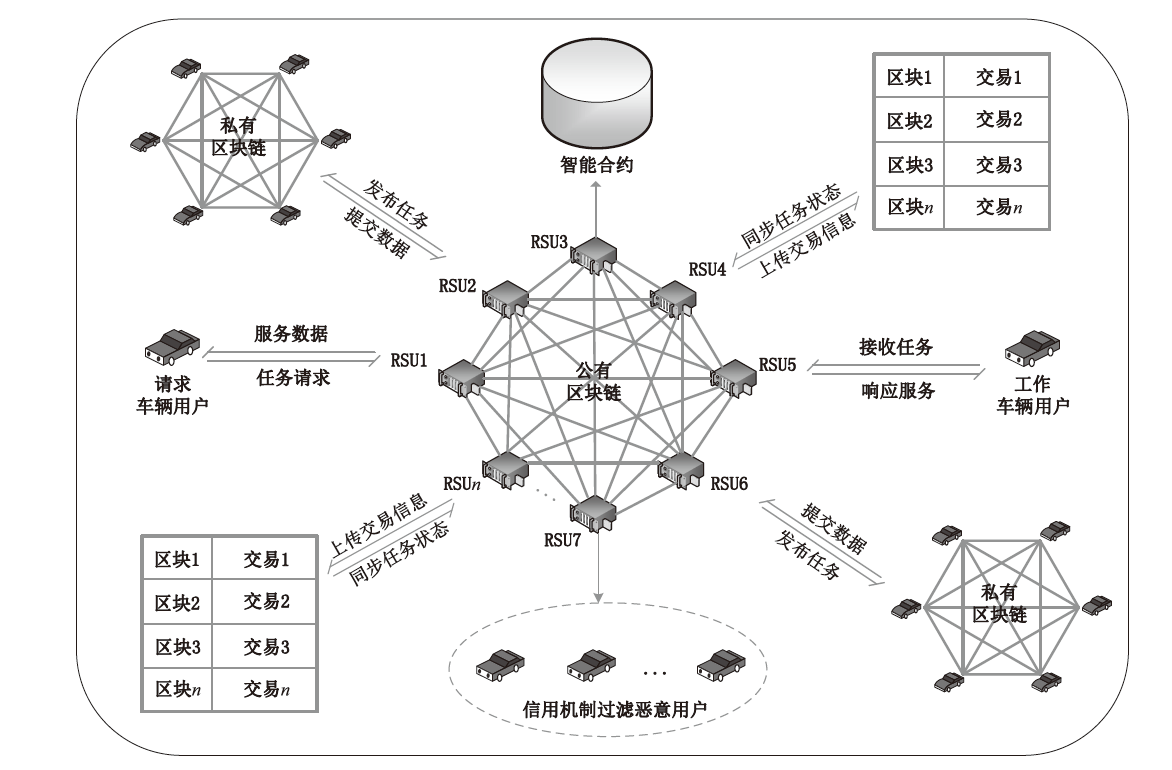
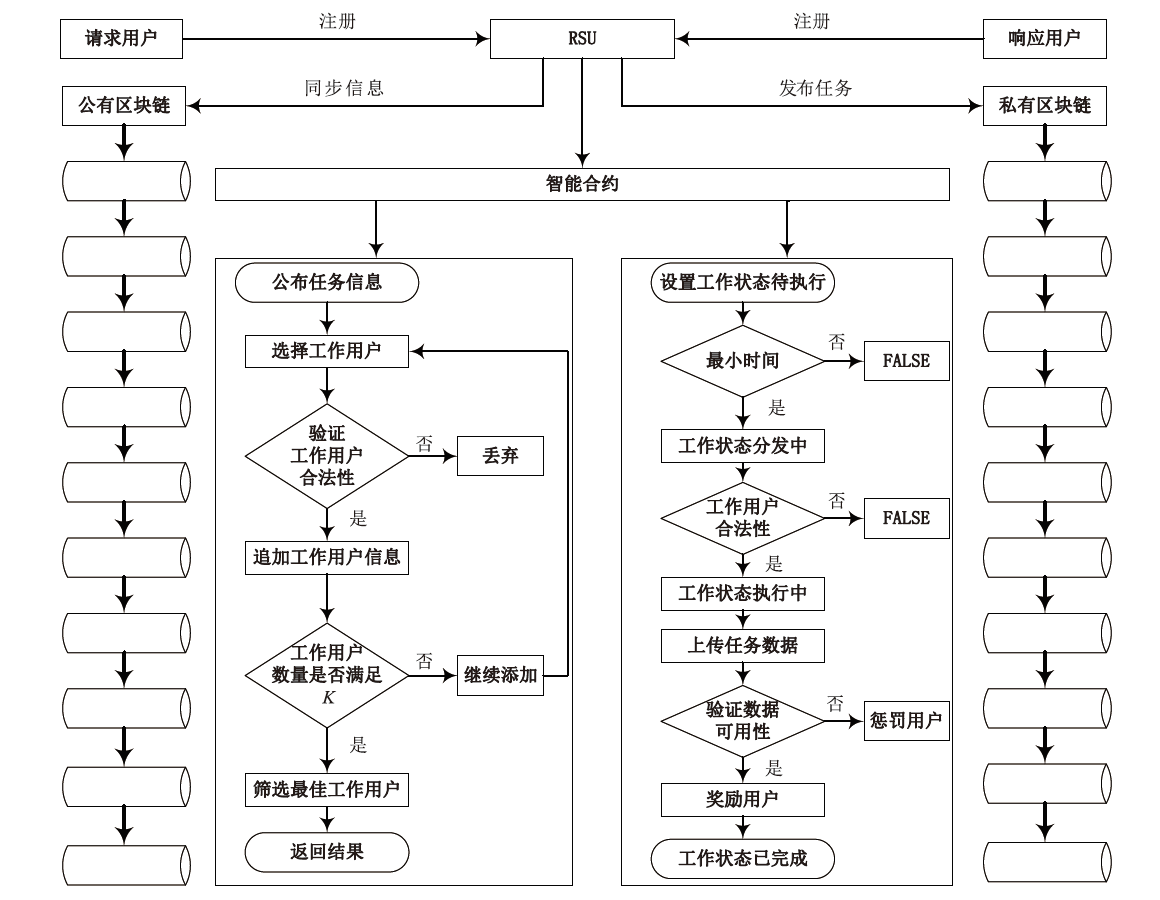
A Location Privacy Protection Scheme Based on Hybrid Blockchain
HE Yefeng, QUAN Jiahui( ), LIU Yan
), LIU Yan
- School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2023-06-12Online:2024-02-10Published:2024-03-06 -
Contact:QUAN Jiahui E-mail:yubeilengzhi@163.com
CLC Number:
Cite this article
HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain[J]. Netinfo Security, 2024, 24(2): 229-238.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.02.006
| [1] | WU W, YANG Z, LI K. Internet of Vehicles and Applications[EB/OL]. (2016-06-17)[2023-06-10]. https://doi.org/10.1016/B978-0-12-805395-9.00016-2. |
| [2] |
ZHOU Haibo, XU Wenchao, CHEN Jiacheng, et al. Evolutionary V2X Technologies Toward the Internet of Vehicles: Challenges and Opportunities[J]. Proceedings of the IEEE, 2020, 108(2): 308-323.
doi: 10.1109/PROC.5 URL |
| [3] |
SUN Yunchuan, WU Lei, WU Shizhong, et al. Attacks and Countermeasures in the Internet of Vehicles[J]. Annals of Telecommunications, 2017, 72: 283-295.
doi: 10.1007/s12243-016-0551-6 URL |
| [4] | OTHMANE L B, WEFFERS H, MOHAMAD M M, et al. A Survey of Security and Privacy in Connected Vehicles[EB/OL]. (2015-03-18)[2023-06-10]. https://doi.org/10.1007/978-1-4939-2468-4_10. |
| [5] |
QIU Ying, LIU Yi, LI Xuan, et al. A Novel Location Privacy-Preserving Approach Based on Blockchain[J]. Sensors, 2020, 20(12): 3519.
doi: 10.3390/s20123519 URL |
| [6] |
KHAN S, SHARMA I, ASLAM M, et al. Security Challenges of Location Privacy in VANETs and State-of-the-Art Solutions: A Survey[J]. Future Internet, 2021, 13(4): 96.
doi: 10.3390/fi13040096 URL |
| [7] | SAGIRLAR G, CARMINATI B, FERRARI E, et al. Hybrid-Iot: Hybrid Blockchain Architecture for Internet of Things-Pow Sub-Blockchains[C]// IEEE. 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData). New York:IEEE, 2018: 1007-1016. |
| [8] | WANG Shuai, YUAN Yong, WANG Xiao, et al. An Overview of Smart Contract: Architecture, Applications, and Future Trends[C]// IEEE. 2018 IEEE Intelligent Vehicles Symposium (IV). New York: IEEE, 2018: 108-113. |
| [9] |
ZHENG Zibin, XIE Shaoan, DAI Hong-Ning, et al. An Overview on Smart Contracts: Challenges, Advances and Platforms[J]. Future Generation Computer Systems, 2020, 105: 475-491.
doi: 10.1016/j.future.2019.12.019 URL |
| [10] |
ZHANG Junwei, YANG Fan, MA Zhuo, et al. A Decentralized Location Privacy-Preserving Spatial Crowdsourcing for Internet of Vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2020, 22(4): 2299-2313.
doi: 10.1109/TITS.2020.3010288 URL |
| [11] | KANG Jiawen, YU Rong, HUANG Xumin, et al. Location Privacy Attacks and Defenses in Cloud-Enabled Internet of Vehicles[J]. IEEE Wireless Communications, 2016, 23(5): 52-59. |
| [12] | WANG Fei, DU Yifan, XU Yongjun, et al. EPAF: An Efficient Pseudonymous-Based Inter-Vehicle Authentication Framework for VANET[C]// Springer. Mobile Ad-Hoc and Sensor Networks:13th International Conference. Heidelberg: Springer, 2018: 252-270. |
| [13] |
FENG Jingyu, WANG Yin, WANG Jialin, et al. Blockchain-Based Data Management and Edge-Assisted Trusted Cloaking Area Construction for Location Privacy Protection in Vehicular Networks[J]. IEEE Internet of Things Journal, 2020, 8(4): 2087-2101.
doi: 10.1109/JIoT.6488907 URL |
| [14] |
CHULERTTIYAWONG D, JAMALIPOUR A. A Blockchain Assisted Vehicular Pseudonym Issuance and Management System for Conditional Privacy Enhancement[J]. IEEE Access, 2021, 9: 127305-127319.
doi: 10.1109/ACCESS.2021.3112013 URL |
| [15] |
CHEN Yanru, LI Jingpeng, WANG Fan, et al. DS2PM: A Data Sharing Privacy Protection Model Based on Blockchain and Federated Learning[J]. IEEE Internet of Things Journal, 2021, 10(14): 12112-12125.
doi: 10.1109/JIOT.2021.3134755 URL |
| [16] |
ZOU Shihong, XI Jinwen, XU Guoai, et al. Crowdhb: A Decentralized Location Privacy-Preserving Crowdsensing System Based on a Hybrid Blockchain Network[J]. IEEE Internet of Things Journal, 2021, 9(16): 14803-14817.
doi: 10.1109/JIOT.2021.3084937 URL |
| [17] |
CASADO-VARA R, CHAMOSO P, DE LA PRIETA F, et al. Non-Linear Adaptive Closed-Loop Control System for Improved Efficiency in IoT-Blockchain Management[J]. Information Fusion, 2019, 49: 227-239.
doi: 10.1016/j.inffus.2018.12.007 URL |
| [18] |
MOHANTA B K, JENA D, RAMASUBBAREDDY S, et al. Addressing Security and Privacy Issues of IoT Using Blockchain Technology[J]. IEEE Internet of Things Journal, 2020, 8(2): 881-888.
doi: 10.1109/JIoT.6488907 URL |
| [19] |
CABALLERO-GIL C, MOLINA-GIL J, HERNÁNDEZ-SERRANO J, et al. Providing K-Anonymity and Revocation in Ubiquitous VANETs[J]. Ad Hoc Networks, 2016, 36: 482-494.
doi: 10.1016/j.adhoc.2015.05.016 URL |
| [20] | LÈBRE M A, LE MOUËL F, MÉNARD E. Microscopic Vehicular Mobility Trace of Europarc Roundabout, Creteil, France[EB/OL]. (2015-04-15)[2023-06-10]. https://zenodo.org/records/16870. |
| [21] |
SWEENEY L. K-Anonymity: A Model for Protecting Privacy[J]. International Journal of Uncertainty, Fuzziness and Knowledge-Based Systems, 2002, 10(5): 557-570.
doi: 10.1142/S0218488502001648 URL |
| [22] |
CHAUDHARY B, SINGH K. A Blockchain Enabled Location-Privacy Preserving Scheme for Vehicular Ad-Hoc Networks[J]. Peer-to-Peer Networking and Applications, 2021, 14: 3198-3212.
doi: 10.1007/s12083-021-01079-5 |
| [23] |
XING Ling, JIA Xiaofan, GAO Jianping, et al. A Location Privacy Protection Algorithm Based on Double K-Anonymity in the Social Internet of Vehicles[J]. IEEE Communications Letters, 2021, 25(10): 3199-3203.
doi: 10.1109/LCOMM.2021.3072671 URL |
| [1] | ZHOU Quan, ZENG Zhikang, WANG Kemeng, CHEN Menglong. Location Privacy Protection Scheme for Group Signature with Backward Unlinkability [J]. Netinfo Security, 2023, 23(3): 62-72. |
| [2] | GU Haiyan, JIANG Tong, MA Zhuo, ZHU Jipeng. Research of Improved k-Anonymity Algorithm and Its Application in Privacy Protection [J]. Netinfo Security, 2022, 22(10): 52-58. |
| [3] | HE Jingsha, DU Jinhui, ZHU Nafei. Research on k-anonymity Algorithm for Personalized Quasi-identifier Attributes [J]. Netinfo Security, 2020, 20(10): 19-26. |
| [4] | Li XU, Rui ZHU, Yali ZENG. Location Privacy-preserving Scheme Based on SpaceTwist in Cognitive Radio Network [J]. Netinfo Security, 2019, 19(2): 18-27. |
| [5] | Yuejian FANG, Jinzhong ZHU, Wen ZHOU, Tongliang LI. A Survey on Data Mining Privacy Protection Algorithms [J]. Netinfo Security, 2017, 17(2): 6-11. |
| [6] | Qing LI, A-yong YE, Li XU. Research on Security Issues of Wireless Access in Public Environment [J]. Netinfo Security, 2016, 16(4): 69-75. |
| [7] | Yijie ZHU, Changgen PENG, Jiashuai LI, Haifeng MA. A Framework of Privacy Metric in LBS Combining Query Privacy with Location Privacy [J]. Netinfo Security, 2016, 16(2): 47-53. |
| [8] | Shasha WU, Jinbo XIONG, Guohua YE, Zhiqiang YAO. Research on Location Privacy Protection Based on Dummy Locations in Mobile Internet Environment [J]. Netinfo Security, 2016, 16(10): 54-59. |
| [9] | Fu-xia ZHANG, Chao-hui JIANG. Research on Query Privacy Anonymity Algorithm Based on Grid Clustering [J]. Netinfo Security, 2015, 15(8): 53-58. |
| [10] | Hai-chuan ZHANG, Ze-mao ZHAO, Yu-jie TIAN. An Optimization Selection Research Based on Personalized Space Anonymous Algorithm [J]. Netinfo Security, 2015, 15(3): 23-27. |
| [11] | Yan-na WU, Ze-mao ZHAO. Research on Location Anonymity Method Based on Continuous Location Services Requests [J]. Netinfo Security, 2015, 15(1): 39-44. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||