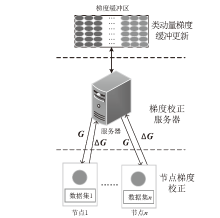
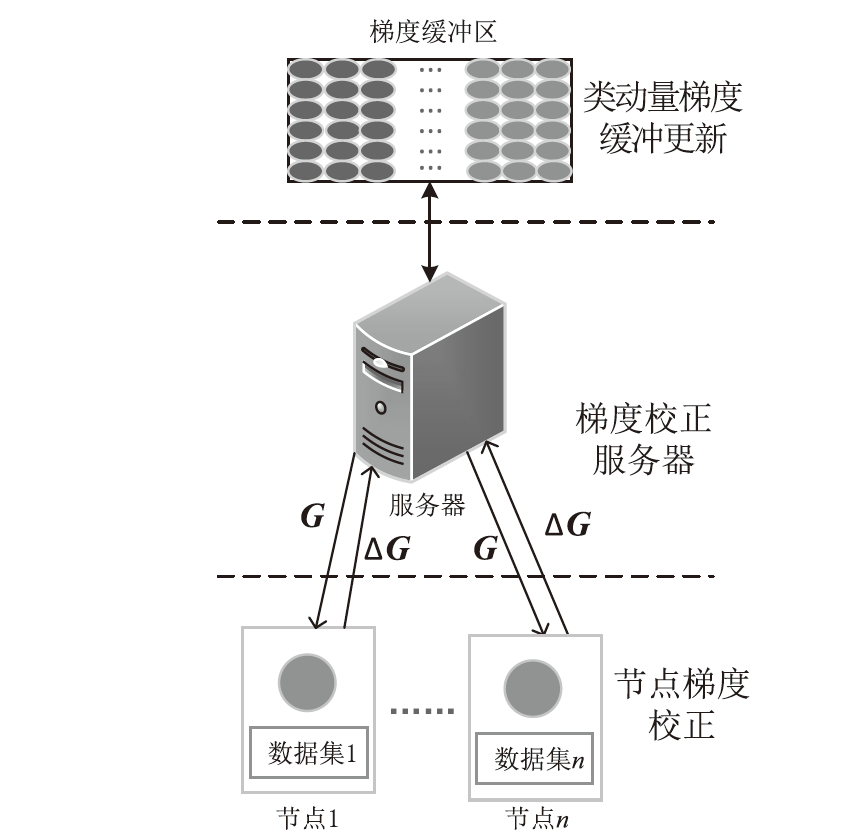
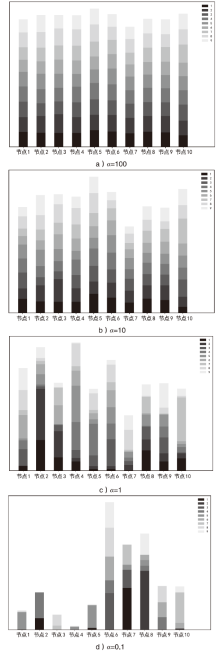
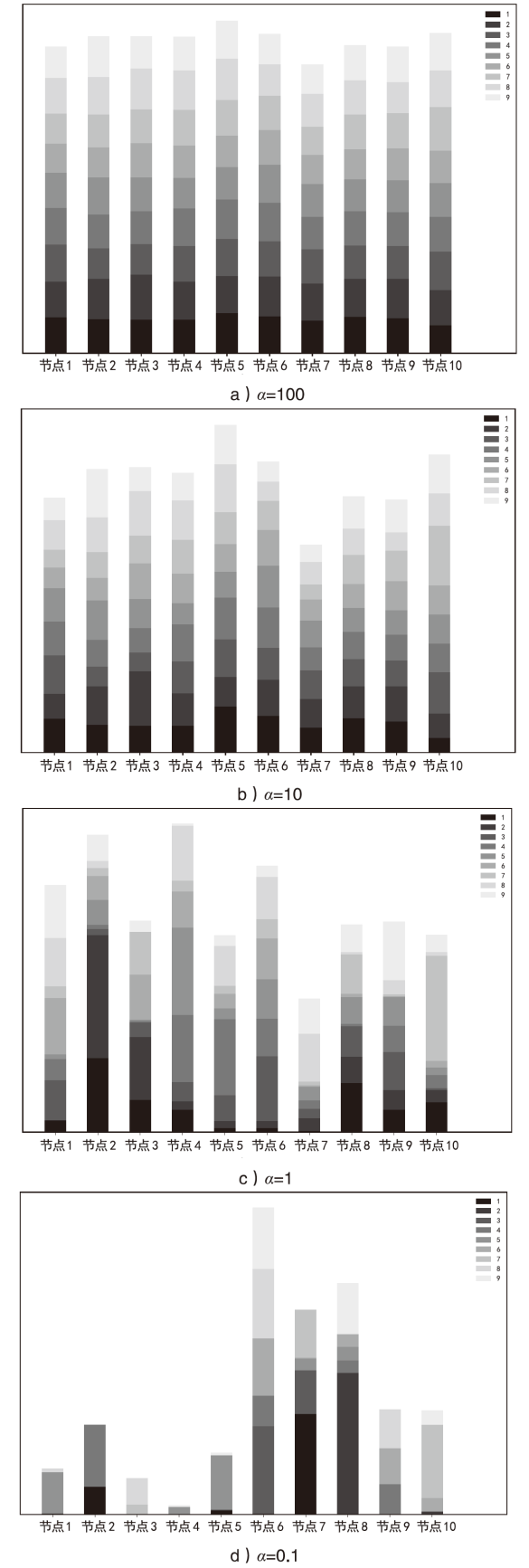
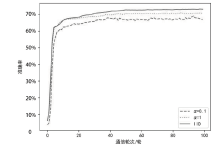
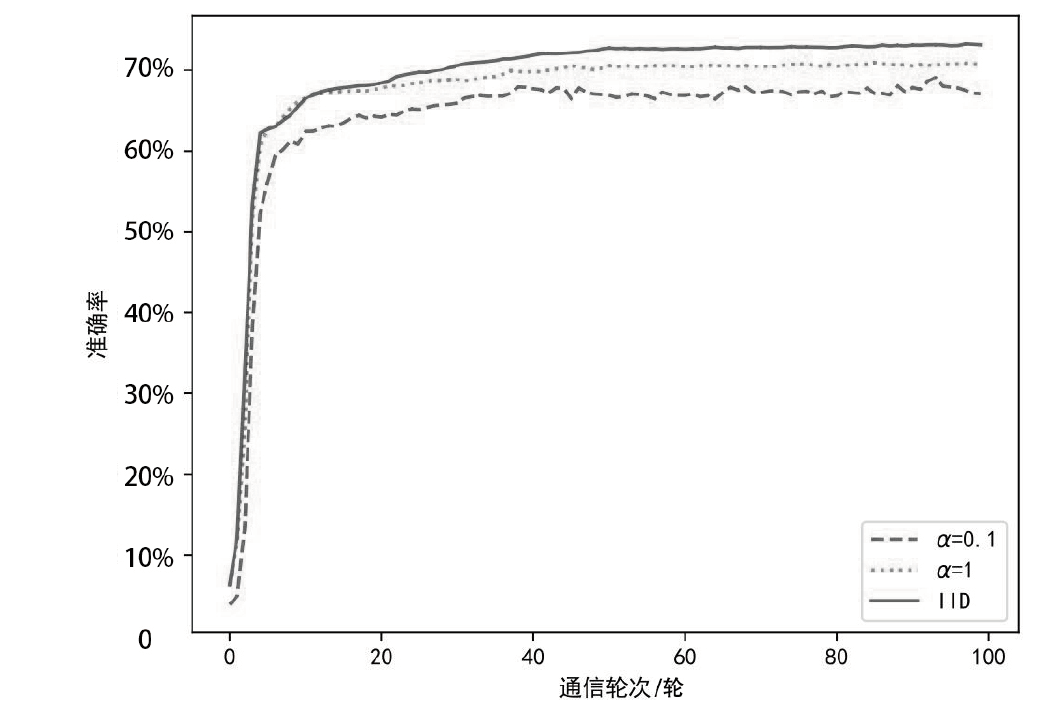
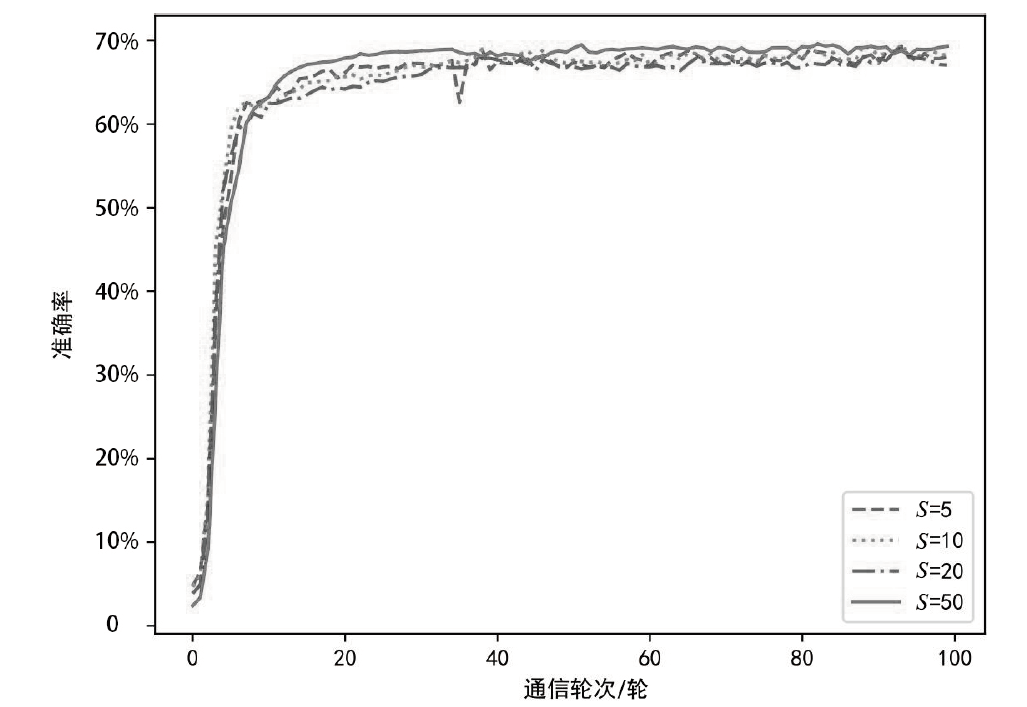
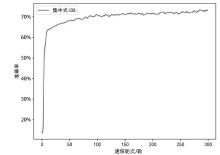
Netinfo Security ›› 2024, Vol. 24 ›› Issue (2): 293-302.doi: 10.3969/j.issn.1671-1122.2024.02.012
Previous Articles Next Articles
Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference
JIN Zhigang, DING Yu, WU Xiaodong( )
)
- School of Electrical and Information Engineering, Tianjin University, Tianjin 300072, China
-
Received:2023-12-28Online:2024-02-10Published:2024-03-06 -
Contact:WU Xiaodong E-mail:xdwu@tju.edu.cn
CLC Number:
Cite this article
JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference[J]. Netinfo Security, 2024, 24(2): 293-302.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.02.012
| [1] | IBM Security, Ponemon Institute. Cost of a Data Breach Report 2022[EB/OL]. (2022-08-08)[2023-12-12]. https://max.book118.com/html/2022/0803/6242012004004221.shtm. |
| [2] | BUCZAK A L, GUVEN E. A Survey of Data Mining and Machine Learning Methods for Cyber Security Intrusion Detection[J]. IEEE Communications Surveys & Tutorials, 2016, 18(2): 1153-1176. |
| [3] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network[J]. Netinfo Security, 2020, 20(4): 47-54. |
| 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. | |
| [4] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2016-02-17)[2023-12-10]. http://arxiv.org/abs/1602.05629. |
| [5] | BAI Hongpeng, DENG Dongxu, XU Guangquan, et al. Research on Intrusion Detection Mechanism Based on Federated Learning[J]. Netinfo Security, 2022, 22(1): 46-54. |
| 白宏鹏, 邓东旭, 许光全, 等. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. | |
| [6] |
RAHMAN S A, TOUT H, TALHI C, et al. Internet of Things Intrusion Detection: Centralized, On-Device, or Federated Learning?[J]. IEEE Network, 2020, 34(6): 310-317.
doi: 10.1109/MNET.65 URL |
| [7] | NGUYEN T D, MARCHAL S, MIETTINEN M, et al. DIoT: A Federated Self-Learning Anomaly Detection System for IoT[C]// IEEE. 39th International Conference on Distributed Computing Systems (ICDCS). New York:IEEE, 2019: 756-767. |
| [8] |
LI Beibei, WU Yuhao, SONG Jiarui, et al. DeepFed: Federated Deep Learning for Intrusion Detection in Industrial Cyber-Physical Systems[J]. IEEE Transactions on Industrial Informatics, 2021, 17(8): 5615-5624.
doi: 10.1109/TII.2020.3023430 URL |
| [9] | LUO Kangyang, LI Xiang, GAO Ming. GradMA: A Gradient-Memory-Based Accelerated Federated Learning with Alleviated Catastrophic Forgetting[C]// IEEE. 2023 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York:IEEE, 2023: 3708-3717. |
| [10] | AGRAWAL S, SARKAR S, AOUEDIET O, et al. Federated Learning for Intrusion Detection System: Concepts, Challenges and Future Directions[EB/OL]. [2023-12-12]. https://www.researchgate.net/publication/352505433_Federated_Learning_for_Intrusion_Detection_System_Concepts_Challenges_and_Future_Directions. |
| [11] | LI Xiang, HUANG Kaixuan, YANG Wenhao, et al. On The Convergence of Fedavg on Non-IID Data[EB/OL]. (2019-07-04)[2023-12-11]. https://arxiv.org/abs/1907.02189. |
| [12] |
LI Jianbin, TONG Xin, LIU Jinwei, et al. An Efficient Federated Learning System for Network Intrusion Detection[J]. IEEE Systems Journal, 2023, 17(2): 2455-2464.
doi: 10.1109/JSYST.2023.3236995 URL |
| [13] | OLIVEIRA J A D, GONÇALVES V P, MENEGUETTE R I, et al. F-NIDS—A Network Intrusion Detection System Based on Federated Learning[EB/OL]. [2023-12-27]. https://doi.org/10.1016/j.comnet.2023.110010. |
| [14] | KAIROUZ P, MCMAHAN H B, AVENT B, et al. Advances and Open Problems in Federated Learning[EB/OL]. (2019-12-10)[2023-12-11]. https://arxiv.org/abs/1912.04977. |
| [15] | ZHONG Zhicong, ZHOU Yipeng, WU Di, et al. P-FedAvg: Parallelizing Federated Learning with Theoretical Guarantees[C]// IEEE. 2021-IEEE Conference on Computer Communications. New York: IEEE, 2021: 1-10. |
| [16] | LI Tian, SAHU A K, ZAHEER M, et al. Federated Optimization in Heterogeneous Networks[EB/OL]. (2018-12-14)[2023-12-13]. https://arxiv.org/abs/1812.06127. |
| [17] | LI Qinbin, HE Bingsheng, SONG D. Model-Contrastive Federated Learning[C]// IEEE. 2021 Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2021: 10708-10717. |
| [18] | KIM J, KIM G, HAN B. Multi-Level Branched Regularization for Federated Learning[EB/OL]. (2022-07-14)[2023-12-13]. https://arxiv.org/abs/2207.06936. |
| [19] |
ZHAO Ruijie, WANG Yijun, XUE Zhi, et al. Semisupervised Federated-Learning-Based Intrusion Detection Method for Internet of Things[J]. IEEE Internet of Things Journal, 2023, 10(10): 8645-8657.
doi: 10.1109/JIOT.2022.3175918 URL |
| [20] | YANG Haibo, ZHANG Xin, KHANDURI P, et al. Anarchic Federated Learning[EB/OL]. (2021-08-23)[2023-12-13]. https://arxiv.org/abs/2108.09875. |
| [21] | GU Xinran, HUANG Kaixuan, ZHANG Jingzhao, et al. Fast Federated Learning in the Presence of Arbitrary Device Unavailability[EB/OL]. (2021-06-08)[2023-12-13]. https://arxiv.org/abs/2106.04159. |
| [22] |
JIN Zhigang, ZHOU Junyi, LI Bing, et al. FL-IIDS: A Novel Federated Learning-Based Incremental Intrusion Detection System[J]. Future Generation Computer Systems, 2024, 151: 57-70.
doi: 10.1016/j.future.2023.09.019 URL |
| [23] | MOUSTAFA N, SLAY J. UNSW-NB15: A Comprehensive Data Set for Network Intrusion Detection Systems(UNSW-NB15 Network Data Set)[C]//IEEE. 2015 Military Communications and Information Systems Conference (MilCIS). New York: IEEE, 2015: 1-6. |
| [24] | ZHANG Zheming. Maritime Network Intrusion Detection Based on Deep Learning and Transfer Learning[D]. Shanghai: Shanghai Maritime University, 2022. |
| 张哲铭. 基于深度学习和迁移学习的海事网络入侵检测研究[D]. 上海: 上海海事大学, 2022. |
| [1] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [2] | LIN Yihang, ZHOU Pengyuan, WU Zhiqian, LIAO Yong. Federated Learning Backdoor Defense Method Based on Trigger Inversion [J]. Netinfo Security, 2024, 24(2): 262-271. |
| [3] | ZHAO Pengcheng, YU Junqing, LI Dong. An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning [J]. Netinfo Security, 2024, 24(2): 272-281. |
| [4] | SUN Hongzhe, WANG Jian, WANG Peng, AN Yulong. Network Intrusion Detection Method Based on Attention-BiTCN [J]. Netinfo Security, 2024, 24(2): 309-318. |
| [5] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [6] | ZHAO Jia, YANG Bokai, RAO Xinyu, GUO Yating. Design and Implementation of Tor Traffic Detection Algorithm Based on Federated Learning [J]. Netinfo Security, 2024, 24(1): 60-68. |
| [7] | XU Ruzhi, DAI Lipeng, XIA Diya, YANG Xin. Research on Centralized Differential Privacy Algorithm for Federated Learning [J]. Netinfo Security, 2024, 24(1): 69-79. |
| [8] | LAI Chengzhe, ZHAO Yining, ZHENG Dong. A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(1): 93-105. |
| [9] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [10] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [11] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [12] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| [13] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [14] | CHEN Jing, PENG Changgen, TAN Weijie, XU Dequan. A Multi-Server Federation Learning Scheme Based on Differential Privacy and Secret Sharing [J]. Netinfo Security, 2023, 23(7): 98-110. |
| [15] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||