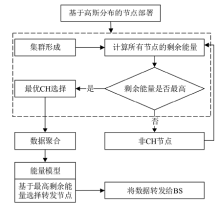
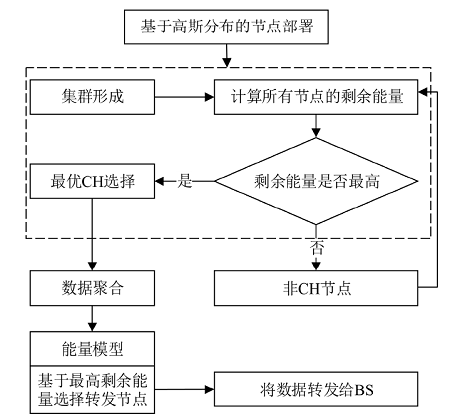
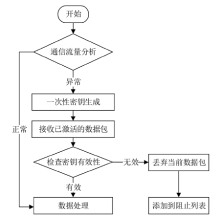
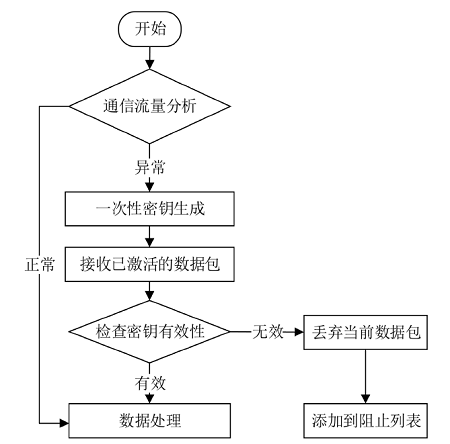
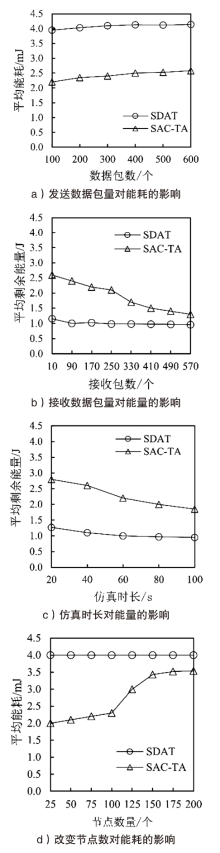
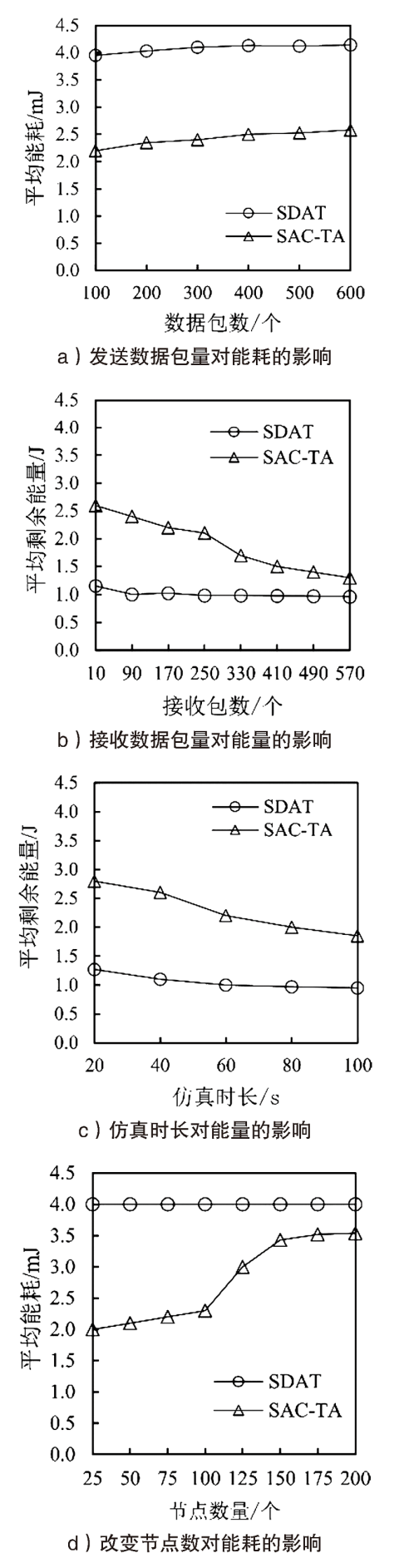
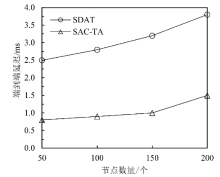
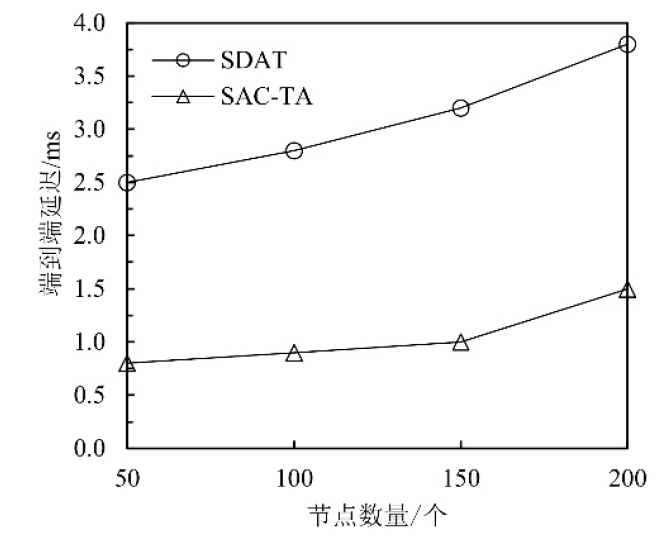
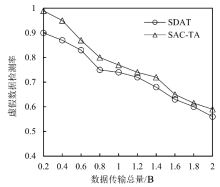
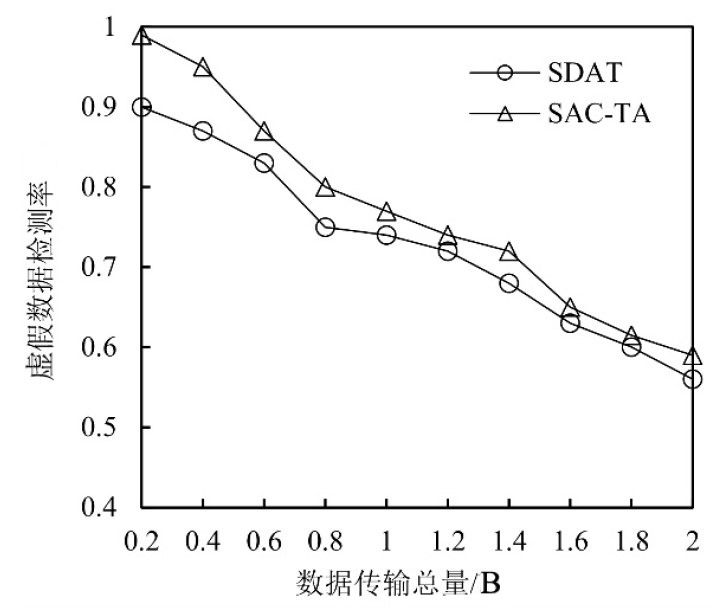
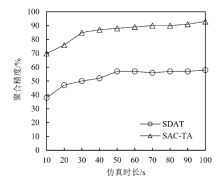
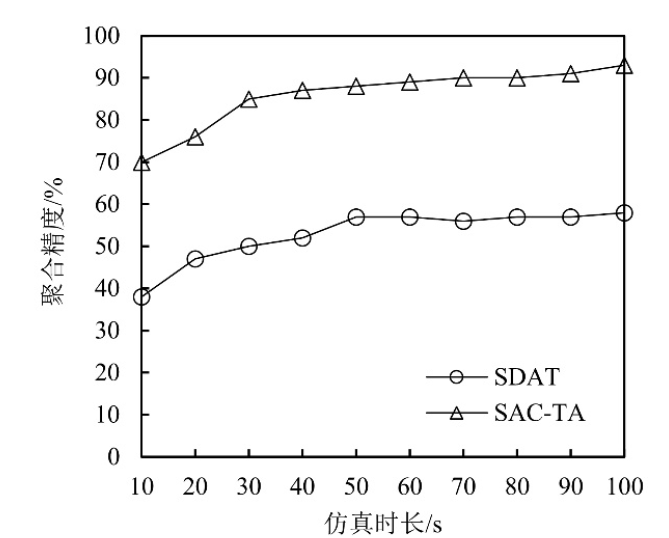
Netinfo Security ›› 2021, Vol. 21 ›› Issue (9): 80-89.doi: 10.3969/j.issn.1671-1122.2021.09.012
Previous Articles Next Articles
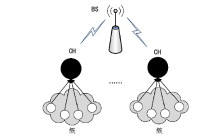
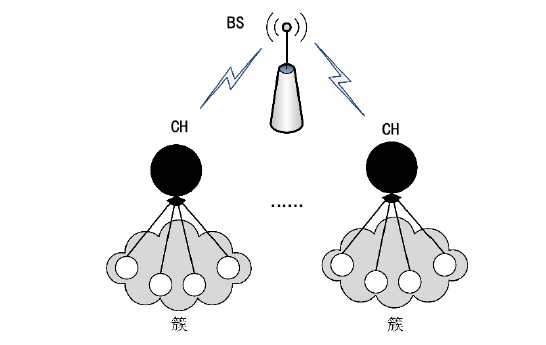
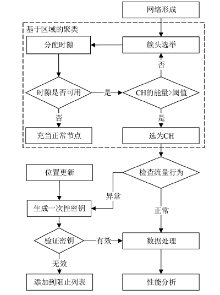
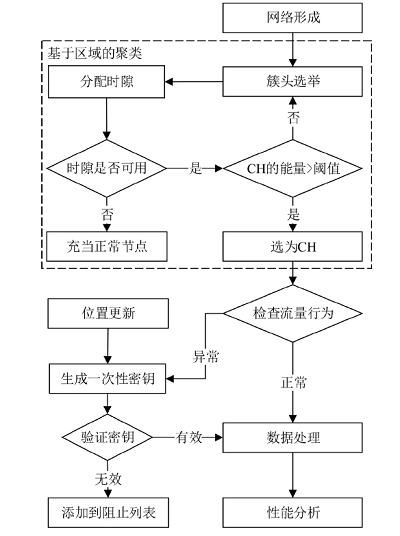
A Secure Area Based Clustering Approach for Traffic Analysis in WSN
- 1. School of Computer, Guangdong Neusoft Institute, Foshan 528225, China
2. Institute of Cooperative Sensing and Advanced Computing Technology, Nanchang Technology Institute, Nanchang 330003, China
-
Received:2021-06-20Online:2021-09-10Published:2021-09-22 -
Contact:ZHANG Yongtang E-mail:gov211@163.com
CLC Number:
Cite this article
ZHANG Yongtang. A Secure Area Based Clustering Approach for Traffic Analysis in WSN[J]. Netinfo Security, 2021, 21(9): 80-89.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.09.012
| [1] |
GOPIKRISHNAN S, PRIAKANTH P. HSDA: Hybrid Communication for Secure Data Aggregation in Wireless Sensor Network[J]. Wireless Networks, 2017, 22(3): 1-18.
doi: 10.1007/s11276-015-0946-8 URL |
| [2] | YU Xiuwu, XIE Xiaoyong, LIANG Beikong, et al. A Deep Mine WSN Localization Algorithm Based on Both Particle Swarm Optimization and Tunnel Partition[J]. China Safety Science Journal, 2019, 29(2): 170-175. |
| 余修武, 谢晓永, 梁北孔, 等. 基于粒子群优化和巷道分区的深井WSN定位算法[J]. 中国安全科学学报, 2019, 29(2): 170-175. | |
| [3] |
XIAN Guangli, WEI Dengjia, YU Benzhi, et al. Aggregation Tree Statistical Computing Based on Functional Encryption[J]. Wuhan University Journal of Natural Sciences, 2019, 24(2): 116-124.
doi: 10.1007/s11859-019-1376-8 URL |
| [4] | HU Xiangdong, XING Youquan, HE Wenxiang. An Energy-efficient Secure Clustering Algorithm Fusing Reputation Evaluation and Patrol Mechanism for WSN[J]. Telecommunication Engineering, 2019, 59(2): 125-132. |
| 胡向东, 邢有权, 何文祥. 融合信誉评估与巡查机制的WSN能量高效安全成簇算法[J]. 电讯技术, 2019, 59(2): 125-132. | |
| [5] | CHEN Xingshu, CHEN Jinghan, SHAO Guolin, et al. A Covert Communication Behavior Detection Method Based on Session Flow Aggregation[J]. Journal of University of Electronic Science and Technology of China, 2019, 48(3): 388-396. |
| 陈兴蜀, 陈敬涵, 邵国林, 等. 基于会话流聚合的隐蔽性通信行为检测方法[J]. 电子科技大学学报, 2019, 48(3): 388-396. | |
| [6] | YING Kezhen, ZHOU Xiannian, MAO Keji. Data Acquisition Algorithm in Wireless Sensor Network Based on Improved Region Growing Method[J]. Journal of Chinese Computer Systems, 2019, 40(3): 567-572. |
| 应可珍, 周贤年, 毛科技, 等. 一种改进区域生长法的WSN数据采集算法研究[J]. 小型微型计算机系统, 2019, 40(3): 567-572. | |
| [7] | MA Dongchao, SUN Xingguo, MA Li. A Regulatable Model Based on Data Aggregation in WSN[J]. Chinese Journal of Computers, 2019, 42(2): 437-452. |
| 马东超, 孙兴国, 马礼. 一种基于数据聚合的传感器网络可调模型[J]. 计算机学报, 2019, 42(2): 437-452. | |
| [8] |
WARD J R, YOUNIS M. Cross-layer Traffic Analysis Countermeasures Against Adaptive Attackers of Wireless Sensor Networks[J]. Wireless Networks, 2019, 25(5): 2869-2887.
doi: 10.1007/s11276-019-02003-9 URL |
| [9] |
ISLAM M, FAHMIN A, HOSSAIN M S, et al. Denial-of-Service Attacks on Wireless Sensor Network and Defense Techniques[J]. Wireless Personal Communications, 2021, 116(4): 1-29.
doi: 10.1007/s11277-020-07702-7 URL |
| [10] |
SONG W, BEASLEY M, PRZYSTUPA K, et al. A Software Deep Packet Inspection System for Network Traffic Analysis and Anomaly Detection[J]. Sensors, 2020, 20(6): 1637-1678.
doi: 10.3390/s20061637 URL |
| [11] |
HAJIAN R, ERFANI S H. CHESDA: Continuous Hybrid And Energy-efficient Secure Data Aggregation For WSN[J]. The Journal of Supercomputing, 2021, 77(5): 5045-5075.
doi: 10.1007/s11227-020-03455-z URL |
| [12] |
PANKHURST R J. Key Generation by Computer[J]. Nature, 2019, 227(5264): 1269-1270.
doi: 10.1038/2271269a0 URL |
| [13] | SONI A, UPADHYAY R, KUMAR A. Performance Improvement of Wireless Secret Key Generation with Colored Noise for IoT[J]. International Journal of Communication Systems, 2019, 32(8): 4124-4137. |
| [14] |
LI GANG, ZHANG ZHE, YU YANG, et al. A Hybrid Information Reconciliation Method for Physical Layer Key Generation[J]. Entropy, 2019, 21(7): 84-90.
doi: 10.3390/e21010084 URL |
| [15] |
BALDI M, CHIARALUCE F, INCIPINI L, et al. Code-based Physical Layer Secret Key Generation in Passive Optical Networks[J]. Ad Hoc Networks, 2019, 89(6): 1-8.
doi: 10.1016/j.adhoc.2019.02.003 URL |
| [16] |
JIAO LING, WANG NING, WANG Peng, et al. Physical Layer Key Generation in 5G Wireless Networks[J]. IEEE Wireless Communications, 2019, 26(5): 48-54.
doi: 10.1109/MWC.7742 URL |
| [17] |
HAZAY C, MIKKELSEN G L, RABIN T, et al. Efficient RSA Key Generation and Threshold Paillier in the Two-party Setting[J]. Journal of Cryptology, 2019, 32(2): 265-323.
doi: 10.1007/s00145-017-9275-7 URL |
| [18] | ZHANG Yongtang. C-RAN Dynamic Resource Allocation Method for DRL. Journal of Chinese Computer Systems, 2021, 42(1): 132-136. |
| 张永棠. 一种深度强化学习的C-RAN动态资源分配方法[J]. 小型微型计算机系统, 2021, 42(1): 132-136. | |
| [19] | CHEN Liangchen, GAO Shu, LIU Baoxu, et al. Research Status and Development Trends on Network Encrypted Traffic Identification[J]. Netinfo Security, 2019, 19(3): 25-31. |
| 陈良臣, 高曙, 刘宝旭, 等. 网络加密流量识别研究进展及发展趋势[J]. 信息网络安全, 2019, 19(3): 25-31. | |
| [20] | WANG Lele, WANG Binqiang, LIU Jiangang, et al. Study on Malicious Program Detection Based on Recurrent Neural Network[J]. Computer Science, 2019, 46(7): 92-96. |
| 王乐乐, 汪斌强, 刘建港, 等. 基于递归神经网络的恶意程序检测研究[J]. 计算机科学, 2019, 46(7): 92-96. | |
| [21] | SINGH P, GUPTA A K, SINGH R. Improved Priority-based Data Aggregation Congestion Control Protocol[J]. Modern Physics Letters B, 2019, 34(2): 1-19. |
| [22] |
CHANG J, LIU F. A Byzantine Sensing Network Based on Majority-ponsensus Data Aggregation Mechanism[J]. Sensors, 2021, 21(1): 248-264.
doi: 10.3390/s21010248 URL |
| [1] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [2] | JIANG Jinfang, HAN Guangjie. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [3] | Baoyuan KANG, Jiaqiang WANG, Dongyang SHAO, Chunqing LI. A Secure Authentication and Key Agreement Protocol for Heterogeneous Ad Hoc Wireless Sensor Networks [J]. Netinfo Security, 2018, 18(1): 23-30. |
| [4] | Hongyan ZHANG, Li XU, Limei LIN. Research on Pairwise Key Establishment Scheme Based on Hypercube in Wireless Sensor Network [J]. Netinfo Security, 2017, 17(12): 1-5. |
| [5] | Bixiu CHEN, Hanxiang JIANG, Zhihong LIN, Jiayue YANG. Research and Discussion on the Construction Data Cloud Platform [J]. Netinfo Security, 2016, 16(9): 154-157. |
| [6] | Dunhao ZHONG, Dongmei ZHANG, Yu ZHANG. A Method of Intrusion Detection in Wireless Sensor Network Based on Similarity Algorithm [J]. Netinfo Security, 2016, 16(2): 22-27. |
| [7] | Wei LIU, Qing YE, Cheng WANG. Improved LEACH Algorithm Based on Dynamic Key Management [J]. Netinfo Security, 2015, 15(8): 41-46. |
| [8] | Bin-ting SU, He FANG, Li XU. Q-Learning-based Routing Protocol for the Balance of WSN Lifetime [J]. Netinfo Security, 2015, 15(4): 74-77. |
| [9] | Wan-wan GONG, Shi-xing LIU, Ting-ting FENG. The Platform Design of Smart-house Based on Wireless Sensor Networks [J]. Netinfo Security, 2015, 15(3): 79-83. |
| [10] | Gege QIU, Xueming WANG, Yansheng ZHANG. Research on WSN Identity Authentication Protocol Based on HECC [J]. Netinfo Security, 2015, 26(12): 54-58. |
| [11] | Shasha SHI, Wenhong SUN, Mingjian JIANG, Haipeng QU. Research on Smart Grid Privacy Protocol Based on Distributed Data Aggregation [J]. Netinfo Security, 2015, 26(12): 59-65. |
| [12] | . Research on Routing Algorithm of Wireless Sensor Network based on Link Quality [J]. , 2014, 14(5): 59-. |
| [13] | . Reference-based Recoverable Concealed Data Aggregation in Heterogeneous Wireless Sensor Networks [J]. , 2014, 14(3): 74-. |
| [14] | HUANG Qi, HUANG Hai, XIE Dong-qing. A Novel AOA Clustering-based Localization Algorithm with High Accuracy [J]. 信息网络安全, 2014, 14(12): 51-55. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||