Netinfo Security ›› 2021, Vol. 21 ›› Issue (9): 40-45.doi: 10.3969/j.issn.1671-1122.2021.09.006
Previous Articles Next Articles
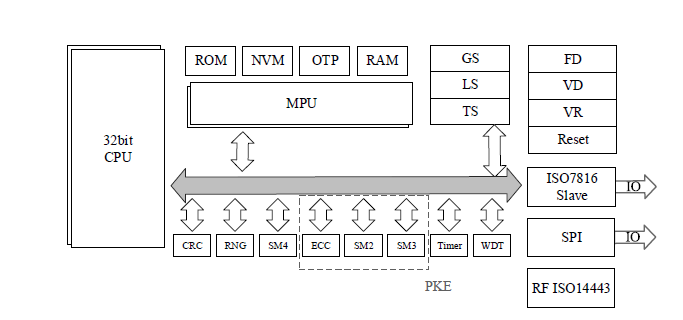
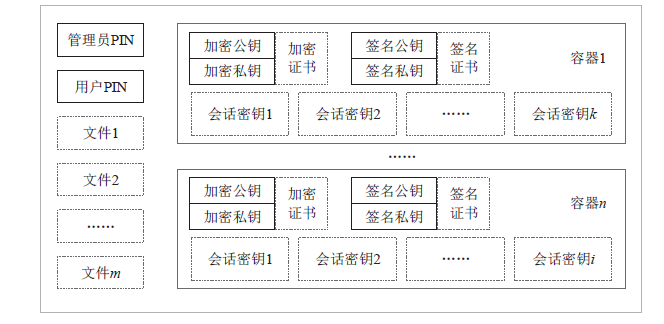
Design and Implementation of Smart Token Based on THD89
JIANG Haozhen1,2, JIANG Bifei1,2( ), HE Langyue1,2, SHAN Yiwei1,2
), HE Langyue1,2, SHAN Yiwei1,2
- 1. State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100195, China
2. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100195, China
-
Received:2021-04-26Online:2021-09-10Published:2021-09-22 -
Contact:JIANG Bifei E-mail:jiangbifei@iie.ac.cn
CLC Number:
Cite this article
JIANG Haozhen, JIANG Bifei, HE Langyue, SHAN Yiwei. Design and Implementation of Smart Token Based on THD89[J]. Netinfo Security, 2021, 21(9): 40-45.
share this article
| [1] | RANKL W, EFFING W. Smart Card Handbook[M]. New York: Wiley Press, 2004. |
| [2] | ZHANG Yinbing, LIU Nannan, ZHANG Li. Authentiation Technology Overview[J] Computer Knowledge and Technology, 2011, 7(9), 2014-2016. |
| 张引兵, 刘楠楠, 张力. 身份认证技术综述[J]. 电脑知识与技术, 2011, 7(9),2014-2016. | |
| [3] | GM/T 0016-2012 Smart Token Cryptography Application Interface Specification[S]. Beijing: State Cryptography Administration, 2012. |
| GM/T 0016-2012 智能密码钥匙密码应用接口规范[S].北京:国家密码管理局, 2012. | |
| [4] | CORDONNIER V M. Smart Cards: Present and Future Applications and Techniques[J]. Electronics & Communication Engineering Journal, 1991, 3(5): 207-212. |
| [5] | WANG Lina, TANG Chuan, XU Jing. Analysis on the Development Trends of Future Chip[J]. World Sci-Tech R&D, 2020, 42(1): 47-56. |
| 王立娜, 唐川, 徐婧. 未来芯片技术发展态势分析[J]. 世界科技研究与发展, 2020, 42(1): 47-56. | |
| [6] | SHAO Xudong. The Research of Access and Control Technology of USB Key[D]. Shanghai: Shanghai Jiao Tong University, 2008. |
| 邵旭东. USB 智能密码钥匙访问控制技术研究[D]. 上海:上海交通大学, 2008. | |
| [7] | YUN M, BU Y. Research on the Architecture and Key Technology of Internet of Things (IoT) Applied on Smart Grid [C]//IEEE. 2010 International Conference on Advances in Energy Engineering, June 19-20, Beijing, China. NJ: IEEE, 2010: 69-72. |
| [8] | GM/T 0017-2012 Smart Token Cryptography Application Interface Data Format Specification[S]. Beijing: State Cryptography Administration, 2012. |
| GM/T 0017-2012 智能密码钥匙密码应用接口数据格式规范[S]. 北京:国家密码管理局, 2012. | |
| [9] | GM/T 0027-2014 Technique Requirements for Smart Token[S]. Beijing: State Cryptography Administration, 2014. |
| GM/T 0027-2014 智能密码钥匙技术规范[S]. 北京:国家密码管理局, 2014. | |
| [10] | FENG Dengguo, QIN Yu, WANG Dan, et al. Research on Trusted Computing Technology[J]. Journal of Computer Research and Development, 2011, 48(8): 1332-1349. |
| 冯登国, 秦宇, 汪丹, 等. 可信计算技术研究[J]. 计算机研究与发展, 2011, 48(8): 1332-1349. | |
| [11] | IT House. Ziguang: The Security Chip THD89 Has Obtained the World Highest Level Certification[EB/OL]. https://www.ithome.com/0/495/550.htm, 2020-07-10. |
| IT 之家. 紫光:安全芯片 THD89 获全球最高等级认证[EB/OL]. https://www.ithome.com/0/495/550.htm, 2020-07-10. | |
| [12] | LI Guojun, WANG Hongxian. Information Security Evaluation and EAL4+ Test for Smart Card Products[J]. Tracks for Standard & Technology, 2008, 10(1): 23-26. |
| 李国俊, 王鸿娴. 信息安全评估与智能卡产品 EAL4 +测评[J]. 信息技术与标准化, 2008, 10(1): 23-26. | |
| [13] |
BEZ R, PIROVANO A. Non-volatile Memory Technologies: Emerging Concepts and New Materials[J]. Materials Science in Semiconductor Processing, 2004, 7(4-6): 349-355.
doi: 10.1016/j.mssp.2004.09.127 URL |
| [14] | XU Junwu, XIE Fang. Developing Smart Card Application with PC/SC [C]//IEEE. 2011 International Conference on Internet Computing and Information Services, September 17-18, 2011, Hong Kong, China. NJ: IEEE, 2011: 286-289. |
| [1] | WANG Yuedong, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Formal Analysis Scheme for 5G Private Network Authentication Protocol [J]. Netinfo Security, 2021, 21(9): 1-7. |
| [2] | GU Zhaojun, YAO Feng, DING Lei, SUI He. Network Security Test of Airport Fuel Supply Automatic Control System Based on Semi-physical Object [J]. Netinfo Security, 2021, 21(9): 16-24. |
| [3] | MA Ling, QIN Liangcheng. Blind Watermarking Algorithm of Color Images Based on DCT-DQFT and QR Decomposition [J]. Netinfo Security, 2021, 21(9): 25-31. |
| [4] | SUN Li. Research and Application of Information Protection Mechanism for Online Education Resource Alliance [J]. Netinfo Security, 2021, 21(9): 32-39. |
| [5] | TAO Yunting, KONG Fanyu, YU Jia, XU Qiuliang. Survey of Number Theoretic Transform Algorithms for Quantum-resistant Lattice-based Cryptography [J]. Netinfo Security, 2021, 21(9): 46-51. |
| [6] | YI Xiaoyang, ZHANG Jian. Image-based Phishing Email Detection Method and Implementation [J]. Netinfo Security, 2021, 21(9): 52-58. |
| [7] | LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm [J]. Netinfo Security, 2021, 21(9): 59-66. |
| [8] | CHEN Qinggang, DU Yanhui, HAN Yi, LIU Xiangyu. IoT Device Recognition Model Based on Depthwise Separable Convolution [J]. Netinfo Security, 2021, 21(9): 67-73. |
| [9] | ZHENG Haixiao, WEN Bin. Bitcoin Illegal Transaction Identification Method Based on Graph Convolutional Network [J]. Netinfo Security, 2021, 21(9): 74-79. |
| [10] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [11] | ZHANG Yongtang. A Secure Area Based Clustering Approach for Traffic Analysis in WSN [J]. Netinfo Security, 2021, 21(9): 80-89. |
| [12] | YANG Xiaoqi, BAI Lifang, TANG Gang. Research and Design of Data Security Evaluation Model Based on DSMM Model [J]. Netinfo Security, 2021, 21(9): 90-95. |
| [13] | JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning [J]. Netinfo Security, 2021, 21(8): 52-61. |
| [14] | BAO Liang, YU Shaohua, TANG Xiaoting. Early Warning of Web Business Security Analysis Based on Markov Chain [J]. Netinfo Security, 2021, 21(8): 91-96. |
| [15] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||