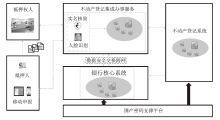
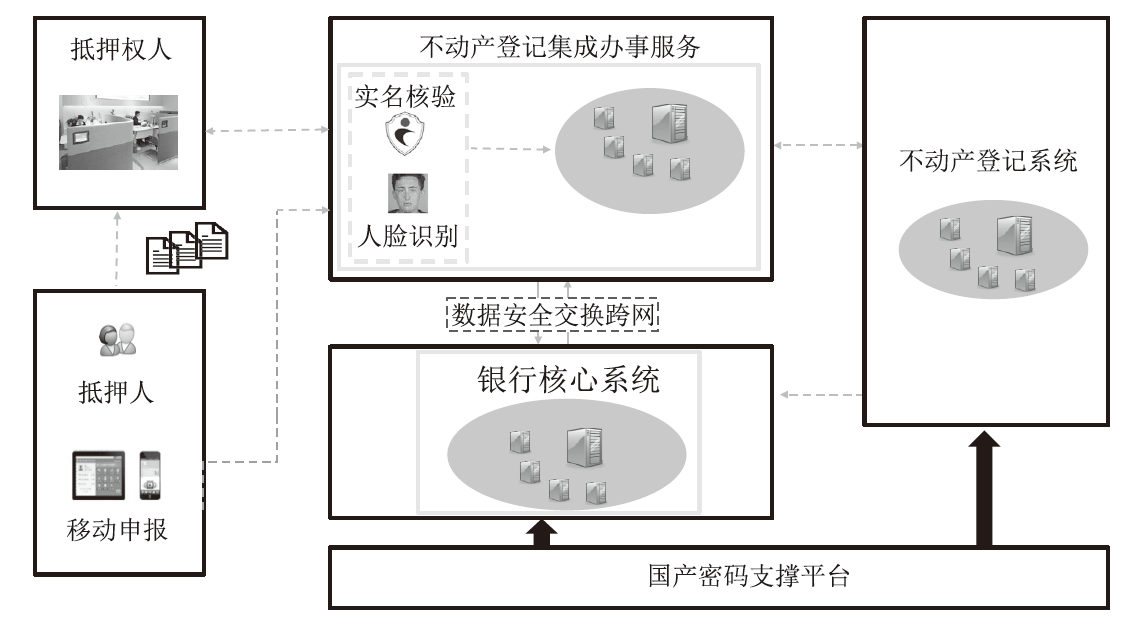
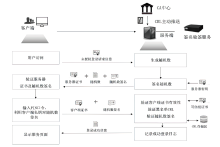
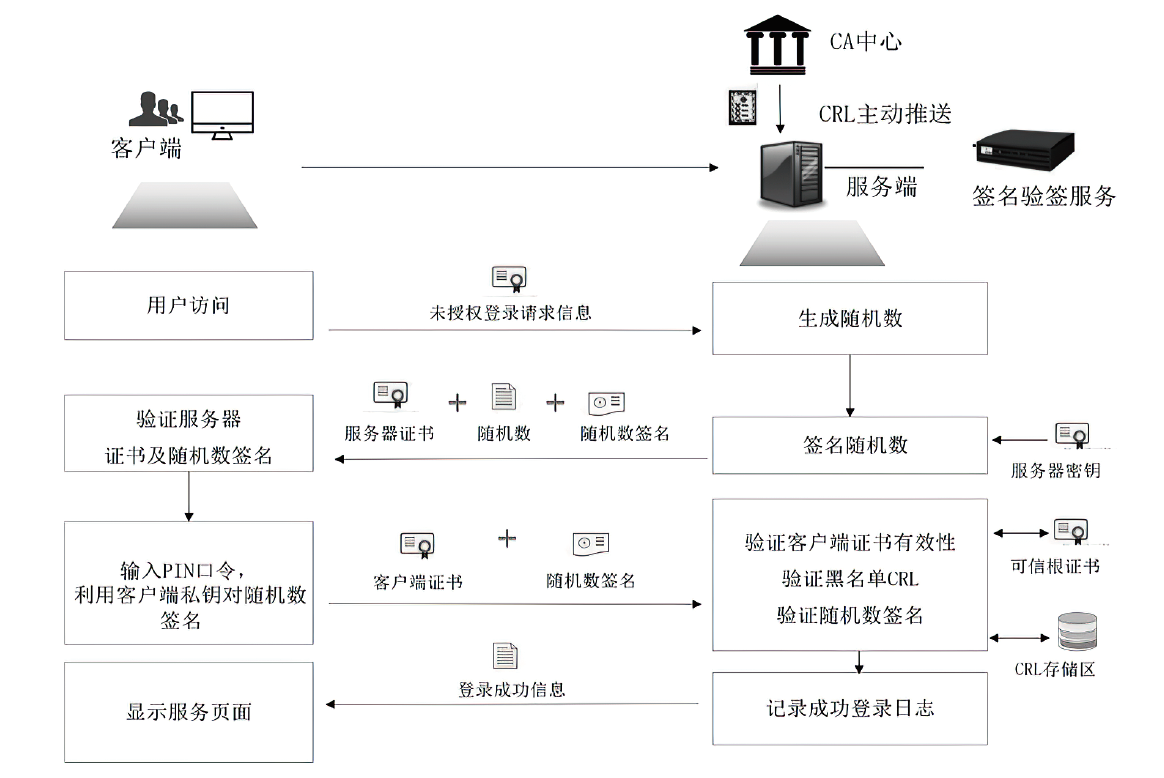
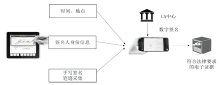
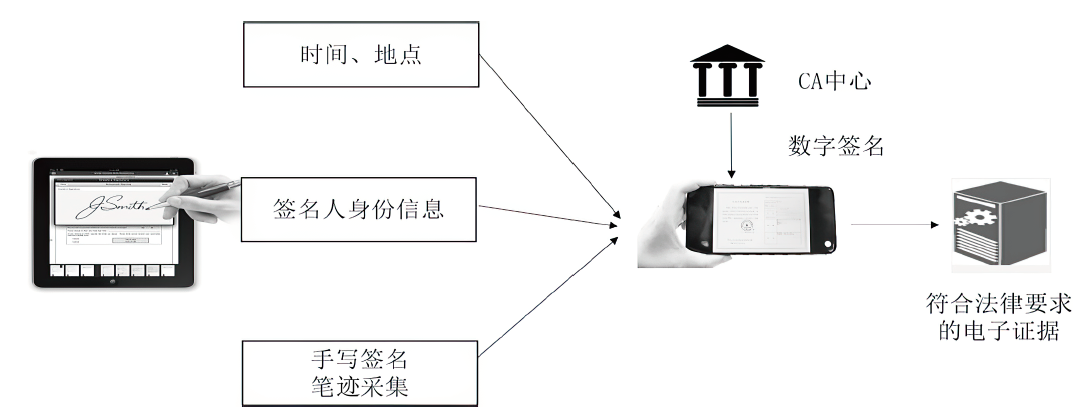
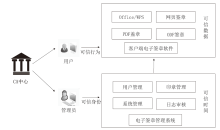
| [1] |
WEN Qingfeng, YANG Wenjie, ZHANG Yongqiang. Application of SM9 and PKI in E-Government E-Mail System[J]. Computer Applications and Software, 2017, 34(4): 105-109.
|
|
闻庆峰, 杨文捷, 张永强. SM9及其PKI在电子政务邮件系统中的应用[J]. 计算机应用与软件, 2017, 34(4): 105-109.
|
| [2] |
TEWARI H, HUGHES A, WEBER S, et al. X509 Cloud-Framework for a Ubiquitous PKI[C]// IEEE. MILCOM 2017 IEEE Military Communications Conference. New York: IEEE, 2017: 225-230.
|
| [3] |
LOZUPONE V. Analyze Encryption and Public Key Infrastructure (PKI)[J]. International Journal of Information Management, 2018, 38(1): 42-44.
doi: 10.1016/j.ijinfomgt.2017.08.004
URL
|
| [4] |
MANE A E, YOUNES C, KORCHIYNE R. Digital Signature for Data and Documents Using Operating PKI Certificates[EB/OL]. (2021-01-01)[2023-07-01]. https://www.shs-conferences.org/articles/shsconf/pdf/2021/30/shsconf_qqr2021_07004.pdf.
|
| [5] |
DOLGOV V I, LISITSKA I V, LISITSKYI K Y. The New Concept of Block Symmetric Ciphers Design[J]. Telecommunications and Radio Engineering, 2017, 76(2): 157-184.
doi: 10.1615/TelecomRadEng.v76.i2
URL
|
| [6] |
BRADLEY T, CAMENISCH J, JARECKI S, et al. Password-Authenticated Public-Key Encryption[C]// Springer. 17th Applied Cryptography and Network Security:International Conference. Heidelberg: Springer, 2019: 442-462.
|
| [7] |
ZHAO Yuliang, HU Wei, ZHANG Bing, et al. A Survey on National Commercial Cryptography Algorithms[C]// Chinese Society for Electrical Engineering. 2016 Electricity Industry Informatization Annual Conference. Beijing: China Industrial and Information Publishing Group, 2016: 132-134.
|
|
赵宇亮, 胡威, 张冰, 等. 国家商用密码算法综述[C]// 中国电机工程学会. 2016电力行业信息化年会. 北京: 中国工信出版集团, 2016: 132-134.
|
| [8] |
EUM S W, KIM H J, KWON H D, et al. Implementation of SM4 Block Cipher on CUDA GPU and Its Analysis[C]// IEEE. 2022 International Conference on Platform Technology and Service (PlatCon). New York:IEEE, 2022: 22-24.
|
| [9] |
LIU Ying, LIANG Hua, WANG Wen, et al. New Linear Cryptanalysis of Chinese Commercial Block Cipher Standard SM4[EB/OL]. (2017-06-08)[2023-07-01]. https://www.hindawi.com/journals/scn/2017/1461520/.
|
| [10] |
LANG Huan, ZHANG Lei, WU Wenling. Fast Software Implementation of SM4[J]. Journal of University of Chinese Academy of Sciences, 2018, 35(2): 180-187.
doi: 10.7523/j.issn.2095-6134.2018.02.005
|
|
郎欢, 张蕾, 吴文玲. SM4的快速软件实现技术[J]. 中国科学院大学学报, 2018, 35(2): 180-187.
doi: 10.7523/j.issn.2095-6134.2018.02.005
|
| [11] |
LU Jie, LI Jie.Cryptanalysis of Two White-Box Implementations of the SM4 Block Cipher[C]// Springer. Information Security:24th International Conference(ISC 2021). Heidelberg:Springer, 2021: 54-69.
|
| [12] |
GB/T 33133.1-2016 Information Security Technology-ZUC Stream Cipher Algorithm-Part 1: Algorithm Description[S]. Beijing: Standards Press of China, 2016.
|
|
GB/T 33133.1-2016 信息安全技术祖冲之序列密码算法第1部分:算法描述[S]. 北京: 中国标准出版社, 2016.
|
| [13] |
GB/T 38635.1-2020 Information Security Technology, SM9 Identification Password Algorithm Part 1: General[S]. Beijing: Standards Press of China, 2020.
|
|
GB/T 38635.1-2020 信息安全技术 SM9标识密码算法第1部分:总则[S]. 北京: 中国标准出版社, 2020.
|
| [14] |
GB/T 32905-2016 Information Security Technology, SM3 Password Hash Algorithm[S]. Beijing: Standards Press of China, 2016.
|
|
GB/T 32905-2016 信息安全技术 SM3密码杂凑算法[S]. 北京: 中国标准出版社, 2016.
|
| [15] |
GB/T 38540-2020 Information Security Technology, Technical Specification for Secure Electronic Signature Password[S]. Beijing: Standards Press of China, 2020.
|
|
GB/T 38540-2020 信息安全技术安全电子签章密码技术规范[S]. 北京: 中国标准出版社, 2020.
|
| [16] |
GB/T 15843.3-2016 Information Security Technology, Security Technology, Entity Authentication Part 3: Mechanisms Using Digital Signature Technology[S]. Beijing: Standards Press of China, 2008.
|
|
GB/T 15843.3-2016 信息技术安全技术实体鉴别第3部分:采用数字签名技术的机制[S]. 北京: 中国标准出版社, 2008.
|