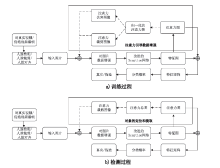
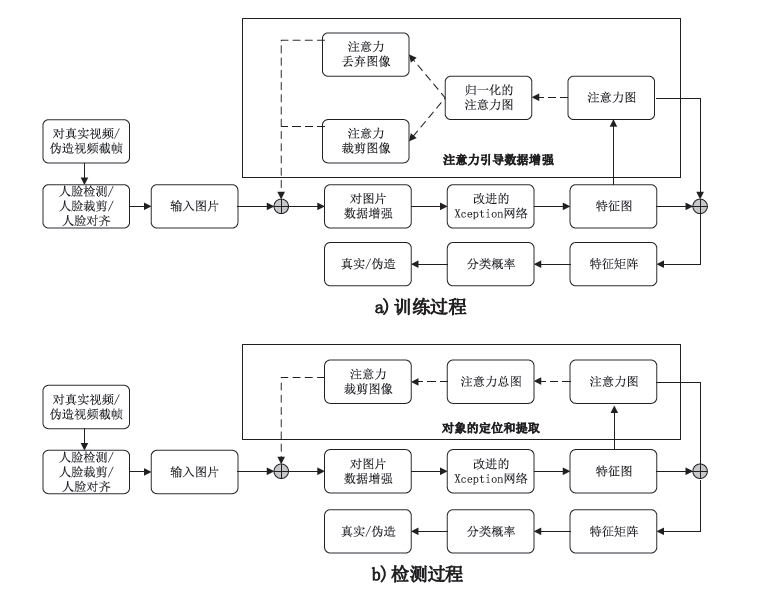
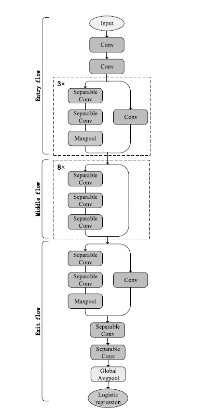
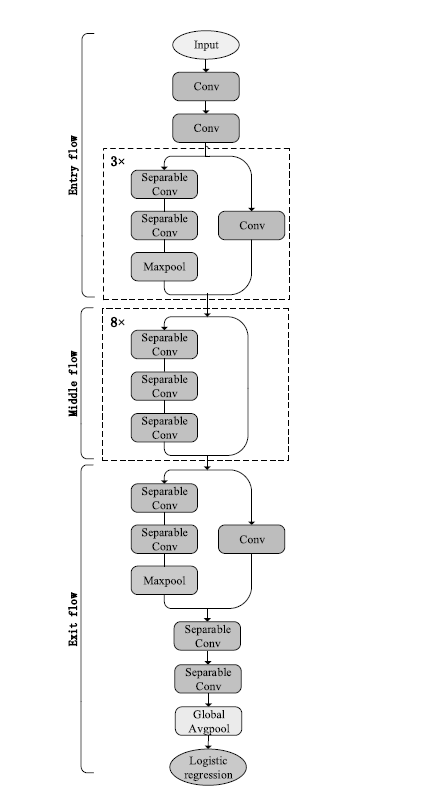
Netinfo Security ›› 2021, Vol. 21 ›› Issue (12): 109-117.doi: 10.3969/j.issn.1671-1122.2021.12.015
Previous Articles Next Articles
A Deep Forgery Video Detection Model Based on Improved Xception Network
MA Rui, CAI Manchun( ), PENG Shufan
), PENG Shufan
- College of Information Network Security, People’s Public University of China, Beijing 100038, China
-
Received:2021-11-05Online:2021-12-10Published:2022-01-11 -
Contact:CAI Manchun E-mail:caimanchun@ppsuc.edu.cn
CLC Number:
Cite this article
MA Rui, CAI Manchun, PENG Shufan. A Deep Forgery Video Detection Model Based on Improved Xception Network[J]. Netinfo Security, 2021, 21(12): 109-117.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.12.015
| Model | Acc | CrossEntropy Loss | Param-eters/MB | |||||
|---|---|---|---|---|---|---|---|---|
| Xception | Mini_Xception | SENet | WSDAN | FS | DP | FS | DP | |
| √ | — | — | — | 98.17% | 97.50% | 0.0863 | 0.1027 | 21.80 |
| √ | — | √ | — | 99.17% | 98.33% | 0.0752 | 0.0863 | 22.30 |
| √ | — | √ | √ | 99.50% | 98.83% | 0.0628 | 0.0786 | 20.53 |
| — | √ | — | — | 97.67% | 97.16% | 0.0893 | 0.1063 | 1.96 |
| — | √ | √ | — | 98.50% | 98.16% | 0.0796 | 0.0886 | 2.37 |
| — | √ | √ | √ | 99.17% | 98.50% | 0.0746 | 0.0832 | 2.05 |
| [1] |
SHU Kai, SLIVA A, WANG Suhang, et al. Fake News Detection on Social Media: A Data Mining Perspective[J]. ACM SIGKDD Explorations Newsletter, 2017, 19(1):22-36.
doi: 10.1145/3137597.3137600 URL |
| [2] | KINGMA D P, WELLING M. Auto-encoding Variational Bayes[EB/OL]. https://arxiv.org/abs/1312.6114, 2013-12-20. |
| [3] | REZENDE D J, MOHAMED S, WIERSTRA D. Stochastic Backpropagation and Approximate Inference in Deep Generative Models[C]// ICML. International Conference on Machine Learning, June 21-26,2014, Beijing, China. New York: PMLR, 2014: 1278-1286. |
| [4] |
GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[J]. Communications of the ACM, 2020, 63(11):139-144.
doi: 10.1145/3422622 URL |
| [5] | AGARWAL S, FARID H, GU Y, et al. Protecting World Leaders against Deep Fakes[C] // IEEE. In: Proc. of the IEEE Conf. on Computer Vision and Pattern Recognition Workshops, June 16-20, 2019, Long Beach, CA, USA. New York: IEEE, 2019: 38-45. |
| [6] | WANG Run, MA Lei, JUEFEI-XU F, et al. Fakespotter: A Simple Yet Robust Baseline for Spotting Ai-synthesized Fake Faces[EB/OL]. https://arxiv.org/abs/1909.06122, 2019-09-13. |
| [7] | AMOS B, LUDWICZUK B, SATYANARAYANAN M. Openface: A General-purpose Face Recognition Library with Mobile Applications[EB/OL]. http://reports-archive.adm.cs.cmu.edu/anon/anon/usr0/ftp/2016/CMU-CS-16-118.pdf, 2021-10-06. |
| [8] | SCHROFF F, KALENICHENKO D, PHILBIN J. Facenet: A Unified Embedding for Face Recognition and Clustering[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, June 7-12, 2015, Boston, MA, USA. New York: IEEE, 2015: 815-823. |
| [9] | AMERINI I, GALTERI L, CALDELLI R, et al. Deepfake Video Detection through Optical Flow Based CNN[C]// IEEE. In: Proc. of the IEEE International Conference. on Computer Vision Workshops, October 27-28, 2019, Seoul, Korea (South). New York: IEEE, 2019: 1205-1207. |
| [10] | SABIR E, CHENG Jiaxin, JAISWAL A, et al. Recurrent Convolutional Strategies for Face Manipulation Detection in Videos[J]. Interfaces (GUI), 2019, 3(1):80-87. |
| [11] | MITTAL T, BHATTACHARYA U, CHANDRA R, et al. Emotions Don’t Lie: An Audio-uisual Deepfake Detection Method Using Affective Cues[C]// ACM. Proceedings of the 28th ACM International Conference on Multimedia, October 12-16, 2020, Seattle, WA, USA. New York: ACM, 2020: 2823-2832. |
| [12] | LIMA O D, FRANKLIN S, BASU S, et al. Deepfake Detection Using Spatiotemporal Convolutional Networks[EB/OL]. https://arxiv.org/abs/2006.14749, 2020-06-26. |
| [13] | AFCHAR D, NOZICK V, YAMAGISHI J, et al. Mesonet: A Compact Facial Video Forgery Detection Network[C]// IEEE. In: Proc. of the IEEE Int’l Workshop on Information Forensics and Security (WIFS), December 11-13, 2018, Hong Kong, China. New York: IEEE, 2018: 1-7. |
| [14] | NGUYEN HH, YAMAGISHI J, ECHIZEN I. Capsule-forensics: Using Capsule Networks to Detect Forged Images and Videos[C]// IEEE. In: Proc. Of the IEEE Int’l Conf. on Acoustics, Speech and Signal Processing (ICASSP 2019), May 12-17, 2019, Brighton, United Kingdom. New York: IEEE, 2019: 2307-2311. |
| [15] | DANG Hao, LIU Feng, STEHOUWER J, et al. On the Detection of Digital Face Manipulation[C]// IEEE. In:Proc. of the IEEE Conference. on Computer Vision and Pattern Recognition (CVPR), May 12-17, 2019, Brighton, United Kingdom. New York: IEEE, 2020: 5780-5789. |
| [16] | TAN Mingxing, LE Q. Efficientnet: Rethinking Model Scaling for Convolutional Neural Networks[C]// ICML. International Conference on Machine Learning. June 9-15, 2019, Long Beach, California, USA. New York: PMLR, 2019: 6105-6114. |
| [17] | ZHU Xintong, TANG Yunqi, GENG Pengzhi. Detection Algorithm of Tamper and Deepfake Image Based on Feature Fusion[J]. Netinfo Security, 2021, 21(8):70-81. |
| 朱新同, 唐云祁, 耿鹏志. 基于特征融合的篡改与深度伪造图像检测算法[J]. 信息网络安全, 2021, 21(8):70-81. | |
| [18] | CHOLLET F. Xception: Deep Learning with Depthwise Separable Convolutions[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, July 21-26, 2017, Honolulu, HI, USA. NewYork: IEEE, 2017: 1251-1258. |
| [19] | CHEN Shuping, CHEN Bingcai. Research on Image Classification Method Based on Improved Xception Model[M]// LIANG Qilian,WANG Wei, MU Jiasong,et al.Artificial Intelligence in China. Singapore: Springer, 2021: 538-547. |
| [20] | WOO S, PARK J, LEE J Y, et al. Cbam: Convolutional Block Attention Module[C]// ICAIS. Proceedings of the European Conference on Computer Vision (ECCV), July 26-28, 2019, New York, NY, USA. New York: Springer, 2019: 3-19. |
| [21] | LIN Hao, LUO Weiqi, WEI Kangkang, et al. Improved Xception with Dual Attention Mechanism and Feature Fusion for Face Forgery Detection[EB/OL]. https://arxiv.org/abs/2109.14136, 2021-9-29. |
| [22] | HU Jie, SHEN Li, SUN Gang. Squeeze-and-excitation networks[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, July 26-28, 2019, New York, USA. New York: IEEE, 2018: 7132-7141. |
| [23] | HU Tao, QI Honggang, HUANG Qingming, et al. See Better Before Looking Closer: Weakly Supervised Data Augmentation Network for Fine-grained Visual Classification[EB/OL]. https://arxiv.org/abs/1901.09891, 2019-01-26. |
| [24] | DENG Jiankang, GUO Jia, ZHOU Yuxiang, et al. Retinaface: Single-stage Dense Face Localisation in the Wild[EB/OL]. https://arxiv.org/abs/1905.00641, 2019-05-02. |
| [25] |
SHORTEN C, KHOSHGOFTAAR T M. A Survey on Image Data Augmentation for Deep Learning[J]. Journal of Big Data, 2019, 6(1):1-48.
doi: 10.1186/s40537-018-0162-3 URL |
| [26] | CUBUK E D, ZOPH B, MANE D, et al. Autoaugment: Learning Augmentation Policies from Data[EB/OL]. https://arxiv.org/abs/1805.09501, 2018-05-24. |
| [27] | ROSSLER A, COZZOLINO D, VERDOLIVA L, et al. Faceforensics++: Learning to Detect Manipulated Facial Images[C]// IEEE. Proceedings of the IEEE/CVF International Conference on Computer Vision, October 27-November 2, 2019, Seoul, Korea (South). New York: IEEE, 2019: 1-11. |
| [1] | ZHU Xintong, TANG Yunqi, GENG Pengzhi. Detection Algorithm of Tamper and Deepfake Image Based on Feature Fusion [J]. Netinfo Security, 2021, 21(8): 70-81. |
| [2] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [3] | PAN Xiaoqin, DU Yanhui. Forged Voice Identification Method Based on Feature Fusion and Multi-channel GRU [J]. Netinfo Security, 2021, 21(10): 1-7. |
| [4] | XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM [J]. Netinfo Security, 2021, 21(10): 41-47. |
| [5] | WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model [J]. Netinfo Security, 2020, 20(9): 6-11. |
| [6] | WANG Wenhua, HAO Xin, LIU Yan, WANG Yang. The Safety Evaluation and Defense Reinforcement of the AI System [J]. Netinfo Security, 2020, 20(9): 87-91. |
| [7] | ZHANG Leihua, HUANG Jin, ZHANG Tao, WANG Shengyu. Portrait Intelligent Analysis Application and Algorithm Optimization in Video Investigation [J]. Netinfo Security, 2020, 20(5): 88-93. |
| [8] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [9] | BI Xinliang, YANG Haibin, YANG Xiaoyuan, HUANG Siyuan. Generative Steganography Scheme Based on StarGAN [J]. Netinfo Security, 2020, 20(12): 64-71. |
| [10] | CHENG Yang, LEI Min, LUO Qun. Access Authentication Method for IoT Terminal Devices Based on Deep Learning [J]. Netinfo Security, 2020, 20(11): 67-74. |
| [11] | Yongheng XIE, Yubo FENG, Qingfeng DONG, Mei WANG. Research on Data Ingestion Method Based on Deep Learning [J]. Netinfo Security, 2019, 19(9): 36-40. |
| [12] | Chunguang MA, Yaoyao GUO, Peng WU, Haibo LIU. Review of Image Enhancement Based on Generative Adversarial Networks [J]. Netinfo Security, 2019, 19(5): 10-12. |
| [13] | Yong FANG, Guangxiatian ZHU, Luping LIU, Peng JIA. Research on Browser Fuzz Sample Generation Technology Based on Deep Learning [J]. Netinfo Security, 2019, 19(3): 26-33. |
| [14] | ZHU Haiqi, JIANG Feng. Research and Analysis of Anomaly Detection Technology for Operation and Maintenance Data in the Era of Artificial Intelligence [J]. Netinfo Security, 2019, 19(11): 24-35. |
| [15] | Dagao DUAN, Yongheng XIE, Xinxin GAI, Zhanbin LIU. A Rumor Detection Model Based on Neural Network [J]. Netinfo Security, 2017, 17(9): 134-137. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||