Netinfo Security ›› 2023, Vol. 23 ›› Issue (3): 62-72.doi: 10.3969/j.issn.1671-1122.2023.03.007
Previous Articles Next Articles
Location Privacy Protection Scheme for Group Signature with Backward Unlinkability
ZHOU Quan1( ), ZENG Zhikang1, WANG Kemeng2, CHEN Menglong2
), ZENG Zhikang1, WANG Kemeng2, CHEN Menglong2
- 1. School of Mathematics and Information Science, Guangzhou University, Guangzhou 510006, China
2. School of Computer Science and Cyber Engineering, Guangzhou University, Guangzhou 510006, China
-
Received:2022-10-20Online:2023-03-10Published:2023-03-14 -
Contact:ZHOU Quan E-mail:zhouqq@gzhu.edu.cn
CLC Number:
Cite this article
ZHOU Quan, ZENG Zhikang, WANG Kemeng, CHEN Menglong. Location Privacy Protection Scheme for Group Signature with Backward Unlinkability[J]. Netinfo Security, 2023, 23(3): 62-72.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.03.007
| 符号 | 描述 |
|---|---|
| 安全参数,素数,循环群,生成元,哈希 函数 | |
| 群公钥,群私钥,追踪密钥,黑名单,系统参数 | |
| 位置服务请求计数器 | |
| 位置服务请求次数,最大位置服务请求次数 | |
| 位置服务请求,位置服务协同 | |
| 聚合结果,位置服务请求结果 |
| 阶段 | 实体 | 计算成本 |
|---|---|---|
| 用户注册 | ||
| 位置服务请求 | ||
| 协同服务响应 | ||
| 协同服务聚合 | ||
| 服务结果响应 | ||
| 用户追踪与撤销 |
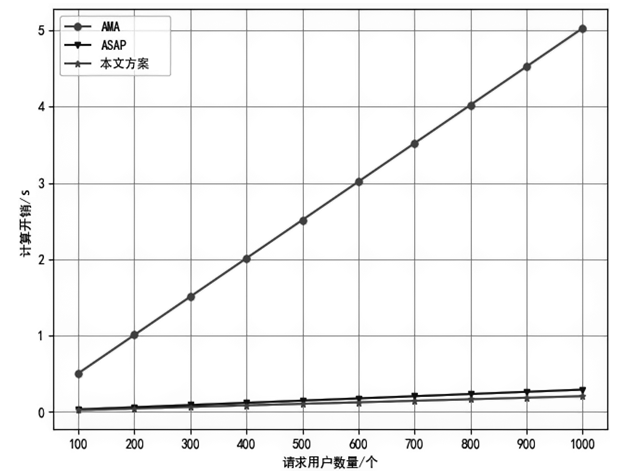
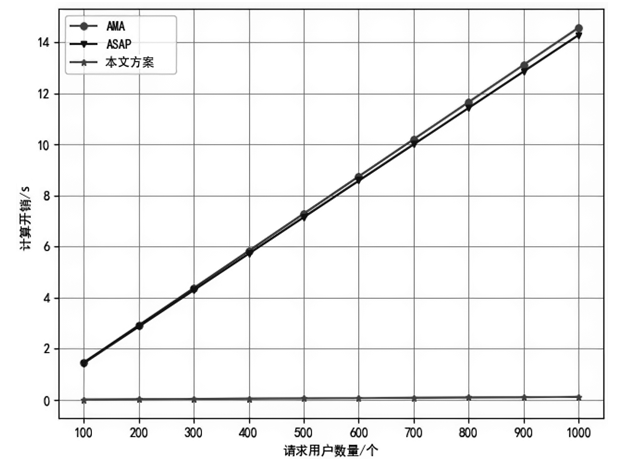
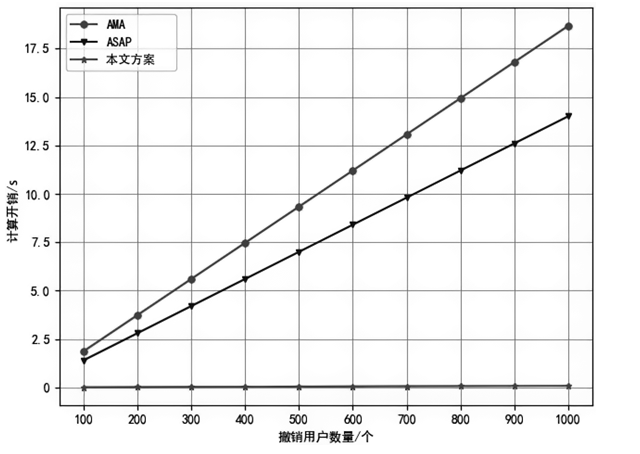
| 方案 | 用户注册 | 签名 | 签名验证 | 用户撤销 |
|---|---|---|---|---|
| AMA | ||||
| ASAP | ||||
| 本文方案 |
| [1] | QIAN Ping, WU Meng. Overview of Research and Methods on Privacy Protection of Internet of Things[J]. Application Research of Computers, 2013, 30 (1): 13-20. |
| 钱萍, 吴蒙. 物联网隐私保护研究与方法综述[J]. 计算机应用研究, 2013, 30(1): 13-20. | |
| [2] | LEE M, ATKISON T. VANET Applications: Past, Present, and Future[J]. Vehicular Communications, 2021, 28: 1-14. |
| [3] | ZHANG Shibing, WANG Tingting, ZHANG Xiaoge, et al. Current Situation and Development Strategy of Intelligent Transportation Vehicle Network[J]. Communications Technology, 2017, 50(7): 1345-1350. |
| 张士兵, 王婷婷, 张晓格, 等. 智能交通车载网的现状及其发展策略[J]. 通信技术, 2017, 50(7): 1345-1350. | |
| [4] | CHANG Cuyu, XIANG Yong, SHI Meilin. Status and Development of Vehicular Ad Hoc Networks[J]. Journal on Communications, 2007 (11): 116-126. |
| 常促宇, 向勇, 史美林. 车载自组网的现状与发展[J]. 通信学报, 2007(11): 116-126. | |
| [5] | SHEN Zhengchen, ZHANG Qianli, ZHANG Chaofan, et al. Location Privacy Attack Based on Deep Learning[J]. Journal of Computer Research and Development, 2022, 59(2): 390-402. |
| 沈钲晨, 张千里, 张超凡, 等. 基于深度学习的位置隐私攻击[J]. 计算机研究与发展, 2022, 59(2): 390-402. | |
| [6] | JIANG S, ZHU X, WANG L. An Efficient Anonymous Batch Authentication Scheme Based on HMAC for VANETs[J]. Journal of Robotics & Machine Learning, 2016, 17(8): 2193-2204. |
| [7] | MATSUO Y, OKAZAKI N, IZUMI K, et al. Inferring Long-Term User Properties Based on Users' Location History[C]// ACM.International Joint Conference on Artifical Intelligence. New York: ACM, 2007: 2159-2165. |
| [8] | HOH B, GRUTESER M. Protecting Location Privacy through Path Confusion[C]// IEEE. First International Conference on Security and Privacy for Emerging Areas in Communications Networks (SECURECOMM'05). New York: IEEE, 2005: 194-205. |
| [9] |
SONG C, QU Z, BLUMM N, et al. Limits of Predictability in Human Mobility[J]. Science, 2010, 327(5968): 1018-1021.
doi: 10.1126/science.1177170 pmid: 20167789 |
| [10] | ZHANG Xuejun, GUI Xiaolin, WU Zhongdong. Overview of Location Services Privacy Protection[J]. Journal of Software, 2015, 26(9): 2373-2395. |
| 张学军, 桂小林, 伍忠东. 位置服务隐私保护研究综述[J]. 软件学报, 2015, 26(9): 2373-2395. | |
| [11] | LU R L R, LIN X L X, LUAN T H, et al. Anonymity Analysis on Social Spot Based Pseudonym Changing for Location Privacy in VANETs[C]// IEEE. 2011 IEEE International Conference on Communications (ICC). New York: IEEE, 2011: 1-5. |
| [12] | WANG D, LI D, LI X, et al. An Analysis of Anonymity on Capacity Finite Social Spots Based Pseudonym Changing for Location Privacy in VANETs[C]// IEEE.12th International Conference on Fuzzy Systems and Knowledge Discovery (FSKD). New York:IEEE, 2015: 763-767. |
| [13] |
LI X, LIU T, OBAIDAT M S, et al. A Lightweight Privacy-Preserving Authentication Protocol for VANETs[J]. IEEE Systems Journal, 2020, 14(3): 3547-3557.
doi: 10.1109/JSYST.4267003 URL |
| [14] | CHEN X, LENZINI G, MAUW S, et al. A Group Signature Based Electronic Toll Pricing System[C]// IEEE. 2012 Seventh International Conference on Availability, Reliability and Security. New York: IEEE, 2012: 85-93. |
| [15] | ZHU Xiaoling, LU Yang, HOU Zhengfeng, et al. A Strong Privacy Protection Scheme Based on Inadvertent Transmission and Group Signature in VANET[J]. Application Research of Computers, 2014, 31(1): 226-230. |
| 朱晓玲, 陆阳, 侯整风, 等. VANET中基于不经意传输和群签名的强隐私保护方案[J]. 计算机应用研究, 2014, 31(1): 226-230. | |
| [16] | ZHENG Minghui, DUAN Yangyang, LYU Hanxiao. Research on Identity Authentication Protocol Based on Group Signature in Internet of Vehicles[J]. Advanced Engineering Sciences, 2018, 50(4): 130-134. |
| 郑明辉, 段洋洋, 吕含笑. 车联网中基于群签名的身份认证协议研究[J]. 工程科学与技术, 2018, 50(4): 130-134. | |
| [17] |
VIJAYAKUMAR P, AZEES M, CHANG V, et al. Computationally Efficient Privacy Preserving Authentication and Key Distribution Techniques for Vehicular Ad Hoc Networks[J]. Cluster Computing, 2017, 20(3): 2439-2450.
doi: 10.1007/s10586-017-0848-x URL |
| [18] |
YING B, NAYAK A. Anonymous and Lightweight Authentication for Secure Vehicular Networks[J]. IEEE Transactions on Vehicular Technology, 2017, 66(12): 10626-10636.
doi: 10.1109/TVT.2017.2744182 URL |
| [19] | NI J, ZHANG K, LIN X, et al. AMA: Anonymous Mutual Authentication with Traceability in Carpooling Systems[C]// IEEE. 2016 IEEE International Conference on Communications (ICC). New York: IEEE, 2016: 1-6. |
| [20] |
ZHU L, LI M, ZHANG Z, et al. ASAP: An Anonymous Smart-Parking and Payment Scheme in Vehicular Networks[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 17 (4): 703-715.
doi: 10.1109/TDSC.8858 URL |
| [21] | XIONG H, HOU Y, HUANG X, et al. Secure Message Classification Services Through Identity-Based Signcryption with Equality Test Towards the Internet of Vehicles[J]. Vehicular Communications, 2020, 26: 1-9. |
| [1] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [2] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [3] | CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology [J]. Netinfo Security, 2021, 21(4): 39-48. |
| [4] | WANG Xirui, LU Tianliang, ZHANG Jianling, DING Meng. Tor Anonymous Traffic Identification Method Based on Weighted Stacking Ensemble Learning [J]. Netinfo Security, 2021, 21(12): 118-125. |
| [5] | Quan ZHOU, Shumei XU, Ningbin YANG. A Privacy Protection Scheme for Smart Grid Based on Attribute-based Group Signature [J]. Netinfo Security, 2019, 19(7): 25-30. |
| [6] | Li XU, Rui ZHU, Yali ZENG. Location Privacy-preserving Scheme Based on SpaceTwist in Cognitive Radio Network [J]. Netinfo Security, 2019, 19(2): 18-27. |
| [7] | A-yong YE, Qing LI, Junlin JIN, Lingyu MENG. Research on a Dual-stealth Mechanism of User Identity and Location in Accessing Wireless Network [J]. Netinfo Security, 2018, 18(7): 29-35. |
| [8] | Zhibin ZHOU, Shaobo ZHANG, Entao LUO, Chaoliang LI. A Group RFID Tag Ownership Transfer Protocol without Trusted Third Party [J]. Netinfo Security, 2018, 18(6): 18-27. |
| [9] | Yue WANG, Xiangguo CHENG, Xuqi WANG. Research on Key-insulated Group Signature Scheme Based on Bilinear Pairings [J]. Netinfo Security, 2018, 18(6): 61-66. |
| [10] | Le WANG, Zherong YANG, Rongjing LIU, Xiang WANG. A CP-ABE Privacy Preserving Method for Wearable Devices [J]. Netinfo Security, 2018, 18(6): 77-84. |
| [11] | Yimin XIA, Chungen XU, Bennian DOU. An Anonymous Identity-based Encryption Scheme in the Standard Model [J]. Netinfo Security, 2018, 18(4): 72-78. |
| [12] | Na ZHAO, Hui LONG, Jinshu SU. A Scheme for Anonymous Authentication and Privacy Protection in the Internet of Things Environment [J]. Netinfo Security, 2018, 18(11): 1-7. |
| [13] | Shuo WANG, Xiangguo CHENG, Yameng CHEN, Yue WANG. Research on Key-insulated Group Signature Scheme [J]. Netinfo Security, 2017, 17(4): 40-45. |
| [14] | Yameng CHEN, Xiangguo CHENG, Shuo WANG, Ming GAO. Research on Certificateless Group Signature Scheme Based on Bilinear Pairings [J]. Netinfo Security, 2017, 17(3): 53-58. |
| [15] | Qing LI, A-yong YE, Li XU. Research on Security Issues of Wireless Access in Public Environment [J]. Netinfo Security, 2016, 16(4): 69-75. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||