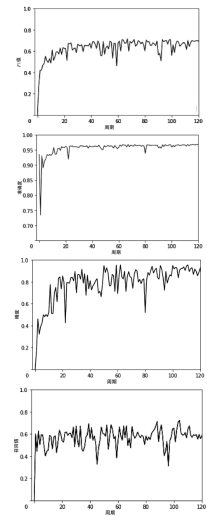
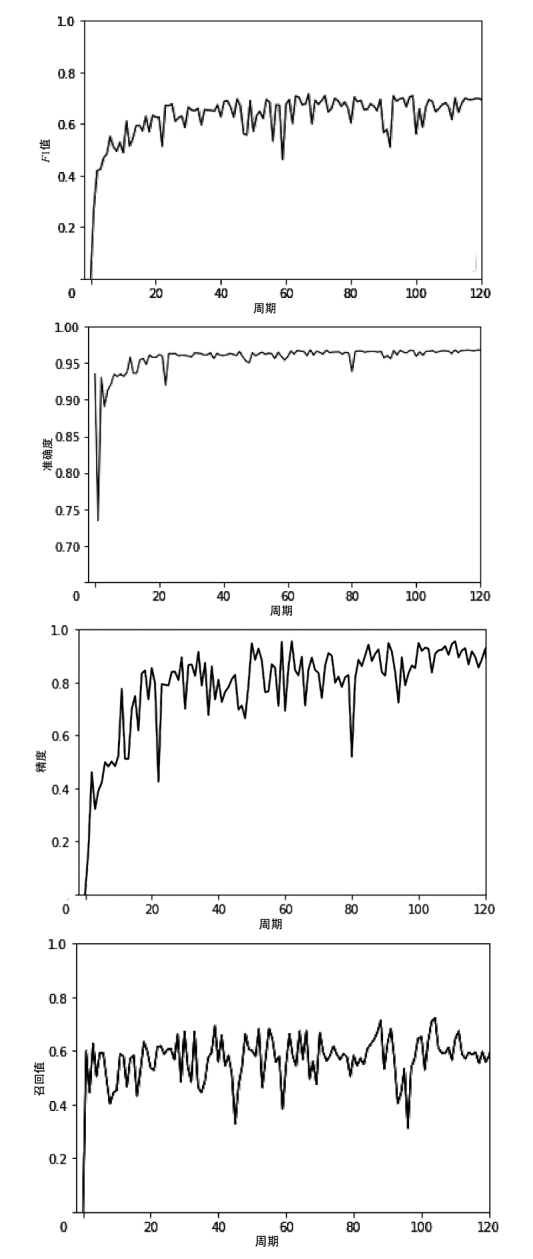
Netinfo Security ›› 2021, Vol. 21 ›› Issue (9): 74-79.doi: 10.3969/j.issn.1671-1122.2021.09.011
Previous Articles Next Articles
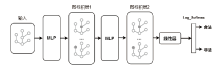
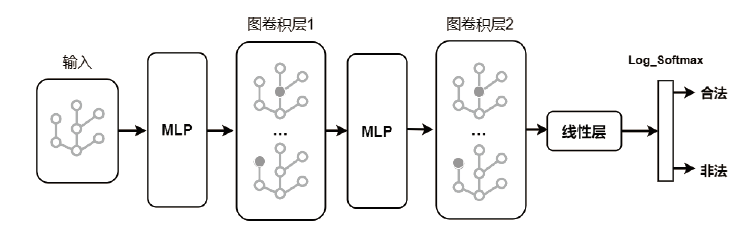
Bitcoin Illegal Transaction Identification Method Based on Graph Convolutional Network
ZHENG Haixiao1,2, WEN Bin1,2( )
)
- 1. School of Information Science and Technology, Hainan Normal University, Haikou 571158, China
2. Key Laboratory of Data Science and Smart Education of Ministry of Education, Haikou 571158, China
-
Received:2021-06-14Online:2021-09-10Published:2021-09-22 -
Contact:WEN Bin E-mail:binwen@hainnu.edu.cn
CLC Number:
Cite this article
ZHENG Haixiao, WEN Bin. Bitcoin Illegal Transaction Identification Method Based on Graph Convolutional Network[J]. Netinfo Security, 2021, 21(9): 74-79.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.09.011
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-peer Electronic Cash System[EB/OL]. https://nakamotoinstitute.org/bitcoin/, 2008-10-31. |
| [2] | BISTARELLI S, SANTINI F. Go with the-bitcoin-flow, with Visual Analytics [C]//ACM. Proceedings of the 12th International Conference on Availability, Reliability and Security, August 29-September 1, 2017, Calabria, ITALY. New York: ACM, 2017: 1-6. |
| [3] | DECKER C, WATTENHOFER R. Information Propagation in the Bitcoin Network [C]// IEEE. IEEE P2P 2013 Proceedings, September 9-11, 2013, Trento, Italy. Piscataway: IEEE, 2013: 1-10. |
| [4] | HARLEV M A, SUN Yinhaohua, LANGENHELDT K C, et al. Breaking Bad: De-anonymising Entity Types on the Bitcoin Blockchain Using Supervised Machine Learning [C]//IEEE. Proceedings of the 51st Hawaii International Conference on System Sciences, January 2-6, 2018, Koloa, Hawaii. Piscataway: IEEE, 2018: 3497-3506. |
| [5] | MONAMO P, MARIVATE V, TWALA B. Unsupervised Learning for Robust Bitcoin Fraud Detection [C]//IEEE. 2016 Information Security for South Africa (ISSA), August 17-18, 2016, Johannesburg, SOUTH AFRICA. New York: IEEE, 2016: 129-134. |
| [6] | WEBER M, DOMENICONI G, CHEN Jie, et al. Anti-money Laundering in Bitcoin: Experimenting with Graph Convolutional Networks for Financial Forensics[EB/OL]. https://arxiv.org/abs/1908.02591, 2019-07-31. |
| [7] | ALARAB I, PRAKOONWIT S, NACER M I. Comparative Analysis Using Supervised Learning Methods for Anti-money Laundering in Bitcoin [C]//ACM. Proceedings of the 2020 5th International Conference on Machine Learning Technologies, June 19-21, 2020, Beijing, China. New York: ACM, 2020: 11-17. |
| [8] | PHAM T, LEE S. Anomaly Detection in Bitcoin Network Using Unsupervised Learning Methods[EB/OL]. https://arxiv.org/abs/1611.03941, 2016-11-12. |
| [9] | LORENZ J, SILVA M I, APARICIO D, et al. Machine Learning Methods to Detect Money Laundering in The Bitcoin Blockchain in The Presence of Label Scarcity[EB/OL]. https://arxiv.org/abs/2005.14635, 2020-05-29. |
| [10] | LI Yang, CAI Yue, TIAN Hao, et al. Identifying Illicit Addresses in Bitcoin Network [C]//Springer. International Conference on Blockchain and Trustworthy Systems, August 6-7, 2020, Dali, China. Singapore: Springer, 2020: 99-111. |
| [11] | ALARAB I, PRAKOONWIT S, NACER M I. Competence of graph Convolutional Networks for Anti-Money Laundering in Bitcoin Blockchain [C]//ACM. Proceedings of the 2020 5th International Conference on Machine Learning Technologies, June 19-21, 2020, Beijing, China. New York: ACM, 2020: 23-27. |
| [12] | ZHANG Chi, GUO Yuan, LI Ming. Review of Development and Application of Artificial Neural Network Models[J]. Computer Engineering and Applications, 2021, 57(11): 57-69. |
| 张驰, 郭媛, 黎明. 人工神经网络模型发展及应用综述[J]. 计算机工程与应用, 2021, 57(11): 57-69. | |
| [13] | KIPF T N, WELLING M. Semi-supervised Classification with Graph Convolutional Networks[EB/OL]. http://arxiv.org/abs/1609.02907, 2016-09-09. |
| [14] | DEFFERRARD M, BRESSON X, VANDERGHEYNST P. Convolutional Neural Networks on Graphs with Fast Localized Spectral Filtering [C]//ACM. Proceedings of the 30th International Conference on Neural Information Processing Systems, December 5-10, 2016, Barcelona, Spain. Red Hook: Curran Associates, 2016: 3844-3852. |
| [15] | BUSCH J, KOCHETUROV A, TRESP V, et al. NF-GNN: Network Flow Graph Neural Networks for Malware Detection and Classification [C]//ACM. 33rd International Conference on Scientific and Statistical Database Management, July 6-7, 2021, FL, Tampa, USA. New York: ACM, 2021: 121-132. |
| [16] | FEY M, LENSSEN J E. Fast Graph Representation Learning with PyTorch Geometric[EB/OL]. https://arxiv.org/abs/1903.02428, 2019-03-06. |
| [1] | WANG Yuedong, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Formal Analysis Scheme for 5G Private Network Authentication Protocol [J]. Netinfo Security, 2021, 21(9): 1-7. |
| [2] | GU Zhaojun, YAO Feng, DING Lei, SUI He. Network Security Test of Airport Fuel Supply Automatic Control System Based on Semi-physical Object [J]. Netinfo Security, 2021, 21(9): 16-24. |
| [3] | MA Ling, QIN Liangcheng. Blind Watermarking Algorithm of Color Images Based on DCT-DQFT and QR Decomposition [J]. Netinfo Security, 2021, 21(9): 25-31. |
| [4] | SUN Li. Research and Application of Information Protection Mechanism for Online Education Resource Alliance [J]. Netinfo Security, 2021, 21(9): 32-39. |
| [5] | JIANG Haozhen, JIANG Bifei, HE Langyue, SHAN Yiwei. Design and Implementation of Smart Token Based on THD89 [J]. Netinfo Security, 2021, 21(9): 40-45. |
| [6] | TAO Yunting, KONG Fanyu, YU Jia, XU Qiuliang. Survey of Number Theoretic Transform Algorithms for Quantum-resistant Lattice-based Cryptography [J]. Netinfo Security, 2021, 21(9): 46-51. |
| [7] | YI Xiaoyang, ZHANG Jian. Image-based Phishing Email Detection Method and Implementation [J]. Netinfo Security, 2021, 21(9): 52-58. |
| [8] | LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm [J]. Netinfo Security, 2021, 21(9): 59-66. |
| [9] | CHEN Qinggang, DU Yanhui, HAN Yi, LIU Xiangyu. IoT Device Recognition Model Based on Depthwise Separable Convolution [J]. Netinfo Security, 2021, 21(9): 67-73. |
| [10] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [11] | ZHANG Yongtang. A Secure Area Based Clustering Approach for Traffic Analysis in WSN [J]. Netinfo Security, 2021, 21(9): 80-89. |
| [12] | YANG Xiaoqi, BAI Lifang, TANG Gang. Research and Design of Data Security Evaluation Model Based on DSMM Model [J]. Netinfo Security, 2021, 21(9): 90-95. |
| [13] | JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning [J]. Netinfo Security, 2021, 21(8): 52-61. |
| [14] | BAO Liang, YU Shaohua, TANG Xiaoting. Early Warning of Web Business Security Analysis Based on Markov Chain [J]. Netinfo Security, 2021, 21(8): 91-96. |
| [15] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||