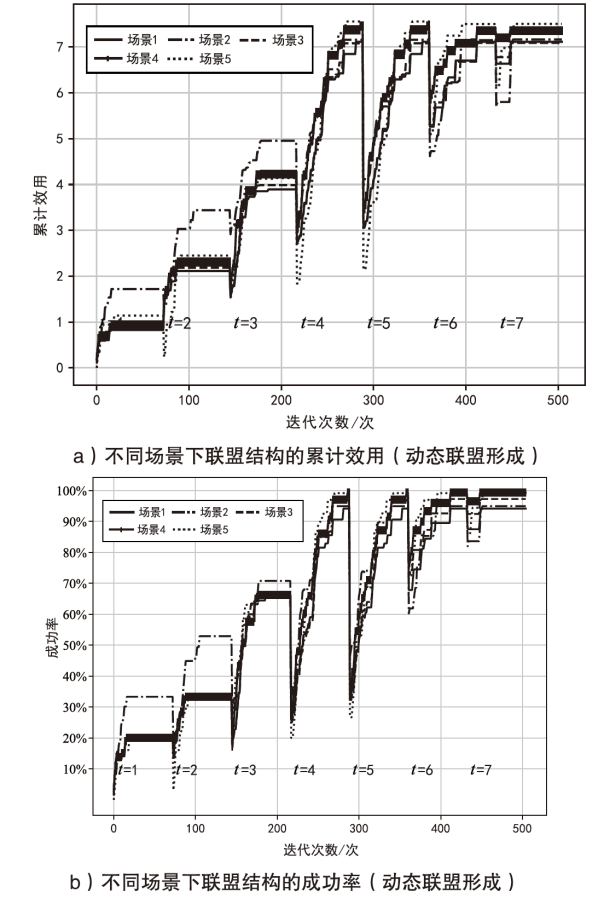
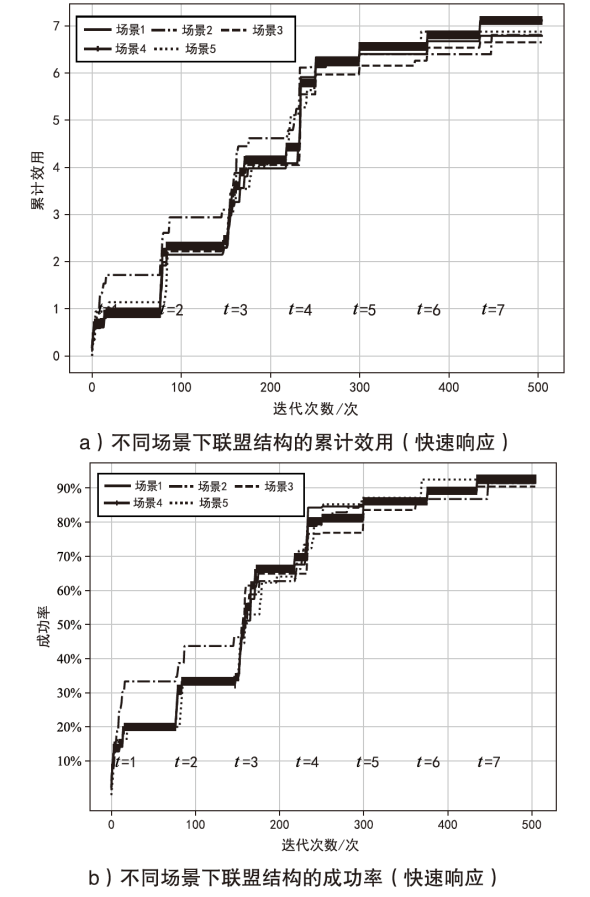
Netinfo Security ›› 2024, Vol. 24 ›› Issue (2): 217-228.doi: 10.3969/j.issn.1671-1122.2024.02.005
Previous Articles Next Articles
A Task Allocation Method for Unmanned Clusters Based on Dynamic Overlapping Coalition Toward Heterogeneous Composite Tasks
YAO Changhua1, CHENG Tianyuan1( ), QU Yuben2, SU Ting3
), QU Yuben2, SU Ting3
- 1. School of Electronics & Information Engineering, Nanjing University of Information Science & Technology, Nanjing 210044, China
2. College of Electronic and Information Engineering, Nanjing University of Aeronautics and Astronautics, Nanjing 211106, China
3. School of Information and Communication Engineering, Hainan University, Haikou 570228, China
-
Received:2023-06-21Online:2024-02-10Published:2024-03-06 -
Contact:CHENG Tianyuan E-mail:3383774180@qq.com
CLC Number:
Cite this article
YAO Changhua, CHENG Tianyuan, QU Yuben, SU Ting. A Task Allocation Method for Unmanned Clusters Based on Dynamic Overlapping Coalition Toward Heterogeneous Composite Tasks[J]. Netinfo Security, 2024, 24(2): 217-228.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.02.005
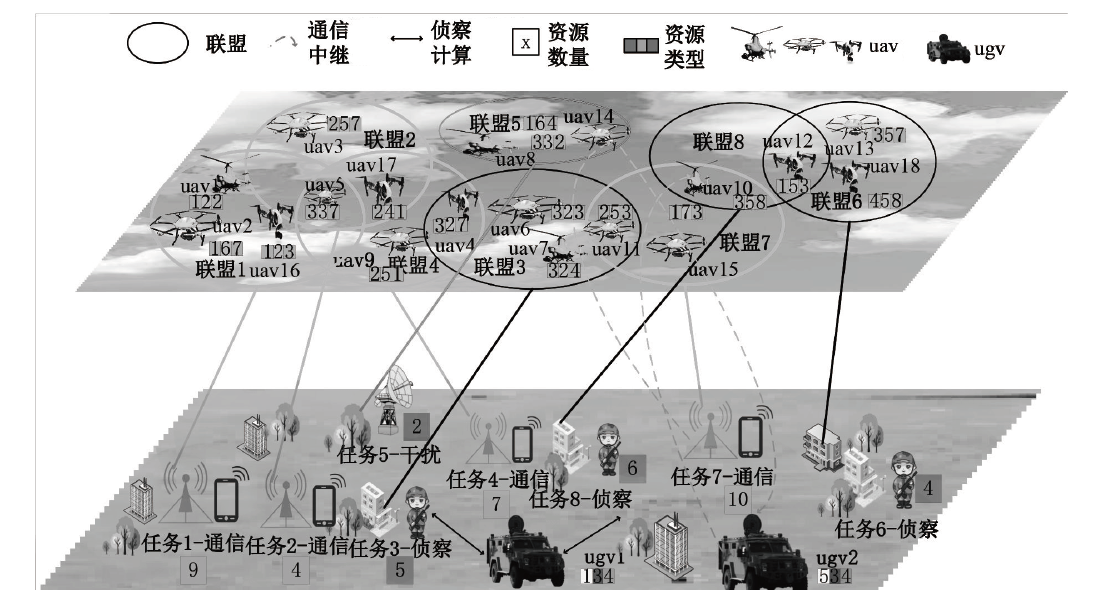
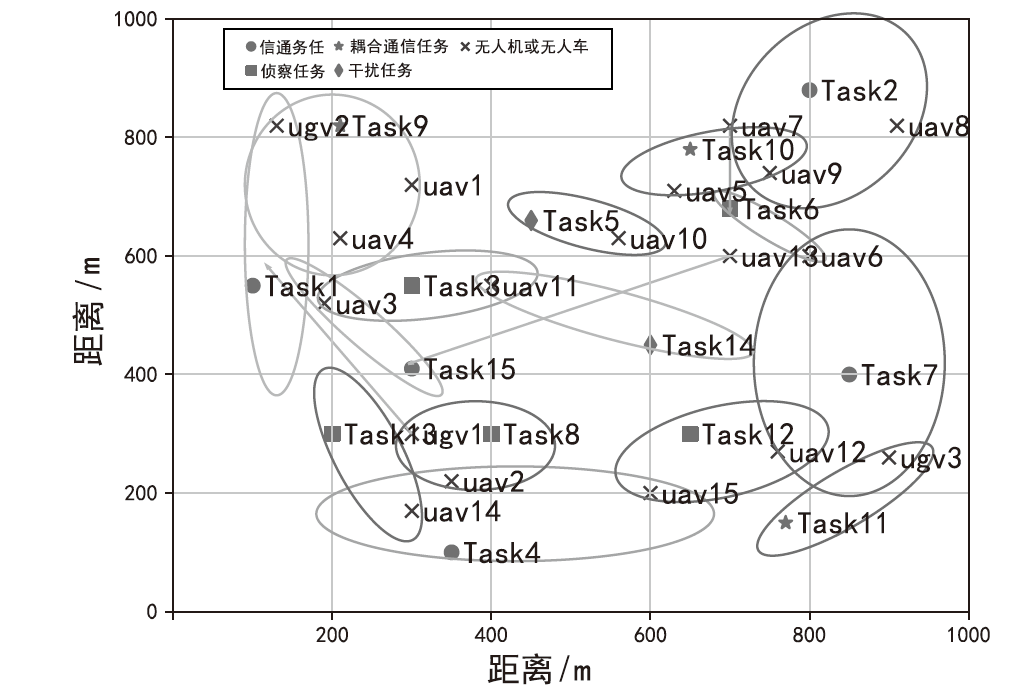
| 任务和无人集群成员的属性 | 任务15个、无人机15架、无人车3辆 |
|---|---|
| 任务开始时间/s | [4,3,1,3,3,4,2,4,1,4,4,1,3,3,2] |
| 任务结束时间/s | [8,6,3,7,7,7,5,6,6,6,8,6,6,6,4] |
| 任务价值 | [0.40,0.70,0.50,0.20,0.90,0.40,0.30,0.20,0.90,0.40,0.30,0.90,0.90,0.40,0.98] |
| 任务优先级 | [0.80,0.30,0.90,0.80,0.60,0.50,0.20,0.40,0.70,0.50,0.60,0.70,0.10,0.20,0.99] |
| 任务通信需求/Hz | [0.9,0.75,0.80,0.00,0.00,0.00,0.70,0.00,0.00,0.90,0.90,0.00,0.00,0.50,0.70] |
| 任务侦察需求/pixel | [0.00,0.00,0.00,0.84,0.80,1.00,0.00,0.80,0.60,0.80,0.84,0.00,0.00,0.00,0.80] |
| 任务干扰需求/Hz | [0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.50,0.75,0.00,0.00] |
| 任务位置/m | [(100,550),(800,880),(350,100),(300,550),(700,680),(400,300),(850,400),(650,300),(200,300),(210,820),(770,150),(450,660),(600,450),(300,410),(650,780)] |
| 无人机通信资源/Hz | [0.375,0.3125,0.250,0.475,0.500,0.3125,0.300,0.250,0.550,0.350,0.3125,0.400,0.550,0.3125,0.400] |
| 无人机侦察资源/pixel | [0.50,0.25,0.20,0.25,0.25,0.375,0.80,0.40,0.80,0.50,0.90,0.375,0.375,0.40,0.60] |
| 无人机干扰资源/Hz | [0.40,0.60,0.50,0.40,0.60,0.50,0.40,0.60, 0.50,0.15,0.70,0.50,0.40,0.60,0.50] |
| 无人机位置/m | [(300,720),(350,220),(190,520),(210,630),(630,710),(800,600),(700,820),(910,820),(750,740),(560,630),(400,550),(760,270),(700,600), (300,170),(600,200)] |
| 无人车通信资源/Hz | [0.500,0.700,0.975] |
| 无人车侦察资源/pixel | [0.7,0.7,0.8] |
| 无人车干扰资源/Hz | [0.4,0.6,0.5] |
| 无人车位置/m | [(300,300),(130,820),(900,260)] |
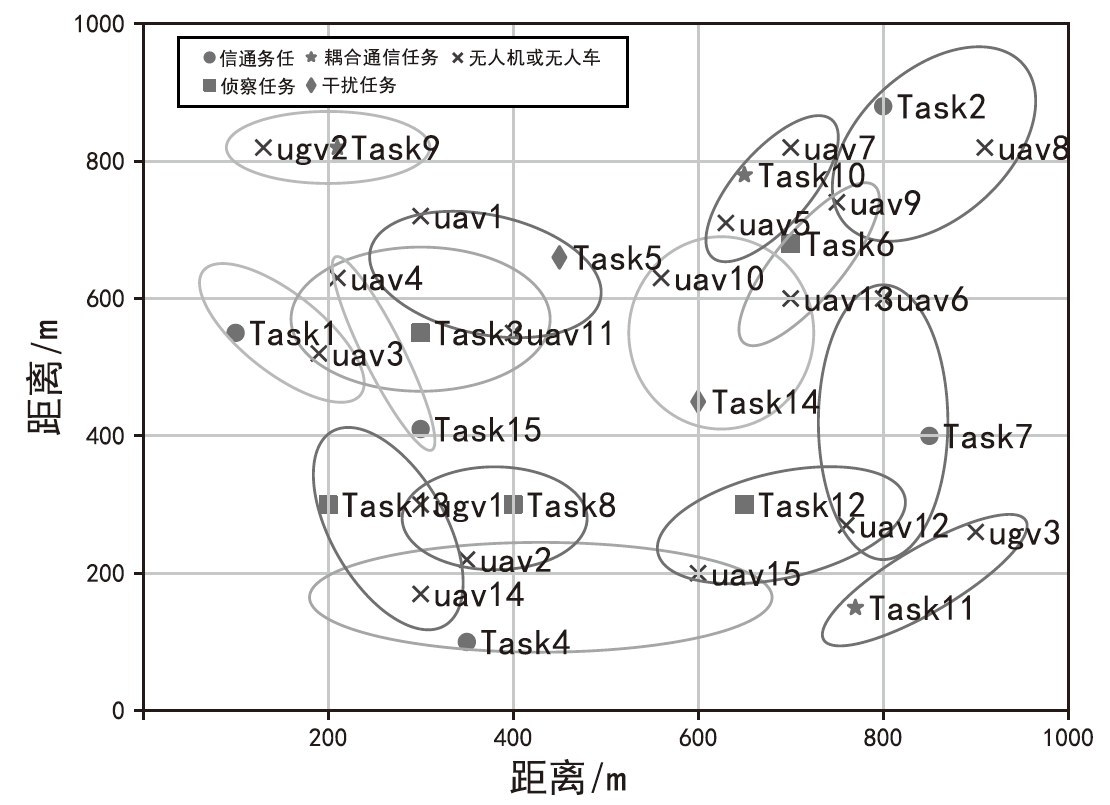
| 任务的属性 | 任务15个 |
|---|---|
| 任务通信需求/Hz | [0.90, 0.75, 0.50, 0.00, 0.00, 0.00, 0.70, 0.00, 0.00, 0.90, 0.90, 0.00, 0.00, 0.60, 0.70] |
| 任务侦察需求/pixel | [0.000, 0.000, 0.000, 1.000, 0.800, 1.000, 0.000, 0.375, 0.600, 0.800, 0.840, 0.000, 0.000, 0.000, 0.800] |
| 任务干扰需求/Hz | [0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.75, 0.50, 0.00, 0.00] |
| 无人集群成员的属性 | 无人机15架、无人车3辆 |
|---|---|
| 无人机通信资源/Hz | [0.3750, 0.3750, 0.4750, 0.4750, 0.5000, 0.4750, 0.3000, 0.2500, 0.5500, 0.3500, 0.3125, 0.4000, 0.5500, 0.3125, 0.400] |
| 无人机侦察资源/pixel | [0.500, 0.500, 0.250, 0.250, 0.250, 0.375, 0.800, 0.400, 0.800, 0.500, 0.800, 0.600, 0.375, 0.400, 0.600] |
| 无人机干扰资源/Hz | [0.4, 0.6, 0.5, 0.4, 0.4, 0.5, 0.4, 0.6, 0.5, 0.5, 0.7, 0.5, 0.4, 0.6, 0.5] |
| 无人车通信资源/Hz | [0.500, 0.550, 0.975] |
| 无人车侦察资源/pixel | [0.7, 0.7, 0.8] |
| 无人车干扰资源/Hz | [0.4, 0.6, 0.5] |
| 任务和无人集群成员的属性 | 无人机15架、无人车3辆 |
|---|---|
| 任务位置/m | [(100, 200),(800, 800),(180, 880),(520, 520),(390, 400),(870, 620),(650, 300),(110, 410),(310, 800),(610, 800),(300, 600),(200, 610),(600, 450),(800, 400),(700, 600)] |
| 无人机位置/m | [(250, 800),(360, 650),(180, 500),(260, 910),(130, 300),(260, 550),(60, 290),(300, 420),(900, 700),(440, 480),(520, 400),(700, 800),(800, 600),(770, 300),(700, 500)] |
| 无人车位置/m | [(500, 600),(630, 630),(300, 300)] |
| [1] |
PENG Qiang, WU Husheng, XUE Ruisong. Review of Dynamic Task Allocation Methods for UAV Swarms Oriented to Ground Targets[J]. Complex System Modeling and Simulation, 2021, 1(3): 163-175.
doi: 10.23919/CSMS.2021.0022 URL |
| [2] |
MOTLAGH N H, BAGAA M, TALEB T. Energy and Delay Aware Task Assignment Mechanism for UAV-Based IoT Platform[J]. IEEE Internet of Things Journal, 2019, 6(4): 6523-6536.
doi: 10.1109/JIoT.6488907 URL |
| [3] | MA Peibo, ZHONG Lin. Assignment of UAV Reconnaissance Task Based on Ant Colony Algorithm[J]. Radio Communications Technology, 2022, 48(2): 371-375. |
| 马培博, 钟麟. 基于蚁群算法的无人机侦察任务分配[J]. 无线电通信技术, 2022, 48(2): 371-375. | |
| [4] | GHAMRY K A, KAMEL M A,ZHANG Youmin. Multiple UAVs in Forest Fire Fighting Mission Using Particle Swarm Optimization[C]// IEEE. 2017 International Conference on Unmanned Aircraft Systems (ICUAS). New York:IEEE, 2017: 1404-1409. |
| [5] | BEKMEZCI I, ERMIS M, KAPLAN S. Connected Multi UAV Task Planning for Flying Ad Hoc Networks[C]// IEEE. 2014 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom). New York:IEEE, 2014: 28-32. |
| [6] |
CHEN Jiaxin, WU Qihui, XU Yuhua, et al. Joint Task Assignment and Spectrum Allocation in Heterogeneous UAV Communication Networks: A Coalition Formation Game-Theoretic Approach[J]. IEEE Transactions on Wireless Communications, 2021, 20(1): 440-452.
doi: 10.1109/TWC.7693 URL |
| [7] | SAAD W, ZHU Han, BASAR T, et al. A Selfish Approach to Coalition Formation Among Unmanned Air Vehicles in Wireless Networks[C]// Springer. 2009 International Conference on Game Theory for Networks. Heidelberg: Springer, 2009: 259-267. |
| [8] |
LUAN Heyu, XU Yitao, LIU Dianxiong, et al. Energy Efficient Task Cooperation for Multi-UAV Networks: A Coalition Formation Game Approach[J]. IEEE Access, 2020, 8: 149372-149384.
doi: 10.1109/Access.6287639 URL |
| [9] |
NGJS, LIM W YB, DAI H N, et al. Joint Auction-Coalition Formation Framework for Communication-Efficient Federated Learning in UAV-Enabled Internet of Vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2021, 22(4): 2326-2344.
doi: 10.1109/TITS.2020.3041345 URL |
| [10] |
LIU Dianxiong, XU Yuhua, XU Yitao, et al. Opportunistic Data Collection in Cognitive Wireless Sensor Networks: Air-Ground Collaborative Online Planning[J]. IEEE Internet of Things Journal, 2020, 7(9): 8837-8851.
doi: 10.1109/JIoT.6488907 URL |
| [11] | BARDHAN R, GHOSE D. Resource Allocation and Coalition Formation for UAVs: A Cooperative Game Approach[C]// IEEE. 2013 IEEE International Conference on Control Applications (CCA). New York:IEEE, 2013: 1200-1205. |
| [12] | CHEN Jiaxin, CHEN Ping, WU Qihui, et al. A Game-Theoretic Perspective on Resource Management for Large-Scale UAV Communication Networks[J]. China Communications, 2021, 18(1): 70-87. |
| [13] |
ZHANG Zengfeng, SONG Lingyang, HAN Zhu, et al. Coalitional Games with Overlapping Coalitions for Interference Management in Small Cell Networks[J]. IEEE Transactions on Wireless Communications, 2014, 13(5): 2659-2669.
doi: 10.1109/TWC.2014.032514.130942 URL |
| [14] |
DUAN Xiaojun, LIU Huiying, TANG Hong, et al. A Novel Hybrid Auction Algorithm for Multi-UAVs Dynamic Task Assignment[J]. IEEE Access, 2020, 8: 86207-86222.
doi: 10.1109/Access.6287639 URL |
| [15] | FU Xiaowei, FENG Peng, GAO Xiaoguang. Swarm UAVs Task and Resource Dynamic Assignment Algorithm Based on Task Sequence Mechanism[J]. IEEE Access, 2019, 99: 1-11. |
| [16] | ZHENG Hongxing, GUO Jifeng, XIE Xudong, et al. A Distributed Coalition Formation Method of Heterogeneous UAV Swarm in Unknown Dynamic Environment[J]. Journal of Astronautics, 2022, 43(2): 189-197. |
| 郑红星, 郭继峰, 谢旭东, 等. 一种未知动态环境下异构无人机集群分布式联盟形成方法[J]. 宇航学报, 2022, 43(2): 189-197. | |
| [17] | AFGHAH F, ZAERI-AMIRANI M, RAZI A, et al. A Coalition Formation Approach to Coordinated Task Allocation in Heterogeneous UAV Networks[C]// IEEE. 2018 Annual American Control Conference (ACC). New York:IEEE, 2018: 5968-5975. |
| [18] |
SAAD W, ZHU Han, BASAR T, et al. Hedonic Coalition Formation for Distributed Task Allocation among Wireless Agents[J]. IEEE Transactions on Mobile Computing, 2011, 10(9): 1327-1344.
doi: 10.1109/TMC.2010.242 URL |
| [19] |
LIU Zhong, GAO Xiaoguang, FU Xiaowei, et al. Coalition Formation of Multiple Heterogeneous Unmanned Aerial Vehicles in Cooperative Search and Attack in Unknown Environment[J]. Acta Armamentarii, 2015, 36(12): 2284-2297.
doi: 10.3969/j.issn.1000-1093.2015.12.011 |
|
刘重, 高晓光, 符小卫, 等. 未知环境下异构多无人机协同搜索打击中的联盟组建[J]. 兵工学报, 2015, 36(12): 2284-2297.
doi: 10.3969/j.issn.1000-1093.2015.12.011 |
|
| [20] |
QI Nan, HUAGN Zanqi, ZHOU Fuhui, et al. A Task-Driven Sequential Overlapping Coalition Formation Game for Resource Allocation in Heterogeneous UAV Networks[J]. IEEE Transactions on Mobile Computing, 2022, 22(8): 4439-4455.
doi: 10.1109/TMC.2022.3165965 URL |
| [21] | WANG Hui, LIU Shuang. Task Allocation of Multi-UAV Coalition Based on Resource Constraints[J]. Journal of East China University of Science and Technology, 2021, 47(4): 504-509. |
| 王辉, 刘爽. 基于资源约束的多无人机联盟的任务分配[J]. 华东理工大学学报(自然科学版), 2021, 47(4): 504-509. | |
| [22] | YAO Changhua, AN Lei. Autonomous Collaborative Optimization of UAV Swarms for Multimode Heterogeneous Task[J]. Telecommunication Engineering, 2023, 63(8): 1151-1158. |
| 姚昌华, 安蕾. 面向多模异构任务的无人机群自主协同优化[J]. 电讯技术, 2023, 63(8): 1151-1158. |
| [1] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [2] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [3] | GU Yanyan, SHEN Limin, GAO Chenxu, ZHU Ting. Efficient and Secure Certificateless Aggregate Signature Scheme in Vehicle Networks [J]. Netinfo Security, 2024, 24(2): 188-202. |
| [4] | ZHAO Geng, MA Yingjie, DONG Youheng. New Progress in Research and Application of Chaotic Cryptography Theory [J]. Netinfo Security, 2024, 24(2): 203-216. |
| [5] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [6] | NIU Ke, LIANG Yucheng, MENG Yifei, WANG Jingjing. Dual Embedding Domain Based Video Robust Reversible Watermarking Algorithm [J]. Netinfo Security, 2024, 24(2): 239-251. |
| [7] | HUANG Haiyan, AI Yuxin, LIANG Linlin, LI Zan. Analysis of Physical Layer Security Performance in RSMA Wireless Communication Systems under Eavesdropper Attacks [J]. Netinfo Security, 2024, 24(2): 252-261. |
| [8] | LIN Yihang, ZHOU Pengyuan, WU Zhiqian, LIAO Yong. Federated Learning Backdoor Defense Method Based on Trigger Inversion [J]. Netinfo Security, 2024, 24(2): 262-271. |
| [9] | ZHAO Pengcheng, YU Junqing, LI Dong. An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning [J]. Netinfo Security, 2024, 24(2): 272-281. |
| [10] | WANG Juan, GONG Jiaxin, LIN Ziqing, ZHANG Xiaojuan. Multidimensional Depth Oriented Fuzzing Method of Java Web Applications [J]. Netinfo Security, 2024, 24(2): 282-292. |
| [11] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [12] | YAN Hailong, WANG Shulan. Design and Implementation of Integrated Service Platform for Real Estate Registration Based on Domestic Cryptographic Technology [J]. Netinfo Security, 2024, 24(2): 303-308. |
| [13] | SUN Hongzhe, WANG Jian, WANG Peng, AN Yulong. Network Intrusion Detection Method Based on Attention-BiTCN [J]. Netinfo Security, 2024, 24(2): 309-318. |
| [14] | YU Shangrong, XIAO Jingbo, YIN Qilin, LU Wei. A Social Heterophily Focused Framework for Social Bot Detection [J]. Netinfo Security, 2024, 24(2): 319-327. |
| [15] | LAI Chengzhe, ZHAO Yining, ZHENG Dong. A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(1): 93-105. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||