Netinfo Security ›› 2021, Vol. 21 ›› Issue (12): 118-125.doi: 10.3969/j.issn.1671-1122.2021.12.016
Previous Articles Next Articles
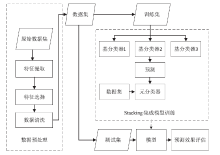
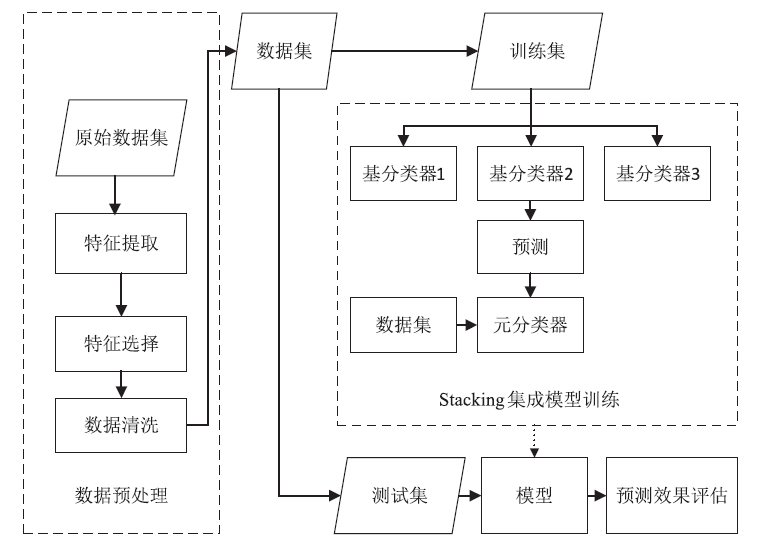
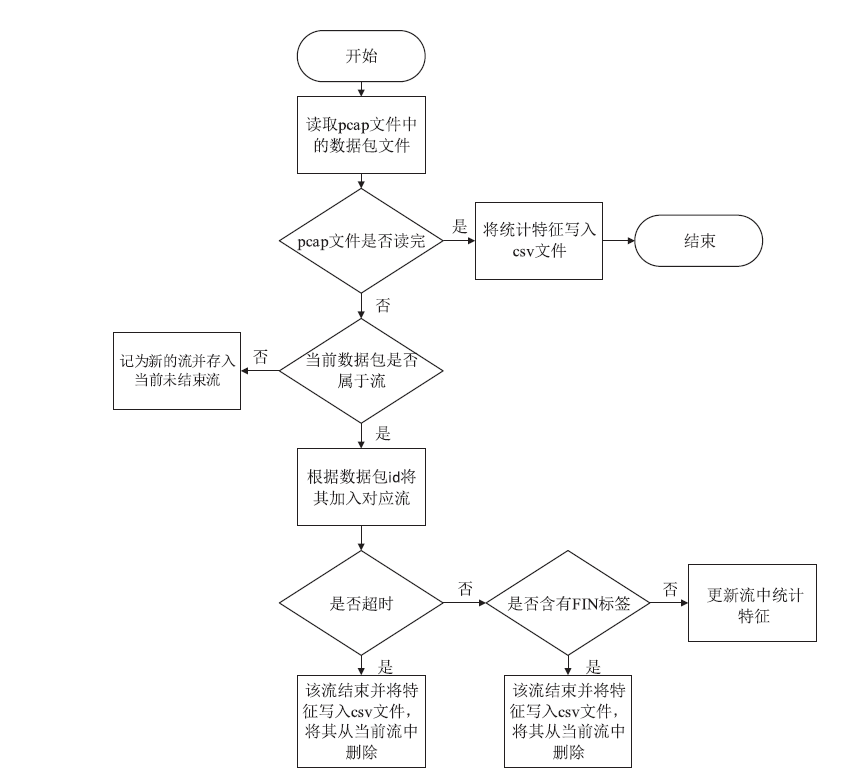
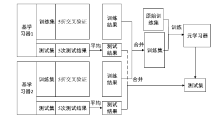
Tor Anonymous Traffic Identification Method Based on Weighted Stacking Ensemble Learning
WANG Xirui, LU Tianliang( ), ZHANG Jianling, DING Meng
), ZHANG Jianling, DING Meng
- College of Information Technology and Internet Security, People’s Public Security University of China, Beijing 100038, China
-
Received:2021-08-16Online:2021-12-10Published:2022-01-11 -
Contact:LU Tianliang E-mail:lutianliang@ppsuc.edu.cn
CLC Number:
Cite this article
WANG Xirui, LU Tianliang, ZHANG Jianling, DING Meng. Tor Anonymous Traffic Identification Method Based on Weighted Stacking Ensemble Learning[J]. Netinfo Security, 2021, 21(12): 118-125.
share this article
| 特征 | 特征描述 | 重要性 |
|---|---|---|
| Bwd IAT Std | 反向间隔时间标准差 | 138.9 |
| Bwd IAT Max | 反向间隔时间最大值 | 36.3 |
| Flow Bytes/s | 流字节/s | 28.3 |
| Flow Duration | 流持续时间 | 18.1 |
| Bwd IAT Min | 反向间隔时间最小值 | 13.8 |
| Flow IAT Min | 流间隔时间最小值 | 12.0 |
| Flow IAT Std | 流间隔时间标准差 | 11.6 |
| Flow IAT Max | 流间隔时间最大值 | 11.2 |
| Fwd IAT Mean | 正向间隔时间均值 | 10.9 |
| Bwd IAT Mean | 反向间隔时间均值 | 9.5 |
| Fwd IAT Std | 正向间隔时间标准差 | 9.5 |
| Fwd IAT Min | 正向间隔时间最小值 | 9.5 |
| Flow Packets/s | 流包数/s | 6.8 |
| Fwd IAT Max | 正向间隔时间最大值 | 6.0 |
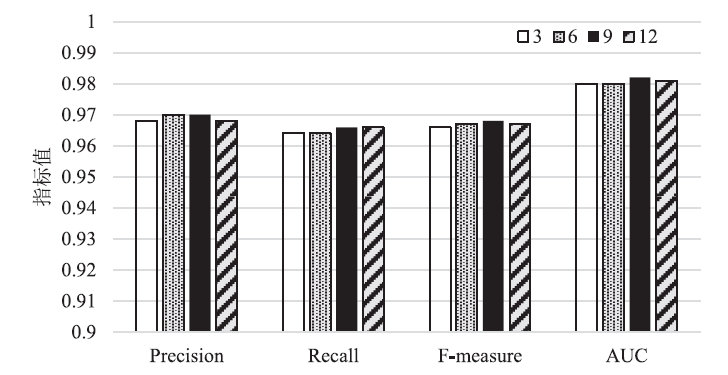
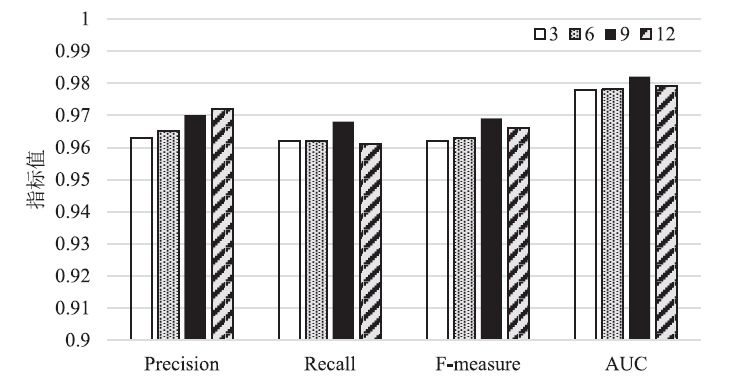
| Precision | Recall | F-measure | AUC | |
|---|---|---|---|---|
| SVM | 0.575 | 0.683 | 0.624 | 0.808 |
| KNN | 0.843 | 0.867 | 0.855 | 0.923 |
| NB | 0.349 | 0.934 | 0.508 | 0.851 |
| MLP | 0.826 | 0.838 | 0.832 | 0.907 |
| RF | 0.960 | 0.923 | 0.941 | 0.959 |
| GBDT | 0.914 | 0.768 | 0.835 | 0.879 |
| LightGBM | 0.956 | 0.951 | 0.953 | 0.972 |
| XGBoost | 0.964 | 0.959 | 0.962 | 0.977 |
| CNN[ | 0.982 | 0.884 | 0.930 | 0.940 |
| SAE[ | 0.974 | 0.877 | 0.922 | 0.936 |
| 加权Stacking模型(本文方案) | 0.978 | 0.975 | 0.976 | 0.986 |
| [1] | LASHKARI A H, DRAPER-GIL G, MAMUN M S I, et al. Characterization of Tor Traffic Using Time Based Features[C]// INSTICC. Proceedings of the 3rd International Conference on Information Systems Security and Privacy, February 19-21, 2017, Porto, Portugal. Lisbon: INSTICC, 2017: 253-262. |
| [2] | YAO Zhongjiang, GE Jingguo, ZHANG Xiaodan, et al. Research Review on Traffic Obfuscation and Its Corresponding Identification and Tracking Technologies[J]. Journal of Software, 2018, 29(10):313-330. |
| 姚忠将, 葛敬国, 张潇丹, 等. 流量混淆技术及相应识别,追踪技术研究综述[J]. 软件学报, 2018, 29(10):313-330. | |
| [3] | QI Yaxuan, XU Lianghong, YANG Baohua, et al. Packet Classification Algorithms: From Theory to Practice[C]// IEEE. INFOCOM 2009: International Conference on Computer Communications, April 19-25, 2009, Rio De Janeiro, Brazil. New York: IEEE, 2009: 648-656. |
| [4] | YEGANEH S H, EFTEKHAR M, GANJALI Y, et al. Cute: Traffic Classification Using Terms[C]// IEEE. 2012 21st International Conference on Computer Communications and Networks (ICCCN 2012), July 30-August 2, 2012, Munich, Germany. New York: IEEE, 2012: 1-9. |
| [5] |
HE Gaofeng, YANG Ming, LUO Junzhou, et al. Online Identification of Tor Anonymous Communication Traffic[J]. Journal of Software, 2013, 24(3):540-546.
doi: 10.3724/SP.J.1001.2013.04253 URL |
| 何高峰, 杨明, 罗军舟, 等. Tor匿名通信流量在线识别方法[J]. 软件学报, 2013, 24(3):540-556. | |
| [6] | WANG Liang, DYER KP, AKELLA A, et al. Seeing Through Network-protocol Obfuscation[C]// ACM. Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, October 12-16, 2015, Denver, CO, USA. New York: ACM, 2015: 57-69. |
| [7] | TAN Qingfeng, SHI Jinqiao, FANG Binxing, et al. Towards Measuring Unobservability in Anonymous Communication Systems[J]. Journal of Computer Research and Development, 2015, 52(10):2373-2381. |
| 谭庆丰, 时金桥, 方滨兴, 等. 匿名通信系统不可观测性度量方法[J]. 计算机研究与发展, 2015, 52(10):2373-2381. | |
| [8] | HU Bin, ZHOU Zhihong, YAO Lihong, et al. Malicious Traffic Detection Combining Features of Packet Payload and Stream Fingerprint[J]. Computer Engineering, 2020, 46(11):157-163. |
| 胡斌, 周志洪, 姚立红, 等. 结合报文负载与流指纹特征的恶意流量检测[J]. 计算机工程, 2020, 46(11):157-163. | |
| [9] | CAI Zhenzhen, JIANG Bo, LU Zhigang, et al. IsAnon: Flow-based Anonymity Network Traffic Identification Using Extreme Gradient Boosting[C]// IEEE. 2019 International Joint Conference on Neural Networks (IJCNN 2019), July 14-19, 2019, Budapest, Hungary. New York: IEEE, 2019: 1-8. |
| [10] | LIANG Di, HE Yongzhong. Obfs4 Traffic Identification Based on Multiple-feature Fusion[C]// IEEE. 2020 IEEE International Conference on Power, Intelligent Computing and Systems (ICPICS 2020), July 28-30, 2020, Shenyang, China. New York: IEEE, 2020: 323-327. |
| [11] |
LOTFOLLAHI M, SIAVOSHANI M J, ZADE R S H, et al. Deep Packet: A Novel Approach for Encrypted Traffic Classification Using Deep Learning[J]. Soft Computing, 2020, 24(3):1999-2012.
doi: 10.1007/s00500-019-04030-2 URL |
| [12] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN 2017), January 11-13, 2017, Da Nang, Vietnam. New York: IEEE, 2017: 712-717. |
| [13] |
HWANG R H, PENG Min Chun, NGUYEN V L, et al. An LSTM-based Deep Learning Approach for Classifying Malicious Traffic at the Packet Level[J]. Applied Sciences, 2019, 9(16):3414-3420.
doi: 10.3390/app9163414 URL |
| [14] |
DONG Xibin, YU Zhiwen, CAO Wenming, et al. A Survey on Ensemble Learning[J]. Frontiers of Computer Science, 2020, 14(2):241-258.
doi: 10.1007/s11704-019-8208-z |
| [15] | BREIMAN L. Bagging Predictors[J]. Machine learning, 1996, 24(2):123-140. |
| [16] | SCHAPIRE R E. A Brief Introduction to Boosting[C]// IJCAI. Proceedings of the 16th International Joint Conference on Artificial Intelligence, July 31-August 6, 1999, Stockholm, Sweden. San Mateo: Morgan Kaufmann, 1999: 1401-1406. |
| [17] | TING K M, WITTEN I H. Stacking Bagged and Dagged Models[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=bd4c4a7d1a38256b5e5099961f824232, 2021-06-21. |
| [18] |
KUMAR G, THAKUR K, AYYAGARI M R. MLEsIDSs: Machine Learning-based Ensembles for Intrusion Detection Systems—A Review[J]. The Journal of Supercomputing, 2020, 64(11):1-34.
doi: 10.1007/s11227-012-0817-3 URL |
| [19] | CHEN Tianqi, GUESTRIN C. XGBoost: A Scalable Tree Boosting System[C]// ACM. Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 13-17, 2016, San Francisco, CA, USA. New York: ACM, 2016: 785-794. |
| [20] | WANG Tengfei, CAI Manchun, YUE Ting, et al. Tor Anonymous Traffic Identification Based on Histogram-XGBoost[J]. Computer Engineering and Applications, 2021, 57(14):110-115. |
| 王腾飞, 蔡满春, 岳婷, 等. Histogram-XGBoost的Tor匿名流量识别[J]. 计算机工程与应用, 2021, 57(14):110-115. | |
| [21] | KE Guolin, MENG Qi, FINLEY T, et al. Lightgbm: A Highly Efficient Gradient Boosting Decision Tree[J]. Advances in Neural Information Processing Systems, 2017, 30(6):3146-3154. |
| [1] | LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm [J]. Netinfo Security, 2021, 21(9): 59-66. |
| [2] | WEN Weiping, HU Yezhou, ZHAO Guoliang, CHEN Xiarun. Design and Implementation of an Abnormal IP Identification System Based on Traffic Feature Classification [J]. Netinfo Security, 2021, 21(8): 1-9. |
| [3] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [4] | LI Dan, YAN Ting, GUO Rui. Quantum Color Image Encryption Algorithm Based on Alternating Quantum Walk [J]. Netinfo Security, 2021, 21(6): 45-51. |
| [5] | XU Guotian*, SHEN Yaotong. Multiple Classification Detection Method for Malware Based on XGBoost and Stacking Fusion Model [J]. Netinfo Security, 2021, 21(6): 52-62. |
| [6] | CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology [J]. Netinfo Security, 2021, 21(4): 39-48. |
| [7] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [8] | WANG Huazhong, CHENG Qi. Research on Intrusion Detection of Industrial Control System Based on Improved Whale Algorithm [J]. Netinfo Security, 2021, 21(2): 53-60. |
| [9] | LIU Yi, LI Jianhua, ZHANG Yitao, MENG Tao. Network Abnormal Flow Detection Method Based on Feature Attribute Information Entropy [J]. Netinfo Security, 2021, 21(2): 78-86. |
| [10] | CHU Zhiqiang, WU Jiying, XU Lei, DU Cong. A Distributed Off-chain Storage Framework Based on Blockchain [J]. Netinfo Security, 2021, 21(2): 87-93. |
| [11] | KANG Wenjie, ZHAO Wei, LIU Xuchong, SU Xin. Adjoint Relation Mining Model of Key Personnel Based on Discrete Trajectory [J]. Netinfo Security, 2021, 21(12): 31-37. |
| [12] | LI Pengchao, LIU Yanfei. Research on Forensics Technology of Malicious Code Based on Deleted PE File Header [J]. Netinfo Security, 2021, 21(12): 38-43. |
| [13] | GAO Jian, WANG Kaiyue, HUANG Shuhua. Research on Security Evaluation Index System for Video Monitoring Network [J]. Netinfo Security, 2021, 21(12): 78-85. |
| [14] | WANG Jian, YU Hang, HAN Zhen, HAN Lei. Access Control Methods of Data Sharing in Cloud Storage Based on Smart Contract [J]. Netinfo Security, 2021, 21(11): 40-47. |
| [15] | ZHANG Fucheng, FU Shaojing, XIA Jing, LUO Yuchuan. GlusterFS-based Distributed Data Integrity Verification System [J]. Netinfo Security, 2021, 21(1): 72-79. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||